IT Exam Questions and Solutions Library
Which type of service provider is responsible for secure, private connections between data centers, access regions, and cloud providers in Cisco SD-WAN Multi-Region Fabric? A. distributed network providers B. middle-mile network providers C. last-mile network providers D. first-mile network providers Suggested Answer: B
Refer to the exhibit. The SD-WAN network is configured with a default full-mesh topology. The SD-WAN engineer wants the Barcelona WAN Edge to use the MPLS TLOC as the preferred TLOC when communicating with the Rome site. Which configuration must the engineer use to create a list to select MPLS color toward the Rome TLOC? A.
B.
C.
D.
Suggested Answer: D
DRAG DROP - Drag and drop the phases of TrustSec from the left onto the targets on the right. Not all options are used.Suggested Answer:

Which application list is preconfigured? A. Cisco_Apps B. P2P_Apps C. Microsoft_Office365 D. Google_Apps Suggested Answer: D
DRAG DROP - Drag and drop the steps from the left into the sequence on the right for a WAN Edge router after powering on for zero touch provisioning.Suggested Answer:

The application team is getting ready to deploy a new business-critical application to the network. To protect the traffic, the network team must add another queue to the QoS map and then deploy the map to the fabric. Which configuration step must be completed prior to adding the queue to the QoS map and applying it? A. The relationship between the new QoS class and the hardware queue must be configured from the "lists" page of the Local Policy section of vManage. The QoS map is then applied to the WAN interface. B. The relationship between the new QoS class and the hardware queue must be configured from the "lists" page of the Local Policy section of vManage. The QoS map is then applied to the service-side interface. C. The relationship between the new QoS class and the hardware queue must be configured from the "lists" page of the Centralized Policy section of vManage. The QoS map is then applied to the service-side interface. D. The relationship between the new QoS class and the hardware queue must be configured from the "lists" page of the Centralized Policy section of vManage. The QoS map is then applied to the WAN interface. Suggested Answer: C
Which protocol runs between the vSmart controllers and WAN Edge routers when the vSmart controller acts like a route reflector? A. IPsec inside the DTLS/TLS control connection B. BGP inside the DTLS/TLS C. OMP outside the DTLS/TLS control connection D. OMP inside the DTLS/TLS control connection Suggested Answer: D
Which protocol does vManage use to provision the WAN Edge device during the onboarding process? A. RESTCONF B. NETCONF C. EPP D. HTTPS Suggested Answer: B
What is the BFD multiplier in application-aware routing? A. 6 B. 7 C. 8 D. 9 Suggested Answer: B
Which platform is a Cisco SD-WAN virtual platform? A. Cisco ASR 1000 B. Cisco Nexus 1000V C. Cisco CSR 1000V D. Cisco ISR 4000 Suggested Answer: C
A customer has two branch sites with overlapping IPs. How must the data policy be configured to establish communication between the sites and server to avoid overlapping?
A.
 B.
B.
 C.
C.
 D.
D.
 Suggested Answer: A
Suggested Answer: A
Which configuration allows VPN 10 traffic to have direct internet access locally from the WAN Edge device?
A.
 B.
B.
 C.
C.
 D.
D.
 Suggested Answer: C
Suggested Answer: C
What is a requirement for deployment of on-premises vBond controllers through the Cisco Plug and Play Connect process? A. a defined controller profile B. a DNS name that identifies vBond C. Internet connectivity from vManage D. a CSV file that contains all controllers Suggested Answer: B
How is vBond reachability resolved by vManage? A. IPsec B. DNS C. BGP D. OMP Suggested Answer: B
Refer to the exhibit. A user has selected the options while configuring a VPN Interface Ethernet feature template. What is the required configuration parameter the user must set in this template for this feature to function? A. The "Shaping Rate (Kbps)" field must be configured with a value. B. The "IP MTU" field must be increased from the default value of 1500 to support the additional overhead. C. The "Bandwidth Downstream" field must be configured with a value. D. The "Adaptive QoS" field must be set to "on". Suggested Answer: C
Which SD-WAN devices require multicast PIM and IGMP configurations when setting up SD-WAN multicast? A. datacenter replicator devices B. datacenter devices with multicast sources C. branch devices with multicast receivers D. branch devices with unicast traffic Suggested Answer: C
An engineer is modifying an existing data policy for VPN 115 to meet these additional requirements: • When browsing government websites, the traffic must use direct internet access. • The source address of the traffic leaving the site toward the government websites must be set to an IP range associated with the country itself, a particular TLOC. The policy configuration is as follows:A.
B.
C.
D.
Suggested Answer: C
What problem happens on a device with two serial numbers, a unique device identifier (UDI), and a secure unique device identifier (SUDI) when an engineer provisions ISR 4000 by PnP using only a UDI? A. It faces interface buffer overflow problems. B. It encounters memory overload problems. C. It encounters spanning tree issues. D. It encounters redirection problems. Suggested Answer: D
What is a key element used in a vBond Orchestrator redundancy topology? A. load-balancer with health probes B. DHCP server C. fully qualified domain name D. stun server Suggested Answer: C
What is one way an SD-WAN Edge router originates a vRoute? A. learned from OSPF intra-area B. learned from BGP C. from TLOCs connected to the WAN transports D. from the vBond controller Suggested Answer: C
Which signature sets are available in vManage under the security policy configuration for IPS? A. Connectivity, Balanced, Security B. Malware, Blacklist, Connectivity C. Malware, Security, Connectivity D. Blacklist, Balanced, Security Suggested Answer: A
Which Cisco SD-WAN configuration provides the advantages of day-zero deployment and reusable configuration components? A. configuration groups B. configuration via the vBond controller C. configuration through a Cisco Prime server D. CLI-based templates Suggested Answer: A
What is the role of the Session Traversal Utilities for NAT server provided by the vBond orchestrator? A. It prevents SD-WAN Edge routers from forming sessions with public transports among different service providers. B. It facilitates SD-WAN Edge routers to stay behind a NAT-enabled firewall while the transport addresses of the SD-WAN controller are unNAT-ed. C. It allows WAN Edge routers to form sessions among MPLS TLOCs using only public IP addresses. D. It facilitates SD-WAN routers and controllers to discover their own mapped or translated IP addresses and port numbers. Suggested Answer: D
How many network interface cards are needed to add in virtual machine settings when installing vSmart controller on VMware vSphere ESXi Hypervisor software? A. 1 B. 2 C. 3 D. 4 Suggested Answer: B
What is the purpose of a TLOC extension interface? A. gives access to business Internet B. provides access to the transport of its neighboring WAN Edge router C. forms an alternate connection to connected transport D. synchronizes the configuration with the neighboring WAN Edge router Suggested Answer: B
Which REST API call is used for real-time monitoring of application-aware routing? A. history B. SLA class C. event D. alarm Suggested Answer: C
Refer to the exhibit. A WAN Edge router is configured with SLAs. Which TLOC does the traffic take if the internet TLOC has latency 100 ms, loss 2%, jitter 50ms, and the MPLS TLOC has latency 50 ms, loss 1%, and jitter 150 ms? A. MPLS B. internet C. MPLS or internet D. drop Suggested Answer: A
Which two types of SGT propagation are supported by Cisco TrustSec? (Choose two.) A. key chain B. offline tagging C. SXP D. reconciliation E. inline tagging Suggested Answer: CE
An engineer configured a data policy called ROME-POLICY. Which configuration allows traffic flow from the Rome internal network toward other sites?
A.
 B.
B.
 C.
C.
 D.
D.
 Suggested Answer: A
Suggested Answer: A
Which configuration component is used in a firewall security policy? A. intrusion prevention policy B. numbered sequences of match-action pairs C. application match parameters D. URL filtering policy Suggested Answer: B
DRAG DROP - Drag and drop the steps from the left into the order on the right to delete a software image for a WAN Edge router starting with Maintenance > Software Upgrade > Device list on vManage.Suggested Answer:

Which capability does Cisco SD-WAN Multi-Region Fabric provide? A. end-to-end SLA-aware routing B. overlay support for IP multicast C. assignment of a single vSmart controller to handle region 0 and noncore regions D. end-to-end encryption for inter-region traffic Suggested Answer: D
How do WAN Edge devices operate when vSmart is inaccessible or fails to be reached by the WAN Edge? A. They continue operation normally. B. They continue operating normally for a configurable time. C. They continue to receive reachability updates. D. They cease to forward traffic in the data plane. Suggested Answer: B
What is the size of SGT data in the metadata header? A. 8 bits B. 16 bits C. 24 bits D. 32 bits Suggested Answer: B
A network engineer sets tags in OMP for routes that were originated in the Service VPN. Which monitoring tab must be used to verify tags on the next hop? A. Troubleshooting > Simulate Flows B. Realtime > OMP Received TLOCs C. Troubleshooting > Tunnel Health D. Realtime > OMP Received Routes Suggested Answer: D
What are the two advantages of configuration groups in a Cisco SD-WAN deployment? (Choose two.) A. An individual device has multiple tag rules. B. Individual devices are grouped based on a shared configuration. C. Individual devices are added to multiple groups. D. A subset of devices is identified with tags. E. Individual devices are associated with a configuration group and a device template. Suggested Answer: BD
Which controller is used for provisioning and configuration in a Cisco SD-WAN solution? A. vManage B. vBond C. WAN Edge router D. vSmart Suggested Answer: A
How many cloud gateway instance(s) can be created per region when provisioning Cloud OnRamp for Multicloud from AWS in a multiregion environment? A. one B. two C. three D. four Suggested Answer: A
What is the result during a WAN Edge software upgrade process if the version of the WAN Edge software is higher than the one running on a controller device? A. The upgrade button is greyed out. B. The upgrade fails with a warning message. C. The upgrade proceeds with a warning message. D. The upgrade proceeds with no warning message. Suggested Answer: B
What does forward error correction addresses in Cisco SD-WAN? A. reduced application performance degradation related to service degradation B. applications with occasional invalid data input and poor performance C. traffic flows with increased delay over a particular transport D. inefficient traffic forwarding caused by inbound shapers Suggested Answer: B
Which process is continued by Cisco SD-WAN when packet duplication is enabled? A. Additional headers are added to outgoing packets to perform custom routing policies. B. Dynamic traffic is compressed and signaled before it is forwarded though the WAN. C. Copies of packets are sent over multiple WAN circuits to overcome packet loss. D. Application traffic is analyzed to find patterns and enable custom detection rules. Suggested Answer: C
What is the function of the AppNav Controller in the Cisco SD-WAN AppNav solution? A. It provides information about configured optimization policies on SD-WAN edge devices. B. It accelerates specific traffic based on preconfigured policies. C. It intercepts and distributes network traffic based on configured policies. D. It provides configuration and monitoring for WAAS nodes. Suggested Answer: C
Which set of platforms must be in separate VMs as of release 16.1? A. vManage and vSmart B. vSmart and WAN Edge C. vBond and vSmart D. WAN Edge and vBond Suggested Answer: C
DRAG DROP - Drag and drop key features from the left onto the corresponding firewall type on the right.Suggested Answer:

Which two advanced security features are available on the Cisco SD-WAN WAN Edge (vEdge) device? (Choose two.) A. Cisco Umbrella DNS Security B. Enterprise Firewall C. snort intrusion prevention system D. Cisco AMP and AMP Threat Grid E. URL filtering Suggested Answer: BD
What are three types of data that JSON uses when Cisco APIC REST API uses JavaScript? A. GET, PUT, and DELETE B. SCALAR, OBJECT, and ARRAY C. GET, PUT, and POST D. SCALAR, POST, and OBJECT Suggested Answer: B
Drag and drop the REST API calls from the left onto the functions on the right. Select and Place:
Correct Answer:
Drag and drop the Cisco SD-WAN components from the left onto their functions on the right. Select and Place:Correct Answer:

Drag and drop the security terminologies from the left onto the PCI-compliant network features and devices on the right. Select and Place:
Correct Answer:
Drag and drop the alarm states from the left onto the corresponding alarm descriptions on the right. Select and Place:Correct Answer:
Drag and drop the devices from the left into order on the right to upgrade the software from version 19 to version 20. Select and Place:
Correct Answer:
Drag and drop the devices from the left onto the correct functions on the right. Select and Place:
Correct Answer:
Drag and drop the components from the left onto the corresponding Cisco NFV Infrastructure Building Blocks on the right. Not all options are used. Select and Place:
Correct Answer:
Drag and drop the BFD parameters from the left onto the BFD configurations on the right. Select and Place:
Correct Answer:
Drag and drop the vManage policy configuration procedures from the left onto the correct definitions on the right. Select and Place:Correct Answer:

Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used. Select and Place:
Correct Answer:
Drag and drop the policies from the left onto the policy types on the right. Select and Place:
Correct Answer:
Drag and drop the actions from the left into the correct sequence on the right to create a data policy to direct traffic to the Internet exit. Select and Place:
Correct Answer:
Drag and drop the functions from the left onto the correct templates on the right. Select and Place:
Correct Answer:
Drag and drop the definitions from the left to the configuration on the right. Select and Place:Correct Answer:
%E2%80%94A%20grouping%20of,part%20of%20only%20one%20zone.&text=A%20VPN%20can%20be%20part%20of%20only%20one%20zone.,- Firewall%
Drag and drop the route verification output from show omp tlocs from the left onto the correct explanations on the right. Select and Place:
Correct Answer:
Drag and drop the steps from the left into the order on the right to upload software on vManage repository that is accessible from Maintenance > Software Repository. Select and Place:Correct Answer:

What is the size of SGT data in the metadata header? A. 8 bits B. 16 bits C. 24 bits D. 32 bits Correct Answer: B
Which service VPN must be reachable from all WAN Edge devices and the controllers? A. VPN0 B. VPN10 C. VPN215 D. VPN512 Correct Answer: B
What is the function of colocation in Cloud OnRamp SaaS? A. In Cloud OnRamp, colocation supports the capability of virtualizing access-only locations and using colocation centers that require the customer to extend to the cloud. B. Cloud OnRamp incorporates regional colocation facilities by choosing between cloud access points at the remote site and regional cloud access points at the colocation facilities. C. With colocation facility in Cloud OnRamp, the customer faces challenges to virtualize the security and optimization infrastructure that influence traffic through network elements. D. The Cloud OnRamp for colocation solution restricts the creation of different VNF service chains orchestrated in Cisco vManage and deployed on a cluster in a colocation facility. Correct Answer: B
What are the two impacts of losing vManage connectivity to fabric in the Cisco SD-WAN network? (Choose two.) A. Policy changes propagation stops. B. Creation of templates is impossible. C. BFD peering between WAN Edge devices are established. D. Statistics collection stops. E. IPsec tunnels tear down for WAN Edge devices. Correct Answer: AD
Refer to the exhibit.A vBond controller was added to the controller list with the same Enterprise Root CA certificate as vManage. The two controllers can reach each other via VPNO and share the same organization name, but the control connection is not initiated. Which action resolves the issue? A. configure a valid vBond IP on vManage. B. Synchronize the WAN Edge list on vManage with controllers. C. configure NTP on both controllers to establish a connection. D. configure a valid system IP on the vBond controller. Correct Answer: A
Which type of connection is created between a host VNet and a transit VNet when configuring Cloud OnRamp for lease? A. GRE tunnel B. Azure peer link C. IPsec turtle D. Azure private endpoint Correct Answer: C
Refer to the exhibit.Which two configurations are needed to get the WAN Edges registered with the controllers when certificates are used? (Choose two.) A. Install the certificate received from the CA server manually on the WAN Edge. B. Generate a CSR manually within vManage server. C. Generate a CSR manually on the WAN Edge. D. Install the certificate received from the CA server manually on the vManage. E. Request a certificate manually from the Enterprise CA server. Correct Answer: BD
In which Cisco SD-WAN deployment scenario does Cisco Umbrella SIG deliver the most value? A. when Cisco IOS XE SD-WAN devices are deployed throughout the network B. when resource-intensive security operations are o oaded from entry-level WAN Edge devices C. when the identity of several WAN Edge devices is verified throughout the network D. when a centralized Internet breakout solution is implemented Correct Answer: D
Which capability does Cisco SD-WAN Multi-Region Fabric provide? A. end-to-end SLA-aware routing B. overlay support for IP multicast C. assignment of a single vSmart controller to handle region 0 and noncore regions D. end-to-end encryption for inter-region traffic Correct Answer: D
Which VPN must be present on at least one interface to install Cisco vManage and integrate it with WAN Edge devices in an overlay network site ID:S0123T4E56F78? A. VPN 512 B. any VPN number selected C. services VPN range 0-511 D. VPN 0 Correct Answer: D
A network administrator configures SNMPv3 on a Cisco WAN Edge router from CLI for monitoring purposes. How many characters are supported by the snmp user command? A. from 1 to 8 B. from 1 to 16 C. from 1 to 32 D. from 1 to 48 Correct Answer: C
Which two actions are necessary to set the Controller certificate Authorization mode to indicate a root certificate? (Choose two.) A. Select a private certificate signing authority instead of a public certificate signing authority. B. Change the organization name of the Cisco SD-WAN fabric. C. Select the Controller certificate Authorization mode that is recommended by Cisco. D. Upload an SSL certificate to vManage. E. Select a validity period from the drop-down menu. Correct Answer: AD
Which component is used for stateful inspection of TCP, UDP, and ICMP ows in Cisco SD-WAN firewall policies? A. subnets B. sites C. interfaces D. zones Correct Answer: D
An engineer must create a QoS policy by creating a class map and assigning it to the LLQ queue on a WAN Edge router. Which configuration accomplishes the task?


A. Correct Answer: D
Which compression algorithm does DRE use in a Cisco SD-WAN environment? A. Lempel-Ziv-Welch encoding B. Huffman encoding C. run-length encoding D. Ziv Huffman encoding Correct Answer: B
Which topology type is supported in each noncore region in a Cisco SD-WAN Multi-Region fabric environment with three or more regions? A. any topology type B. full mesh and partial mesh C. hub and spoke D. full mesh Correct Answer: D
What two functions describe the TCP optimization tool used in the Cisco SD-WAN? (Choose two.) A. It uses TCP acknowledgment (ACK). B. It uses TCP selective acknowledgment (SACK). C. It terminates TCP connections locally at the WAN edge. D. It terminates TCP connections at the remote WAN edge E. It is used to take care of high packet loss for control traffic. Correct Answer: BC
Which component creates a feature profile using a structured approach to configuring Cisco SD-WAN in UX 2.0? A. feature template B. feature parcel C. configuration group D. device template Correct Answer: C
Which two different states of a WAN Edge certificate are shown on vManage? (Choose two.) A. active B. inactive C. staging D. provisioned E. invalid Correct Answer: CE
An engineer creates a data policy to prevent communication from the 172.20.21.0/24 network to the 172.20.41.0/24 network. Which configuration accomplishes this task?


A. Correct Answer: D
Refer to the exhibit.The network team must configure application-aware routing for the Service VPN 50.0.0.0/16. The SLA must prefer MPLS for video traffic, but the remaining traffic must use a public network. What must be defined other than applications before the application-aware policy is created? A. Color, SLA Class, Site, VPN B. Data prefix, Site, VPN, TLOC C. Application, SLA, VPN, prefix D. SLA Class, Site, VPN, prefix Correct Answer: C
An engineer must configure VRRP for redundancy on WAN Edge router 1 running an earlier version than 20.6, considering WAN Edge router2 is configured correctly. Which configuration meets the requirement?


A. Correct Answer: D
Which set of key security components of authentication, encryption, and integrity is used to establish an IPsec tunnel in the Cisco SD-WAN solution? A. Authentication is 1024-bit key; encryption is AES-128 cipher, and integrity is ESP, HMAC-MD5. B. Authentication is 1024-bit key; encryption is AES-256 cipher, and integrity is ESP, HMAC-MD5. C. Authentication is 2048-bit key; encryption is AES-256 cipher, and integrity is ESP, HMAC-SHA1. D. Authentication is 2048-bit key; encryption is AES-128 cipher, and integrity is ESP, HMAC-SHA1. Correct Answer: C
Which VPNs must be configured outside the work flow to complete the SD-WAN overlay setup when using the Quick Connect work flow? A. service VPNs B. transport VPNs C. service and transport VPNs D. management VPNs Correct Answer: A
Refer to the exhibit.An engineer configures Rome WAN Edge to use MPLS cloud as the preferred link to reach Paris WAN Edge and use biz-internet as a backup. Which policy configuration must be applied in the outbound direction toward Rome to accomplish the task?



A. Correct Answer: D
How many vBond controllers must be installed when vManager is installed in a multitenancy environment for four tenants? A. One vBond controller is shared between the tenants. B. Multitenancy deployment requires three vBand controllers. C. Each tenant requires two vBond controllers for redundancy. D. Each tenant requires a dedicated vBond controller. Correct Answer: D
What is the advantage of installing the controller on-premises? A. automatic geographical redundancy and security B. full control of the data plane and the control plane C. scalability and a cost-saving D. ease of deployment and management Correct Answer: B
How many concurrent sessions does a vManager REST API have before it invalidates the least recently used session if the maximum concurrent session number is reached? A. 150 B. 200 C. 250 D. 300 Correct Answer: C
An engineer creates this data policy for DIA for VPN 10:Which policy sequence enables DIA for external networks?



A. Correct Answer: C
An engineer must avoid routing loops on the SD-WAN fabric for routes advertised between data center sites. Which BGP loop prevention attribute must be configured on the routers to meet this requirement? A. static routing on all WAN Edge routers instead of BGP B. same BGP AS between all CE and PE routers C. same OMP overlay-as on WAN Edge routers of all data centers D. same BGP AS between all WAN Edge routers and CE routers Correct Answer: B
Which routing protocol has the highest default administrative distance? A. IS-IS B. OMP C. IBGP D. external EIGRP Correct Answer: B
How should the IP addresses be assigned for all members of a Cisco vManager cluster located in the same data center? A. in overlapping IPs B. in different subnets C. in the same subnet D. in each controller with a /32 subnet Correct Answer: C
What are the two functions of smart? (Choose two.) A. It ensures that valid WAN Edge routers can build the control plane connectivity. B. It validates that the WAN Edge trying to join the overlay is authorized to join. C. It orchestrates connectivity between WAN Edge routers using policies to create network topology. D. It uses TLOCs to uniquely identify the circuit interface to control plane and data plane information. E. It builds control plane connections with WAN Edge routers using TLS or DTLS. Correct Answer: BC
Refer to the exhibit.Company ABC has a hub-and-spoke topology in place and currently is load balancing their data traffic at the hub site over MPLS and the public Internet. The leased circuit must be preferred over the shared circuit. Which configuration meets the requirement?



Correct Answer: B Correct Answer: B
Which encryption algorithm is used for encrypting SD-WAN data plane traffic? A. AES-256 GCM B. Triple DES C. AES-128 D. IPsec Correct Answer: A
Refer to the exhibit.Which configuration must the engineer use to form underlay connectivity for the Cisco SD-WAN network?



A. D Correct Answer:
A WAN Edge device has several service VPNs with no routing protocol configured in the service VPNs. The device must be configured so that all connected routes are visible in OMP for VPN 10. Which configuration meets the requirement?


A. Correct Answer: D
Which TLOC color is used for site-to-site communication in a Google Cloud integration with Cisco SD-WAN? A. private1 B. private2 C. private3 D. private4 Correct Answer: A
Refer to the exhibit.A network administrator is configuring OSPF advanced configuration parameters from a template using the vManager GUI for a branch WAN Edge router to calculate the summary routes to an ASBR. Which action achieves this configuration? A. Enable Originate. B. Disable RFC 1583 Compatible. C. Disable Originate. D. Enable RFC 1583 Compatible. Correct Answer: D
Refer to the exhibit.An engineer must configure a QoS policy between the hub and site A (spoke) over a standard Internet circuit where traffic shaping is adjusted based on available bandwidth. Which configuration meets the requirement?



A. Correct Answer: D
How are policies deployed on cloud-hosted Cisco SD-WAN controllers? A. Policies are created on vManage and enforced by vManage. B. Policies are created on vSmart and enforced by vManage. C. Policies are created on vManage and enforced by vSmart. D. Policies are created on vSmart and enforced by vSmart. Correct Answer: C
Which REST API call checks the status of an action that is performed on a device? A. admin status B. troubleshoot status C. configuration status D. monitor status Correct Answer: C
Which two actions must be taken to allow certain department to require firewall protection when interacting with data center networks without including other departments? (Choose two.) A. Use classification, policing, and marking B. Advertise to vSmart controllers. C. The regional hub advertises the availability of the firewall service. D. Apply data policies at vEdge. E. Deploy a service-chained firewall service per VPN. Correct Answer: AE
Which behavior describes a WAN Edge router running dual DIA when its DPI engine has identified a cloud SaaS application? A. The gateway WAN Edge router DPI engine accepts the DNS query for SaaS applications, and DNS queries for noncloud applications follow the explicit path. B. The WAN Edge DPI engine never selects a subperforming DIA circuit for the first application, and the WAN Edge router finds the SaaS application. C. Existing ows change the path and drop the traffic when the performance of the chosen path degrades. D. Application traffic ows are routed over best performing DIA circuit, which makes the routing decision based on the best performing path. Correct Answer: C
Which Cisco SD-WAN component centralizes policy configuration? A. Cisco DNA Center B. vBond C. WAN Edge D. vSmart Correct Answer: D
Which multicast component is irrelevant when de ning a multicast replicator outside the local network without any multicast sources or receivers? A. overlay BFD B. PIM interfaces C. OMP D. TLOC Correct Answer: A
An organization wants to discover, monitor, and track the applications running on the WAN Edge device on the LAN. Which configuration achieves the goal?


A. C Correct Answer:
What are the components of zone configuration in an application-aware firewall? A. destination zone, interface zone, source zone, and zone pair B. source zone, interface zone, and zone pair C. destination zone, interface zone, and zone pair D. source zone, destination zone, and zone pair Correct Answer: D
Refer to the exhibit. The network team must configure EIGRP peering at HQ with devices in the service VPN connected to WAN Edge CSRv. CSRv is currently configured with:
Which configuration on the WAN Edge meets the requirement?


A. Correct Answer: B
Refer to the exhibit. An engineer is troubleshooting a control connection issue on a WAN Edge device that shows socket errors. The packet capture shows some ICMP packets dropped between the two devices. Which action resolves the issue? A. Remove IP duplication in the network and configure a unique IP address. B. Recover vBond or wait for the controller to reload, which could be caused by a reset. C. Recover the vManage controller that is down in a high availability cluster. D. Change the system IP or restart the WAN Edge if the system IP is changed. Correct Answer: A
Which data policy configuration influences BGP routing traffic flow from LAN to WAN?


A. A Correct Answer:
Which color type is assigned when a TLOC is configured behind NAT? A. MPLS B. private C. blue D. public Correct Answer: D
Which cloud-based component in Cisco SD-WAN is responsible for establishing a secure connection to each WAN Edge router and distributes routes and policy information via OMP? A. vBond B. WAN Edge C. vManage D. vSmart Correct Answer: D
Which attribute is used to tie all the controllers together by vManage? A. vManage system-ip B. region ID C. organization name D. secure device ID Correct Answer: C
What is the main purpose of using TLOC extensions in WAN Edge router configuration? A. transports control traffic to remote-site WAN Edge routers B. creates an IPsec tunnel from WAN Edge to vBond Orchestrator C. creates hardware-level transport redundancy at the local site D. transports control traffic to a redundant vSmart Controller Correct Answer: D
An engineer is applying QoS policy for the transport-side tunnel interfaces to enable scheduling and shaping for a WAN Edge cloud router. Which command accomplishes the task? A. cloud-qos-service-side B. qos-scheduler QOS_0 C. rewrite-rule QOS-REQWRITE D. qos-map QOS Correct Answer: A
Which control policy assigned to branches in the out direction establishes a strict hub-and-spoke topology for VPN2?


A. B Correct Answer:
The Cisco SD-WAN engineer is configuring service chaining for a next-generation firewall located at the headquarters. Which configuration creates the service?


A. Correct Answer: B
Which component of the Cisco SD-WAN network assures that only valid customer nodes are participating in the overlay network? A. vBond B. vManage C. vSmart D. WAN Edge Correct Answer: A
How many vManage NMSs should be installed in each domain to achieve scalability and redundancy? A. two clusters B. two instances C. two or more in a cluster D. three or more in a cluster Correct Answer: C
What are the two components of centralized policy deployment in vManage? (Choose two.) A. policy definition B. lists C. QoS map D. policy-based routing E. route policy Correct Answer: AB
Refer to the exhibit. An engineer must block FTP traffic coming in from a particular Service VPN on a WAN Edge device. Which set of steps achieves this goal? A. Create a localized policy and add it to the interface feature template. B. Create a localized policy, add it to VPN template, and add an ACL to the interface feature template. C. Create a prefix list, add it to the localized policy, and add it to the interface feature template. D. Create a localized policy, add it to the device template, and add an ACL to the interface feature template. Correct Answer: B
Which feature delivers traffic to the Cisco Umbrella SIG cloud from a Cisco SD-WAN domain? A. L2TPv3 tunnel B. IPsec tunnel C. local umbrella agent D. source NAT Correct Answer: C
What must an engineer consider when deploying an SD-WAN on-premises architecture based on ESXI hypervisor? A. Cisco must provision the backup and snapshots platform for the SD-WAN architecture. B. The IT team will be given access by Cisco to a vManage for configuration templates and policies configuration. C. The IT team is required to provision the SD-WAN controllers and is responsible for backups and disaster recovery implementation. D. The managed service provider must provision controllers with their appropriate certificates. Correct Answer: C
Which protocol detects path status (up/down), measures loss/latency/jitter, and measures the quality of the IPsec tunnel MTU? A. DTLS B. BFD C. OMP D. IP-SLA Correct Answer: B
What is the default value for the number of paths advertised per prefix in the OMP feature template? A. 4 B. 8 C. 12 D. 16 Correct Answer: D
Refer to the exhibit. vManage and vBond have an issue establishing a connection to vSmart. Which two actions does the administrator take to fix the issue? (Choose two.) A. Reconfigure the vSmart from CLI with the proper Hostname & System IP. B. Manually resync vManage and vBond. C. Install the certificate received from the certificate server. D. Delete and re-add vSmart. Click Generate and validate CSR. E. Request a certificate from the certificate server based on the CSR for the vSmart. Correct Answer: CE
Which two vRoute attributes should be matched or set in vSmart policies and modified by data policies? (Choose two.) A. VPN B. preference C. site ID D. origin E. TLOC Correct Answer: AB
An enterprise deployed a Cisco SD-WAN solution with hub-and-spoke topology using MPLS as the preferred network over the Internet. A network engineer must implement an application-aware routing policy to allow ICMP traffic to be load-balanced over both the available links. Which configuration meets the requirement?


A. C Correct Answer:
What are the two components of an application-aware firewall? (Choose two.) A. default action B. sequence C. zone pair D. lists E. firewall policy Correct Answer: CE
An administrator modifies an application-aware routing policy to support newly deployed file servers. File transfers must be sent over the Internet- bound transports first and only use MPLS-bound transports as a backup. This policy is configured:Which configuration sequence meets the requirements?



A. Correct Answer: A
What are the two prerequisites for a Cloud OnRamp for SaaS feature to show the accurate vQoE score? (Choose two.) A. internet exit in VPN0 B. NAT in VPN 0 C. Cloud OnRamp enabled on WAN Edge router D. static route tracker for SaaS application E. DNS in service VPN Correct Answer: CE

Refer to the exhibit. vManage and vBond have an issue establishing a connection to each other. Which configuration resolves the issue? A. configure the timezone on vBond to Europe/London. B. configure the encapsulation ipsec command under the tunnel interface on vManage. C. configure a default route on vBond pointing to 172.16.2.254. D. Remove the encapsulation ipsec command under the tunnel interface of vBond. Correct Answer: C
Which website allows access to visualize the geography screen from vManager using the internet? A. *.globalstreetmaps.org B. *.fullstreetmaps.org C. *.callstreetmaps.org D. *.openstreetmaps.org Correct Answer: D
Which queue must an engineer configure for control and BFD traffic for convergence on a WAN Edge router? A. queue 0 B. queue 1 C. queue 2 D. queue 7 Correct Answer: C
Refer to the exhibit. A company requires a data traffic policy that uses the "mpls" and "biz-internet" colors for Google Apps if the SLA is met. A link with the "public-internet" color must be used if the other two links violate the data SL A. Which configuration meets these requirements?



B. Correct Answer: D
How are custom application ports monitored in Cisco SD-WAN controllers? A. Customers add custom application ports in vAnalytics and vSmart. B. Cisco adds custom application ports in vAnalytis and vManage. C. Customers add custom application ports in vAnalytics and vManage. D. Cisco adds custom application ports in vAnalytics and vSmart. Correct Answer: A
An engineer modifies a data policy for DIA in VPN 200 to meet the requirements for traffic destined to these locations: · external networks; must be translated · external networks; must use a public TLOC color · syslog servers, must use a private TLOC color Here is the existing data policy configuration:Which policy configuration sequence set meets the requirements?



A. Correct Answer: D
Which storage format is used when vManage is deployed as a virtual machine on a KVM hypervisor? A. .iso B. .tgz C. .ova D. .qcow2 Correct Answer: D
An engineer must configure the SD-WAN Edge router to identify DSCP 26 traffic coming from the router's local site and then change the DSCP value to DSCP 18 before sending it over to the SD-WAN fabric. What are the two ways to create the required configuration? (Choose two.)



A. AC Correct Answer:
Which two resource data types are used to collect information for monitoring using REST API in Cisco SD-WAN? (Choose two.) A. POST B. PUT C. scalar D. array E. DELETE Correct Answer: CD
A customer wants to use flaws for Cisco SD-WAN IaaS services by deploying virtual SD-WAN routers in a transit flaws VP A. The transit VPC then connects via site-to-site IPsec tunnels to an flaws transit gateway. Which transit VPC connects via site-to-site IPsec tunnels to an flaws transit gateway? B. Cisco Cloud onRamp for SaaS C. Cisco Cloud onRamp for Colocation D. Cisco Cloud onRamp for IaaS E. Cisco Cloud onRamp for Multicloud Correct Answer: C
Which protocol is used by the REST API to communicate with network devices in the Cisco SD-WAN network? A. HTTP B. SSL C. IPsec D. SSH Correct Answer: A
Refer to the exhibit.A WAN Edge device was recently added to vManage, but a control connection could not be established. Which action resolves this issue? A. Rectify the Root CA certificate mismatch on WAN Edge devices. B. Resolve the ZTP reachability and rectify smart account credentials issue. C. Install the bootstrap code on WAN Edge and check for CSR. D. Send the serial number to vBond from the vManage controller. Correct Answer: C
Refer to the exhibit. Cisco SD-WAN is deployed with controllers hosted in a data center. All branches have WAN Edge devices with dual connections to the data center: one via Internet and the other using MPLS. Three branches out of 20 have issues with their control connections on MPLS circuit. The local error refers to Control Connection Failure. Which action resolves the issue? A. Update the system IP on vManage and then resend it to the controllers. B. Rectify any issues with the underlay routing configuration. C. Match the TLOC color on the controllers and all WAN Edge devices. D. Math certificates for the DTLS connection and Root CA must be installed first on WAN Edge devices. Correct Answer: B
Which two mechanisms are used by vManage to ensure that the certificate serial number of the WAN Edge router that is needed to authenticate is listed in the WAN Edge Authorized Serial Number list? (Choose two.) A. Synchronize to the PnP. B. The vManage is shipped with the list. C. Synchronize to the Smart Account. D. Manually upload it to vManage. E. The devices register to vManage directly as the devices come online. Correct Answer: DE
Refer to the exhibit. Which NAT type must the engineer configure for the vEdge router to bring up the data plane tunnels? A. Use private color on the TLO B. Enable Full Cone NAT on the vEdge interface. C. Enable Symmetric NAT on the vEdge interface. D. Use public color on the TLO E. Correct Answer: D
Which component is responsible for creating and maintaining the secure DTLS/TLS connection on the vSmart controller? A. vdaemon B. OMP C. SNMP D. NETCONF Correct Answer: A
A customer has 1 to 100 service VPNs and wants to restrict outbound updates for VPN1. Which control policy configuration restricts these updates?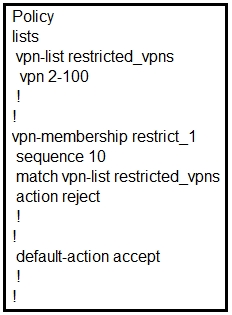


A. Correct Answer: A
What is the order of operations for software upgrades of Cisco SD-WAN nodes? A. vBond, vManage, vSmart, WAN Edge B. vManage, vBond, vSmart, WAN Edge C. vManage, vBond, WAN Edge, vSmart D. vManage, vSmart, vBond, WAN Edge Correct Answer: B
Which two architectural components are part of an SD-WAN high availability vManage cluster? (Choose two.) A. network configuration system B. WAN Edge router C. NAT router D. messaging server E. application server Correct Answer: AD
An engineer modifies a data policy for DIA in VPN 67. The location has two Internet-bound circuits. Only the web browsing traffic must be admitted for DIA, without further discrimination about which transport to use. Here is the existing data policy configuration:Which policy configuration sequence meets the requirements?



A. B Correct Answer:
Which two performance data details are provided by Cisco SD-WAN vAnalytics? (Choose two.) A. certificate authority status (health and expiration dates) for all controllers B. application quality of experience score from zero to ten C. details on total cost of ownership for the fabric D. jitter, loss, and latency for data tunnels E. view devices connected to a vManage NMS Correct Answer: BD
How is the software managed in Cisco SD-WAN? A. Software upgrade operation in the group must include vManage, vBond, and vSmart. B. Software downgrades are unsupported for vManage. C. Software images must be uploaded to vManage through HTTP or FTP. D. Software images must be transferred through VPN 512 or VPN 0 of vManage. Correct Answer: A
A network engineer must configure all branches to communicate with each other through the Service Chain Firewall located at the headquarters site. Which configuration allows the engineer to accomplish this task?


A. B Correct Answer:
Which configuration defines the groups of interest before creation of the access list or route map?


A. C Correct Answer:
What happens if the intelligent proxy is unreachable in the Cisco SD-WAN network? A. The block-listed domains are unresolved. B. The Cisco Umbrella Connector locally resolves the DNS request. C. The grey-listed domains are unresolved. D. The Cisco Umbrella Connector temporarily redirects HTTPS traffic. Correct Answer: B
Which keyword is used to choose a specific type of tunnel when SLA class is matched by the data traffic? A. sia-preferred-color B. preferred-color C. default D. strict Correct Answer: A
What is the OMP graceful restart default value on vSmart controllers and WAN Edge routers? A. 21,600 seconds B. 43,200 seconds C. 86,400 seconds D. 604,800 seconds Correct Answer: C
An engineer must configure egress QoS for voice traffic. Which queue must the engineer configure on the WAN Edge router to accomplish the task? A. queue 0 B. queue 1 C. queue 3 D. queues 7 Correct Answer: B
How must the application-aware enterprise firewall policies be applied within the same WAN Edge router? A. within zone pair B. within and between zones C. between two VPN tunnels D. between two VRFs Correct Answer: B
Which policy configuration must be used to classify traffic as it enters the branch WAN Edge router to be put into the desired output queue?


A. A Correct Answer:
Refer to the exhibit.An enterprise network is connected with an ISP network on an 80 Mbps bandwidth link. The network operation team observes 100 Mbps traffic on the 1 Gig-ISP link during peak hours. Which configuration provides bandwidth control to avoid traffic congestion during peak hours?



A. A Correct Answer:
Refer to the exhibit.The SD-WAN network is configured with a default full-mesh topology. An engineer wants Barcelona and Paris to communicate to each other through the London site using a control policy. Which control policy configuration accomplishes the task?



A. A Correct Answer:
Which protocol advertises WAN Edge routes on the service side? A. OSPF B. BGP C. ISIS D. EIGRP Correct Answer: B
What are the two reasons a customer chooses to use IPsec tunnels over GRE? (Choose two.) A. IPsec failure detection is faster. B. Generally, they provide a higher bandwidth for tunnel connection. C. CFlowd is required. D. A WAN Edge router is behind NAT. E. IPsec is more secure. Correct Answer: AE
Which SD-WAN component allows an administrator to manage and store software images for SD-WAN network elements? A. WAN Edge routers B. vSmart controllers C. vManage NMS D. vBond controllers Correct Answer: C
An enterprise is continuously adding new sites to its Cisco SD-WAN network. It must configure any cached routes ushed when OMP peers have lost adjacency. Which configuration allows the cached OMP routes to be ushed after every 24 hours from its routing table?


A. Correct Answer: A
A company deploys a Cisco SD-WAN solution but has an unstable Internet connection. When the link to vSmart comes back up, the WAN Edge router routing table is not refreshed, and some traffic to the destination network is dropped. The headquarters is the hub site, and it continuously adds new sites to the SD-WAN network. An engineer must configure route refresh between WAN Edge and vSmart within 2 minutes. Which configuration meets this requirement?


A. A Correct Answer:
After deploying Cisco SD-WAN, the company realized that by default, all sites built direct IPsec VPN tunnels to each other. In their previous topology, all spoke sites used the head office as their next hop for the LAN segment that belongs to network 40.0.0.0/16. The company wants to deploy its previous policy, which allows the 40.0.0.0/16 network that originates at the hub to advertise to the spokes. Which configuration meets the requirement?


A. C Correct Answer:
What are two benefits of installing Cisco SD-WAN controllers on cloud-hosted services? (Choose two.) A. utilizes well-known cloud services such as Azure, flaws, and GCP B. accelerates Cisco SD-WAN deployment C. installs the controllers in two cloud regions in a primary and backup setup D. allows integration of the WAN Edge devices in the cloud E. automatically implements zone-based rewalling on the controllers Correct Answer: AB
Which type of policy must be applied on a WAN Edge application-aware firewall to control traffic between two or more VPNs? A. firewall policy B. data policy C. service-insertion policy D. control policy Correct Answer: A
REST applications communicate over HTTP or HTTPS to make calls between network devices. Which two HTTPS standard methods are included? (Choose two.) A. DELETE B. Scalar C. Array D. POST E. Object Correct Answer: AD
A Cisco SD-WAN customer is running BGP and wants to pass on the AS number to BGP speaking routers on the service sidefinetwork via OMP. Which configuration accomplishes this goal?


A. D Correct Answer:
What is the maximum number of IPsec SAs that are temporarily created and converged on a new set of IPsec SAs in the pairwise keys process during a simultaneous rekey? A. 2 B. 4 C. 6 D. 8 Correct Answer: B
Refer to the exhibit. The Cisco SD-WAN is deployed using the default topology. The engineer wants to configure a service insertion policy such that all data traffic between Rome to Paris is forwarded through the NGFW located in London. Which configuration fulfills this requirement, assuming that the Service VPN ID is 1?



A. Correct Answer: B
Which protocol is used to propagate multicast join requests over the Cisco SD-WAN fabric? A. Auto-RP B. ARP C. OMP D. IGMP Correct Answer: D
An engineer builds a three-node vManage cluster and then realizes that multiple nodes are unnecessary for the size of the company. How should the engineer revert the setup to a single vManage? A. Use the cluster conversion utility to convert to standalone vManage. B. Restore vManage from the backup VM snapshot. C. Leave the cluster as is and point to one vManage. D. Remove two nodes from the three-node vManage cluster. Correct Answer: D
What is the default value for the Multiplier field of the BFD basic configuration in vManage? A. 3 B. 4 C. 5 D. 6 Correct Answer: A
Which platform cannot provide IPS and URL filtering capabilities? A. Cisco CSR 1000V B. Cisco ISR 1000 C. Cisco ISR 4000 D. Cisco Catalyst 8300 Correct Answer: AD
What are the default username and password for vSmart Controller when it is installed on a VMware ESXi hypervisor? A. username admin password admin B. username admin password cisco C. username cisco password admin D. username cisco password cisco Correct Answer: A
Which OMP route is selected for equal OMP route preference values on WAN Edge routers? A. route with origin type of connected B. route with origin type of static C. route with lower TLOC preference value D. route with higher TLOC preference value Correct Answer: D
Which percentage of total memory or total CPU usage for a device is classi ed as normal in the WAN Edge Health pane? A. more than 80 percent usage B. more than 90 percent usage C. less than 70 percent usage D. between 70 to 90 percent usage Correct Answer: C
Which timer speci es how long the router keeps routing information in the cache after all OMP sessions are lost at location S4317T8E35F76? A. graceful restart timer B. advertisement interval C. EOR timer D. hold time Correct Answer: A
Which type of certificate is installed on vManage for a user to access vManage via a web browser? A. Controller certificate B. Web Server certificate C. SD-AVC certificate D. WAN Edge certificate Correct Answer: A
An engineer configures an application-aware routing policy for a group of sites. The locations depend on public and private transports. The policy does not work as expected when one of the transports does not perform properly. This policy is configured:Which configuration completes the policy so that it works for all locations?



Correct Answer: B Correct Answer: B
Which routes are similar to the IP route advertisements when the routing information of WAN Edge routers is learned from the local site and local routing protocols? A. BGP B. OMP C. TLOC D. service Correct Answer: B
Which issue triggers the Cisco Umbrella resolver to forward DNS requests to the intelligent proxy? A. A domain is locally reachable. B. A domain is block-listed. C. A domain is nonexistent. D. A domain is grey-listed. Correct Answer: D
Which device should be configured with the service chain IP address to route intersite traffic through a firewall? A. vSmart B. spoke WAN Edge C. hub WAN Edge D. firewall Correct Answer: A
What are two components of vSmart? (Choose two.) A. key reflection B. policy engine C. NAT traversal D. device template creation E. monitoring Correct Answer: AB
What is a restriction when configuring a tunnel interface? A. Up to six tunnel interfaces are configurable on a vSmart. B. It is manually assigned when using vManage feature templates. C. It must be configured for the interface under all VPNs. D. Up to six tunnel interfaces are configurable on a WAN Edge. Correct Answer: B
Refer to the exhibit. vManage and vSmart have an issue establishing a connection to vBond. Which configuration resolves the issue? A. Change the timezone on the vSmart to Europe/London. B. configure the (11.1.1.X/24) IP addresses on the eth0 interfaces on vManage and vSmart. C. configure the tunnel interface on all three controllers with a color of transport. D. Reconfigure the system-ip parameter on vSmart to 11.1.1.2. Correct Answer: D
An engineer must configure local redundancy on a site. Which configuration accomplishes the task? A. vpn 0 tloc-extension interface interface-name B. interface interface-name tloc-extension C. tloc-extension interface interface-name D. vpn 0 interface interface-name tloc-extension interface-name Correct Answer: D
An engineer is configuring the branch office with a 172.16.0.0/16 subnet to use DIA for Internet traffic. All other traffic must flow to the central site or branches using the MPLS circuit. Which configuration meets the requirement?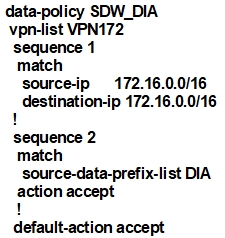


A. D Correct Answer:
An engineer provisions a WAN Edge router. Which command should be used from the WAN Edge router to activate it with vManage? A. request vedge-cloud activate serial token B. request vedge-cloud activate chassis-number organization C. request vedge-cloud activate chassis-number serial D. request vedge-cloud activate chassis-number token Correct Answer: D
Which policy allows communication between TLOCs of data centers and spokes and blocks communication between spokes? A. centralized data policy B. localized control policy C. centralized control policy D. localized data policy Correct Answer: A
Which OMP route is selected if it was learned from the same Cisco SD-WAN device at location S4406T9E02F15? A. route with the lower origin metric B. route with the higher OMP route preference value C. route with the higher router ID D. route with the lower administrative distance Correct Answer: D
Which SD-WAN component detects path performance information in the organization to report the issue to the service provider at site ID:123456? A. vBond Orchestrator B. Cisco DNA C. vManage NMS D. vAnalytics Correct Answer: C
An enterprise has these three WAN connections: · public Internet · business Internet · MPLS An engineer must configure two available links to route traffic via both links. Which configuration achieves this objective? A. omp no shutdown ecmp-limit 2 B. omp no shutdown send-path-limit 2 C. omp no shutdown overlay-as 2 D. omp no shutdown route-limit 2 Correct Answer: B
Refer to the exhibit. An enterprise decides to use the Cisco SD-WAN Cloud onRamp for SaaS feature and utilize A. Q site Biz iNET to reach SaaS Cloud for branch C, currently reaching SaaS Cloud directly. Which role must be assigned to devices at both sites in vManage Cloud Express for this solution to work? B. Branch to be added as Client Sites and C. Q as DI D. Q to be added as Gateway and Branch as DI E. Branch to be added as DIA and F. Q as Client Site. G. Q to be added as Gateway and Branch as Client Site. Correct Answer: C
Which action is performed during the onboarding process when a WAN Edge router is connected to ZTP server ztp.viptela.com? A. The router is connected to WAN Edge Cloud Center. B. The router receives its vBond Orchestrator information. C. The router is synced with vSmart Controller via an IPsec tunnel. D. The router is connected to vSmart Controller via a DTLS/TLS tunnel. Correct Answer: A
Which protocol is configured on tunnels by default to detect loss, latency, jitter, and path failures in Cisco SD-WAN? A. TLS B. BFD C. OMP D. BGP Correct Answer: B
Refer to the exhibit. Customer XYZ cannot provision dual connectivity on both of its routers due to budget constraints but wants to use both R1 and R2 interlaces for users behind them for load balancing toward the hub site. Which configuration achieves this objective?



A. Correct Answer: A
An engineer must apply the configuration for certificate installation to vBond Orchestrator and vSmart Controller. Which configuration accomplishes this task?


A. A Correct Answer:
Which component of the Cisco SD-WAN secure extensible network provides a single pane of glass approach to network monitoring and configuration? A. APIC-EM B. vSmart C. vManage D. vBond Correct Answer: C
An administrator is configuring the severity level on the vManage NMS for events that indicate that an action must be taken immediately. Which severity level must be configured? A. error B. critical C. warning D. alert Correct Answer: D
Refer to the exhibit. A customer wants to implement primary and secondary Cisco SD-WAN overlay routing for prefixes that are advertised for both data centers. The east data center (TLOC 101.101.101.101) is primary for east sites, and the west data center (TLOC 100.100.100.100) is primary for west sites. Which configuration change achieves this objective?



A. Correct Answer: B
Refer to the exhibit. The Cisco SD-WAN network is configured with a default full-mesh topology. An engineer wants Paris WAN Edge to use the Internet TLOC as the preferred TLOC for MSN Messenger and AOL Messenger traffic. Which policy achieves this goal?



Correct Answer: C Correct Answer: C
How is an event monitored and reported for an individual device in the overlay network at site ID:S4300T6E43F36? A. The device sends event notifications to vManage. B. The device sends notifications to vSmart that sends them to vManage. C. The device sends a critical alarm of events to vManage. D. The device sends a critical alarm to vSmart that sends it to vManage. Correct Answer: A
An engineer must automate certificate signing through Cisco. Which vManage configuration achieves this task? A. vpn 0 allow-service dns allow-service sshd allow-service netconf B. vpn 512 dns 208.67.222.222 primary allow-service dns allow-service sshd allow-service netconf C. vpn 0 dns 208.67.222.222 primary allow-service dns allow-service sshd allow-service netconf D. vpn 512 allow-service dns allow-service sshd allow-service netconf Correct Answer: C
An engineer must deploy a QoS policy with these requirements: · policy name: App-police · police rate: 1000000 · burst: 1000000 · exceed: drop Which configuration meets the requirements?


A. B Correct Answer:
Refer to the exhibit. An enterprise has hub and spoke topology where it has several VPNs. An engineer must allow users in VPN91 to reach users in VPN92 and VPN10 to reach VPN91 and VPN92. Which configuration meets these requirements?



Correct Answer: D Correct Answer: D
Which controller manages the orchestration plane of Cisco SD-WAN in a cloud deployment? A. Cisco DNA Center B. vSmart C. vBond D. vManage Correct Answer: B
How many subnets are necessary in Azure VNet for a WAN Edge device to function in the cloud deployment? A. CSR is the WAN Edge device that is supported in the Microsoft cloud. The Microsoft underlay cloud fabric performs the management function. B. There must be three subnets in VNet: management, public, and services. C. One public subnet is required in VNet. The Microsoft underlay cloud fabric performs all of the routing functions for WAN Edge. D. Public and services subnets are required in VNet. The Microsoft underlay cloud fabric performs the management function. Correct Answer: D
Which two sets of identifiers does OMP carry when it advertises TLOC routes between WAN Edge routers? (Choose two.) A. TLOC public and private address, carrier, and preference B. source and destination IP address, MAC, and site ID C. system IP address, link color, and encapsulation D. VPN ID, local site network, and BGP next-hop IP address E. TLOC public and private address, tunnel ID, and performance Correct Answer: AC

Refer to the exhibit. vManage and vBond have an issue establishing a connection to each other. Which configuration resolves the issue? A. configure the timezone on vBond to Europe/London. B. configure the encapsulation ipsec command under the tunnel interface on vManage. C. configure a default route on vBond pointing to 172.16.2.254. D. Remove the encapsulation ipsec command under the tunnel interface of vBond. Correct Answer: C
Refer to the exhibit. An organization is testing a Cisco SD-WAN solution and decided to have the control plane established first and not the data plane at the time of migration. Which configuration achieves this goal?



A. Correct Answer: A
Which policy tracks path characteristics such as loss, latency, and jitter in vManage? A. VPN B. control C. app-route D. data Correct Answer: C
Refer to the exhibit. An engineer configured OMP with an overlay-as of 10666. What is the AS-PATH for prefix 104.104.104.104/32 on R100? A. 100 10666 B. 100 20 104 C. 100 10666 20 104 D. 100 10666 104 Correct Answer: D
Which table is used by the vSmart controller to maintain service routes of the WAN Edge routers in the hub and local branches? A. RIB B. FIB C. OMP D. TLOC Correct Answer: C
An administrator wants to create a policy to add a traffic policer called "politer-ccnp" to police data traffic on the WAN Edge. Which configuration accomplishes this task in vSmart?


A. B Correct Answer:
Which device in the Cisco SD-WAN solution receives and categorizes event reports, and generates alarms? A. WAN Edge routers B. vSmart controllers C. vBond controllers D. vManage NMS Correct Answer: D
What is the minimum Red Hat Enterprise Linux operating system requirement for a Cisco SD-WAN controller deployment via KVM? A. RHEL 7.5 B. RHEL 4.4 C. RHEL 6.7 D. RHEL 6.5 Correct Answer: A
What is a description of vManage NMS? A. A cluster consists of a minimum of two vManage NMSs. B. It is a software process on a dedicated WAN Edge router in the network. C. A cluster requires device templates to be created on an attached to the same server. D. It is accessible only from VPN 512 (the management VPN). Correct Answer: D
An engineer must configure two branch WAN Edge devices where an Internet connection is available and the controllers are in the headquarters. The requirement is to have IPsec VPN tunnels established between the same colors. Which configuration meets the requirement on both WAN Edge devices?


Correct Answer: C Correct Answer: C
A network administrator is creating an OMP feature template from the vManage GUI to be applied to WAN Edge routers. Which configuration attribute will avoid the redistribution of the routes back into the OMP from the LAN side? A. configure ECMP limit B. configure Send Backup Paths C. configure Number of Paths Advertised per prefix D. configure Overlay AS Number Correct Answer: D
Which two metrics must a cloud Edge router use to pick the optimal path for a SaaS application reachable via a gateway site? (Choose two.) A. HTTP loss and latency metrics to the SaaS application B. BFD loss and latency metrics to the gateway site C. ICMP loss and latency metrics to the SaaS application D. HTTP loss and latency metrics to the gateway site E. BFD loss and latency metrics to the SaaS application Correct Answer: BC
Where on vManage does an engineer find the details of control node failure? A. Alarms B. Events C. Audit log D. Network Correct Answer: D
Which destination UDP port is used by WAN Edge router to make a DTLS connection with vBond Orchestrator? A. 12343 B. 12345 C. 12346 D. 12347 Correct Answer: C
Refer to the exhibit. vManage logs are available for the past few months. A device name change was deployed mistakenly at a critical site. How is the device name change tracked by operations and design teams?



Correct Answer: B Correct Answer: B
A customer must upgrade the Cisco SD-WAN devices and controllers from version 19.2 to version 20.3. The devices include WAN Edge Cloud, vManage, vSmart, and vBond. Which types of image files are needed for this upgrade? A. one file for vManage and one file for all other devices with extension .bin B. one file for vManage, one for vSmart, and one for vBond + WAN Edge Cloud with extension .bin C. one file for vManage and one file for all other devices with extension tar.gz D. one file for vManage, one for vSmart, and one for vBond + WAN Edge Cloud with extension tar.gz Correct Answer: D
An engineer wants to automate the onboarding process for a WAN Edge router with vManage. Which command will accomplish this? A. request vedge-cloud activate chassis-number <chassis-number> serial <serial> B. request vedge-cloud activate chassis-number <chassis-number> token <token-number> C. request vedge-cloud activate serial <serial> token <token-number> D. request vedge-cloud activate chassis-number <chassis-number> organization <organization> Correct Answer: B
Company ABC has decided to deploy the controllers using the On-Prem method. How does the administrator upload the WAN Edge list to the vManage?


Correct Answer: C Correct Answer: C
An engineer is adding a tenant with location ID 123456789 in vManage. What is the maximum number of alphanumeric characters that is accepted in the tenant name field? A. 8 B. 256 C. 128 D. 64 Correct Answer: C
What is the procedure to upgrade all Cisco SD-WAN devices to a recent version? A. The upgrade is performed for a group of WAN Edge devices first to ensure data-plane availability when other controllers are being updated. B. Upgrade and reboot are performed first on vManage, then on vBond, then on vSmart, and nally on the Cisco WAN Edge devices. C. The upgrade is performed first on vManage, then on WAN Edge devices, then on vBond, and nally on vSmart. The reboot must start from WAN Edge devices. D. Upgrade and reboot are performed first on vBond, then on vSmart, and nally on the Cisco WAN Edge devices. Correct Answer: B
A customer has MPLS and Internet as the TLOC colors. An engineer must configure controllers with the Internet and not with MPLS. Which configuration achieve this requirement on vManage?


Correct Answer: A Correct Answer: A
An administrator must deploy the controllers using the On-Prem method while vManage can access the PnP portal from inside. How are the two WAN Edge authorized allowed lists to be made available to vManage? (Choose two.)



Correct Answer: AD Correct Answer: AD
What is a benefit of using REST APIs? A. predefined automation and orchestration platform for event management and logging B. user-defined automation and integration into other orchestration systems or tools C. vAnalytics to simplify operational services integration and real-time event monitoring D. predefined SD-WAN controller with other platform integration for event management and logging Correct Answer: B
What prohibits deleting a VNF image from the software repository? A. if the image is stored by vManage B. if the image is referenced by a service chain C. if the image is included in a configured policy D. if the image is uploaded by a WAN Edge device Correct Answer: A
An organization requires the use of integrated preventative engines, exploit protection, and the most updated and advanced signature-based antivirus with sandboxing and threat intelligence to stop malicious attachments before they reach users and get executed. Which Cisco SD-WAN solution meets the requirements? A. Cisco Trust Anchor module B. Cisco AMP and Threat Grid C. URL filtering and Umbrella DNS security D. Snort IPS Correct Answer: C
An enterprise needs DIA on some of its branches with a common location ID: A042:B49C:D02E::72. Which WAN Edge configuration meets the requirement? A. vpn 1 interface ge0/1 ip address 172.16.0.1/24 vpn 512 ip route 0.0.0.0/0 vpn 0 B. vpn 1 ip route 0.0.0.0/0 vpn 1 interface ge0/0 ip address 172.16.0.1/24 nat C. vpn 0 ip route 0.0.0.0/0 vpn 0 vpn 1 interface ge0/1 ip address 172.16.0.1/24 nat D. vpn 0 interface ge0/0 ip address 172.16.0.1/24 nat vpn 1 ip route 0.0.0.0/0 vpn 0 Correct Answer: D
Which two criteria are supported to filter traffic on a Cisco Umbrella Cloud-delivered firewall? (Choose two.) A. geolocation B. site ID C. URL D. protocol E. tunnels Correct Answer: CD
Which command disables the logging of syslog messages to the local disk? A. no system logging disk local B. system logging server remote C. no system logging disk enable D. system logging disk disable WAN_Release_16.3/02System_and_Interfaces/08configuring_System_Logging Correct Answer: C
Which combination of platforms is managed by vManage? A. ISR4351, ASR1002HX, vEdge2000, vEdge Cloud B. ISR4321, ASR1001, Nexus, ENCS C. ISR4321, ASR1001, ENCS, ISRv D. ISR4351, ASR1009, vEdge2000, CSR1000v Correct Answer: C
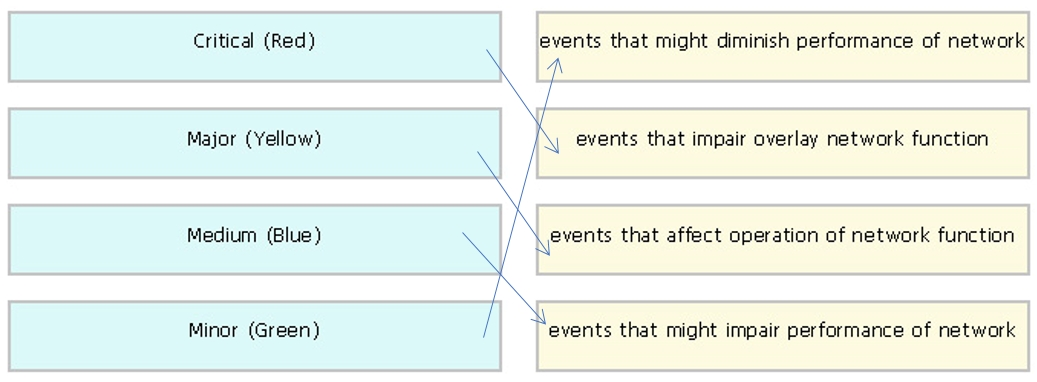
Which alarm setting is configured to monitor serious events that affect, but do not shut down, the operation of a network function? A. Critical B. Medium C. Major D. Minor Correct Answer: C
Which pathway under Monitor > Network > Select Device is used to verify service insertion configuration? A. System Status B. ACL Logs C. Real Time D. Events Correct Answer: C
Which API call retrieves a list of all devices in the network?
A. https://vmanage_IP_address/dataservice/system/device/{{model}}
B. http://vmanage_IP_address/dataservice/system/device/{{model}}
C. http://vmanage_IP_address/api-call/system/device/{{model}}
D. https://vmanage_IP_address/api-call/system/device/{{model}}
Correct Answer: A
Which template configures the out-of-band management VPN?


Correct Answer: B Correct Answer: B
When software is upgraded on a vManage NMS, which two image-adding options store images in a local vManage software repository? (Choose two.) A. To be downloaded over an ICMP connection B. To be downloaded over a SNMP connection C. To be downloaded over a control plane connection D. To be downloaded over an out-of-band connection E. To be downloaded over a SMTP connection Correct Answer: CD
Which logs verify when a device was upgraded? A. ACL B. Email C. SNMP D. Audit Correct Answer: D
Which protocol is used to measure loss, latency, jitter, and liveliness of the tunnel between WAN Edge router peers? A. OMP B. NetFlow C. BFD D. IP SLA Correct Answer: C
Which two algorithms authenticate a user when configuring SNMPv3 monitoring on a WAN Edge router? (Choose two.) A. AES-256 B. MD5 C. SHA-2 D. AES-128 E. SHA-1 Correct Answer: BE
Refer to the exhibit. A network administrator is configuring OMP in vManage to advertise all the paths for the same prefix from a site that has two WAN Edge devices. Each WAN Edge device is connected to three ISPs and two private MPLS transports. What is the minimum value for `Number of Paths advertised per prefix` that should be configured? A. 2 B. 3 C. 5 D. 10 Correct Answer: D
In Cisco SD-WAN, which protocol is used for control connections between Cisco SD-WAN devices? A. BGP B. DTLS C. OSPF D. OMP 20Management%20Protocol%20is,described%20in%20Overlay%20Routing%20Overview Correct Answer: D
An engineer must improve video quality by limiting HTTP traffic to the Internet without any failover. Which configuration in vManage achieves this goal?


Correct Answer: A Correct Answer: A
Which two products that perform lifecycle management for virtual instances are supported by WAN Edge cloud routers? (Choose two.) A. flaws B. Azure C. VMware vCenter D. OpenStack E. IBM Cloud Correct Answer: CD
An engineer configures policing with a rate of 125 Bps and a burst rate of 8000 bits, as shown here:Which configuration completes this task? A. configure 125 for rate and 1000 for burst. B. configure 125 for rate and 8000 for burst. C. configure 1000 for rate and 1000 for burst. D. configure 1000 for rate and 64000 for burst. Correct Answer: C
Which secure connection should be used to access the REST APIs through the Cisco vManage web server? A. authenticated DTLS B. authenticated HTTPS C. JSON Inspector interface D. HTTP inspector interface Correct Answer: B
A Cisco SD-WAN customer has a requirement to calculate the SHA value for files as they pass through the device to see the returned disposition and determine if the file is good, unknown, or malicious. The customer also wants to perform real-time traffic analysis and generate alerts when threats are detected. Which two Cisco SD-WAN solutions meet the requirements? (Choose two.) A. Cisco Threat Grid B. Cisco Trust Anchor Module C. Cisco AMP D. Cisco Secure Endpoint E. Cisco Snort IPS Correct Answer: AC
A network administrator is configuring an application-aware firewall between inside zones to an outside zone on a WAN Edge router using vManage GUI. Which kind of inspection is performed when the `inspect` action is used? A. Layer 7 inspection for TCP and Layer 4 inspection for UDP B. stateful inspection for TCP and stateless inspection of UDP C. IPS inspection for TCP and Layer 4 inspection for UDP D. stateful inspection for TCP and UDP Correct Answer: D
Which hardware component is involved in the Cisco SD-WAN authentication process for ISR platforms? A. ZTP B. OTPC C. SUDI D. TPMD Correct Answer: C
A network administrator is configuring QoS on a WAN Edge 5000 router and needs to enable it on the transport side interface. Which policy setting must be selected to accomplish this goal? A. Cloud QoS B. Net flow C. Application D. Cloud QoS Service side Correct Answer: A
What is a benefit of the application-aware firewall feature in the Cisco SD-WAN solution? A. application visibility B. control policy enforcement C. application monitoring D. application malware protection 20Firewall&text=This%20application%2Daware%20 firewall%20feature,of%201400%2B%20layer%207%20applications Correct Answer: A
An engineer is tasked to improve throughput for connection-oriented traffic by decreasing round-trip latency. Which configuration will achieve this goal? A. turn off Enable TCP Optimization B. turn on Enhance ECMP Keying C. turn on Enable TCP Optimization D. turn off Enhance ECMP Keying Correct Answer: C
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two.) A. Apply a data policy on WAN interface B. configure a control policy C. Apply a QoS map policy D. configure NAT on the transport interface E. configure a centralized data policy Correct Answer: AE
Refer to the exhibit. The ge0/0 interface connects to a 30-MB link. A network administrator wants to always have 10 MB available for high priority traffic. When lower-priority traffic bursts exceed 20 MB, traffic should be redirected to the second WAN interface ge0/1. Which set of configurations accomplishes this task?



Correct Answer: D WAN_Release_17.1/08Forwarding_and_QoS/03Forwarding_and_QoS_configuration_Examples Correct Answer: D
Refer to the exhibit. Which shaping-rate does the engineer use to shape traffic at 9 Mbps? A. 9 B. 9000 C. 90000 D. 9000000 Correct Answer: B
An engineer wants to change the configuration of the certificate authorization mode from manual to automated. Which GUI selection will accomplish this? A. Maintenance > Security B. configuration > certificates C. Administration > Settings D. Tools > Operational Commands Correct Answer: B
Which two requirements must be met for DNS inspection when integrating with Cisco Umbrella? (Choose two.) A. Attach security policy to the device template. B. Create and attach a System feature template with the Umbrella registration credentials. C. Register and configure the vManage public IP and serial number in the Umbrella portal. D. Upload the WAN Edge serial allow list to the Umbrella portal. E. configure the Umbrella token on the vManage. Correct Answer: AE
At which layer does the application-aware firewall block applications on a WAN Edge? A. 3 B. 5 C. 2 D. 7 Correct Answer: D
Which two features does the application firewall provide? (Choose two.) A. blocks traffic by application or application-family B. numbered sequences of match-action pairs C. classification of 1000+ layer 4 applications D. application match parameters E. classification of 1400+ layer 7 applications Correct Answer: AE
What is a benefit of the application-aware firewall? A. It blocks traffic by MTU of the packet B. It blocks encrypted traffic C. It blocks traffic by application D. It blocks traffic by MAC address Correct Answer: C
The network administrator is configuring a QoS scheduling policy on traffic received from transport side tunnels on WAN Edge 5000 routers at location:405608122. Which command must be configured on these devices? A. mls qos B. cloud-qos C. service qos D. cloud-mls qos Correct Answer: B
Refer to the exhibit. Which QoS treatment results from this configuration after the access list acl-guest is applied inbound on the vpn1 interface? A. A TCP packet sourcing from 172.16.10.1 and destined to 172.16.20.1 is dropped B. A UDP packet sourcing from 172.16.20.1 and destined to 172.16.10.1 is accepted C. A UDP packet sourcing from 172.16.10.1 and destined to 172.16.20.1 is dropped D. A TCP packet sourcing from 172.16.20.1 and destined to 172.16.10.1 is accepted Correct Answer: C
Refer to the exhibit. A network administrator is setting the queueing value for voice traffic for one of the WAN Edge routers using vManager GUI. Which queue value must be set to accomplish this task? A. 0 B. 1 C. 2 D. 3 Correct Answer: A
Which configuration changes the packet loss priority from low to high?


Correct Answer: B Correct Answer: B
An engineer is configuring a shaping rate of 1 Mbps on the WAN link of a WAN Edge router. Which configuration accomplishes this task?


Correct Answer: C Correct Answer: C
Which on-the-box security feature is supported by the Cisco ISR 4451 SD-WAN device and not on vEdge? A. IPsec/GRE cloud proxy B. reverse proxy C. Enterprise Firewall with Application Awareness D. Cloud Express service Correct Answer: C
Which two mechanisms are used to guarantee the integrity of data packets in the Cisco SD-WAN architecture data plane? (Choose two.) A. certificates B. transport locations C. authentication headers D. encapsulation security payload E. TPM chip Correct Answer: BD
Which value is verified in the certificates to confirm the identity of the physical WAN Edge device? A. Serial Number B. OTP C. System-IP D. Chassis-ID Correct Answer: A
An engineer must use data prefixes to configure centralized data policies using the vManage policy configuration wizard. What is the first step to accomplish this task? A. configure network topology. B. Apply policies to sites and VPNs. C. configure traffic rules. D. Create groups of interest. Correct Answer: D
Refer to the exhibit. The Cisco SD-WAN network is configured with a default full-mesh topology. Islamabad HQ and Islamabad WAN Edges must be used as the hub sites. Hub sites MPLS TLOC must be preferred when forwarding FTP traffic based on a configured SLA class list. Which policy configuration does the network engineer use to call the SLA class and set the preferred color to MPLS? A. Centralized Policy, traffic Policy B. Centralized Policy, Topology C. Localized Policy, Forwarding Class D. Localized Policy, Route Policy Correct Answer: B
Refer to the exhibit. Which command allows traffic through the IPsec tunnel configured in VPN 0? A. service netsvc1 vpn1 B. service netsvc1 address 1.1.1.1 C. service FW address 1.1.1.1 D. service local Correct Answer: A
Refer to the exhibit. Which configuration sets up direct Internet access for VPN 1?



Correct Answer: C Correct Answer: C
An enterprise has several sites with multiple VPNs that are isolated from each other. A new requirement came where users in VPN 73 must be able to talk to users in VPN 50. Which configuration meets this requirement?


Correct Answer: A Correct Answer: A
Refer to the exhibit. An engineer is configuring service chaining. Which set of configurations is required for all traffic from Site ID 1 going toward Site ID 2 to get ltered through the firewall on the hub site?



Correct Answer: B Correct Answer: B
An engineer is configuring a data policy for IPv4 prefixes for a single WAN Edge device on a site with multiple WAN Edge devices. How is this policy added using the policy configuration wizard? A. In vBond orchestrator, select the configure --> policies screen, select the localized policy tab, and click add policy. B. In vManage NMS, select the configure --> policies screen, select the localized policy tab, and click add policy. C. In vSmart controller, select the configure --> policies screen, select the localized policy tab, and click add policy. D. In vManage NMS, select the configure --> policies screen, select the centralized policy tab, and click add policy. Correct Answer: B
An engineer is configuring a data policy for packets that must be captured through the policy. Which command accomplishes this task? A. policy > data-policy > vpn-list > sequence > default-action > accept B. policy > data-policy > vpn-list > sequence > match C. policy > data-policy > vpn-list > sequence > action D. policy > data-policy > vpn-list > sequence > default-action > drop Correct Answer: C
An engineering team must prepare a traffic engineering policy where an MPLS circuit is preferred for traffic coming from the Admin VLAN. Internet should be used as a backup only. Which configuration fulfills this requirement?


Correct Answer: A Correct Answer: A
An administrator must configure an ACL for traffic coming in from the service-side VPN on a specific WAN Edge device with circuit ID 123456789. Which policy must be used to configure this ACL? A. local data policy B. central data policy C. app-aware policy D. central control policy Correct Answer: D
In a customer retail network with multiple data centers, what does the network administrator use to create a regional hub topology? A. app route policy on vSmart B. data policy on vSmart C. control policy on vSmart D. control policy on vManage Correct Answer: C
Refer to the exhibit. The tunnel interface configuration on both WAN Edge routers is:
Which configuration for WAN Edge routers will connect to the Internet?



Correct Answer: B Correct Answer: B
Which scheduling method is configured by default for the eight queues in the cloud vEdge router? A. weighted round robin B. priority queue C. low latency queue D. weighted random early detection Correct Answer: A
Refer to the exhibit. Which configuration routes Site 2 through the firewall in Site 1?



Correct Answer: C Correct Answer: C
A customer is receiving routes via OMP from vSmart controller for a specific VPN. The customer must provide access to the W2 loopback received via OMP to the OSPF neighbor on the service-side VPN. Which configuration fulfills these requirements?


Correct Answer: D Correct Answer: D
Refer to the exhibit. An administrator is configuring a policy in addition to an existing hub-and-spoke policy for two sites that should directly communicate with each other. How is this policy configured? A. mesh B. custom control (route and TLOC) C. hub-and-spoke D. import existing topology Correct Answer: B
Which feature allows reachability to an organization's internally hosted applications for an active DNS security policy on a device? A. data policy with redirect B. local domain bypass C. DNSCrypt configuration D. DHCP option 6 Correct Answer: B
A network administrator is configuring a centralized control policy based on match action pairs for multiple conditions. Which order must be configured to prefer prefix List over TLOC and TLOC over Origin? A. deterministic order B. lowest to highest sequence number C. highest to lowest sequence number D. nonsequential order Correct Answer: B
Refer to the exhibit. The network administrator has configured a centralized topology policy that results in the displayed routing table at a branch office. Which two configurations are verified by the output? (Choose two.) A. The default route is configured locally. B. This routing table is from a cEdge router. C. The configured policy is adding a route tag of 300 to learned routes. D. The default route is learned via OMP. E. The routing table is for the transport VPN. Correct Answer: AB
An engineer must configure a centralized policy on a site in which all HTTP traffic should use the Public Internet circuit if the loss on this circuit is below 10%, otherwise MPLS should be used. Which configuration wizard fulfills this requirement? A. Create Applications or Groups of Interest > configure traffic Data > Apply Policies to Sites and VPNs. B. configure VPN Membership > Apply Policies to Sites and VPNs. C. Create Applications or Groups of Interest > configure traffic Rules > Apply Policies to Sites and VPNs. D. configure Topology > Apply Policies to Sites and VPNs. Correct Answer: C
An engineer wants to track tunnel characteristics within a SLA-based policy for convergence. Which policy configuration will achieve this goal? A. app-route policy B. VPN membership policy C. control policy D. data policy Correct Answer: D
Refer to the exhibit. Which configuration value is used to change the administrative distance of iBGP routes to 20? A. configure Internal Routes Distance to 20. B. configure Propagate AS Path to off. C. configure Local Routes Distance to 20. D. configure External Routes Distance to 20. Correct Answer: C
An administrator needs to configure Cisco SD-WAN to divert traffic from the company's private network to an ISP network. Which action should be taken to accomplish this goal? A. configure the security policy B. configure the control policy C. configure the data policy D. configure the application aware policy Correct Answer: C
How is multicast routing enabled on devices in the Cisco SD-WAN overlay network? A. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as speci ed in the original PIM join message. B. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as speci ed in the original PIM join message. C. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as speci ed in the original PIM join message. D. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as speci ed in the original PIM join message. Correct Answer: A
An engineer is configuring a centralized policy to influence network route advertisement. Which controller delivers this policy to the fabric? A. vSmart B. vBond C. vManage D. WAN Edge Correct Answer: A
Refer to the exhibit. The network team must configure branch B WAN Edge device 103 to establish dynamic full-mesh IPsec tunnels between all colors with branches over MPLS and Internet circuits. The branch is configured with:
Which configuration meets the requirements?



Correct Answer: D Correct Answer: D
Which VPN connects the transport-side WAN Edge interface to the underlay/WAN network? A. VPN 1 B. VPN 0 C. VPN 512 D. VPN 511 Correct Answer: B
Refer to the exhibit. The engineering must assign community tags to 3 of its 74 critical server networks as soon as they are advertised to BGP peers. These server networks must not be advertised outside AS. Which configuration fulfills this requirement?



Correct Answer: B Correct Answer: B
An engineer is configuring a list that matches all IP prefixes with lengths from /1 to /16 in a centralized control policy. Which list accomplishes this task? A. 0.0.0.0/0 file 16 B. 0.0.0.0/1 file 16 C. 0.0.0.0/0 ge 1 D. 0.0.0.0/16 ge 1 Correct Answer: B
WAN Edge routers are configured manually to use UDP port offset to use nondefault offset values when IPsec tunnels are created. What is the offset range? A. 1-19 B. 0-18 C. 0-19 D. 1-18 Correct Answer: C
A company must avoid downtime at the remote sites and data plane to continue forwarding traffic between WAN Edge devices if the branch router loses connectivity to its OMP peers. Which configuration meets the requirement?


Correct Answer: A Correct Answer: A
Refer to the exhibit. An MPLS connection on R2 must extend to R1. Users behind R1 must have dual connectivity for data traffic. Which configuration provides R1 control connectivity over the MPLS connection?



Correct Answer: D Correct Answer: D
Refer to the exhibit. Which command-line configuration on a WAN Edge device achieves these results?



Correct Answer: C Correct Answer: C
In which VPN is the NAT operation on an outgoing interface configured for direct Internet access? A. 0 B. 512 C. 10 D. 1 Correct Answer: A
Which SD-WAN component is configured to enforce a policy to redirect branch-to-branch traffic toward a network service such as a firewall or IPS? A. vBond B. vSmart C. WAN Edge D. Firewall Correct Answer: B
Which command verifies a policy that has been pushed to the vEdge router? A. vSmart# show running-config policy B. vEdge# show running-config data policy C. vSmart# show running-config apply policy D. vEdge# show policy from-vsmart Correct Answer: D
Which policy configures an application-aware routing policy under configuration > Policies? A. Data policy B. Centralized policy C. Localized policy D. Control policy Correct Answer: A
When the VPN membership policy is being controlled at the vSmart controller, which policy disallows VPN 1 at sites 20 and 30?


Correct Answer: C Correct Answer: C
Which policy is configured to ensure that a voice packet is always sent on the link with less than a 50 msec delay? A. localized data policy B. centralized control policy C. localized control policy D. centralized data policy Correct Answer: D
When VPNs are grouped to create destination zone in Zone-Based Firewall, how many zones can a single VPN be part of? A. two B. four C. one D. three docs.cisco.com/Product_Documentation/Software_Features/Release_18.4/Security/Enterprise_Firewall_with_Application_Awareness Community vote distribution Correct Answer: C
Refer to the exhibit. Which configuration change is needed to configure the tloc-extension on Branch1-Edge1?



Correct Answer: D Correct Answer: D
Refer to the exhibit. Which configuration extends the INET interface on R1 to be used by R2 for control and data connections? A. R1 interface ge0/2 interface ge0/2.10 ip address 43.43.43.2/30 tloc-extension ge0/0 tunnel-interface color public-internet R2 interface ge0/2 interface ge0/2.10 ip address 43.43.43.1/30 tunnel-interface color public-internet B. R1 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.2/30 tunnel-interface color public-internet R2 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.1/30 tloc-extension ge0/0 C. R1 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.2/30 tloc-extension ge0/0 R2 interface ge0/2 mtu 1504 no shutdown interface ge0/2.10 ip address 43.43.43.1/30 tunnel-interface color public-internet D. R1 interface ge0/2 no shutdown interface ge0/2.10 ip address 43.43.43.2/30 tloc-extension ge0/0 R2 interface ge0/2 no shutdown interface ge0/2.10 ip address 43.43.43.1/30 tloc-extension ge0/0 Correct Answer: C
Two sites have one WAN Edge each. Each WAN Edge has two public TLOCs with no restrict configured. There is full reachability between the TLOCs. How many data tunnels are formed on each WAN Edge router? A. 6 B. 2 C. 4 D. 8 Correct Answer: A
Which command on a WAN Edge device displays the information about the colors present in the fabric that are learned from vSmart via OMP? A. show omp peers B. show omp route C. show omp sessions D. show omp tlocs Correct Answer: D
Which two WAN Edge devices should be deployed in a cloud? (Choose two.) A. ASR1000v B. vEdge 100wm C. CSR1000v D. vEdge cloud E. vEdge 5000v Correct Answer: CD
Refer to the exhibit. Which binding is created using the tloc-extension command? A. between ge 0/2.101 of port-type transport and ge 0/0 of port-type service B. between ge 0/2.101 of port-type service and ge 0/0 of port-type service C. between ge 0/2.101 of port-type service and ge 0/0 of port-type transport D. between ge 0/2.101 of port-type transport and ge 0/0 of port-type transport Correct Answer: D
A network administrator is configuring a tunnel interface on a branch Cisco IOS XE router to run TLOC extensions. Which configuration will extend a TLOC over a GRE tunnel to another router in the branch?


Correct Answer: C Correct Answer: C
Which feature builds transport redundancy by using the cross link between two redundant WAN Edge routers? A. TLOC extension B. quality of service C. zero-touch provisioning D. OMP Correct Answer: A
In a Cisco SD-WAN architecture, what is the role of the WAN Edge? A. It provides orchestration to assist automatic provisioning of WAN Edge routers and overlay B. It is the management plane responsible for centralized configuration and monitoring C. It is the control plane that builds and maintains network topology D. It is the data plane that is responsible for forwarding traffic Correct Answer: D
Which TCP Optimization feature is used by WAN Edge to prevent unnecessary retransmissions and large initial TCP window sizes to maximize throughput and achieve a better quality? A. SACK B. SEQ C. RTT D. SYN Correct Answer: A
A network administrator is configuring VRRP to avoid a traffic black hole when the transport side of the network is down on the primary device. What must be configured to get the fastest failover to standby? A. OMP tracking B. higher group ID number C. prefix-list tracking D. lower timer interval WAN_Release_17.1/02System_and_Interfaces/06configuring_Network_Interfaces/configuring_VRRP Community vote distribution Correct Answer: D
A network administrator is tasked to make sure that an OMP peer session is closed after missing three consecutive keepalive messages in 3 minutes. Additionally, route updates must be sent every minute. If a WAN Edge router becomes unavailable, the peer must use last known information to forward packets for 12 hours. Which set of configuration commands accomplishes this task?


Correct Answer: D Correct Answer: D
Which policy blocks TLOCs from remotes and allows TLOCs from the data center to form hub-and-spoke peering? A. centralized data policy B. localized control policy C. centralized control policy D. localized data policy Correct Answer: C
Which plane assists in the automatic onboarding of the SD-WAN routers into the SD-WAN overlay? A. data B. orchestration C. management D. control Correct Answer: B
Which command displays BFD session summary information per TLOC on vEdge routers? A. show bfd tloc-summary-list B. show bfd history C. show bfd summary D. show bfd sessions Correct Answer: A
Which component is responsible for routing protocols such as BGP and OSPF in a Cisco SD-WAN solution? A. vSmart Controller B. WAN Edge Router C. vManage D. vBond Orchestrator Correct Answer: B
Which configuration allows users to reach YouTube from a local Internet breakout?


Correct Answer: C Correct Answer: C
What are the two protocols redistributed into OMP? (Choose two.) A. OSPF B. RSVP C. LDP D. RIP E. EIGRP Correct Answer: AE
Which feature template configures OMP?


Correct Answer: A Correct Answer: A
How does the replicator role function in Cisco SD-WAN? A. WAN Edge devices advertise the rendezvous point to all the receivers through the overlay network. B. WAN Edge devices advertise the rendezvous point to all the receivers through the underlay network. C. vSmart Controllers advertise the rendezvous point to all the receivers through the overlay network. D. vSmart Controllers advertise the rendezvous point to all the receivers through the underlay network. Correct Answer: C
Which set of elements are verified by the controller to confirm the identity of edge devices? A. certificates, organization name, and serial number of the device B. organization name, serial number, and system IP of the device C. certificates, organization name, and vBond domain D. certificates, system IP, and vBond domain Correct Answer: D
Refer to the exhibit. vManage and vBond have an issue establishing a connection with each other. Which action resolves the issue? A. Change the organization name on both controllers to match viptela.com. B. configure the encapsulation ipsec command under the tunnel interface on vManage. C. Reconfigure the system IPs to belong to the same subnet. D. Remove the encapsulation ipsec command under the tunnel interface of vBond. Correct Answer: A
Refer to the exhibit. An engineer is getting a CTORGNMMIS error on a controller connection. Which action resolves this issue? A. configure a valid certificate on vSMART. B. configure a valid organization name. C. configure a valid serial number on the WAN Edge. D. configure a valid product I E. Correct Answer: B
Refer to the exhibit. A small company was acquired by a large organization. As a result, the new organization decided to update information on their Enterprise RootCA and generated a new certificate using openssl. Which configuration updates the new certificate and issues an alert in vManage Monitor | Events Dashboard?



Correct Answer: B Correct Answer: B
A vEdge platform is sending VRRP advertisement messages every 10 seconds. Which value configures the router back to the default timer? A. 2 seconds B. 5 seconds C. 1 second D. 3 seconds Correct Answer: C
Which OSPF command makes the WAN Edge router a less preferred exit from a site with a dual WAN Edge design?


Correct Answer: A Correct Answer: A
Which two services are critical for zero touch provisioning on-boarding? (Choose two.) A. EMAIL B. SNMP C. AAA D. DHCP E. DNS Correct Answer: DE
When redistribution is configured between OMP and BGP at two Data Center sites (DC) that have Direct Connection Interlink, which step avoids learning the same routes on WAN Edge routers of the DCs from LAN? A. Set down-bit on WAN Edge routers on DC1 B. define different VRFs on both DCs C. Set OMP admin distance lower than BGP admin distance D. Set same overlay AS on both DC WAN Edge routers Correct Answer: BD
Which device information is required on PNP/ZTP to support the zero touch onboarding process? A. serial and chassis numbers B. interface IP address C. public DNS entry D. system IP address Correct Answer: A
What is the purpose of `vpn 0` in the configuration template when onboarding a WAN Edge node? A. It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vEdge and vManager. B. It carries control traffic over secure IPsec connections between vSmart controllers and vEdge routers, and between vSmart and vBond. C. It carries control traffic over secure DTLS or TLS connections between vSmart controllers and vEdge routers, and between vSmart and vBond. D. It carries out-of-band network management traffic among the Cisco SD-WAN devices in the overlay network. WAN_Release_17.1/04Segmentation/02configuring_Segmentation_ (VPNs) Correct Answer: C
Which configuration step is taken on vManage after WAN Edge list is uploaded to support the on-boarding process before the device comes online? A. Verify the device certificate B. Enable the ZTP process C. Set the device as valid D. Send the list to controllers Correct Answer: C
A policy is created to influence routing path in the network using a group of prefixes. Which policy application will achieve this goal when applied to a site list? A. control-policy B. vpn-membership policy C. app-route policy D. c owd-template Correct Answer: A
On which device is a service FW address configured to insert firewall service at the hub? A. vSmart at the branch B. vEdge at the branch C. vEdge at the hub D. vSmart at the hub Correct Answer: C
Refer to the exhibit. An engineer is troubleshooting an issue where vManage and vSmart have a problem establishing a connection to vBond. Which action xes the issue? A. Remove the encapsulation ipsec command under the tunnel interface of vBond B. Reconfigure the vbond command on the vBond as vbond 150.5.1.3 local C. configure the tunnel interface on all three controllers with a color of transport D. configure encapsulation as IPsec under the tunnel interface of vManage and vSmart Correct Answer: B
Which attributes are configured to uniquely identify and represent a TLOC route? A. system IP address, link color, and encapsulation B. origin, originator, and preference C. site ID, tag, and VPN D. firewall, IPS, and application optimization Release_18.2/03Routing/01Unicast_Overlay_Routing_Overview#TLOC_Routes Correct Answer: A
Refer to the exhibit. The control connection is failing. Which action resolves the issue? A. Validate the certificates authenticity on vSmart B. Restore the reachability to the vSmart C. Import vSmart in vManager D. Upload the WAN Edge list on vManage Correct Answer: B
Which type of route advertisement of OMP can be verified? A. Origin, TLOC, and VPN B. Origin, TLOC, and service C. OMP, VPN, and origin D. OMP, TLOC, and service Release_18.2/03Routing/01Unicast_Overlay_Routing_Overview#OMP_Route_Advertisements Community vote distribution Correct Answer: D
Refer to the exhibit. An engineer is troubleshooting tear down of control connections even though a valid certificateSerialNumber is entered. Which two actions resolve the issue? (Choose two.) A. Enter a valid product ID (model) on the PNP portal B. Match the serial number file between the controllers C. Remove the duplicate IP in the network D. Restore network reachability for the controller E. Enter a valid serial number on the controllers for a given device Correct Answer: AC
Which protocol is used for the vManage to connect to the vSmart Controller hosted in Cloud? A. PnP Server B. ZTP C. HTTP D. NETCONF Correct Answer: B
Which third-party Enterprise CA server must be used for a cloud-based vSmart controller? A. RootCert B. VeriSign C. Microsoft D. RADIUS Correct Answer: A
What are the two advantages of deploying cloud-based Cisco SD-WAN controllers? (Choose two.) A. centralized control and data plane B. infrastructure as a service C. management of SLA D. centralized raid storage of data E. distributed authentication policies Correct Answer: AC
Which two image formats are supported for controller codes? (Choose two.) A. .nxos B. .qcow2 C. .iso D. .ova E. .bin Correct Answer: BD
Which two platforms for the Cisco SD-WAN architecture are deployable in a hypervisor on-premises or in IAAS Cloud? (Choose two.) A. CSR 1000v B. ISR 4431 C. vEdge 100c D. vEdge 2000 E. vEdge Cloud Correct Answer: AE
How is the scalability of the Manage increased in Cisco SD-WAN Fabric? A. Increase the bandwidth of the WAN link connected to the vManage B. Increase licensing on the vManage C. Deploy more than one vManage controllers on different physical server D. Deploy multiple vManage controllers in a cluster Correct Answer: D
Which component of the Cisco SD-WAN control plane architecture facilitates the storage of certificates and configurations for network components? A. vSmart B. WAN Edge C. vManage D. vBond Correct Answer: C
Which Cisco SD-WAN component facilitates the initial communication between WAN Edge devices to join the fabric? A. WAN Edge Router B. vSmart Controller C. vManage D. vBond Orchestrator Correct Answer: D
An engineer is troubleshooting a vEdge router and identifies a `DCONFAIL `" DTLS connection failure` message. What is the problem? A. memory issue B. certificate mismatch C. organization mismatch D. connectivity issue Correct Answer: D
What is an attribute of TLOC? A. tag B. service C. local preference D. encryption WAN_Release_17.1/06Policy_Basics/01Policy_Overview/01Viptela_Policy_Framework_Basics#:~:text=configured%20policy%20affects).-,TLOC %20Attributes% 20Used%20in%20Policies,address%2C%20color%2C%20and%20encapsulation Correct Answer: A
An engineer is troubleshooting a certificate issue on vEdge. Which command is used to verify the validity of the certificates? A. show control local-properties B. show control summary C. show certificate installed D. show certificate status Correct Answer: A
What is the behavior of vBond orchestrator? A. It builds permanent connections with vSmart controllers. B. It builds permanent connections with WAN Edge routers. C. It updates vSmart of WAN Edge routers behind NAT devices using OMP. D. It maintains vSmart and WAN Edge routers secure connectivity state. Correct Answer: C
Refer to the exhibit. An engineer is troubleshooting a control connection issue. What does `connect` mean in this show control connections output? A. Control connection is down B. Control connection is up C. Control connection attempt is in progress D. Control connection is connected Correct Answer: C
Which routing protocol is used to exchange control plane information between vSmart controllers and WAN Edge routers in the Cisco SD-WAN secure extensible network? A. BGP B. OSPF C. BFD D. OMP Correct Answer: D
In which device state does the WAN Edge router create control connections, but data tunnels are not created? A. valid B. backup C. active D. staging Correct Answer: D
What is a requirement for a WAN Edge to reach vManage, vBond, and vSmart controllers in a data center? A. OMP B. IGP C. QoS D. TLS Correct Answer: A
Company E wants to deploy Cisco SD-WAN with controllers in flaws. The company's existing WAN is on private MPLS without Internet access to controllers in flaws. An Internet circuit is added to a site in addition to the existing MPLS circuit. Which interface template establishes BFD neighbors over both transports?


Correct Answer: A Correct Answer: A
Which secure tunnel type should be used to connect one WAN Edge router to other WAN Edge routers? A. DTLS B. SSL VPN C. IPsec D. TLS Correct Answer: C
What is the default value (in milliseconds) set for the poll interval in the BFD basic configuration? A. 300,000 B. 600,000 C. 900,000 D. 1,200,000 Correct Answer: B
Which plane builds and maintains the network topology and makes decisions on traffic ows? A. data B. orchestration C. management D. control Correct Answer: D
How is TLOC defined? A. It is represented by a unique identifier to specify a site in a SD-WAN architecture. B. It speci es a Cisco SD-WAN overlay in a multitenant vSMART deployment. C. It is represented by a group of QoS policies applied to a WAN Edge router. D. It is a unique collection of GRE or IPsec encapsulations, link color, and system IP address. Correct Answer: D
Which vBond system configuration under VPN 0 allows for a routable public IP address even if the DNS name, hostname, or IP address of the vBond orchestrator are omitted? A. WAN B. local C. dns-name D. vbond-only Correct Answer: B
Which two prerequisites must be met before the Cloud onRamp for IaaS is initiated on vManage to expand to the flaws cloud? (Choose two.) A. Attach an OSPF feature template to the flaws cloud Edge router template. B. Attach the AmazonCreateVPC and AmazonProvisionEC2 permission policy to the IAM account. C. Subscribe to the SD-WAN Edge router AMI in the flaws account. D. Attach a device template to the cloud WAN Edge router to be deployed in the flaws. E. Preprovision the transit VPC in the flaws region. Correct Answer: CD
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections between the WAN Edge devices that form the Cisco SD-WAN fabric? A. APIC-EM B. vSmart C. vManage D. vBond Correct Answer: B
In a Cisco SD-WAN network, which component is responsible for distributing route and policy information via the OMP? A. vManage B. vSmart Controller C. vBond Orchestrator D. WAN Edge Router Correct Answer: B
Which two hardware platforms support Cisco IOS XE SD-WAN images? (Choose two.) A. ISR4000 series B. ISR9300 series C. vEdge-1000 series D. ASR9000 series E. ASR1000 series Correct Answer: AE
For data plane resiliency, what does the Cisco SD-WAN software implement? A. multiple vBond orchestrators B. establishing a nity between vSmart controllers and WAN Edge routers C. OMP D. BFD Correct Answer: D
What is a default protocol for control plane connection? A. HTTPS B. TLS C. IPsec D. DTLS WAN_Release_16.3/05Security/02configuring_Security_Parameters Correct Answer: D
Refer to the exhibit. Which configuration configures IPsec tunnels in active and standby? A. vpn 1 service netsvc1 interface ipsec1 ipsec2 from-vsmart lists vpn-list 1 vpn 1 B. vpn 0 service netsvc1 interface ipsec1 ipsec2 from-vsmart lists vpn-list 0 vpn 0 C. vpn 1 service netsvc1 interface ipsec1 ipsec2 vpn-list 1 count ServicePSec1_275676046 from-vsmart lists vpn-list 1 vpn 1 D. vpn 0 service netsvc1 interface ipsec1 ipsec2 vpn-list 1 count ServicePSec1_275676046 from-vsmart lists vpn-list 0 vpn 0 Correct Answer: C
Which component of the Cisco SD-WAN control plane architecture should be located in a public Internet address space and facilitates NAT- traversal? A. WAN Edge B. vSmart C. vBond D. vManage Correct Answer: C
An organization wants to use the Cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with applications in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement? A. Cloud onRamp for Colocation B. Cloud onRamp for IaaS C. Cloud Services Platform D. VNF Service Chaining Correct Answer: A
Which Cisco SD-WAN WAN Edge platform supports LTE and Wi-Fi? A. ISR 1101 B. ASR 1001 C. CSR 1000v D. vEdge 2000 Correct Answer: A
Refer to the exhibit. What does the BFD value of 8 represent? A. dead timer of BFD session B. poll-interval of BFD session C. hello timer of BFD session D. number of BFD sessions Correct Answer: D
A network administrator is bringing up one WAN Edge router for branch connectivity. Which types of tunnels form when the WAN edge router connects to the Cisco SD-WAN fabric? A. DTLS or TLS tunnel with vSmart controller and IPsec tunnel with vBond controller B. DTLS or TLS tunnel with vBond controller and IPsec tunnel with vManage controller C. DTLS or TLS tunnel with vBond controller and IPsec tunnel with other WAN Edge routers D. DTLS or TLS tunnel with vSmart controller and IPsec tunnel with other WAN Edge routers Correct Answer: D
If Smart Account Sync is not used, which Cisco SD-WAN component is used to upload an authorized serial number file? A. WAN Edge B. vSmart C. vBond D. vManage Correct Answer: D
Which port is used for vBond under controller certificates if no alternate port is configured? A. 12344 B. 12345 C. 12347 D. 12346 Correct Answer: D
In the Cisco SD-WAN solution, vSmart controller is responsible for which two actions? (Choose two.) A. Authenticate and authorize WAN Edge routers. B. configure and monitor WAN Edge routers. C. Distribute route and policy information via OMP. D. Distribute the IP address from DHCP server to WAN Edge routers. E. Distribute crypto key information among WAN Edge routers. Correct Answer: CE
When a WAN Edge device joins the Cisco SD-WAN overlay, which Cisco SD-WAN component orchestrates the connection between the WAN Edge device and a vSmart controller? A. vManage B. vBond C. OMP D. APIC-EM Correct Answer: B
In an flaws cloud, which feature provisions WAN Edge routers automatically in Cisco SD-WAN? A. Cloud OnRamp B. Cloud app C. vAnalytics D. Network Designer Correct Answer: A
A large retail organization decided to move some of the branch applications to the flaws cloud. How does the network architect extend the in- house Cisco SD- WAN branch to cloud network into flaws? A. Create virtual instances of vSmart Cloud through the flaws online software store B. Create GRE tunnels to flaws from each branch over the Internet C. Install the flaws Cloud Router in the main data center and provide the connectivity from each branch D. Create virtual WAN Edge devices Cloud through the flaws online software store Correct Answer: D
Which two products are used to deploy Cisco WAN Edge Router virtual platforms? (Choose two.) A. Sun Enterprise M4000 Server running Sun Solaris B. Sun SPARC Node running AIX C. Cisco UCS D. HP ProLiant DL380 Generation 10 running HP-UX E. Cisco ENCS 5000 Series Correct Answer: CE
A bank is looking for improved customer experience for applications and reduce overhead related to compliance and security. Which key feature or features of the Cisco SD-WAN solution will help the bank to achieve their goals? A. Integration with PaaS providers to offer the best possible application experience B. QoS including application prioritization and meeting critical applications SLA for selecting optimal path C. Implementation of BGP across the enterprise routing for selecting optimal path D. Implementation of a modern age core banking system Correct Answer: A