IT Exam Questions and Solutions Library
A resource named /item is protected by oAuth2 authentication. An endpoint named /login must request authentication. Which method must be used to access the resource by using the REST API? A. Make a GET call to /login that includes the username and password, and retrieve a token to insert into the /item call. B. Make a POST call to /login including the user credentials in the message, and retrieve a token to insert into the authorization header of the /item call. C. Make a GET call to /item, then make a call to /login that includes the username and password in the body of the message, and wait for the authorization code. D. Make a POST call to /item that includes the username and password in the body of the request message, and submit it to request access. Suggested Answer: B
Refer to the exhibit. What occurs when the script runs? A. The contents of both files are displayed. B. The total length of the files is displayed. C. The files are combined. D. File differences are compared. Suggested Answer: D
What is a capability of Cisco Webex? A. Join preconfigured or new spaces with fixed user rights. B. Configure devices at scale via automation scripts or by manual execution. C. Initiate or respond to calls automatically via automation. D. Get space history or notified in real time when new messages are posted. Suggested Answer: D
Refer to the exhibit. A developer uses a REST API to retrieve information about wireless access points. The API returns an HTTP 403 error when making a GET request. What resolves this issue? A. Provide the developer with the correct user access rights. B. Change the request HTTP method from GET to POST. C. Change the request timeout in the client software. D. Include a username/password request header. Suggested Answer: A
A developer starts to learn about building applications that use Cisco APIs. The developer needs access to Cisco security products in a development lab to test the first new application that has been built. Which DevNet resource must be used? A. DevNet Code Exchange B. DevNet Automation Exchange C. DevNet Sandbox D. DevNet Communities Suggested Answer: C
Refer to the exhibit. A network engineer is creating a Python script to programmatically save network device configurations. Which code snippet must be placed onto the blank in the code? A. self.save B. {self.headers} C. restconf D. netconf Suggested Answer: C
DRAG DROP - Drag and drop the characteristics from the left onto the software development methodologies on the right.Suggested Answer:

Which two HTTP code series relate to errors? (Choose two.) A. 100 B. 200 C. 300 D. 400 E. 500 Suggested Answer: DE
What is a benefit of using Python classes? A. They improve code organization by keeping data members and methods together. B. They remove the concept of inheritance to improve code readability and maintainability. C. They allow a Python script to import code from various independent modules. D. They simplify integration by testing the classes independently from other components. Suggested Answer: A
What is a capability of model-driven programmability for infrastructure automation? A. compatibility with any networking device B. automatic version control C. generic APIs that are compatible with multiple platforms D. a single data model across the network Suggested Answer: D
Refer to the exhibit. A developer needs to create a webhook to send all Cisco Webex messages to a third-party tool by using the Cisco Webex API The developer must authenticate with the API before any API calls can be made. To automate the procedure, a Python script is used. Which code snippet must be placed onto the blank in the code? A. ‘Authentication’: f’Bearer {token}’, B. ‘Authentication’: f’Basic {token}’, C. ‘Authorization: f’Basic {token}’, D. ‘Authorization: f’Bearer {token}’, Suggested Answer: D
An engineer must run tests on several Cisco controllers. Due to the nature of the task, the infrastructure must be running at all times and have access to APIs. Which Cisco DevNet source must the engineer use? A. DevNet Learning Labs B. DevNet Code Exchange C. DevNet Sandbox D. DevNet API documentation Suggested Answer: C
What does a developer import in a script to parse a file from XML to Python? A. function B. library C. variable D. method Suggested Answer: B
Refer to the exhibit. Which API is called when the REMOTE TU sends a TCONNECT Response to the LOCAL TU? A. TCONNECT completion B. TCONNECT request C. TCONNECT indication D. TCONNECT confirm Suggested Answer: A
A lead engineer is managing the development of a web application with a team of remote developers using Git as the version control system. What is the advantage of a version control system that allows developers to pick code from any part of the project and perform updates on it? A. efficient handling of projects B. linear development C. build automation D. nonlinear development Suggested Answer: D
Refer to the exhibit. A developer needs to write a Python script to automate a task using a NETCONF query. What does the query do? A. It deletes some device configurations. B. It deletes all the device configurations. C. It shuts off the device. D. It adds a new device configuration. Suggested Answer: A
An engineer clones a repository that contains a Python script from GitLab to a laptop. After modifying the code, the engineer wants to validate the changes. Which command starts the CI/CD pipeline and runs the automated tests? A. git commit B. git test C. git fetch D. git push Suggested Answer: D
Refer to the exhibit. A developer needs to create a Docker image that listens on port 5000. Which code snippet must be placed onto the blank in the code? A. PORT 5000 B. LISTEN 5000 C. EXPOSE 5000 D. OPEN 5000 Suggested Answer: C
What is a benefit of version control? A. application of code directly to hardware B. tracking development changes C. reuse of code-on-code patches D. compatibility with back-end systems Suggested Answer: B
A network engineer makes several API calls to Cisco Prime to retrieve a list of all devices. Each time a response is received, only a subset of the devices is returned. The engineer notices that HTTP code 429 is returned instead of 200 for some API calls. Why did the response exclude some of the devices? A. The API applied an offset that was indicated in the request. B. The API failed to identify how many items to retrieve. C. The API timed out the request. D. The API rate limited the request. Suggested Answer: D
Refer to the exhibit. An engineer wants to create a Bash script to automate a workflow that is related to a machine learning-based application. The engineer wants to use the application as a container and use an image from the open-source public repository. What is accomplished by the script? A. Create a new software package B. Install and remove files. C. Update an existing software package. D. Install a software package. Suggested Answer: D
A distributed application was developed using the Cisco Intersight SDK. While testing the interaction between the application and the Intersight API. the requests that were sent to the server could not execute because the application was blocked by the firewall. Which URL and port must be provided to the firewall administrator to allow the traffic? A. svc.intersight.com port 443 B. intersight.com port 443 C. intersight.com port 80 D. svc.intersight.com port 80 Suggested Answer: A
What is a characteristic of test-driven development? A. It enables code refactoring. B. User tests are created after deployment. C. Infrastructure testing is done at every stage. D. Large updates are applied infrequently. Suggested Answer: A
What is the purpose of Infrastructure as Code? A. to provide the ability of independent development process B. to manually configure and manage infrastructure at scale C. to apply new practices on the development process D. to use development engineering practices on the infrastructure Suggested Answer: D
Refer to the exhibit. The IT team deployed a new Linux virtual machine for a software engineer to use, but the engineer is not comfortable configuring services using Bash. Which workflow is automated by the Ansible playbook? A. Restart the network on the eth0 interface and start the httpd service if it is not already started. B. Restart the httpd service and start the network service for the eth0 interface. C. Start the network service on the eth0 interface even if it was brought down manually. D. Restart the httpd service and the network service regardless of the state. Suggested Answer: A
An engineer must investigate the problems on a web application and address them to related teams. The engineer verifies the application reachability from the single public IP address with port and discovers that HTTPS access works to three servers of a network farm with IP 172.16.50.1 .2 and .4, but HTTPS access to the server with IP 172.16.50.3 does not work. Which problem type must be addressed as the cause for the case? A. VPN connectivity B. NAT C. blocked transport port D. proxy Suggested Answer: C
DRAG DROP - Drag and drop the Python data transformation methods from the left onto the data formats on the right.Suggested Answer:

Which RFC 1918 address space includes a subnet of 172.16.0.0 that uses a mask of 255.255.0.0? A. class A B. class B C. class C D. class D Suggested Answer: B
Refer to the exhibit. A network engineer makes a RESTCONF API call to Cisco IOS XE to retrieve information. Which HTTP method and URL does the engineer use to make the API call? A. GET https://devnetlab.local/restconf/api/running/native/GigabitEthernet B. GET https://devnetlab.local/restconf/api/running/native/interface/GigabitEthernet C. GET https://devnetlab.local/restconf/api/running/native/interface/GigabitEthernet/2/ D. GET https://devnetlab.local/restconf/api/running/ios/native/interface/GigabitEthernet/1/ Suggested Answer: C
Which Cisco compute management platform controls server, network, storage, and virtual resources with policy-driven management for up to 10000 physical Cisco servers? A. UCS Central B. Cisco Intersight C. Cisco DNA Center D. Cisco HyperFlex Suggested Answer: A
An engineer must review and clean up a code repository. During the review, the engineer finds a file named config.json that contains API URLs, shared keys, and other application configurations. Which two methods, according to best practice, must be used to protect secrets? (Choose two.) A. Store in plaintext if they are not stored in a code repository. B. Store as plaintext when the server is secured physically. C. Never appear in plaintext at rest or in transit. D. Make them long, secure strings that include numbers with special characters. E. Always store in a secure vault. Suggested Answer: CE
Which IP service is responsible for automatically assigning an IP address to a device? A. DNS B. DHCP C. SNMP D. NAT Suggested Answer: B
Refer to the exhibit. The server.js Node.js script runs after the Dockerfile creates its container. What is the working directory of the application inside the container? A. /source B. /app C. /app/source D. /app/production Suggested Answer: B
What is an advantage of device-level management as compared to controller-level management to automate the configuration of network devices? A. Device-level management has access to all devices from a single point on the network and controller-level management does not. B. Device-level management supports all subsets of the potential device settings and controller-level management does not. C. Device-level management supports REST API-enabled devices and controller-level management does not. D. Device-level management requires one controller per vendor and controller-level management does not. Suggested Answer: B
Refer to the exhibit. A network engineer changes the configuration of a device interface, and the device becomes unreachable. The engineer accesses the server console to review the differences with the backup file. Which change must be made in the eth1.cfg file to restore the original configuration? A. Remove the line GATEWAY="192.168.1.254". B. Remove the line IPADDR="192.168.1.20/32". C. Add lines ONBOOT=yes and GATEWAY="192.168.1.254". D. Add lines ONBOOT=yes and IPADDR="192.168.1.20/32". Suggested Answer: A
What is a benefit of organizing code into modules? A. improves compatibility with the hardware B. improves the user interface C. easier to work with the code D. easy to compile and test Suggested Answer: C
A company wants to optimize the use of its existing compute resources by running multiple operating systems on a single Cisco UCS server. The company also wants to minimize new purchases for physical resources such as hard drives. The network connectivity between virtual hosts and the physical host needs to be bridged. Which deployment model type must be used? A. bare metal B. Docker C. container D. virtual machine Suggested Answer: D
A retail store is launching an online presence through their new application. The amount of end-user traffic on the application is expected to fluctuate depending on whether there are sales on or not. The application developer has decided to adopt an application-deployment model that allows them to leverage cloud bursting. Which deployment approach would allow cloud bursting? A. local infrastructure B. edge computing C. on-premises D. hybrid Suggested Answer: D
Which HTTP status code means that the server cannot or will not process the request because of a perceived client error? A. 100 B. 203 C. 303 D. 400 Suggested Answer: D
Refer to the exhibit. A developer created a Python script that is used by network engineers to retrieve information from Cisco DNA Center by using the Cisco DNA Center API. Which workflow does the Python script execute? A. Retrieve all the devices and serial numbers in Cisco DNA Center. B. Provision a new device in Cisco DNA Center. C. Retrieve all network information in Cisco DNA Center. D. Retrieve a specific device from Cisco DNA Center by using a serial number. Suggested Answer: D
Refer to the exhibit. A developer is using cURL to test connectivity to a webpage. The request times out after 10 seconds. The developer tested connectivity by using Ping and can open a TCP socket to the remote server by using Telnet. Other users confirm that they can access the webpage from their device. The developer has SSH access to the remote server and runs commands to troubleshoot. What causes the issue? A. Connectivity from the remote server back to the client is down. B. Firewall rules on the remote server block the client on port 443. C. Application-layer security features on the remote server block the connection. D. HTTPS proxy configured on the remote server blocks the connection. Suggested Answer: D
Which CI/CD component is used to store and track code changes during development? A. Artifactory B. Vault C. version control system D. ticketing system Suggested Answer: C
Refer to the exhibit. A network engineer wants to change the name of a device. The engineer submits a NETCONF request and receives a response. Which NETCONF request did the engineer submit? A.
B.
C.
D.
Suggested Answer: D
Which service must be configured to provide time synchronization to the devices on a network to make it easier to correlate log events? A. DHCP B. SNMP C. NAT D. NTP Suggested Answer: C
A distributed application is under development and the interaction between the application and an API is being tested using the URL and port: devasc468262987.com port 443 The requests that were sent to the server could not execute because the application was blocked by the firewall. Which protocol must be allowed by the firewall to fix the issue? A. SSH B. HTTP C. HTTPS D. FTP Suggested Answer: C
Refer to the exhibit. A developer is creating a YANG file to design data with Python. Which code must be used for the tree of the YANG file? A. pyang -f tree future-industries-tech.yang B. pyang -i tree future-industries-tech.yang C. pyang -f leaf future-industries-tech.yang D. pyang tree future-industries-tech.yang Suggested Answer: C
Which data structure is created when parsing XML data in Python? A. item B. list C. library D. dictionary Suggested Answer: D
What should be used to send real-time notifications to a third-party application when an event occurs in an SD-WAN deployment? A. loopback B. callback C. API D. webhook Suggested Answer: D
A network engineer developed an application that performs configuration automation. The engineer used the MVC model for the application design. It has a web interface for users to interact, collect configuration directives for specific devices, and communicate with network devices through REST-based APIs. What is the advantage of the model component in MVC design in this scenario? A. It contains data and responds to state queries and updates. B. It keeps views and controllers updated during the execution. C. It defines main application behavior and contains functions to run. D. It renders the data for easy use by the remaining parts of the design. Suggested Answer: A
DRAG DROP - Drag and drop the characteristics from the left onto the software development methods on the right.Suggested Answer:

What is impacted by the network bandwidth on an application? A. time taken for a data packet to travel between two endpoints B. number of data packets dropped during transmission C. consistency in the arrival of data packets between two endpoints D. rate of data transferred between two endpoints Suggested Answer: A
What is a benefit of a model-driven approach for infrastructure automation? A. It automates the translation of a declarative language of the model into an actionable script. B. It enforces the generation and verification of all automation scripts through the modeling environment. C. It provides a small learning curve and helps system administrators with limited coding experience. D. It ensures that system administrators gain a good understanding of coding, and expand their experience and capabilities. Suggested Answer: A
Which network device plane is responsible for handling QoS? A. management plane B. data plane C. configuration plane D. control plane Suggested Answer: B
Which two protocols are associated with the control plane on a network device? (Choose two.) A. BGP B. UDP C. SNMP D. FTP E. OSPF Suggested Answer: AE
Drag and drop the first four stages of a DevOps toolchain from the left into the order on the right to create a new complex product. Not all options are used. Select and Place:Correct Answer:

Drag and drop the code from the bottom onto the box where the code is missing to retrieve the RESTCONF running configuration for an interface named TwentyFiveGigabitEthernet 1/1/2. Not all options are used. Select and Place:
Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing in the Python unittest to verify whether the function returns the correct values. Not all options are used. Select and Place:
Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that allows an engineer to retrieve interface data. Not all options are used. Select and Place:
Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing in the Cisco Meraki code to obtain the connectivity testing destinations for an MX network. Not all options are used. Select and Place:
Correct Answer:

Refer to the exhibit. Drag and drop the code snippets from the bottom into the blanks in the Python code to import the Cisco Meraki library and set the API key for authorization. Select and Place:
Correct Answer:

An engineer must configure devices over Cisco DNA Center. A repository already exists that contains scripts to communicate with Cisco DNA Center over APIs. The engineer wants to add their own scripts to the same repository. Drag and drop the actions from the left into the order on the right to clone a Git repository named DN Select and Place:Correct Answer:

Drag and drop the steps from the left into the order on the right to create a testdriven development cycle. Some options are used more than once. Select and Place:Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script by using the Cisco SDK. Not all options are used. Select and Place:

Correct Answer:
Drag and drop the steps from the left into the order on the right to implement a CI/CD toolchain. Not all options are used. Select and Place:
Correct Answer:
Refer to the exhibit. A developer is responsible for managing an application. The developer wants to deploy the new version of the application on the test environment whenever it is released. To automate this work flow, the developer writes a bash script. Drag and drop the deployment steps from the left into the order on the right to identify the work flow that is automated by the script. Select and Place:

Correct Answer:
Refer to the exhibit. Running the git merge example_branch command results in an error due to conflicts. The exhibit shows the output of the git log command on a branch named example_branch. Drag and drop the code from the bottom into the order to resolve the conflicts and merge example_branch into the remote master branch. Select and Place:

Correct Answer:
Refer to the exhibit. A new loopback34 must be created on a Cisco IOS XE router that has an IP address of 10.34.1.2/24. Drag and drop the code from the bottom onto the box where the code is missing to construct the Python script that configures the IP address on the interface according to the YANG data model of ietf-interfaces. Not all options are used. Select and Place:

Correct Answer:
Drag and drop the common API styles from the left onto the requirement on the right. Select and Place:
Correct Answer:
Refer to the exhibit. A script must create a new team, create a new space, send a message, and create a participant. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used. Select and Place:

Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to configure the GigabitEthernet 3 interface. Not all options are used. Select and Place:
Correct Answer:

Drag and drop the protocols from the left onto the management technologies on the right that expose the protocols to network engineers. Select and Place:
Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to create a new room within Webex Teams. Not all options are used. Select and Place:
Correct Answer:

Drag and drop the characteristics from the left onto the software development methods on the right. Select and Place:
Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to return the number of interfaces on a network device by using the Cisco DNA Center SDK. Not all options are used. Select and Place:
1: Device_id 2: DNACenterApi 3: port_list 4: devices
Refer to the exhibit. A bespoke meeting booking system must be integrated with Cisco Webex so that meetings are created automatically. Drag and drop the code from the bottom onto the box where the code is missing to create a sample meeting. Not all options are used. Select and Place:

Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a request that generates a security token and gets a list of network devices. Not all options are used. Select and Place:

Correct Answer:
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. The Python script retrieves a list of tasks from a to-do list for effective project management purposes. Not all options are used. Select and Place:
Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used. Select and Place:

Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to add a subnet to each bridge domain in the Ten1 tenant. Not all options are used. Select and Place:

Correct Answer:
Drag and drop characteristics from the left onto the infrastructure management methodologies on the right. Select and Place:
Correct Answer:
Refer to the exhibit. Drag and drop the Docker file contents from the left onto the functions on the right that create a container image to run traceroute to track network path to specific targets. Not all options are used. Select and Place:

Correct Answer:
Drag and drop the code from the bottom onto the box where the code is missing to enable ports on a switch by using RESTCON Not all options are used.
Drag and drop the code from the bottom onto the box where the code is missing to complete the error path scenario. Not all options are used. Select and Place:
Correct Answer:
Drag and drop the characteristics from the left onto the corresponding categories on the right to compare RESTful and RPC APIs. Select and Place:
Correct Answer:
Drag and drop the code from the bottom onto the box where the code is missing to authenticate with the Cisco DNA Center REST API by using basic authentication. Then generate a token for later use. Not all options are used. Select and Place:
Correct Answer:
Drag and drop the capabilities from the left onto the Cisco Network Management Platforms that support the capabilities on the right. Select and Place:
Correct Answer:
An engineer must make changes on a network device through the management platform API. The engineer prepares a script to send the request and analyze the response, check headers, and read the body according to information inside response headers. Drag and drop the HTTP header values from the left onto the elements of an HTTP response on the right. Select and Place:
Correct Answer:
Drag and drop the API characteristics from the left onto the corresponding categories on the right. Select and Place:Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct an API request that creates a new IPv4 prefix. Not all options are used. Select and Place:
Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing on the Meraki Python script to create a new network. Select and Place:
Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to delete Developer1 from the ACI programmers' meeting room. Not all options are used. Select and Place:
Correct Answer:

Drag and drop the code from the bottom onto the box where the code is missing to obtain an authorization token by using the Cisco DNA Center API. Not all options are used. Select and Place:Correct Answer:

Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used. Select and Place:Correct Answer:

Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to construct a request to find the Cisco DNA Center switch count. Not all options are used. Select and Place:
Correct Answer:

Drag and drop the Docker file instructions from the left onto the descriptions on the right. Not all options are used. Select and Place:Correct Answer:

Drag and drop the code from the bottom onto the box where the code is missing in the Bash script to complete the missing assignments. Select and Place:
Correct Answer:
Drag and drop the Bash commands from the left onto the related actions on the right. Select and Place:Correct Answer:
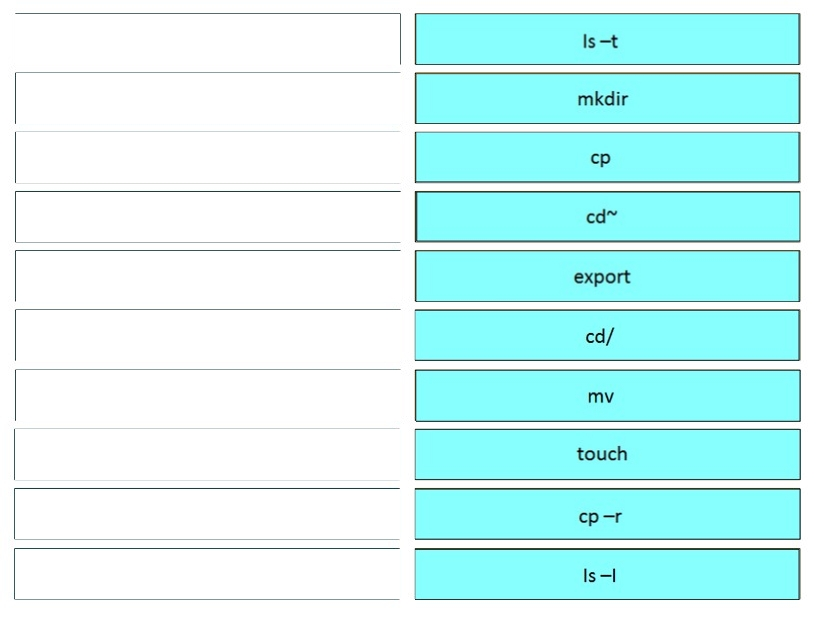
Refer to the exhibit.Drag and drop the variables from the left onto the item numbers on the right that match the missing assignments in the exhibit. Select and Place:
Correct Answer:
(use tar in order to create your backup file)
Drag and drop the descriptions from the left onto the correct application deployment models on the right. Select and Place:Correct Answer:

Drag and drop elements of the RESTCONF Protocol stack from the left onto the correct descriptors on the right. Not all elements on the left are used. Select and Place:Correct Answer:

Drag and drop the types of management from the left onto the levels at which they are performed on the right. Select and Place:Correct Answer:

Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used. Select and Place:
Correct Answer:

Drag and drop the network component names from the left onto the correct descriptions on the right. Not all options are used. Select and Place:Correct Answer:

Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used. Select and Place:Correct Answer:

Drag and drop the functionalities from the left onto the correct networking devices on the right. Select and Place:Correct Answer:

Drag and drop the function on the left onto the type of plane that handles the function on the right. Select and Place:Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script by using the Cisco SDK. Not all options are used.
Drag and drop the functions from the left onto the networking devices on the right. Select and Place:
Correct Answer:
Refer to the exhibit. A script must output details of all the Cisco Meraki MS220-BP switches across all organizations and networks. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used. Select and Place:

Correct Answer:
Drag and drop the code snippets from the bottom onto the blanks in the code to complete the happy path scenario. Not all options are used. Select and Place:
Correct Answer:
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of network devices from Cisco DNA Center. Not all options are used. Select and Place:Correct Answer:

Drag and drop the steps from the left into order on the right to create a common CI/CD pipeline process. Not all options are used. Select and Place:
Correct Answer:
Drag and drop the code from the bottom onto the box where the code is missing to obtain a list of network devices by using the Cisco Meraki API. Not all options are used. Select and Place:Correct Answer:

Refer to the exhibit. Drag and drop the actions from the left that the contents of this Docker file accomplish onto the right. Not all options are used. Select and Place:

Correct Answer:
Drag and drop the Git commands from the left onto the right that add modified local files to a remote repository. Not all options are used. Select and Place:Correct Answer:

Refer to the exhibits.
Drag and drop the code from the left onto the item numbers on the right to complete the Meraki Python script shown in the exhibit. Select and Place:

Correct Answer:
Drag and drop the Python code from the left onto the correct step on the right to call a REST API. Select and Place:Correct Answer:

Refer to the exhibit.Drag and drop the descriptors from the left onto the corresponding parts of the API request and response on the right. Select and Place:

Correct Answer:
Drag and drop the HTTP status codes from the left onto the correct descriptions on the right. Select and Place:Correct Answer:

Refer to the exhibit. A developer needs to automatically retrieve all of the messages of a Webex room with the roomId of `Y2lzY29zcGFyazovL3Vz397468502YjU5NjAtNTk0Zi0xMWVhLTk0Mj`. Using the Webex API documentation shown, drag and drop the code snippets from below onto the code to complete the Python script to list all of the messages in the room. Not all options are used. Select and Place:
Correct Answer:

Refer to the exhibit. Drag and drop the code from the bottom onto the blanks in the code to construct a cURL command using the Cisco DNA Center API, which will provide the details of a WLAN controller with Id ab123456789. Not all options are used. Select and Place:
Correct Answer:

Drag and drop the HTTP methods from the left onto their generally accepted corresponding create, read, update, and delete operations on the right. Select and Place:Correct Answer:

Refer to the exhibit.
Drag and drop the code from the left onto the item numbers on the right to complete the Meraki code to obtain a list of clients which have used this network. Select and Place:
Correct Answer:

Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used. Select and Place:Correct Answer:

Drag and drop the code snippets from the bottom to the blanks in the code to test the API response through the Python unittest library. Not all options are used. Select and Place:Correct Answer:

Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements: * Must time out if the response is not received within 2 seconds. * Must utilize client certificates and SSL certificate verification. * Must utilize basic authentication that uses a username of admin and a password of cisco. * Must save the response to an object named response. Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used. Select and Place: Correct Answer:
Drag and drop the code snippets from the bottom to the blanks in the code to complete the HTTP response. Not all options are used. Select and Place: Correct Answer:
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to complete the function that adds a new global access rule that denies traffic using the Cisco ASA REST API. Not all options are used. Select and Place:
Correct Answer:
Drag and drop the API characteristics from the left onto the categories on the right. Select and Place:Correct Answer:

Drag and drop the requests from the left into the order on the right to create and check the path trace between two devices using Cisco DNA center API. Select and Place:Correct Answer:

Refer to the exhibit. A Python script must delete all Cisco Catalyst 9300 Series switches that have an uptime that is greater than 90 days. The script must also query for the status of all the other devices. Drag and drop the code from the bottom onto the box where the code is missing to complete the script. Not all options are used. Select and Place:
Correct Answer:

Drag and drop the element of the Finesse API on the left onto its functionality on the right. Select and Place:Correct Answer:
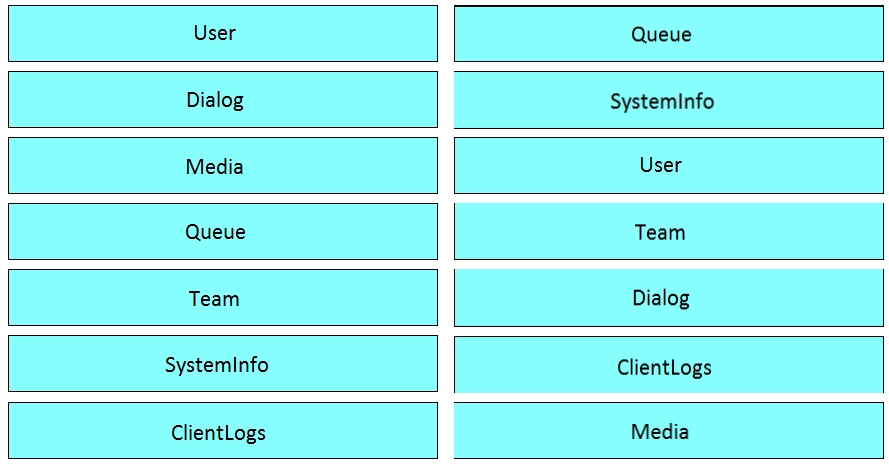
Drag and drop the capability on the left onto the Cisco compute management platform that supports the capability on the right. Select and Place:Correct Answer:

Drag and drop the code from the bottom onto the box where the code is missing in the Python script to complete a function to return all the clients on a network by using the Cisco Meraki Dashboard API. Not all options are used. Select and Place:Correct Answer:

What is a benefit of organizing code into modules? A. improves compatibility with the hardware B. improves the user interface C. easier to work with the code D. easy to compile and test Correct Answer: C
Which HTTP status code is returned when a server is down for maintenance? A. 401 B. 403 C. 501 D. 503 Correct Answer: B
What is the well-known port for HTTPS? A. 81 B. 443 C. 80 D. 440 Correct Answer: B
Which data structure is created when parsing XML data in Python? A. item B. list C. library D. dictionary Correct Answer: D
Refer to the exhibit. A network engineer changes the configuration of a device interface, and the device becomes unreachable. The engineer accesses the server console to review the differences with the backup file. Which change must be made in the eth1.cfg file to restore the original configuration? A. Remove the line GATEWAY="192.168.1.254". B. Remove the line IPADDR="192.168.1.20/32". C. Add lines ONBOOT=yes and GATEWAY="192.168.1.254". D. Add lines ONBOOT=yes and IPADDR="192.168.1.20/32". Correct Answer: A
A company wants to optimize the use of its existing compute resources by running multiple operating systems on a single Cisco UCS server. The company also wants to minimize new purchases for physical resources such as hard drives. The network connectivity between virtual hosts and the physical host needs to be bridged. Which deployment model type must be used? A. bare metal B. Docker C. container D. virtual machine Correct Answer: D
A retail store is launching an online presence through their new application. The amount of end-user traffic on the application is expected to uctuate depending on whether there are sales on or not. The application developer has decided to adopt an application-deployment model that allows them to leverage cloud bursting. Which deployment approach would allow cloud bursting? A. local infrastructure B. edge computing C. on-premises D. hybrid Correct Answer: D
Which HTTP status code means that the server cannot or will not process the request because of a perceived client error? A. 100 B. 203 C. 303 D. 400 Correct Answer: D
Refer to the exhibit. A developer created a Python script that is used by network engineers to retrieve information from Cisco DNA Center by using the Cisco DNA Center API. Which work flow does the Python script execute? A. Retrieve all the devices and serial numbers in Cisco DNA Center. B. Provision a new device in Cisco DNA Center. C. Retrieve all network information in Cisco DNA Center. D. Retrieve a specific device from Cisco DNA Center by using a serial number. Correct Answer: D
Refer to the exhibit. A developer is using cURL to test connectivity to a webpage. The request times out after 10 seconds. The developer tested connectivity by using Ping and can open a TCP socket to the remote server by using Telnet. Other users confirm that they can access the webpage from their device. The developer has SSH access to the remote server and runs commands to troubleshoot. What causes the issue? A. Connectivity from the remote server back to the client is down. B. Firewall rules on the remote server block the client on port 443. C. Application-layer security features on the remote server block the connection. D. HTTPS proxy configured on the remote server blocks the connection. Correct Answer: D
Which CI/CD component is used to store and track code changes during development? A. Artifactory B. Vault C. version control system D. ticketing system Correct Answer: C
Refer to the exhibit. A network engineer wants to change the name of a device. The engineer submits a NETCONF request and receives a response. Which NETCONF request did the engineer submit?



Correct Answer: D Correct Answer: D
Which service must be configured to provide time synchronization to the devices on a network to make it easier to correlate log events? A. DHCP B. SNMP C. NAT D. NTP Correct Answer: C
A distributed application is under development and the interaction between the application and an API is being tested using the URL and port: devasc468262987.com port 443 The requests that were sent to the server could not execute because the application was blocked by the firewall. Which protocol must be allowed by the firewall to fix the issue? A. SSH B. HTTP C. HTTPS D. FTP Correct Answer: C
Refer to the exhibit. A developer is creating a YANG file to design data with Python. Which code must be used for the tree of the YANG file? A. pyang -f tree future-industries-tech.yang B. pyang -i tree future-industries-tech.yang C. pyang -f leaf future-industries-tech.yang D. pyang tree future-industries-tech.yang Correct Answer: C
What should be used to send real-time notifications to a third-party application when an event occurs in an SD-WAN deployment? A. loopback B. callback C. API D. webhook Correct Answer: D
A network engineer developed an application that performs configuration automation. The engineer used the MVC model for the application design. It has a web interface for users to interact, collect configuration directives for specific devices, and communicate with network devices through REST-based APIs. What is the advantage of the model component in MVC design in this scenario? A. It contains data and responds to state queries and updates. B. It keeps views and controllers updated during the execution. C. It defines main application behavior and contains functions to run. D. It renders the data for easy use by the remaining parts of the design. Correct Answer: A
What is impacted by the network bandwidth on an application? A. time taken for a data packet to travel between two endpoints B. number of data packets dropped during transmission C. consistency in the arrival of data packets between two endpoints D. rate of data transferred between two endpoints Correct Answer: A
Which port does HTTP use by default? A. 22 B. 80 C. 430 D. 443 Correct Answer: B
Which automation tool uses NEDs to abstract southbound interfaces? A. Chef B. Puppet C. Ansible D. Cisco NSO Correct Answer: D
What is the impact on an application from having a large distance between a client device and a host server? A. latency B. increased bandwidth C. loss of connectivity D. jitter Correct Answer: A
What is a feature of Cisco Modeling Labs? A. Practice administration skills for exam certi cation. B. Automate simulations that connect to external networks. C. Design and test against virtual network equipment. D. Create and manage user groups to control lab access. Correct Answer: C
A developer is working on a branch called topic that was created from the master branch to add a new feature to the product. After making a few commits on the branch, the developer wants to compare the changes between the topic and the master branches. Which two Git commands are used? (Choose two.) A. git diff topic - -cached B. git diff topic...master C. git diff topic HEAD D. git diff topic-master E. git diff topic master Correct Answer: BE
What is a capability of Cisco UCS Director? A. It is used to generate work flow reports on any hardware equipment in the network. B. It is used to create multistep work ows to automate large and repetitive tasks. C. It supports only hardware created by Cisco to ensure scalability across the network. D. It is a platform for monitoring and troubleshooting server-related issues. Correct Answer: B
Refer to the exhibit. A developer created a Python script by using the Cisco Meraki API. The solution must: · Obtain a list of HTTP servers for a network named "net1". · Print the response body if the HTTP status code is 200. · Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout. Which block of code completes the script?



Correct Answer: B Correct Answer: B
What is a benefit of using a version control system? A. tracks changes to the files B. enforces change management controls C. centralizes binary files D. prevents code from being stored locally Correct Answer: A
What is a principle of test-driven development? A. write and run tests before writing new code B. write tests after adding new blocks of code C. run tests after writing new code D. write documentation for tests Correct Answer: A
Calling a REST API returns a 404 error. What does this code represent? A. A query parameter is missing. B. The URI being requested is incorrect. C. A header is missing. D. The payload is formatted incorrectly. Correct Answer: B
A developer prepares a Python application to monitor network performance on specific applications. The developer tests the code on a test environment but requires more use cases and wants the scripts to be improved for different networks. Which resource must be used to take advantage of open-source communities and contributors for the application? A. code exchange B. sandbox C. packet tracer D. learning labs Correct Answer: A
Which Cisco network management platform should be used for integration with DevOps toolchains and third-party services in a service provider environment? A. Cisco NSO B. Cisco DNA Center C. Cisco ACI D. Cisco SD-WAN Correct Answer: A
Which unique identifier allows network traffic to be routed to a host? A. hostname B. network prefix C. IP address D. subnet mask Correct Answer: C
An engineer must investigate the problems on a web application and address them to related teams. The engineer verifies that the network farm serving the application is working properly and is accessible through the internal IP address and port. Each server has a public DNS name and public IP. While name resolutions from the outsidefinetwork to the public IP address are working properly too, the engineer discovers that some servers are not accessible from the public Internet. Which problem type must be addressed as the cause for the case? A. internal network connectivity B. blocked transport block C. proxy D. NAT Correct Answer: D
An engineer is creating an API to automatically obtain specific zones from Cisco Meraki MV cameras. The data that is provided when the API runs must represent the current analytic zones that are configured on the cameras. The API must start automatically at 6 p.m. every day and save the data on a server for further processing. Which part of the HTTP request must be configured to meet these requirements? A. request body with Status Code set to "302" B. request body with Content-Type set to "application/xml" C. request header with Content-Type set to "application/json" D. request header with Content-Encoding set to "application/xml" Correct Answer: C
A developer has created a three-tier web application for network device control and management. The application consists of multiple objects assigned for different functionalities. The architecture of the application is based on the Observer pattern. Which advantage does this pattern provide for the application design and architecture? A. Independent observers are updated automatically. B. It updates the state of dependent subjects directly. C. One observer can query the state of other subjects D. It decouples the subjects from the observers. Correct Answer: C
Which type of OWASP threat forges a malicious HTTP request into an application? A. Clickjacking B. SQL Injection C. XSS D. CSRF Correct Answer: D
What is a difference between REST and RPC API styles? A. RPC uses HTML format and REST uses JSON format. B. RPC has a single style and REST has multiple styles C. RPC uses the POST operation to update and REST uses the PUT operation to update. D. RPC is stateful in nature and REST is stateless in nature. Correct Answer: D
Which tool is able to create a network design that simulates a topology? A. Docker B. pyATS C. Cisco DevNet Sandbox D. CML Correct Answer: B
Which API has the capability to configure phone books and contacts in Cisco unified Contact Center? A. AXL B. Cisco Webex Meetings C. Cisco Finesse D. Cisco Webex Correct Answer: A
What is an advantage of the Agile software development method as compared to Waterfall? A. In Agile the development teams deliver the whole project at once, and in Waterfall the project is delivered in phases. B. In Agile the customer involvement is limited to the requirement collection phase, and in Waterfall the customer is involved in all development phases. C. In Agile every aspect of development is continually revisited, and in Waterfall the revision takes place in another project. D. In Agile each development team works independently, and in Waterfall the development team collaborate. Correct Answer: C
What are two benefits of using version control? (Choose two.) A. It enables multiple team members to work on the same project simultaneously. B. It provides a complete long-term change history of every file of an application. C. It improves code availability by distributing the data across different machines. D. It provides automation of the build and deployment process out of the box. E. It executes tests and reveals compilation errors before the code is committed. Correct Answer: AB
A system administrator works with a software development department to implement code to production. The administrator wants to review the code to be implemented and not do it automatically. The code must be ready for production and should be implemented by the administrator without additional intervention from the development team. Which DevOps concept does this scenario represent? A. continuous deployment B. continuous testing C. continuous integration D. continuous delivery Correct Answer: D
What is a difference between device-level and controller-level infrastructure management? A. Device-level management uses NETCONF, whereas controller-level management does not support NETCONF to automate the infrastructure. B. Controller-level management uses APIs to simplify the developer experience, whereas device-level management uses traditional management protocols. C. Controller-level management is more widely supported because it is standards-based, whereas device-level management is proprietary to each vendor. D. Controller-level management exposes northbound, southbound, eastbound, and westbound APIs, easing integration with other technologies, whereas device-level management does not use a controller-based API. Correct Answer: B
What are the two benefits of edge computing architecture? (Choose two.) A. run applications B. centralized implementation C. event logging D. node distribution E. complex event processing Correct Answer: DE
Refer to the exhibit. What are two results of running the RESTCONF query? (Choose two.) A. GigabitEthernet1 becomes shut down. B. Interfaces are created as containers. C. GigabitEthernet2 becomes shut down. D. Descriptions for two interfaces are applied. E. The module left-interfaces:interfaces is created. Correct Answer: DE
Refer to the exhibit. A network engineer must automate a work flow to get device volume data from Endpoint xAPI-enabled devices. The engineer prepares a Python script to send the request by adding an access token and device I A. However, the request receives a status code of 401. Which action solves the problem? B. Access token must be changed with a valid one. C. Network connectivity between client and API must be fixed. D. Internal server problems that relate to code must be fixed. E. API endpoint must be restarted to serve again. Correct Answer: A
Which benefit does CI/CD provide to the infrastructure? A. supports connectivity between network resources and external platforms B. supports the integration of network devices with external databases C. provides version control during application development D. enables frequent and reliable code deployments Correct Answer: D
What is a characteristic of Agile software development compared to the Waterfall method? A. Agile method values comprehensive documentation whereas Waterfall focuses on working software. B. Agile delivers at the end of a linear process whereas in Waterfall each phase depends on the deliverables of the previous phase. C. In Agile, development iterations last from one to four weeks whereas the Waterfall method does not utilize iterations. D. In Agile, code is deployed to production immediately whereas in Waterfall deployment is processed gradually on each cycle. Correct Answer: C
A developer is working on a new feature and finds an old piece of code that must be discussed. The developer wants to find the original coders for the code to discuss the issue. Which Git command annotates the listing of the source file with the author that created or last edited a line? A. cat lename | git diff B. git log C. git blame lename D. git re og Correct Answer: C
Refer to the exhibit. A Cisco Meraki network was recently installed. Which TCP port is used to gain access to the Meraki dashboard to complete the configuration? A. 22 B. 23 C. 443 D. 8080 Correct Answer: C
A developer must add an idempotent task to an Ansible playbook that configures a Cisco IOS device. HTTP traffic must be permitted from 192.168.1.1 to 192.168.1.5 host machine. Which code snippet must be used?


Correct Answer: C Correct Answer: C
Refer to the exhibit. An engineer is creating a Docker file for an application to run on a container. Application is a web application build on the Python Flask framework. Which port of the Docker file provides desired reachability to the application from the outside of the container? A. RUN pip3 install Flask B. MAINTAINER User One (userone@domain.com) C. EXPOSE 80 D. COPY ./app Correct Answer: C
How does a synchronous API request differ from an asynchronous API request? A. clients are able to access the results immediately B. clients subscribe to a webhook for operation results C. clients poll for the status of the execution of operations D. clients receive responses with a task ID for further processing Correct Answer: A
Refer to the exhibit. What is the result of running the Docker file? A. Copy the directory /app from the ubuntu:18.04 image, build it with make, and execute the application with the Python command. B. Copy the directory app from the current directory of the Docker client, execute the application with make, and after it runs, execute an additional application. C. Copy the directory app from the current directory of the Docker client, build it with make, and execute the application with the Python command. D. Copy the /app directory from the ubuntu:18.04 image, execute the application with make, and after it runs, execute an additional application. Correct Answer: C
A developer is working on an existing feature that needs enhancing. The primary production branch for the application is `prim4a3b8c6d80374' and the branch for working on the feature is `feat145678909'. The developer needs to create a clone of the single branch used for the feature that only has commits included in the current line of history. Which Git command must be used? A. git clone [url] - -feat145678909 - -single-branch B. git clone [url] - -branch feat145678909 - -single C. git clone [url] - -single-branch feat145678909 D. git clone [url] - -branch feat145678909 - -single-branch Correct Answer: D
Why should a code review process be used? A. It enables various software design implementations. B. It enables a consistent software design. C. It ensures that members of a team work in isolation. D. It ensures that whole software is secure. Correct Answer: B
An engineer is responsible for several thousand network devices across many campus environments that are all connected to a common controller. Which action updates all devices with new security settings in this network? A. Get a list of all devices from the controller and use a CLI to change the settings on individual devices. B. Track a list of all devices on a spreadsheet and use a CLI to change the settings on individual devices. C. Get a list of all devices from the controller and use RESTCONF to set a YANG model on the devices. D. Track a list of all devices on a spreadsheet and use RESTCONF to set a YANG model on the devices. Correct Answer: C
Which security platform rapidly analyzes files and suspicious behavior across an environment? A. Cisco Threat Grid B. Cisco Firepower C. Cisco ISE D. Cisco ASA Correct Answer: A
A developer prepared the Docker file and already built a web application container with the image name: "myWebApp". Requests made to the server public IP address on port 8080 must be redirected to port 80 on the container. The developer wants to start the container and access the Bash shell while the application serves the requests. Which command is used?


Correct Answer: A Correct Answer: A
Which network device forwards packets between networks? A. router B. load balancer C. firewall D. switch Correct Answer: D
Which Python data type resembles JSON data structures? A. list B. dictionary C. string D. tuple Correct Answer: B
What are two advantages of model-driven programmability as compared to traditional network management? (Choose two.) A. standardized transport protocol B. better performance C. better visibility and control D. device abstraction E. access to more routing features Correct Answer: CD
Which cloud-based security solution is focused on DNS resolution? A. Cisco AMP B. Cisco Meraki Dashboard C. Cisco DNA Center D. Cisco Umbrella Correct Answer: D
Refer to the exhibit. An engineer needs to construct a Bash command to create a new backup folder and then copy all files from the current folder to the backup folder. Which code snippet must be placed on the blank in the code?



Correct Answer: B Correct Answer: B
The API documentation has this requirement for a REST API request: "For methods that accept request parameters, the platform accepts either application/json or application/x-www-form-urlencoded content types and currently only supports returning data in application/json format". Which field returns content in the required format?


Correct Answer: B Correct Answer: B
A developer checks the performance of a web application. The application is in the local data center and used a REST-based API. Based on the API logs, it is discovered that many users abandon API requests. Also, the response is taking too long to get back. What is the reason for this issue? A. Token-based authentication is disabled. B. Pagination is not implemented. C. Rate limiting is not implemented. D. Token-based authentication is enabled. Correct Answer: C
Refer to the exhibit. A developer creates a Python script to query a REST API by using an HTTP GET request. The remote server will authorize the request only if it includes HTTP Basic Auth parameters. The username is admin and the password is devnet123. Which line of codefineeds to be placed on the snippet where the code is missing?



Correct Answer: A Correct Answer: A
Refer to the exhibit. An engineer is comparing two files by using the unified diff format. What is determined by the content in the le2.py file? A. Line 93 of file.py is `DEVICE-STATS'. B. Line 92 of le2.py is `DEVICE-STATS'. C. Line 16 of le2.py is auth=HTTPBasicAuth(USERNAME, PASSWORD). D. Line 17 of le2.py is auth = HTTPBasicAuth(USERNAME, PASSWORD). Correct Answer: D
What is the reason for an HTTP 404 code returned from a REST API request? A. The requested URL exists, but the HTTP method is not applicable. B. The requested resource is not found. C. The request was missing or had an invalid authentication token. D. The request was successful, but nothing is in the response body. Correct Answer: B
An existing application is accessible from an external IP address. Which device or service must be configured to make the application accessible through a URL by using a domain name? A. reverse proxy B. DNS C. firewall D. load balancer Correct Answer: B
Refer to the exhibit. Which device should be used to interconnect the hosts? A. load balancer B. VPN gateway C. Layer 2 switch D. Layer 3 switch Correct Answer: C
What is the main purpose of a code review? A. to identify and review errors with the team B. to detect logical errors C. to ensure that all code is checked in simultaneously D. to provide the technical lead visibility into all code Correct Answer: A
What are two benefits of organizing code into classes, methods, functions, and modules? (Choose two.) A. improves readability B. improves reusability C. improves parallelism D. improves performance E. decreases complexity Correct Answer: AB
Refer to the exhibit. Which code should be added at the snippet to perform a unit test?



Correct Answer: D Correct Answer: D
A development team must find a cloud deployment model to scale its new product to external and internal users. The team is small and the data is massive. The team wants high exibility and higher security. Which application deployment model should the team use? A. hybrid cloud B. edge C. public cloud D. private cloud Correct Answer: A
An application developer deploys several applications on the same server. The environment runs on a single operating system and allows the developer to bind dependencies with the application code. Which environment has the code been developed in? A. bare metal server B. virtual machine C. container D. Linux server Correct Answer: C
How do JSON and XML compare? A. The syntax of JSON contains tags, elements, and attributes whereas XML objects are collections of key-value pairs. B. JSON objects are an ordered set of element attributes whereas XML arrays are an unordered set of key-value pairs. C. The syntax of XML contains tags, elements, and attributes whereas JSON objects are collections of key-value pairs. D. JSON arrays are an unordered set of key-value pairs whereas XML objects are an ordered set of element attributes. Correct Answer: C
Which Cisco compute management platform is a premises based solution that Automates and Orchestrates Cisco and non-Cisco infrastructure? A. UCS Manager B. Cisco Integrated Management Controller C. UCS Director D. Cisco Intersight Correct Answer: C
When changes are made to the same file across two branches, which git status is shown when the branches are combined? A. unmerged B. uncommitted C. conflict D. branched Correct Answer: C
What is a characteristic of a VLAN? A. associated with IP address subnetworks B. consist of physically segmented LANs C. users access data from different VLANs D. associated with MAC address subnetworks Correct Answer: D
Package updates from a local server are failing to download. The same updates work when a much slower external repository is used. The server has the configuration: · hostname: devbox111012120 · IP: 192.168.1.51 · Mask: 255.255.255.0 Why are local updates failing? A. The Internet is down at the moment, which causes the local server to not be able to respond. B. The Internet connection is too slow. C. The server is running out of disk space. D. The update utility is trying to use a proxy to access the internal resource. Correct Answer: D
Which HTTP response code is returned from a successful REST API call to create a new resource? A. 201 B. 204 C. 302 D. 429 Correct Answer: A
Refer to the exhibit. A software engineer needs to collect data about devices that are registered in Cisco DNA Center using the API. Before collecting the data, the engineer must obtain a token and authenticate with the API. To automate the procedure, a Python script is used. Which code snippet must be placed onto the blank in the code? A. get(uri,headers = headers,data={}, verify-True) B. post(uri,headers=headers,data={}, verify=False) C. get(uri,headers= headers,data={}, verify=False) D. post(uri,headers=headers,data={"Basic"}, verify=False) Correct Answer: A
A developer needs to create an application with these requirements: · decouples from the underlying infrastructure · runs application on any cloud or on-premises provider Which deployment type must be used for this application? A. bare metal B. hyperconverged C. container D. virtual machine Correct Answer: C
Refer to the exhibit. An engineer develops an Ansible playbook to perform tasks that automate the provisioning of a server. What occurs on the server after the playbook is run? A. The Vim, Git, and Pip packages are removed. B. The Vim, Git, and Pip packages are backed up. C. Only the Vim package is installed as the most recent package. D. The most relevant versions of the Vim, Git, and Pip packages are installed. Correct Answer: D
Which network component enables communication between broadcast domains? A. router B. firewall C. switch D. load balancer Correct Answer: A
What type of efficiency is achieved by using model-driven programmability for infrastructure automation? A. Apply configuration changes across devices using the same model. B. Implement infrastructure components using a single platform. C. Collect logging information using a single model across the infrastructure. D. configure the infrastructure using a multi-interface API. Correct Answer: A
A developer prepares an API to be used by administrators. API requires username and password to be verified for validated access to data, however username-password combination of users must not be sent to the API service itself. Authentication and authorization will be provided over the same mechanism. Which authentication mechanism must be used by the API service? A. OAuth Authentication B. Digest Access Authentication C. Basic Authentication D. API Key Authentication Correct Answer: A
A developer creates a REST API that runs on a load balancer for clients to query information about stocks. The data in the back-end database is updated every 15 minutes, but clients are polling the API every 2 minutes. The developer needs to reduce the load on the database without making changes to the client side. Which constraint must the engineer address? A. The load balancer is not configured to use memcached as the primary back end. B. Use of Cache-Control headers and max-age validation is not enforced. C. Request throttling on the load balancer database is not enabled. D. Dynamic IP deny listing, which allows requests every 15 minutes, is not configured. Correct Answer: B
What are two advantages of the MVC design pattern? (Choose two.) A. It represents the visualization of data contained with a model. B. It allows filtering of a set of objects using different criteria. C. It controls the data flow into a model object and updates a view whenever data changes. D. It separates low-level data accessing operations from high-level business services. E. It builds a final object through a step-by-step approach. Correct Answer: CD
Refer to the exhibit. A security team observes an attack that originates from a Cisco Meraki device. To mitigate the attack, the team requests that the engineering team remove the device from the network. The security team also requests information about the device, such as its name and location. Which tool must the engineering team use to meet the requirements by using tasks? A. cURL B. Postman C. Ansible D. Puppet Correct Answer: C
Which response code family is returned when further action must be taken to complete the request? A. 2xx B. 3xx C. 4xx D. 5xx Correct Answer: B
Which Cisco compute management platform enables the management of Cisco UCS, Cisco HyperFlex, Pure Storage, and Cisco Network Insights from a single platform? A. Cisco UCS Manager B. Cisco Intersight C. Cisco HyperFlex D. Cisco UCS Director Correct Answer: B
A customer is building a new DevOps business. The customer plans to deploy a modern version control system that supports multiple branches. Then the customer will aim to integrate into a Cl/CD pipeline for automated provisioning and agile development. What should the customer use first for the version control system? A. Cisco ACI B. Jenkins C. GitHub D. Ansible Correct Answer: C
Refer to the exhibit. A development team is creating a Python application. After several days of work, a developer notices several pycache folders and creates a Bash script to clean up the folders. What being automated by the Bash script? A. Recursively delete all the __pycache__ folders. B. Find all the empty __pycache__ folders and delete them. C. Delete all the files in the __pycache__ folders. D. Find all the files named PWD and delete them. Correct Answer: A
Which type of OWASP threat uses malicious scripts that are injected into otherwise benign and trusted websites? A. brute force B. man-in-the-middle C. XSS D. SQL injection Correct Answer: C
Refer to the exhibit. The sequence diagram shows a RESTful API call. Which step and response will represent the behavior of the REST API call to be synchronous? A. POST/discovery/ when there is a slot available and get the response from the POST call with the discovery details. B. GET/discovery/ when the discovery is nished and get the response from the GET call with the discovery requirements. C. POST/discovery?discoveryid= when the discovery is created and get the response from the POST call with the discovery details. D. PUT/discovery/ when the discovery is created and get the response of the discovery when it is updated. Correct Answer: C
How do the processes used by the Agile methodology compare with the processes used by the Lean methodology? A. Agile concentrates on optimizing the development process, and Lean concentrates on optimizing the production process. B. Agile and Lean concentrate on optimizing the production process. C. Agile and Lean concentrate on optimizing the development process. D. Agile concentrates on optimizing the production process, and Lean concentrates on optimizing the development process. Correct Answer: A
A developer is working on a new feature named `feat434370483' in a branch. A file named `devasc321345515.jpg' has accidentally been staged. The developer needs to remove this so that the commit is performed and branches are merged. Which Git command must be used to unstage the file? A. get delete HEAD devasc321345515.jpg B. get reset HEAD devasc321345515.jpg C. git remove HEAD devasc321345515.jpg D. git revert HEAD devasc321345515.jpg Correct Answer: B
What are two benefits of edge architecture? (Choose two.) A. device authentication B. secure access C. service deployment D. offline support E. data management Correct Answer: BE
Which plane is used to enable routing on a network-connected device? A. management B. data C. control D. forwarding Correct Answer: C
What is the IANA-assigned TCP port for NETCONF over SSH? A. 21 B. 22 C. 830 D. 8443 Correct Answer: C
What is a feature of a MAC address? A. It consists of 38 bits. B. It consists of 12 hexadecimal numbers. C. It consists of 6 hexadecimal numbers. D. It consists of 24 bits. Correct Answer: C
Which TCP port is used by default for HTTPS? A. 53 B. 80 C. 143 D. 443 Correct Answer: D
What is a capability of the AXL API? A. It adds a user to a collaboration space to share information and files. B. It allows a meeting to be created with users that do not belong to same organization. C. It collects information about system, cluster, and database settings. D. It executes SQL commands in Cisco unified Communications Manager. Correct Answer: D
Refer to the exhibit. A developer has created an XML-based configuration model for a Cisco switch that is going to configure the device using NETCON A. From which configuration is the Interface Ethernet 0/0 deleted when this script is executed? B. candidate C. startup D. current E. base Correct Answer: D
Which CI/CD component allows for the storing of code packages and enables the testing of the same code that is running on the live system? A. Artifactory B. Jira C. ITSM D. Git Correct Answer: A
A development team needs to containerize an application named 'custapp4o3p2r6d3s6w7x6t9'. A Docker file has been created and now the docker build command must be run using the current folder to find the Docker file, build the image and create a local repository named 'custapp4d5c-repo' that points to that image. Which command must be used? A. docker build custapp4d5c-repo Docker file . B. docker build -t acustapp4d5c-repo Docker file.txt C. docker build custapp4d5c-repo -f Docker file.txt D. docker build -t custapp4d5c-repo -f Docker file . Correct Answer: D
A web app must be accessible from computers and mobile devices. It must maintain the same data structure on both types of devices. What is the advantage of using the MVC design pattern for this app? A. to asynchronously update the graphical interface B. to define different algorithms for data manipulation C. to separate the logic of the graphic interface of the different devices D. to have only one instance of the objects that contain the data Correct Answer: A
What is the purpose of a router in a network? A. to provide wireless connectivity to a LAN B. to filter harmful incoming traffic on a network C. to connect multiple networks D. to implement network high availability Correct Answer: C
Refer to the exhibit. Which type of YANG object is "interfaces"? A. subitem B. container C. item D. node Correct Answer: B
Which protocol is associated with the management plane on a network device? A. ARP B. ICMP C. BGP D. SSH Correct Answer: D
Refer to the exhibit. What is the result of the API sequence diagram? A. export of the authenticated user on the device B. text file that contains the authentication token C. export of the Cisco IOS XE configuration file D. text file that contains the string IOS-XE 16.6.3 Correct Answer: D
While delivering a product, a team spends a lot of time installing dependencies to maintain the development and test environments. Both environments must be identical. Which action improves the delivery? A. Use an Ansible playbook to install the dependencies. B. Pack everything into the released product. C. Use containers to keep the environment consistent. D. Pre-install the product into a virtual machine. Correct Answer: C
Which process does a developer use to import a string and convert the file into a Python data structure? A. parsing B. exploding C. serializing D. translating Correct Answer: A
Which two commands create a new branch in a Git repository? (Choose two.) A. git branch B. git checkout C. git checkout D. git branch E. git checkout -b Correct Answer: AE
Refer to the exhibit. An astronomer creates a Python script named makeexoplanetapi.py to import external data for comparison with the department data. The astronomer changes the script after a discussion with another astronomer. Which code snippet shows a unified diff of the script?



A. B Correct Answer:
A company plans to develop an application by using Cisco APIs. The application must use code repositories approved by Cisco. The development team wants to make use of community-supported, open-source code. Which resource should be used? A. Cisco DevNet Code Exchange B. Cisco TAC C. Cisco DevNet Sandbox D. Cisco DevNet Learning Labs Correct Answer: A
Which tool simulates a network that runs Cisco equipment? A. Cisco Prime Infrastructure B. VMware C. Docker D. CML Correct Answer: D
What is a function of an application load balancer? A. automatic distribution of TCP traffic B. automatic distribution of HTTP and HTTPS traffic C. manual distribution of TCP traffic D. manual distribution of HTTP and HTTPS traffic Correct Answer: B
Refer to the exhibit. An engineer must create a local user on Cisco ASA and prepares a script to send the request through ASA REST API. The engineer gets a response of 400 Bad Request. Which HTTP request produces a response code of 201?

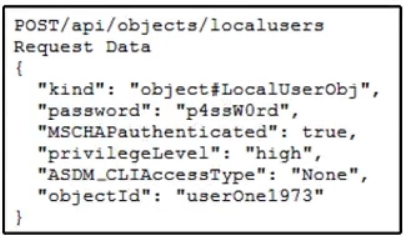

Correct Answer: A Correct Answer: A
What is a component of the first stage of an application development CI/CD pipeline? A. triggering of the automated testing phase B. commitment and pushing of code into a version control system C. triggering of the automated build phase D. developer writing the initial lines of code Correct Answer: B
What must be created on a network to enable devices in different network segments to communicate as if attached to the same wire? A. VLAN B. SAID C. VTP D. MTU Correct Answer: A
When a developer sends an HTTP request to an API, which two elements are expected in an HTTP response? (Choose two.) A. headers B. GET request C. POST request D. scripts E. status code Correct Answer: AE
What is the benefit of organizing data into functions? A. supports using same variable in different modules B. supports altering the state of an object C. organize code in a reusable way D. stores data values of different types Correct Answer: C
Which capability is used by Ansible to run a set of tasks when a property is changed? A. handlers B. playbooks C. roles D. tasks Correct Answer: B
Refer to the exhibit. The YANG module devnet-users shows a data model for user accounts. Which code snippet shows the XML representation of an instantiation of the YANG data model?



Correct Answer: D Correct Answer: D
Which API is used to change the configuration of a device group that contains Cisco Catalyst 9000 Series Switches? A. xAPI B. Cisco Finesse C. JTAPI D. Cisco IOS XE Correct Answer: D
What is a benefit of using model-driven programmability on Cisco devices? A. deeper monitoring B. better logging C. automated configuration D. increased security Correct Answer: C
Refer to the exhibit. A developer got this output during the development of an application. Which action produces this output? A. execution of a Python script with numpy library B. enhancement to Python numpy library C. upload of a script to a git repository D. file comparison within the unified diff format Correct Answer: D
A REST API service requires basic authentication. A user's credentials are "ned/33662255" and the Base64 encoding of the credentials is "a2lsbGE6NDU4ODI5". Which requirement must be met for a request to be authenticated? A. The header must include: Authorization: Basic a2lsbGE6NDU4ODI5 B. The payload must include: Authorization: Basic a2lsbGE6NDU4ODI5 C. The header must include: username: ned, password: 33662255 D. The payload must include: username: ned, password: 33662255 Correct Answer: B
What is a concept of test-driven development? A. Functions that validate the behavior of the product from the end user's perspective are written before any code is written. B. Business decision makers write tests to validate the product from the end user's perspective while the developer writes the code. C. One developer writes tests to validate the functionality of the code while another developer writes the code. D. Tests that validate the functionality of the code are written before any code is written. Correct Answer: D
Within a Bash shell, which command adds the current directory to the PATH without overwriting the current PATH for this shell and any subshells that are spawned from the current shell?
A. export $PATH=PATH:$(pwd)
B. set PATH=$PATH:${pwd}
C. export PATH=$PATH:$(pwc1)
D. set PATH=PATH+$(pwd)
Correct Answer: C
Refer to the exhibit. An administrator uses RESTCONF to retrieve the interface configuration of Gi1/0/1. Which URL path retrieves ltered information only for Gi1/0/1?



Correct Answer: D Correct Answer: D
Which Cisco network management platform facilitates data center automation across private or public clouds? A. Meraki Systems Manager B. Cisco DNA Center C. SD-WAN D. ACI Anywhere Correct Answer: D
Refer to the exhibit. A developer is trying to collect data over RESTCONF API and prepares the request. The developer wants to get data in JSON format and with the IOS-XE-native model, but the request fails. Which HTTP part causes the failure? A. application value B. invalid URL C. missing URI header path D. incorrect request type Correct Answer: A
A development team is using a version control system that has a centralized work flow. Which feature of the version control system ensures the integrity of the central repository? A. central common code versioning backup B. built-in conflict resolution mechanism C. distributed nature of the version control system architecture D. tracked code changes of the developers Correct Answer: D
Which two factors reduce the experience of an application? (Choose two.) A. source location B. traffic class C. packet loss D. network latency E. usage Correct Answer: CD
Which protocol runs over TCP port 830? A. NETCONF B. Telnet C. RESTCONF D. HTTP Correct Answer: A
What is used in JSON to represent a Python tuple? A. collection B. object C. array D. dict Correct Answer: B
Which command reverses the last commit without changing the index file or the working tree position? A. git revert HEAD B. git reset --hard HEAD~3 C. git reset --soft HEAD^ D. git revert Correct Answer: C
A file in a local Git repository has been updated and issued the git add . command. The git diff command has been run to compare the changes to the previous commit, but nothing shows. Which action identifies the problem? A. Run the git add . command again in the correct subdirectory to ensure changes added to the staging area. B. Run the git commit command before the differences are compared to receive the end state of the code. C. Run the git status command to see the differences between current and previous code review stages. D. Run the git diff --staged command to compare the code added to the staging area. Correct Answer: D
Which solution reduces costs from MPLS, improves application performance, and simpli es operations? A. Cisco NSO B. Cisco SD-WAN C. Cisco ACI D. Cisco DNA Center Correct Answer: B
A developer has experienced security issues with a previously developed application. The API offered by that application is open and without any constraints. During a recent attack, the application was overloaded with API requests. To address this issue, an API constraint is implemented to protect the application from future attacks or any sudden throttling. Which API constraint must the application developer implement in this situation? A. pagination B. rate limiting C. filtering D. payload limiting Correct Answer: B
A developer must test the performance and reliability of an application. After functional and load tests are run, the application crashes due to traffic spikes from users. Which type of API constraint must be implemented to maintain reliability? A. rate limiting B. pagination C. payload limits D. filtering Correct Answer: A
A developer is working on a new feature in a branch named 'newfeat123456789' and the current working primary branch is named 'prim987654321'. The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must be used? A. git merge --no-ff newfeat123456789 B. git commit --no-ff newfeat123456789 C. git add --commit-ff newfeat123456789 D. git reset --commit-ff newfeat123456789 Correct Answer: A
A customer's cloud services must: · Migrate services to another data center on demand. · Save the operational state of the machine on demand. · Support Windows and Linux GUIs. · Maximize hardware utilization. Which type of deployment meets these requirements? A. bare metal B. container C. virtual machine D. Kubernetes Correct Answer: C
How does edge computing analyze sensitive data in the context of privacy control? A. locally instead of sending the data to the cloud for analysis B. locally or on the cloud depending on the configuration C. all at once by sending the data to the cloud D. locally on each node, and then sends the data to the cloud Correct Answer: A
Which Python function is used to parse a string that contains JSON data into a Python dictionary? A. json.dumps() B. json.to_json() C. json.parse() D. json.loads() Correct Answer: D
Refer to the exhibit. An engineer prepares a script to automate work flow by using Cisco DNA Center APIs to display: · total count of devices · list of the network devices · information of one device with a hostname filter What is displayed in the final step after the Python script is executed? A. information about a device of type C9500-40x. B. ltered results by the hostname and the platformld C9500-40X C. information about the test devices D. list of devices with platformId C9500-40x Correct Answer: B
A team of developers is responsible for a network orchestration application in the company. The responsibilities also include: · developing and improving the application in a continuous manner · deployment of the application and management of CI/CD frameworks · monitoring the usage and problems and managing the performance improvements Which principle best describes this DevOps practice? A. responsible for IT operations B. automation of processes C. end-to-end responsibility D. quality assurance checks Correct Answer: C
Refer to the exhibit. An administrator attempts to perform a GET operation by using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram in the exhibit illustrates the HTTP messages observed. Which change to the API request resolves the issue? A. Remove the -H 'Accept: application/yang-data+json' header. B. Replace -u cisco:cisco parameter with -u `cisco:cisco'. C. Change the request method from -X `GET' to -X `POST'. D. Add the -H `Content-Type: application/yang-data+json' header. Correct Answer: B
A new application is being developed that requires the ability to be copied and moved from one location to another. The existing infrastructure is already heavily utilized, so the new application must have a low resource footprint. The application includes a small PostgreSQL database component. Which application deployment type meets the requirements? A. Python virtual environment B. bare metal C. virtual machine D. container Correct Answer: D
Refer to the exhibit. The internal client cannot access the app server, but access still works for clients on the Internet. Which two actions resolve the issue? (Choose two.) A. Move port Gi0/0/2 to VLAN 20. B. Add a host route on the server to the client. C. Change the subnet length on the client to 16. D. Change the subnet length on the server to 24. E. Add a host route on the client to the server. Correct Answer: BE
What is a principle of Infrastructure as Code? A. It requires manual resource provisioning. B. It encourages overlaps in services. C. It encourages repeatable processes. D. It requires the use of large components. Correct Answer: C
Refer to the exhibit. A network engineer must improve the fabric discovery process in a data center. The engineer wants to check current ACI scripts in the myproject repository and clone them to a folder named aci. The engineer will optimize the scripts from the new folder. Which command performs this task on the Git repository?



Correct Answer: D Correct Answer: D
A developer improves the code repository to clean a bug on the custom network monitoring application. The developer adds the changes to the staging area and then commits on the local branch. Which command pushes commits that are made on a local branch to the remote repository? A. push origin master B. git push all C. push all D. git push origin master Correct Answer: D
Refer to the exhibit. An engineer must add new users and set privileges for executing a few Python scripts. The engineer prepares a Bash script to automate this task. The script adds a user and a group from the command-line arguments, creates a directory, and copies the Python scripts to it. The script then changes to the directory and lists the scripts. Based on the script work flow, which process is being automated within the loop by using the list of Python scripts? A. assigning execution privileges to the owner, setting the user and group owner to the scripts that were initially created, and storing the script names in a file. B. creating a file with the content of all the files, assigning execution permissions to each script, and then changing ownership to the initially created user and group. C. removing the files that are not Python, listing the Python files, and assigning execution privileges to the initially created user and group. D. assigning execution privileges to everyone and changing the ownership to the initially created user and group. Correct Answer: B
Which IP service is used to monitor the performance of network devices? A. SNMP B. DHCP C. DNS D. NTP Correct Answer: A
Which IP service synchronizes the time across devices? A. DNS B. NTP C. SNMP D. NAT Correct Answer: B
Users cannot access a webserver and after the traffic is captured, the capture tool snows an ICMP packet that reports "time exceeded in-transit". What is the cause of this webserver access issue? A. The large distance between the server and the users means that the packets require too much time to reach the destination. B. A router along the path is misrouting the packets in a wrong direction. C. A router along the path has the wrong time. D. The server is overloaded and the connection was not able to be processed in time. Correct Answer: B
Refer to the exhibit. An engineer is comparing two files by using the unified diff format. Which cade snippet belongs to the new.py file?



Correct Answer: A Correct Answer: A
Refer to the exhibit. A network engineer executes the bash script shown. Which two things are achieved by running the script? (Choose two.) A. A directory called PRODUCTION is created. B. The engineer changes to the parent directory. C. A YAML file is created. D. A YAML file is removed. E. A directory called state.yml is created. Correct Answer: AC
Refer to the exhibit. Which code snippet represents the sequence.



A. Correct Answer: C
A developer attempts to refactor and improve the application code. It is noticed that the code contains several pieces of key information that could be a security threat if this code is accessible by those who are not authorized to this data. Which approach addresses the security concerns noticed by the developer? A. Host the application code on a machine located in a secure data center. B. Utilize environment variables for username and password details. C. Rely on the security teams' goodwill to not give access to those who do not need it. D. Move the hardware that the application is deployed on to a secure location. Correct Answer: B
Which tool provides a testing environment to run tests on network devices and perform network automation scenarios? A. Visual Studio Code B. Cisco VIRL C. pyATS D. Cisco Packet Tracer Correct Answer: B
A developer writes an application that re nes data in temporary secure file storage hosted on the public cloud. Data will be deleted after processing and does not contain any private information. What is the advantage that a public cloud deployment provides to the developer? A. high security with encryption B. ease in infrastructure management C. flexible development D. bespoke services Correct Answer: B
Refer to the exhibit. A network engineer must copy the "config.txt" file from directory TEST to directory PRO A. The copied file must also be renamed into "current.txt". Which command must be used to accomplish these tasks? B. cp ./PROD/current.txt ./TEST/config.txt C. cp ./TESTi/current.txt ./PROD/config.txt D. cp ./PROD/config.txt ./TEST/current.txt E. cp ./TEST/config.txt ./PROD/current.txt Correct Answer: D
What is a benefit of using model-driven programmability for infrastructure automation? A. connected user tracking B. infrastructure resource optimization C. multiple device control protocols D. device performance monitoring Correct Answer: C
What is the function of an Ethernet switch in a networking environment? A. to switch a frame from one port to another port based on IP address B. to switch a frame from one port to another port based on MAC address C. to provide IP addressing to connected hosts D. to block unwanted traffic Correct Answer: B
Refer to the exhibit. An engineer runs a network that consists of Cisco Nexus devices. The network is distributed between data centers in different locations. The switches are configured using standalone connections and a single point of failure. Which process is being automated by the Ansible playbook? A. enabling HSRP on the nxos_rtr inventory host B. enabling HSRP on the rtr-1a inventory host C. executing HSRP configuration from the Ansible controller node D. executing HSRP configuration from the srv-1a inventory host Correct Answer: B
Refer to the exhibit. A developer must use a token to collect data from Cisco DNA Center API and prepares a Python script to send requests. Which line of codefineeds to be placed on the snippet where the code is missing to obtain a token from the Cisco DNA Center API? A. token=BasicAuth(`user',`password')) B. auth=BasicAuth(`user',`password')) C. auth=HTTPBasicAuth(user,password)) D. token=HTTPBasicAuth(user,password)) Correct Answer: C
To which stage of development do Infrastructure as Code principles relate? A. manual configuration B. service provisioning C. physical deployment D. requirement collection Correct Answer: B
Refer to the exhibit. An engineer must authorize a REST API call. The API password is "Cisco123!". Which Bash command must be placed in the code to authorize the call? A. mkdir API_PASSWORD=Cisco123! B. set API_PASSWORD=Cisco123! C. cp API_PASSWORD=Cisco123! D. export API_PASSWORD=Cisco123! Correct Answer: D
Which function does a router provide to a network? A. broadcast domain segmentation B. unique host on a Layer 3 network C. unique hardware address for every node on a LAN D. broadcast domain extension Correct Answer: B
An engineer must configure Cisco Nexus devices and wants to automate this work flow. The engineer will use an Ansible playbook to configure devices through Cisco NX REST API. Before the code is run, which resource must be used to verify that the REST API requests work as expected? A. Cisco Open NX-OS B. Cisco NX-OS SDK C. Cisco Learning Labs D. Cisco Code Exchange for Nexus Correct Answer: C
What is a function of the default gateway in a network? A. to drop traffic that is destined to the default gateway B. to forward traffic to different subnets C. to forward traffic to the same subnet D. to drop traffic that is not destined to the default gateway Correct Answer: B
What is a rehose webhook? A. It collects data from third-party cloud APIs for custom applications. B. It enables an application to receive real-time data from Cisco Webex. C. It enables data to flow from the Cisco Webex API to a user's application. D. It sends a notification of any event for commonly used resources. Correct Answer: D
Which port does HTTPS use by default? A. 433 B. 443 C. 803 D. 883 Correct Answer: B
Which TCP port is used to connect to a network device by using Telnet? A. 23 B. 69 C. 400 D. 830 Correct Answer: A
A developer is developing a web application that uses username and password to authenticate to the next service. The user credentials must be available at any time in the application. The developer must choose and implement a secure method of storing the authentication credentials that are used in the automation code. Which password handling method must be used to minimize the security risk? A. Store the username and password in a separate configuration file. B. Store the username and password in a vault. C. Store the passwords in a dictionary. D. Store the username and password in code. Correct Answer: B
A developer creates a program in which an object maintains a list of classes based on the observer pattern. The classes are dependent on the object. Whenever the state of the object changes, it noti es the dependent classes directly through callbacks. Which advantage of the observer pattern offers minimum dependencies and maximum exibility between dependent objects or classes? A. tight coupling B. cohesion C. mediation D. loose coupling Correct Answer: D
What is a feature of XML compared to other data formats? A. It uses tags to define the structure. B. It uses parenthesis for key-value pairs. C. It uses indentation to define the structure. D. It uses namespaces for list representation. Correct Answer: A
What is a capability of Ansible playbooks? A. They execute scheduled tasks regularly. B. They define the state for a device configuration. C. They collect SNMP logs from networking devices. D. They utilize the target device agent to execute. Correct Answer: A
What is the purpose of running tests before writing code in test-driven development? A. to find unexpected failures in the tests B. to demonstrate that the tests fail for expected reasons C. to ensure that the tests pass D. to provide proof of the work carried out Correct Answer: D
Which HTTP method is used by webhooks and noti es a listener about an event change? A. PUT B. POST C. PATCH D. GET Correct Answer: B
A developer completed the creation of a script using Git. Before delivering it to the customer, the developer wants to be sure about all untracked files, without losing any information. Which command gathers this information? A. git clean n B. git rm f C. git clean r D. git rm * Correct Answer: A
A company deploys an application via containers in its local data center. As soon as the application goes into production, it starts to crash at specific hours of the day. After investigation, it is concluded that the crashes are due to too many users accessing the application simultaneously. The spikes must be addressed and allow for future growth without discarding the investment already made. Which deployment model must be used? A. hybrid cloud B. edge C. private cloud D. public cloud Correct Answer: A
Refer to the exhibit. Which action does the script perform? A. It queries user credentials from Cisco IOS XE devices. B. It retrieves device identification from Cisco DNA Center. C. It exports SSID information from Meraki dashboard. D. It collects group information from ACI. Correct Answer: D
What is the purpose of grouping devices in a VLAN? A. Devices communicate as if they are connected on the same wire. B. Multicast network traffic is limited to the VLAN connected devices. C. Unicast messages are limited to the clients connected on the same VLAN. D. Network traffic is load balanced between the devices connected to the VLAN. Correct Answer: B
Refer to the exhibit. The YAML shown contains an object "param0" that is equal to "Work ow1", a second object "param1" that contains an object called "list" which contains an array of two objects, "name" (equal to "VLAN_ID") and "value" (equal to a text value "198"), and nally a third object "param2" that is equal to "0". What is the equivalent message in JSON data format?



Correct Answer: D Correct Answer: D
An engineer prepares a set of Python scripts to interact with network devices. To avoid network performance issues, the engineer wants to run them in a test environment. Which resource must be used to monitor the live execution of code in an always-available environment? A. packet tracer B. learning labs C. sandbox D. code exchange Correct Answer: C
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method? A. application/yaml-data+json B. application/yang-data+json C. application/xml-data+json D. application/json-data+xml Correct Answer: D
Refer to the exhibit. A developer is part of a team that is working on an open-source project in which source code is hosted in a public GitHub repository. While the application was built, security concerns were addressed by encrypting the credentials on the server. After a few months, the developer realized that a hacker managed to gain access to the account. The exhibit contains part of the source code for the login process. Why was the attacker able to access the developer's account? A. The encoded credentials were available in the source code. B. The application was not encrypting the communication with the server. C. The credentials were encrypted in the source code. D. An SSL certificate was used instead of the TLS protocol to authenticate. Correct Answer: A
Which technology is responsible for matching a name to an IP address of an application running on a host? A. firewall B. proxy C. load balancer D. DNS Correct Answer: D
Which network constraint causes the performance of the application to decrease as the number of users accessing the application increases? A. latency B. loss C. bandwidth D. jitter Correct Answer: C
What is a characteristic of Waterfall compared to Agile software development method? A. Waterfall focuses on continuous improvement, and Agile focuses on the design phase. B. Waterfall separates the project development lifecycle into sprints, and Agile does not use cycles. C. Waterfall speci es requirements before development begins, and Agile responds exibly to changes in requirements. D. Waterfall uses reviews with step by step approach, and Agile uses a serially phased approach. Correct Answer: C
Refer to the exhibit. A network engineer must configure new interfaces on a set of devices and is planning to use an Ansible playbook for the task. All devices support SSH and NETCONF protocol, and the interface variables are unique per device. In which directory are the YAML files including variables hosted to automate the task with the netconf_config module? A. current working directory B. host_vars directory C. group_vars directory D. home directory Correct Answer: A
Which standard supported by Cisco IOS XE and Cisco NX-OS is used for automating the configuration of multiple devices across a network? A. SNMP YANG B. SYSLOG YANG C. CLI YANG D. NETCONF YANG Correct Answer: D
A developer has addressed a bug that was found in the production code of an application. A separate file named `bug427896191v_ x" has been created with the changes to the code. Which Git command must be used to incorporate the bug x into the production code? A. git rebase B. git cat- file C. git merge- file D. git bisert Correct Answer: C
What is a principle of a code review process? A. Changes are made after the code is submitted to source control. B. It must not prevent code from getting into production as quickly as possible. C. Naming standards must be consistent. D. A technical lead must sign off on the review. Correct Answer: D
Why would a developer compare a current version of code to a previous version? A. to provide the single source of truth B. to troubleshoot code failures C. to track who made a change D. to aid in collaboration Correct Answer: B
Which Cisco platform is used to manage data center infrastructure through third-party tools and system integrations? A. Cisco DNA Center B. Cisco UCS Manager C. Cisco Intersight D. Cisco UCS Director Correct Answer: D
Refer to the exhibit. Which RESTCONF request results in this response?



A. D Correct Answer:
Refer to the exhibit. An engineer is managing the network of an enterprise. The network is using a distributed deployment model. The enterprise uses database to store logs. The current policy requires logs to be stored if changes are made to the infrastructure in any of the devices on the data centers. Which work flow is being automated by the Bash script? A. returning backup files that are older than 30 days B. deleting backup files that are older than 30 days C. configuring the directory to delete files automatically D. automating deletion of all backup files every 30 days Correct Answer: B
What is a characteristic of RPC APIs compared to REST APIs? A. Authentication is done over provisions for the service caller and vice versa for RPC API, and REST API uses HTTP headers for authentication. B. All communications between the client and server must be stateless for RPC API, and REST API is stateful. C. The architecture model for RPC API is resource-focused, and REST API is procedure-focused. D. The data payload must be in JSON format for RPC API, and REST API allows JSON and XML formats. Correct Answer: A
Which two situations align with infrastructure as code principles? (Choose two.) A. nonreplicable snow ake servers B. release versions to specific hardware C. maximized configuration drift D. easily reproducible systems E. repeatable processes Correct Answer: BD
Refer to the exhibit. A developer writes a script to create a new network by using the Cisco DNA Center API. After running the script for the first time, the developer observes that HTTP code 404 is printed to the console. Which action resolves the problem? A. The x-auth-token value must be changed to a valid token. B. The API URL must be changed with a valid URL. C. The requested payload must be fixed to include missing parts. D. Internal errors on the code of API server must be fixed. Correct Answer: B
A developer plans to deploy a new application that will use an API to implement automated data collection from Webex with these requirements: · The application was created by using the request library. · Requires HTTP basic authentication. · Provides data in JSON or XML formats. Which Cisco DevNet resource helps the developer with how to use the API? A. DevNet sandbox B. API documentation C. forums D. DevNet code exchange Correct Answer: B
An engineer deploys a Cisco CSR 1000 V instance to a virtual machine. The engineer must output the device configuration in JSON format. Which protocol is used for this task? A. YANG B. NETCONF C. SNMP D. RESTCONF Correct Answer: D
What are two benefits of implementing common data structures when working with APIs in remote systems? (Choose two.) A. ensures that developers are limited to using one data schema type B. prevents multivendor interoperability C. improves security in RESTful web services D. enforces standardized data structures E. leverages code that is easily managed and reused Correct Answer: BE
A development team is creating an application used for contactless payments. The application must: · Be web-based · Capture and process the credit card information for a purchase. Which security action must the web application use to gather and process the private customer data? A. Enable RATs to monitor the web application remotely. B. Disable botnets to eliminate risks. C. Disable TLS to increase the connection speed. D. Enable the encryption of network traffic. Correct Answer: D
An engineer needs to collect information about 20,000 Bluetooth clients using the Cisco Meraki API. The API returns only 1,000 results. One of the HTTP response headers has the data: Link: https://api.meraki.com.info/api/v0/networks/ABC/bluetoothClients?perPage=1000&startingAfter=1000>;rel="next" Which RFC is implemented by the API to apply the restriction? A. RFC 5988 Web Linking B. RFC 5890 Response Constraints C. RFC 5005 Feed Paging and Archiving D. RFC 5446 Content Limits Correct Answer: C
What are two benefits of using classes over functions when writing applications? (Choose two.) A. improved readability B. increased compatibility C. variable reusability D. increased performance E. code organization Correct Answer: AC
A developer creates a new application, but the application must be tested before being released to a customer. When a mobile phone that uses 4G is used to access the application, the request fails. Why does the connection to the application fail? A. The application is hosted on premises and VPN connectivity is required B. The application must be added to the production server before testing. C. The application must be moved to the cloud before testing is possible. D. The application connectivity is limited to HTTPS protocol. Correct Answer: A
Which platform has an API that has the capability to obtain a list of vulnerable software on user devices? A. Cisco Advanced Malware Protection B. Cisco Umbrella C. Cisco Identity Services Engine D. Cisco Firepower Correct Answer: A
A developer creates an application that must provide an encrypted connection or API keys. The keys will be used to communicate with a REST API. Which command must be used for the secure connection? A. curl X PUSH `http://username.app.com/endpoint/?api_key=12345abcdef' B. curl v `ftp://username.app.com/endpoint/?api_key=12345abcdef' C. curl X GET `https://username.app.com/endpoint/?api_key=12345abcdef' D. curl X GET `http://username.app.com/endpoint/?api_key=12345abcdef' Correct Answer: C
Which protocol runs over TCP port 23? A. SSH B. NETCONF C. HTTP D. Telnet Correct Answer: D
Which protocol is used for clock synchronization between network devices? A. FTP B. NNTP C. BGP D. NTP Correct Answer: D
Which traffic is handled on the control plane? A. BGP B. SMB C. NTP D. NETCONF Correct Answer: A
Refer to the exhibit. What does the load balancer enable in the network topology? A. hosted application to access Internet services B. external requests to be routed to the application servers C. application to access the database server D. workstations to access the Internet Correct Answer: B
What are two benefits of using VLANs? (Choose two.) A. limits the devices that can join the network B. enables the logical grouping of devices that belong to different Layer 2 devices C. segments the broadcast domain D. allows all network devices to be accessible from any host on the network E. extends the broadcast domain Correct Answer: BC
What are two considerations when selecting the `best route` for a network device to reach its destination? (Choose two.) A. MAC address B. IP address C. metrics D. administrative distance E. subnet mask Correct Answer: CD
Users cannot access a webserver and after the traffic is captured, the capture tool shows an ICMP packet that reports "communication administratively prohibited". What is the cause of this webserver access issue? A. An access list along the path is blocking the traffic. B. Users must authenticate on the webserver to access it. C. A router along the path is overloaded and thus dropping traffic. D. The traffic is not allowed to be translated with NAT and dropped. Correct Answer: A
Which application should be used to externally access all applications deployed in the same host machine with a single public IP address and port, when each application listens on different local ports? A. reverse proxy B. load balancer C. DNS D. firewall Correct Answer: B
Which implementation creates a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire? A. WLAN B. VLAN C. IPsec D. HSRP Correct Answer: B
What are two properties of private IP addresses? (Choose two.) A. They can be used to access the Internet directly. B. They are more secure than public IP addresses. C. They are not globally unique. D. They can be repeated within the same local network. E. They are controlled globally by an IP address registry. Correct Answer: BC
Which two details are captured from the subnet mask? (Choose two.) A. portion of an IP address that refers to the subnet B. default gateway of the host C. unique number ID assigned to the host D. part of an IP address that refers to the host E. network connection of a host or interface Correct Answer: AD
Refer to the exhibit. While developing a Cisco Webex bot, an application reaches the public IP address of the firewall, but traffic is forwarded to the IP address of server 1 instead of the IP address of server 2. What causes this issue? A. The proxy server that rewrites traffic is misconfigured. B. The router is sending the traffic to server 1 instead of server 2. C. The switch is forwarding IP traffic to the wrong VLAN. D. NAT is misconfigured on the firewall. Correct Answer: D
Developer is working on a new feature and made changes on a branch named 'branch-413667549a-new'. When merging the branch to production, conflicts occurred. Which Git command must the developer use to recreate the pre-merge state? A. git merge "no-edit B. git merge "commit C. git merge "revert D. git merge "abort Correct Answer: D
A company wants to automate the orders processed on its website using API. The network device that supports the solution must: · support XML encoding · support distributed transactions · support YANG data models · be support software redundancy Which requirement prevents the use of RESTCONF for the solution? A. software redundancy B. YANG data models C. distributed transactions D. XML encoding Correct Answer: C
Refer to the exhibit. An engineer sends the request to collect data over Cisco AMP for Endpoints API. The Engineer must list guide and hostname data for all computers, but the first request returns only 500 items out of 2,000. Then, the engineer adds the loop to collect all the data. What must be added to the script where the code is missing to complete the requests?



A. C Correct Answer:
What is the meaning of the HTTP status code 204? A. request completed; new resource created B. server successfully processed request; no content returned C. standard response for successful requests D. invalid query parameters Correct Answer: B
Which two commands download and execute an Apache web server container in Docker with a port binding 8080 in the container to 80 on the host? (Choose two.) A. docker pull apache B. docker run p 8080:80 httpd C. docker run p 80:8080 httpd D. docker pull httpd E. docker pull https Correct Answer: DC
A group of software developers wants to improve its collaboration with the operations team. The group wants to deliver release-ready code that merges code changes back to the main branch and runs the automated testing as often as possible. Which DevOps concept does this scenario represent? A. continuous delivery B. version control C. continuous integration D. continuous deployment Correct Answer: C
A developer is running an application that connects to the Cisco website and collects data. The application will be hosted in a local data center and the data will need to be collected on a frequent basis. The application client requires certain environmental variables to be set before the run. Which Bash command sets the environmental variables for a Linux system?


A. Correct Answer: D
Refer to the exhibit. Which HTTP code is returned after the RESTCONF query is executed? A. 201 B. 204 C. 302 D. 304 Correct Answer: A
Which detail is included in a routing table? A. broadcast address B. TCP or UDP port number C. IP protocol D. destination next hop or outgoing interface Correct Answer: D
What is an example of a network interface hardware address? A. workstation name B. IP address C. domain name D. MAC address Correct Answer: D
On which network plane is routing protocol traffic handled? A. management plane B. data plane C. authentication plane D. control plane Correct Answer: D
Which service provides a directory lookup for IP addresses and host names? A. DNS B. NAT C. SNMP D. DHCP Correct Answer: A
Which two query types does a client make to a DNS server? (Choose two.) A. Inverse B. PTR C. AAAA D. ACK E. DISCOVER Correct Answer: BC
Which protocol runs over TCP port 22? A. SSH B. NETCONF C. HTTP D. Telnet Correct Answer: A
Which device is used to transport traffic from one broadcast domain to another broadcast domain? A. layer 2 switch B. proxy server C. router D. load balancer Correct Answer: C
Users cannot access a webserver and after the traffic is captured, the capture tool shows an ICMP packet that reports "time exceeded in-transit". What is the cause of this webserver access issue? A. A router along the path has the wrong time. B. A router along the path is misrouting the packets in a wrong direction. C. The server is too loaded and the connection could not be handled in time. D. The server is too far away and the packets require too much time to reach it. Correct Answer: B
What is used in Layer 2 switches to direct packet transmission to the intended recipient? A. MAC address B. IPv6 address C. spanning tree D. IPv4 address Correct Answer: A
What is the purpose of a firewall in application deployment? A. adds TLS support to an application that does not support it natively B. limits traffic to only ports required by the application C. provides translation for an application's hostname to its IP address D. forwards traffic to a pool of instances of the application Correct Answer: B
A small company has 5 servers and 50 clients. What are two reasons an engineer should split this network into separate client and server subnets? (Choose two.) A. Subnets will split domains to limit failures. B. A router will limit the traffic types between the clients and servers. C. Subnets provide more IP address space for clients and servers. D. A router will bridge the traffic between clients and servers. E. Internet access to the servers will be denied on the router. Correct Answer: AB
What is the function of an IP address in networking? A. represents a network connection on specific devices B. speci es the type of traffic that is allowed to roam on a network C. speci es resource's location and the mechanism to retrieve it D. represents the unique ID that is assigned to one host on a network Correct Answer: D
Where is an IP packet routed if the packet does not match any routes in the routing table? A. firewall B. load balancer C. central switch D. default gateway Correct Answer: D
What are two functions of a routing table on a network device? (Choose two.) A. It lists the routes to drop traffic. B. It lists the routes to a particular destination. C. It lists the static and dynamic entries. D. It lists hosts that are one hop away. E. It lists entries more than two hops away. Correct Answer: BC
What does a load balancer distribute in a network environment? A. different TCP connections to the routers B. incoming traffic across multiple servers C. traffic in the network by leveraging the switch architecture D. outgoing connections to the network Correct Answer: B
Refer to the exhibit.Which Device limits traffic between Server 1 and Server 2? A. Device B B. Device C C. Device D D. Device E Correct Answer: C
What is the purpose of a MAC address on a network device? A. unique network address that identifies the network interface of a device B. unique network interlace address that is provided by the DHCP server C. unique hardware address that identifies the network interface of a device D. unique hardware interface address that is provided by the central switch Correct Answer: C
How are load balancers used in modern application deployments? A. Turn off traffic and take down compute units, then update and bring the compute units back up. B. Allow traffic to continue as new compute units are brought up and old compute units are taken down. C. Allow HTTP and HTTPS traffic to continue as old compute units are discontinued before new units are brought up. D. Bring up new compute units, test the compute units, and switch the traffic from old units to new units. Correct Answer: B
Which protocol must be allowed on the firewall so that NTP services work properly? A. TCP B. ICMP C. BGP D. UDP Correct Answer: D
What is the purpose of the first three pairs of digits in a MAC address? A. defines packet forwarding priority sent or received by the adapter B. defines a routing identifier for the client C. indicates vendor of the network card or adapter D. indicates the IP address of the client in Hex Correct Answer: C
On which port does NETCONF operate by default? A. 23 B. 443 C. 822 D. 830 Correct Answer: D
Which two types of NAT are used in a network? (Choose two.) A. routed NAT B. static NAT C. multicast NAT D. normal NAT E. dynamic NAT Correct Answer: BE
Refer to the exhibit. A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1? A. enable_function(Loopback1, true, 'iana-if-type:softwareLoopback') B. enable_function('iana-if-type:softwareLoopback', Loopback1, true,) C. def enable_function('iana-if-type:softwareLoopback', Loopback1, false,) D. def enable_function(Loopback1, true, 'iana-if-type:softwareLoopback') Correct Answer: D
An engineer must configure Cisco Nexus devices and wants to automate this work flow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code, which resource must be used to verify that the code works correctly? A. Cisco NX-OS SDK B. Cisco Learning Labs C. Cisco Code Exchange D. Cisco Modeling Labs Correct Answer: A
A new application is being developed with specific platform requirements. The platform and application deployment and the ongoing platform management must be fully automated. The application includes a large database component that has significant disk I/O requirements. Which application deployment type meets the requirements? A. Python virtual environment B. virtual machine C. bare metal D. container Correct Answer: B
Refer to the exhibit. A developer must check packages on web load balancers that use nginx packages. The developer updates the servers as required in Ansible inventory and prepares an Ansible playbook to automate this work flow on related servers. Which process is being automated by the Ansible playbook? A. verifying that nginx is installed only if apache2 is unavailable on the system, and then updating all the other packages B. verifying, without installing, that apache2 is unavailable and that nginx is installed, and then updating the repository to the latest version C. uninstalling the apache2 server, installing the nginx server, and then updating all the packages to the latest version D. installing nginx, uninstalling apache2, and then verifying that the package repository is at the latest version Correct Answer: B
Refer to the exhibit. An engineer must check the admin rights of users on a database regularly and prepares the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection? A. They must be stored in configuration files if there is a possibility of leakage. B. They must be Base64-encoded if stored in the user database. C. They must be encrypted if stored in the user database. D. They must be stored in configuration files if no authentication will be used. Correct Answer: D
Refer to the exhibit. A network engineer must collect information from the network using Cisco DNA Center APIs. The script must query for the devices with 'platformId' 'C9540-x' and then send commands to be executed. Which process is automated by the Python script? A. results gathering of the show version and show ip int brief commands B. output of show ip int brief command on devices of type C9500-40X C. execution information of the show version and show ip int brief commands D. list of executed commands on C9500-40X and the information of show ip int brief command Correct Answer: B
Refer to the exhibit. Which two files are being edited in the unified diff? (Choose two.) A. READM B. md C. setup.py D. axl.py E. ciscoaxl.py F. index.py Correct Answer: BC
Refer to the exhibit. What do all the calls shown in the sequence diagram have in common? A. All the calls are optional. B. All the calls are asynchronous. C. All the calls are synchronous. D. All the calls depend on the catalog. Correct Answer: D
Refer to the exhibit. What are two characteristics of the NETCONF response? (Choose two.) A. ospf is defined by the ietf-ospf module. B. ietf-ospf imports ietf-routing. C. redistribution is a module of type cisco-ospf. D. routing protocols is a list. E. The main module is routing. Correct Answer: BC
A business needs to create a simulated environment that mimics a production infrastructure to make changes to the OSPF process and analyze the impact. What should be used? A. Cisco VIRL / Cisco CML B. Cisco DevNet Sandbox labs C. pyATS D. Puppet Correct Answer: A
What is a benefit of a CI/CD pipeline for infrastructure? A. removes manual errors B. enables manual steps C. removes the need for operations D. provides variety for deployments Correct Answer: A
During which step of the CI/CD pipeline for infrastructure automation is code from multiple developers combined to compile and test different components? A. integration B. deployment C. development D. testing Correct Answer: A
Refer to the exhibit. Which work flow does the script automate? A. retrieves a media server that is being monitored B. updates a media server that is being monitored C. adds a media server to be monitored D. deletes a media server that is being monitored Correct Answer: B
Which description of a default gateway is true? A. It is a security feature that denies certain traffic. B. It is a device that receives IP packets that have no explicit next-hop in the routing table. C. It is a feature that translates between public and private addresses. D. It is a device that receives Layer 2 frames with an unknown destination address. Correct Answer: B
Which device is a system that monitors and controls incoming and outgoing network traffic based on predetermined security roles? A. router B. switch C. load balancer D. firewall Correct Answer: D
In DNS, which record speci es an alias that refers to another name that ultimately resolves to an IP address? A. CNAME B. NS C. AAA D. SOA Correct Answer: A
What is the purpose of a MAC address? A. to uniquely identify a switch in a LAN B. to uniquely identify a router in a LAN C. to uniquely identify a network interface in a LAN D. to uniquely identify a device on the Internet Correct Answer: C
Refer to the exhibit.Which two statements about the network diagram are true? (Choose two.) A. The subnet address of PC-B has 18 bits dedicated to the network portion. B. One of the routers has two connected serial interfaces. C. R1 and R3 are in the same subnet. D. PC-A and PC-B are in the same subnet. E. The subnet of PC-C can contain 256 hosts. Correct Answer: BD
Which configuration management tool has an agentless capability? A. Puppet B. CFEngine C. Ansible D. Chef Correct Answer: C
Refer to the exhibit.What is represented in this YANG module? A. interface management B. BGP C. OpenFlow D. topology Correct Answer: A
Which CI/CD tool is an automation tool used to build, test, and deploy software? A. Git B. Gradle C. Nagios D. Jenkins Correct Answer: D
An automation script fails to connect to an internal server exactly 1 out of 2 times it is executed. This behavior is seen from different clients. Which networking device must be at fault? A. load balancer B. laptop on which the script is running C. switch D. router Correct Answer: A
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.) A. multi-platform vendor abstraction B. compiles to executables that run on network devices C. designed to reflect networking concepts D. directly maps to JavaScript E. command line driven interface Correct Answer: AC
Refer to the exhibit.Which infrastructure automation method is shown? A. CI/CD pipeline B. Lean C. Agile D. Waterfall Correct Answer: A
Refer to the exhibit. An engineer must configure a load balancer server. The engineer prepares a script to automate work flow by using Bash. The script installs the nginx package, moves to the /opt/nginx directory, and reads the sites.txt file for further processing. Based on the script work flow, which process is being automated within the loop by using the information in sites.txt? A. creating a file per each line in sites.txt with the information in template.conf, creating a link for the previously created file, and then changing the ownership of the created files B. using the content of the file to create the template.conf file, creating a link from the created file to the /etc/nginx/sites_enabled, and then changing the file execution permissions C. creating a new file based on template.conf in the /etc/nginx/sites_enabled directory for each line in the sites.txt file, and then changing the file execution permissions D. using the information in the file to create a set of empty files in the /etc/nginx/sites_enabled directory, and then assigning the owner of the file Correct Answer: A
Refer to the exhibit. A network engineer must collect information from the network. The engineer prepares a script to automate work flow by using Cisco Meraki API. The script must run over nested loops to collect organization and network information and uses the collected data for final collection. Which process is being automated by using the Python script? A. Collect the IDs of the clients on the BLDG21 network. B. List the IDs from the ACME organization. C. Provide the BLDG21 network information if it is part of the ACME organization. D. Gather the IDs of the ACME organization, the BLDG21 network, and the clients on the network. Correct Answer: D
Refer to the exhibit.What is the function of the Python script? A. Loop through the returned list of network devices and, for each device, print the device name and management IP address. B. Count and print the total number of available devices. C. For each device that is returned, display the device type and associated management IP address. D. Iterate over a list of network devices and write all device names and management IP addresses to an output file. Correct Answer: A
Refer to the exhibit. The output of the diff -u READM A. md-repo READM B. md command is shown. The original file was 165 lines long. How many lines are in the edited copy of the file? C. 162 D. 165 E. 172 F. 173 Correct Answer: C
Which line is an example of the start of a chunk from a unified diff? A. @@ -20191007T1200 +88,90 @@ B. @@ -88,10 +88,6 @@ C. @@ -90,88 +20191008T1349 @@ D. @@ -20191007T1200 +20191008T1349 @@ Correct Answer: B
Which two NETCONF operations cover the RESTCONF GET operation? (Choose two.) A. <get> B. <get-config> C. <get-update> D. <modify-config> E. <edit> Correct Answer: AB
Refer to the exhibit.What is the result of executing this Ansible playbook? A. The playbook copies a new start-up configuration to CISCO_ROUTER_01 B. The playbook copies a new running configuration to CISCO_ROUTER_01 C. The playbook backs up the running configuration of CISCO_ROUTER_01 D. The playbook backs up the start-up configuration of CISCO_ROUTER_01 Correct Answer: C
Refer to the exhibit.Which two statements describe the configuration of the switch after the Ansible script is run? (Choose two.) A. traffic from ports 0/2 to 0/5 is able to flow on port 0/1 due to the trunk. B. GigabitEthernet0/1 is left unconfigured. C. GigabitEthernet0/2 and GigabitEthernet0/3 are access ports for VLAN 6. D. traffic is able to flow between ports 0/2 to 0/5 due to the trunk on port 0/1. E. traffic on ports 0/2 and 0/3 is connected to port 0/6. Correct Answer: AC
Refer to the exhibit.What is the effect of this Ansible playbook on an IOS router? A. A new running configuration is pushed to the IOS router. B. The start-up configuration of the IOS router is copied to a local folder. C. The current running configuration of the IOS router is backed up. D. A new start-up configuration is copied to the IOS router. Correct Answer: B
Which toot allows changes to the configuration management toolset to be tested? A. pyATS B. NAPALM C. Cisco VIRL D. Ansible Correct Answer: A
Refer to the exhibit. A developer must integrate a bot with an internal communication app. The developer wants to replace the webexbot package with the teamsbot package by using Ansible and prepares a playbook. In the first two tasks, the playbook stops the webexbot and verifies that the teamsbot is installed. What is accomplished in the last task of the work flow when the developer runs the Ansible playbook? A. uninstalls the webexbot package and removes its configuration files B. installs the webexbot and retains the configuration files C. stops the webexbot service and uninstall it and retains its configuration files D. searches whether the purge package is available in the repository and uninstalls the webexbot package Correct Answer: A
Refer to the exhibit.What is the value of the node defined by this YANG structure?



Correct Answer: C Correct Answer: C
What is an advantage of using network programmability? A. Manual configuration is faster. B. No cloud abstraction occurs. C. It removes CLI access for devices. D. It provides for more scalable and replicable network provisioning. Correct Answer: D
What is a capability of an agentless configuration management system? A. It requires managed hosts to have an interpreter for a high-level language such as Python or Ruby. B. It requires managed hosts to connect to a centralized host to receive updated configurations. C. It uses compiled languages as the basis of the domain-specific language to interface with managed hosts. D. It uses existing protocols to interface with the managed host. Correct Answer: D
Refer to the exhibit.Which OWASP threat does this example demonstrate? A. broken access control B. cross-site scripting C. SQL injection D. man-in-the-middle Correct Answer: B
What should a CI/CD pipeline aim to achieve? A. to require minimal manual interaction B. to allow manual testing before deployment C. to support new deployments on a fixed monthly schedule D. to provide a documented process for feedback Correct Answer: A
A function my_func() returns True when it executes normally. Which Python snippet tests my_func()?


Correct Answer: C Correct Answer: C
What are two roles of an artifact repository in a CI/CD pipeline? (Choose two.) A. stores files needed and generated during the build process B. provides traceable, searchable, and manageable binary files C. is required for CI/CD pipelines executed on a public cloud infrastructure D. allows for comparing and merging changes in the source code E. is required for managing open source software Correct Answer: AB
A company is adopting DevOps as part of an internal transformation, and is reviewing the success of the first deployments. Developers and engineers are working together to resolve any resulting issues. However, this new way of working has increased overhead, and the team is nding it difficult to complete releases in time. Which area of the CALMS framework must the company target for improvement? A. Collaboration B. Lean C. Sharing D. Measurement Correct Answer: B
Refer to the exhibit. Which command, including arguments, is executed when the container starts? A. /bin/sh -c "/bin/sleep 30 && nginx -g 'daemon off;'" B. /bin/sh -c "/bin/sleep 10 && nginx -g 'daemon off;'" C. /bin/bash -c "/bin/sleep 30 && nginx -g 'daemon off;'" D. /bin/sh -c "/bin/sleep 30" && nginx -g 'daemon off;' Correct Answer: A
A developer created a new secure API and is testing the functionality locally. The API was added to a container for further testing, and other team members and applications need to connect to the API. Which command exposes the API in the container as port 8443 and allows connections external to the host? A. docker run -p 127.0.0.1:80:8443/tcp myapiservice B. docker run -p 0.0.0.0:443:8443/tcp myapiservice C. docker run -p 0.0.0.0:8443:443/tcp myapiservice D. docker run -p 127.0.0.1:443:8443/tcp myapiservice Correct Answer: C
A developer has created a new image to use in a Docker build and has added a tag for the image by using the command: $ docker tag 84fe411926287 local/app:0.4 Which command must be executed next to build the Docker image using the tag? A. $ docker build -p local/app:0.4 B. $ docker run -t local/app:0.4 C. $ docker run -p local/app:0.4 D. $ docker build -t local/app:0.4 Correct Answer: D
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.) A. 22 B. 23 C. 80 D. 443 E. 880 Correct Answer: AD
What is a benefit of using a code review process in application development? A. accelerates the deployment of new features in an existing application B. provides version control during code development C. enables the quick deployment of new code D. eliminates common mistakes during development Correct Answer: D
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack? A. phishing B. DoS C. brute force attack D. CSRF Correct Answer: D
Refer to the exhibit. An application must be deployed on a server that has other applications installed. The server resources are to be allocated based on the deployment requirements. The OS for each application must be independent. Which type of deployment is used? A. hybrid B. virtual machines C. containers D. bare metal Correct Answer: B
What is a benefit of a distributed version control system? A. encourages users to commit small places of work to the system more frequently B. ensures that all code meets minimum standards before being committed to the system C. allows users to work on the codebase even when not connected to the Internet D. ensures that all code is tested before being committed to the system Correct Answer: C
A company requires a new platform to store large volumes of log data that is generated in their assembly plant. The platform must be scalable, so the underlying technology must provide a path for fast deployment of new nodes for data and indexing? The data contains sensitive information, so specialist encryption tools must be used to secure the data. Which application deployment model meets the requirements? A. edge B. private cloud C. public cloud D. hybrid cloud Correct Answer: B
What is a procedural component of CI/CD pipelines? A. Bundled artifacts must be generated. B. Every test must pass for the pipeline to continue its execution. C. Some tests fall without stopping the pipeline execution. D. The release label that identifies the build is optional. Correct Answer: A
Which OWASP threat occurs when untrusted data is supplied as input to an interpreter as part of a command or query? A. broken authentication B. data exposure C. injection D. cross-site scripting Correct Answer: C
Which product provides network controller-level management features? A. Cisco ISE B. Cisco DNA Center C. Cisco UCS Manager D. Cisco NX-OS Correct Answer: B
What is the purpose of the Cisco VIRL software tool? A. to verify configurations against compliance standards B. to automate API work ows C. to simulate and model networks D. to test performance of an application Correct Answer: C
What are two advantages of the Model-View-Controller software design pattern? (Choose two.) A. allows for multiple views of the same model B. separates responsibilities of the code, which makes future modifications easier C. simpli es network automation D. makes code easier to deploy using CI/CD pipelines E. reduces the need for error handling Correct Answer: AB
Refer to the exhibit. Which JSON snippet configures a new interface according to YANG model?



Correct Answer: D Correct Answer: D
Which platform is run directly on top of a hypervisor? A. bare metal systems B. virtual machines C. containers D. applications Correct Answer: B
A company wants to accelerate the adoption of technologies that will simplify its operations. Staff have different skill levels and are looking for a single site to find easy-to-consume beginner, intermediate, and advanced multidomain use cases. Which site should be used? A. DevNet Ecosystem Exchange B. DevNet Automation Exchange C. DevNet Creations D. DevNet Support Forum Correct Answer: B
Which Cisco product provides malware and content filtering through DNS? A. Cisco ASA Firepower module B. Cisco AMP C. Cisco ISE D. Cisco Umbrella Correct Answer: D
Which Cisco platform provides organization-wide automation, security, policy enforcement, and agility across wired and wireless networks? A. Cisco SD-WAN B. Cisco DNA Center C. Cisco ACI D. Cisco Umbrella Correct Answer: B
What is a characteristic of the Cisco Finesse platform? A. Applications allow services to be invoked on a network triggered event. B. The platform provides a ready-to-go platform for HD video and audio conferencing. C. Applications are added to the platform from the desktop remotely. D. The platform includes an enterprise-class IM engine. Correct Answer: C
An engineer needs to retrieve a list of locally available Firepower Threat Defense upgrade packages by using the Firepower Management Center REST API. The engineer uses a GET request with the URL: /api/fmc_platform/v1/updates/upgradepackages/f413afeb-e6f6-75f4-9169-6d9bd49s625e What does `f413afeb-e6f6-75f4-9169-6d9bd49s625e` represent? A. container UUID B. package UUID C. domain UUID D. object UUID html Correct Answer: B
Refer to the exhibit.A process running on the host wants to access the service running inside this Docker container. Which port or ports are used to make a connection? A. only outbound connections between 3000 and 5000 are possible B. port 3000 C. any port between 3000 and 5000 D. port 5000 Correct Answer: D
What are two security benefits of a Docker-based application? (Choose two.) A. natively secures access to secrets that are used by the running application B. guarantees container images are secured and free of vulnerabilities C. easier to patch because Docker containers include only dependencies that the application requires D. prevents information leakage occurring when unhandled exceptions are returned in HTTP responses E. allows for separation of applications that traditionally run on the same host Correct Answer: CE
A local Docker alpine image has been created with an image ID of a391665405fe and tagged as `latest`. Which command creates a running container based on the tagged image, with the container port 8080 bound to port 80 on the host? A. docker build -p 8080:80 alpine:latest B. docker exec -p 8080:80 alpine:latest C. docker start -p 8080:80 alpine:latest D. docker run -p 8080:80 alpine:latest Correct Answer: D
Refer to the exhibit.Which function does the EXPOSE line perform when building an image from this Docker file? A. Local port 8080 of the container that launched with this docker image is accessible from co-hosted containers and external clients. B. Local port 8080 is not reachable at all because no IP address is speci ed along with the EXPOSE command of the Docker file. C. Local port 8080 is accessible from other containers running on the same docker host as the container that launched with this docker image. D. Local port 8080 of the container that launched with this docker image is accessible to external clients. Correct Answer: C
Which two elements are foundational principles of DevOps? (Choose two.) A. organizing cross-functional teams over organizational silos B. designing applications as microservices C. encouraging containers for the deployment of applications D. automating over documenting E. optimizing the cost of infrastructures Correct Answer: AD
What are two characteristics of Bare Metal environments that are related to application deployment? (Choose two.) A. specifically designed for container-based workloads B. suitable for legacy applications that do not support virtualization C. provides workloads with access to hardware features D. not compatible with other cloud services such as PaaS or SaaS offerings E. provides the hypervisor to host virtual servers Correct Answer: CE
A new application is being developed that must be hardware independent. The application includes an administrative component which is accessed using a Windows desktop GUI. Installation and management of the environment must be fully automated. Which application deployment type meets the requirements? A. virtual machine B. virtual Python environment C. container D. bare metal Correct Answer: C
Refer to the exhibit.What is the action of the Bash script that is shown? A. For all directories in the current folder, the script goes into the directory and makes a new directory. B. The script waits until input is entered. If the directory exists, the script goes into it until there is no directory with the same name, then it creates a new directory. C. The script waits until input is entered, then it goes into the directory entered and creates a new directory with the same name. D. The script goes into the directory called $ndir and makes a new directory called $ndir . Correct Answer: B
When using the Bash shell, how is the output of the devnet command saved to a file named `output.txt`? A. devnet > output.txt B. devnet | output.txt C. devnet < output.txt D. devnet & output.txt Correct Answer: A
After a project is migrated to a new codebase, the `old_project` directory must be deleted. This directory has multiple read-only ies, and it must be deleted recursively without prompting for confirmation. Which Bash command must be used? A. rmdir -p old_project B. rm -rf old_project C. rm -r old_project D. rmdir old_project Correct Answer: B
What is a benefit of using edge computing in an IoT implementation? A. high speed in data processing B. low network design complexity C. low cost in network design D. high availability for network components Correct Answer: A
What is the benefit of edge computing? A. It reduces network latency by moving processing closer to the data source. B. It reduces data velocity from devices or other data sources. C. It simpli es security as devices and processing are brought closer together. D. It removes the need for centralized data processing. Correct Answer: A
Which type of threat occurs when an attacker can send hostile data to an interpreter within an application? A. sensitive data exposure B. broken authentication C. cross-site scripting D. injection Correct Answer: D
A company is looking for a cloud deployment which will only use the on-premise infrastructure, is user self-service, and is easy to scale. Which cloud solution should be selected for these requirements? A. multi B. private C. hybrid D. public Correct Answer: B
Which operation is performed with YANG model-driven programmability in NX-OS? A. configure a device with native and Openconfig-based models B. bootstrap a device that has a factory-default configuration C. send CLI commands to a device and retrieve output in JSON format D. run Linux commands natively on the device Correct Answer: A
What are two benefits of model-driven programmability? (Choose two.) A. easier to design, deploy, and manage APIs B. single choice of transport, protocol, and encoding C. models decoupled from transport, protocol, and encoding D. model-based, structured, and human friendly E. model-driven APIs for abstraction and simpli cation Correct Answer: CE
What is a benefit of model-driven programmability? A. It provides a programmatic and standards-based way of writing configurations to any network device. B. By modeling data, it ensures that vast quantities of data are usable for monitoring. C. It simpli es management and operations by decoupling the networking hardware from its control mechanism. D. It addresses the static architecture of traditional networks being decentralized and complex. Correct Answer: A
Which type of HTTP method is used by the Meraki and Webex Teams APIs to send webhook notifications? A. HTTP POST B. HTTP GET C. HTTP HEAD D. HTTP PUT Correct Answer: A
Refer to the exhibit. The Cisco Meraki API manages two organizations. In each organization, two independent networks are defined. How many calls to the / organizations/{orgId}/networks endpoint will be run parallel by the GetAllNetworks function of the API client? A. 0 B. 1 C. 2 D. 4 Correct Answer: C
Refer to the exhibit.The definition of the YANG module and a RESTCONF query sent to a Cisco IOS XE device is shown. Why does the RESTCONF interface respond with a 204 status code? A. The query retrieved the logging severity level. B. The query updated the logging severity level or created it if not present on the device. C. The query failed at retrieving the logging severity level. D. The query failed to set the logging severity level due to an invalid path. xml/ios/prog/configuration/1611/b_1611_programmability_cg/restconf_programmable_interface.html Community vote distribution Correct Answer: B
What is a requirement when authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software? A. No authentication is required. B. OAuth must be used. C. A token must be retrieved and the associated string must be embedded in the X-Auth-Token header. D. Basic authentication must be used. Correct Answer: D
Which API must an engineer use to change a netmask on a Cisco IOS XE device? A. Meraki B. SD-WAN C. RESTCONF/YANG D. DNAC Correct Answer: C
A developer creates a script that configured multiple Cisco IOS XE devices in a corporate infrastructure. The internal test environment is unavailable, and no maintenance window is available to test on a low-priority production environment. Which resource is used to test the code before it is applied to the production environment? A. Code Exchange B. Cisco Support C. Cisco DevNet Learning Labs D. Cisco DevNet Sandbox Correct Answer: D
Which tool is used to block all traffic to the domain by using a single API call? A. Cisco Firepower B. Cisco AMP C. Cisco Umbrella D. Cisco ISE Correct Answer: C
Why is refactoring done during test-driven development? A. to enable larger objects and longer methods B. to improve maintainability and readability C. to ensure that the previous uses of the objects are explained D. to ensure the duplication of essential code Correct Answer: B
Refer to the exhibit. A network engineer must change the configuration on devices daily. The Python script must collect CLI arguments from the user, organize data according to the Cisco-IOS-XE-native YANG model, and utilize Cisco REST APIs to make the configuration. Which work flow is being automated by the Python script? A. updating an existing route on the device B. adding a new route to a device C. including a route on the device and overwriting the current routes D. deleting the route that is passed through the command-line variables Correct Answer: A
Which platform is used to programmatically create a space and invite users for collaboration? A. Cisco Intersight B. Cisco Finesse C. Cisco Webex D. Cisco UCM Correct Answer: C
Refer to the exhibit. A developer wants to create a room named cisco through Webex API. The developer prepares the request by putting an API token inside the authorization header; however, the given HTTP call returns error code 400. How must the call parameters be changed to ensure a valid response? A. Replace the team body parameter with the name body parameter. B. Replace cisco with a valid name for a team. C. Change the token in the header with the authorization token. D. Change the HTTP method of the call to PUT. Correct Answer: A
Refer to the exhibit. Which line must be included in the Bash script for the Python code to succeed? A. define WEBEX_TEAMS_ACCESS_TOKEN=your_access_token_here B. export WEBEX_TEAMS_ACCESS_TOKEN=your_access_token_here C. set WEBEX_TEAMS_ACCESS_TOKEN=your_access_token_here D. WEBEX_TEAMS_ACCESS_TOKEN=your_access_token_here Correct Answer: B
What is a capability of the NETCONF protocol? A. allows Python scripts to be executed externally from a network device B. uses JSON to encode data in its content layer C. allows XML messages to be exchanged via the SSH protocol D. exposes a web-based interface Correct Answer: C
Refer to the exhibit. A network engineer uses model-driven programmability to monitor and perform changes on the network. The network engineer decides to use the NETCONF RPC message to complete one of their tasks. What is accomplished by sending the RPC message? A. The running-config of the device is returned. B. The name of each interface is reset to a default name. C. All the YANG capabilities supported by the device are returned. D. A list of interface names is returned. Correct Answer: A
Refer to the exhibit. A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function? A. resp = requests.post(url, auth=HTTPBasicAuth(DNAC_USER, DNAC_PASSWORD)) token = resp.json()['Token'] return token B. resp = requests.post(url, auth=(DNAC_USER, DNAC_PASSWORD)) token = resp.json ()['Token'] return token C. resp = http.post(url, auth=HTTPBasicAuth(DNAC_USER, DNAC_PASSWORD)) token = resp.json()['Token'] return token D. resp = http.post(url, auth=(DNAC_USER, DNAC_PASSWORD)) token = resp.json()['Token'] return token Correct Answer: A
Refer to the exhibit. A network engineer wants to use an API to update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which line of codefineeds to be placed in the snippet where the code is missing? A. {'Content-Type': 'application/yang.data+xml', 'Accept': 'application/yang.data+xml'} B. {'Content-Type': 'application/yang.data+yaml', 'Accept': 'application/yang.data+yaml'} C. {'Content-Type': 'application/restconf.data+json', 'Accept': 'application/restconf.data+json'} D. {'Content-Type': 'application/yang.data+utf8', 'Accept': 'application/restconf.data+utf8'} Correct Answer: C
Refer to the exhibit. A network engineer works on a Cisco DevNet application that is available for download on the Cisco DevNet website. The engineer prepares a bash script to automate operations that relate to the application. Which work flow is being automated in the bash script? A. compilation and configuration of the Cisco DevNet application so that it must be started manually B. compilation, installation, and configuration of the Cisco DevNet application so that it starts automatically C. compilation and installation of the Cisco DevNet application for an autonomous deployment model D. installation and configuration of the Cisco DevNet application so that it starts manually Correct Answer: B
Which HTTP error code series relates to redirection? A. 400 B. 500 C. 200 D. 300 Correct Answer: D
Which two items are Cisco DevNet resources? (Choose two.) A. TAC Support B. Software Research C. API Documentation D. Bitbucket E. Sandbox Correct Answer: CE
Refer to the exhibit. An engineer writes a Python script that uses two different API calls to query Cisco DNA Center for the number of interfaces on a device. The engineer notices that the two API calls produce different results. Why are fewer interfaces returned for the same device when the 'get_all_interfaces' API call is used? A. times out B. rate limit C. pagination D. invalid password Correct Answer: C
Refer to the exhibit. A collaboration engineer has developed a script to automate the gathering of information by providing the email address of the individual. When the engineer tests the script, a 401 error is received. Which command xes the script? A. Add Authorization : Bearer <WEBEX_TOKEN> to the headers. B. Add Authentication : Basic <WEBEX_TOKEN> in the base_url after https:// . C. Add <Authorization>:<password>@ in the base_url after https:// . D. Add Authentication : Bearer <WEBEX_TOKEN> to the headers. Correct Answer: A
A developer is attempting to retrieve all the messages from a Cisco Webex space. The server responds by sending the first 1,000 messages. The developer must make additional requests to retrieve the rest of the messages. Which API constraint is described in this scenario? A. payload limiting B. throttling C. pagination D. rate limiting Correct Answer: C
Refer to the exhibit. A developer just nished testing a Python script and wants to save the list of packages and versions installed on the current machine. The developer must make sure that it will not cause any issues if tested on another device due to different library versions. Which line of codefineeds to be placed on the snippet where the code is missing? A. pip freeze 2> requirements.txt B. pip freeze > requirements.txt C. pip freeze => requirements.txt D. pip freeze | requirements.txt Correct Answer: B
A developer pushes an application to production. The application receives a webhook over HTTPS without a secret. The webhook information contains credentials to service in cleartext. When the information is received, it is stored in the database with an SHA-256 hash. Credentials to the database are accessed at runtime through the use of a vault service. While troubleshooting, the developer sets the logging to debug to view the message from the webhook. What is the security issue in this scenario? A. Database credentials should be accessed by using environment variables defined at runtime. B. During the transport of webhook messages, the credentials could be unencrypted and leaked. C. During logging, debugging should be disabled for the webhook message. D. Hashing the credentials in the database is not secure enough; the credentials should be encrypted. Correct Answer: B
Refer to the exhibit. A developer cannot reach the web application behind an NGINX load balancer. The developer sends a request to an application FQDN with cURL but gets an HTTP 502 response. Which action solves the problem? A. Fix errors in the server configuration, which is behind the load balancer. B. Bring up the load balancer to the active state. C. Fix errors in the cURL request sent by the client. D. Change the default gateway on the load balancer to an active one. Correct Answer: D
Refer to the exhibit. A network engineer wants use API update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which value is suitable as the headers variable? A. {'Content-Type': 'application/yang.data+yaml', 'Accept': 'application/yang.data+yaml'} B. {'Content-Type': 'application/yang.data+json', 'Accept': 'application/yang.data+json'} C. {'Content-Type': 'application/yang.data+utf8l', 'Accept': 'application/yang.data+utf8'} D. {'Content-Type': 'application/restconf.data+txt', 'Accept': 'application/restconf.data+txt'} Correct Answer: B
Which action do webhooks enable an application to perform? A. Increase the request rate limit. B. Populate the application with restricted data. C. Receive real-time data. D. Implement a push model. Correct Answer: D
Refer to the exhibit. A developer can access the TLS REST API on server A, but cannot access the API on server A. The developer can ping server B. When the developer performs a packet capture on the TLS REST API port on server B, the capture shows that the packet arrived and the server responded. What causes the issue? C. Port 80 is blocked on the outgoing interface of firewall D. Port 443 is blocked on the outgoing interface of firewall E. Port 443 is blocked on the incoming interface of firewall F. Port 80 is blocked on the incoming interface of firewall G. Correct Answer: C
How are operations on REST APIs performed as compared to RPC APIs? A. In a REST API, operations are performed on an object (node) that is identified by a URL, but RPC APIs are operation-oriented. B. In a REST API, operations are performed on an external resource that is defined on the API, but the RCP APIs are resource-oriented. C. In a REST API, operations are performed on a platform that is identified by the URL, but RPC APIs are platform-oriented. D. In a REST API, operations are performed on an internal resource that is defined on the API, but RPC APIs are resource-oriented. Correct Answer: A
Which platform has an API that can be used to obtain a list of vulnerable software on user devices? A. Cisco Umbrella B. Cisco Firepower C. Cisco Identity Services Engine D. Cisco Advanced Malware Protection Correct Answer: D
While developing a real-time VoIP application on a Cisco Webex platform, users report that their voice gets chopped or parts of the conversation drop out. Which network constraint is impacting the application? A. jitter B. capacity C. delay D. latency Correct Answer: A
A company has written a script that creates a log bundle from the Cisco DNA Center every day. The script runs without error and the log bundles are produced. However, when the script is run during business hours, people report poor voice quality of phone calls. What explains this behavior? A. The script is written in a low-level programming language where there is no memory safety. This causes a buffer over flow and disruption on the network. B. The speed and duplex settings in Cisco DNA Center are set incorrectly, which causes the transfer to be too slow. C. The script is running in the Voice VLAN and causes delays and jitter in the subnet. D. Generating the logs causes the CPU on the network controller to spike, which causes delays in forwarding the voice IP packets. Correct Answer: C
Refer to the exhibit.Given the API documentation for the UCS SDK Python class, UcsHandle, which code snippet creates a handle instance?



Correct Answer: B Correct Answer: B
Refer to the exhibits.
The Python interpreter and the Cisco Python SDK are available by default in the Cisco NX-OS Software. The SDK documentation shows how the clid() API can be used when working with JSON and XML. What are two effects of running the script? (Choose two.) A. configure interface loopback 5 B. show details for the TABLE interface C. issue shutdown on interface loopback 5 D. show only the interfaces in the up status E. show only the interfaces in admin shut status Correct Answer: AD
What are two key capabilities of Cisco Finesse? (Choose two.) A. Agents access Finesse from a browser without needing to install or configure anything on the client machine. B. An OpenDNS utility is preconfigured and ready to use on Finesse. C. Gadget containers provide a seamless experience in a single user interface. D. Finesse automatically collects telemetry data. E. Finesse includes an RPC API that enables the development of custom gadgets. Correct Answer: AC
Which two statements are true about Cisco UCS Manager, Cisco UCS Director, or Cisco Intersight APIs? (Choose two.) A. UCS Manager uses JSON to encode API interactions and utilizes Base64-encoded credentials in the HTTP header for authentication. B. UCS Director API interactions can be XML- or JSON-encoded and require an API key in the HTTP header for authentication. C. Cisco Intersight uses XML to encode API interactions and requires an API key pair for authentication. D. UCS Manager API interactions are XML-encoded and require a cookie in the method for authentication. E. Cisco Intersight API interactions can be encoded in XML or JSON and require an API key in the HTTP header for authentication. Correct Answer: BD
Which model-driven programmability protocol does Cisco IOS XE Software support? A. gNMI B. SOAP C. SSH D. CORBA Correct Answer: A
Which API is used to obtain data about voicemail ports? A. Webex Teams B. Cisco unified Communications Manager C. Finesse Gadgets D. Webex Devices Correct Answer: B
Which method should be used to safely store the API keys? A. in an environment variable unique to the system database B. encrypted in a configuration file that is separate from the code C. plain text in the code as a constant D. encrypted in the code in a function Correct Answer: A
Refer to the exhibit.An administrator attempts to perform a GET using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram illustrates the HTTP messages observed. Which change to the API request resolves the issue? A. Remove the "H 'Accept: application/yang-data+json' HTTP header because it is not required. B. Add "'u cisco:cisco' in the end of the cURL command C. Change the request method from "X GET to "X POST D. Add Content-Type HTTP header with 'application/yang-data+json' using "H 'Content-Type: application/yang-data+json' Correct Answer: B
What are two benefits of managing network configuration via APIs? (Choose two.) A. more security due to locking out manual device configuration B. configuration on devices becomes less complex C. eliminates the need of legacy management protocols like SNMP D. reduction in network changes performed manually E. increased scalability and consistency of network changes Correct Answer: DE
Which Cisco DevNet resource allows access to products in a development lab to explore, learn, and build applications that use Cisco APIs? A. DevNet Code Exchange B. DevNet Sandbox C. DevNet Communities D. DevNet Automation Exchange Correct Answer: B
Refer to the exhibits.
A developer is troubleshooting an API with the given API documentation and cURL command. What is the cause of this problem? A. The authorization header is missing or incomplete. B. The request body is missing or incomplete. C. The API token speci ed is expired. D. The user is not allowed to post messages from their account. Correct Answer: A
Which two statements describe the traits of an asynchronous API call? (Choose two.) A. Code execution blocks or waits for the call to an API to return. B. A callback function typically is used to process the response from an API call. C. A call to an API does not block the code, but rather it allows application processing to continue. D. The end user can experience latency or performance lag while waiting for the API call to return. E. The order in which API calls return can be guaranteed. Correct Answer: BC
Which mechanism is used to consume a RESTful API design when large amounts of data are returned? A. data sets B. scrolling C. pagination D. blobs Correct Answer: C
Refer to the exhibit.What caused the error in this API request? A. The API resource does not support the POST operation. B. The submitted JSON payload has a formatting issue. C. The API resource does not support JSON format payloads. D. The submitted JSON payload includes a field that is not supported by the API resource. Correct Answer: B
Which two use cases are supported by Meraki APIs? (Choose two.) A. Build location-aware apps from Wi-Fi and LoRaWAN devices. B. Build a custom Captive Portal for Mobile Apps. C. configure network devices via the Dashboard API. D. Deploy applications onto the devices. E. Retrieve live streams from a Meraki Camera. Correct Answer: BC
What is a difference between a synchronous API and an asynchronous API? A. Synchronous API calls require an authentication header to be sent while asynchronous calls do not require authentication. B. Synchronous API calls are returned immediately while asynchronous calls do not guarantee an immediate response. C. An asynchronous API can make offline calls while synchronous APIs do not have this capability. D. An asynchronous API can make a larger number of calls in a speci ed time period than a synchronous API. Correct Answer: B
Refer to the exhibit. Which command needs to be placed on the box where the code is missing to output the value of page_id in the Python 3.7 script? A. print(items.get('items')[0].get('page_id')) B. print(items.get('items').get('page_id')) C. print(items['items']['page_id'].keys()) D. print(items['items']['page_id']) Correct Answer: B
Refer to the exhibit.The documentation outlines how to use credentials for the AMP API. Which script successfully performs an API call using basic authentication?



Correct Answer: B Correct Answer: B
Refer to the exhibit. A developer creates a Python script that queries Cisco Webex. When the script is executed, a 401 code is returned. After troubleshooting, the developer discovers that the service is missing privileges. Which change to the header in line 4 of the script results in the code 200? A. header = { Authentication : Bearer YOUR_TOKEN } B. header = { Authentication Bearer : YOUR_TOKEN C. header = { Authorization Bearer : YOUR_TOKEN } D. header = { Authorization : Bearer YOUR_TOKEN } Correct Answer: D
In Python, which expression checks whether the script returns a success status code when the Requests library is used? A. response.status_code == requests.codes.ok B. response.code == requests.codes.ok C. response.status_code == requests.ok D. response.status_code != requests.codes.ok Correct Answer: A
Refer to the exhibit. The script returns an output of 401. To use the supplied URL, an HTTP GET request must be sent with an Authorization header. The header value is a base64 encoded concatenation of the username and password. Which action must be taken to return an output of 200? A. Change the verify=False setting in the request to verify=True to enable HTTP Basic authentication. B. Verify that the username and password values imported from the configuration file are still valid. C. Insert an Authorization header with the values username:password from the supplied configuration file. D. Modify the method from LOGIN to GET and supply the username:password value as JSON payload. Correct Answer: D
Refer to the exhibit. A Python code has been written to query a device. The executed code results in the error shown. Which action resolves the problem? A. import json B. requests( GET , base_url + request_url, cookies=cookies) C. pip install requests D. import requests Correct Answer: D
Which REST architectural constraint indicates that no client context should be stored on the server between requests? A. cacheable B. stateless C. uniform interface D. client-server Correct Answer: B
Which HTTP code group is issued when a request is received successfully, understood, and processed? A. 2xx B. 3xx C. 4xx D. 5xx Correct Answer: A
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario? A. Communication between the application and the services is not encrypted. B. The database credentials should be stored in the configuration files so that they are secured on the same server. C. The API keys are stored in the configuration files but should be stored in the vault service. D. The synchronization logs should be encrypted and not stored in a relational database. Correct Answer: A
What is a benefit of version control? A. prevents two users from working on the same file B. keeps track of all changes to the files C. prevents the sharing of files D. keeps the list of data types used in the files Correct Answer: B
Which HTTP response status code means `Forbidden`? A. 500 B. 401 C. 403 D. 502 Correct Answer: C
Refer to the exhibit. What does the command marked (2) do when it is run? A. It duplicates the test branch. B. It deletes the test branch only if a new branch is created. C. It deletes the test branch. D. It does not delete the branch until it is merged. Correct Answer: C
What is a comparison of YAML and JSON? A. YAML has a more consistent approach to representing data compared to JSON. B. JSON does not support comments and YAML does. C. YAML is a more verbose data structure compared to JSON. D. JSON has more common usage in configuration management tools compared to YAML. Correct Answer: B
Which status code is used by a REST API to indicate that the submitted payload is incorrect? A. 400 B. 403 C. 405 D. 429 Correct Answer: A
An application calls a REST API and expects a result set of more than 550 records, but each time the call is made, only 25 are returned. Which feature limits the amount of data that is returned by the API? A. pagination B. payload limit C. service timeouts D. rate limiting Correct Answer: A
A developer is writing an application that uses a REST API and the application requires a valid response from the API. Which element of the response is used in the conditional check? A. body B. headers C. link D. URL E. status code Correct Answer: E
Refer to the exhibit.A REST API returns this JSON output for a GET HTTP request, which has been assigned to a variable called `vegetables`. Using Python, which output is the result of this command? print( filter(lambda 1: 1['type'] == 'fruit', vegetables) [0]['items'][0]['items'][0]) A. {'color': 'green', 'items': ['kiwi', 'grape']} B. ['kiwi', 'grape'] C. lettuce D. kiwi Correct Answer: D
A 401 HTTP response code is returned when calling a REST API. What is the error state identified by this response code? A. The server cannot process the request as it has detected an issue in the request syntax or body. B. The request has not been accepted because it requires authentication. C. The sever accepted the request but the client is not authorized for this content. D. The server cannot find the requested resource because the path speci ed is incorrect. 101/#:~:text=A%20401%20error%20response%20indicates,credentials%20or%20none%20at%20all Community vote distribution Correct Answer: B
A developer is creating a script to interact with a REST API service which requires basic authentication. The credentials are "devnet:391665405" and the Base64 encoding of the credentials is "GV2bmV0dXNlcjpDaXNj=". Which payload and header combination must be used for authentication?


Correct Answer: B Correct Answer: B
A developer needs a list of clients connected to a specific device in a Meraki network. After making a REST API call, the developer receives an unfamiliar response code. Which Cisco DevNet resource should be used to identify the meaning of the response code? A. API documentation B. Code Exchange C. Learning Labs D. Sandbox Correct Answer: A
A developer is trying to retrieve data over a REST API. The API server responds with an HTTP client error response code. After investigating the response, the developer realizes the response has a Retry-After header. What is the root cause of this error? A. An appliance limited the rate of requests to the transport layer. B. The REST service is unreachable at the time of the REST request. C. Too many requests were sent to the REST service in a given amount of time. D. An appliance limited the rate of requests to the application layer. Correct Answer: C
Refer to the exhibit.A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get a valid response? A. change content-type as JSON B. add the authorization header with the access token C. and a username-password combination to request command D. change request method as GET Correct Answer: B
Which action resolves a 401 error in response to an HTTP GET that is issued to retrieve a configuration statement using RESTCONF on a CSR 1000V? A. Change the HTTP method to PUT. B. Check the MIME types in the HTTP headers. C. Change the transport protocol to HTTPS. D. Check the authentication credentials. Correct Answer: D
Refer to the exhibit.An API call is constructed to retrieve the inventory in XML format by using the API. The response to the call is 401 Unauthorized. Which two headers must be added to the API call? (Choose two.) A. Bearer-Token: dXNlcm5hbWU6cGFzc3dvcmQ= B. Content-Type: application/xml C. Authentication: Bearer dXNlcm5hbWU6cGFzc3dvcmQ= D. Accept: application/xml E. Authorization: Bearer dXNlcm5hbWU6cGFzc3dvcmQ= Correct Answer: DE
Which HTTP response code should be returned when the request is completed, but there is no content to send for the request? A. 100 B. 204 C. 302 D. 402 Correct Answer: B
Refer to the exhibit. Which data is speci ed in the response header? A. Content-Type B. HTTP/1.1 200 OK C. type : switch D. { id : a123456bcde , HTTP/1.1 200 OK status : online , type : switch } Correct Answer: A
What are two use cases where webhooks are effective? (Choose two.) A. Filter out information from a response to an API call. B. Close a session with a web server after a specific amount of time. C. Inform a previously defined chat channel after a deployment fails. D. Send an email to a customer of an online store after payment is complete. E. Change the response format or content type of an API call. Correct Answer: BD
In which two ways is an application characterized when interacting with a webhook? (Choose two.) A. receiver B. transaction monitor C. codec D. processor E. listener Correct Answer: AE
How does requesting a synchronous API operation differ from requesting an asynchronous API operation? A. clients receive responses with a task ID for further processing B. clients subscribe to a webhook for operation results C. clients poll for the status of the execution of operations D. clients can access the results immediately Correct Answer: D
Which two encoding formats do YANG interfaces support? (Choose two.) A. XML B. JSON C. XHTML D. fiber E. plain text Correct Answer: AB
Which action does the Git command git merge allow the developer to perform? A. Combine multiple sequences of commits into one unified history B. Push changes to the remote repository C. Create, list, rename, and delete branches D. Switch between branches Correct Answer: A
How does a developer create and switch to a new branch called `my-bug- x` to develop a product x? A. git checkout -b my-bug- x B. git branch -b my-bug- x C. git branch my-bug- x D. git checkout my-bug- x Correct Answer: A
A developer needs to prepare the file READM A. md in the working tree for the next commit operation using Git. Which command needs to be used to accomplish this? B. git -a READM C. md D. git add READM E. md F. git add READM G. md staging H. git commit READM Correct Answer: B
A developer is reviewing a code that was written by a colleague. It runs ne, but there are many lines of code to do a seemingly simple task repeatedly. Which action organizes the code? A. Refactor the code by removing any unnecessary tests. B. Reverse engineer and rewrite the code logic. C. Using functions, rewrite any pieces of code that are repeated. D. Modify the code to use loops. Correct Answer: C
Which principle is a value from the manifesto for Agile software development? A. processes and tools over teams and interactions B. detailed documentation over working software C. adhering to a plan over responding to requirements D. customer collaboration over contract negotiation Correct Answer: D
Which advantage does the agile process offer compared to waterfall software development? A. to add or update features with incremental delivery B. to view the full scope of end-to-end work C. to have each phase end before the next begins D. to fix any issues at the end of the development cycle Correct Answer: A
How do XML and JSON compare regarding functionality? A. XML provides more support for mapping data structures into host languages than JSON. B. XML provides more human readability than JSON. C. JSON provides less support for data types than XML. D. JSON natively supports arrays and XML does not natively support arrays. Correct Answer: D
What are two principles of an infrastructure as code environment? (Choose two.) A. Components are coupled, and definitions must be deployed for the environment to function. B. Redeployments cause varying environment definitions. C. Environments must be provisioned consistently using the same inputs. D. Service overlap is encouraged to cater for unique environment needs. E. Complete complex systems must be able to be built from reusable infrastructure definitions. Correct Answer: CE
Refer to the exhibit.The JSON data in the exhibit has been parsed and stored into a variable `data`. What returns the value `172.16.0.11`? A. data['items']['host']['value'] B. data['items'][1]['host']['value'] C. data['items'][0]['host']['value'] D. data['items']['host'][1] Correct Answer: C
Refer to the exhibit.What does the Python function do? A. It returns HTTP Basic Authentication. B. It returns DNAC user and password. C. It reads a token from a local JSON file and posts the token to the DNAC URL. D. It returns an authorization token. Correct Answer: A
Package updates from a local server fail to download. However, the same updates work when a much slower external repository is used. Why are local updates failing? A. The server is running out of disk space. B. The Internet connection is too slow. C. The Internet is down at the moment, which causes the local server to not be able to respond. D. The update utility is trying to use a proxy to access the internal resource. Correct Answer: D
What is a functionality of the Waterfall method as compared to the Agile method for software development? A. Waterfall increases agility to implement faster while Agile promotes reliability. B. A phase begins after the previous phase has ended in Waterfall while Agile phases run in parallel. C. Customers get feedback during the process in Waterfall while they can see the result at the end in Agile. D. Requirements can be updated in Waterfall while in Agile it should be gathered in the beginning. Correct Answer: B
What is a benefit of using functions in the code for the development process? A. better user experience in the end product B. improves code performance C. easier to compile the code D. faster code development Correct Answer: D
What is the difference between YAML and JSON data structure? A. YAML uses spaces; JSON uses parentheses B. YAML uses indentation; JSON uses brackets and braces C. YAML uses brackets and braces; JSON uses indentation D. YAML uses parentheses; JSON uses spaces Correct Answer: A
A developer is working on a feature for a new application. The changes in the existing branch named 'feat00304' must be integrated into a single commit with the current working primary branch named 'prodapp411926287'. Which git command must be used? A. git rebase --merge feat00304 B. git merge --squash feat00304 C. git push --rebase feat00304 D. git checkout --squash feat00304 Correct Answer: B
A file that already exists in a local repository is updated. Which command must be executed to ensure that the changes in the file are included in the next Git commit? A. git update B. git merge C. git add D. git rebase Correct Answer: A
Into which type of Python data structure should common data formats be parsed? A. sequence B. set C. dictionary D. list Correct Answer: C
Several teams at a company are developing a new CRM solution to track customer interactions with a goal of improving customer satisfaction and driving higher revenue. The proposed solution contains these components: * MySQL database that stores data about customers * HTML5 and JavaScript UI that runs on Apache * REST API written in Python What are two advantages of applying the MVC design pattern to the development of the solution? (Choose two.) A. to enable multiple views of the same data to be presented to different groups of users B. to provide separation between the view and the model by ensuring that all logic is separated out into the controller C. to ensure data consistency, which requires that changes to the view are also made to the model D. to ensure that only one instance of the data model can be created E. to provide only a single view of the data to ensure consistency Correct Answer: BD
Refer to the exhibit. Which XML snippet has interface information that conforms to the YANG model?



Correct Answer: A Correct Answer: A
Which two concepts describe test-driven development? (Choose two.) A. User acceptance testers develop the test requirements. B. It enables code refactoring. C. Tests are created when code is ready for release. D. Implementation is driven by incremental testing of release candidates. E. Write a test before writing code. Correct Answer: BE
Which task is performed because the test-driven development approach is being used? A. creating test scenarios based on continuous development B. writing code without committing any coding violations C. refactoring code that is covered by existing tests D. testing existing software before developing new code Correct Answer: C
What is the first development task in test-driven development? A. Write code that implements a desired function. B. Write a failing test case for a desired function. C. Reverse engineer the code for a desired function. D. Write a passing test case for existing code. Correct Answer: B
In test-driven development, what are two of the green bar patterns? (Choose two.) A. another test B. break C. triangulate D. starter test E. fake it Correct Answer: CE
In the test-driven development model, what is changed after a test fails? A. schedule B. project requirements C. code D. test Correct Answer: C
What is a benefit of test-driven development? A. strict adherence to product requirements B. faster releases that have minimal features C. early customer involvement D. increased code quality Correct Answer: A
Which two statements describe the advantages of using a version control system? (Choose two.) A. It allows for branching and merging so that different tasks are worked on in isolation before they are merged into a feature or master branch. B. It provides tooling to automate application builds and infrastructure provisioning. C. It allows multiple engineers to work against the same code and configuration files and manage differences and conflicts. D. It provides a system to track User Stories and allocate to backlogs. E. It allows developers to write effective unit tests. Correct Answer: AC
What are two advantages of version control software? (Choose two.) A. It supports tracking and comparison of changes in binary format files. B. It allows new team members to access the current code and history. C. It supports comparisons between revisions of source code files. D. It provides wiki collaboration software for documentation. E. It allows old versions of packaged applications to be hosted on the Internet. Correct Answer: BC
Before which process is code review performed when version control is used? A. checkout of code B. merge of code C. committing code D. branching code Correct Answer: B
What is an advantage of a version control system? A. facilitates resolving conflicts when merging code B. ensures that unit tests are written C. prevents over-writing code or configuration files D. forces the practice of trunk-based development Correct Answer: A
Refer to the exhibit.Which Python data structure does my_json contain? A. map B. list C. json D. dict Correct Answer: D
When a Cisco IOS XE networking device is configured using RESTCONF, what is the default data-encoding method? A. JSON B. YAML C. XML D. x-form-encoding Correct Answer: A
Refer to the exhibit.Which JSON is equivalent to the XML-encoded data?



Correct Answer: B Correct Answer: B
Which two statements about JSON and XML are true? (Choose two.) A. The syntax of JSON contains tags, elements, and attributes. B. XML objects are collections of key-value pairs. C. JSON objects are collections of key-value pairs. D. JSON arrays are an unordered set of key-value pairs. E. The syntax of XML contains tags, elements, and attributes. Correct Answer: CE
Which statement describes the benefit of using functions in programming? A. Functions ensure that a developer understands the inner logic contained before using them as part of a script or application. B. Functions create the implementation of secret and encrypted algorithms. C. Functions allow problems to be split into simpler, smaller groups, and reduce code repetition, which makes the code easier to read. D. Functions store mutable values within a script or application. Correct Answer: C
Refer to the exhibit.The output of a unified diff when comparing two versions of a Python script is shown. Which two `single_request_timeout()` functions are defined in sh.py and cat.py? (Choose two.)




Correct Answer: BC Correct Answer: BC
What is the Git command to delete a local branch named `experiment` without a warning? A. git branch "rm experiment B. git branch "n experiment C. git branch "f experiment D. git branch "D experiment Correct Answer: D
What is the outcome of executing this command? git clone ssh:/john@example.com/path/to/my-project.git A. creates a local copy of a repository called my-project B. initiates a new Git repository called my-project C. creates a copy of a branch called my-project D. creates a new branch called my-project Correct Answer: A