300-635 Practice Test Free – 46 Questions to Test Your Knowledge
Are you preparing for the 300-635 certification exam? If so, taking a 300-635 practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 46 free 300-635 practice questions designed to help you test your skills and identify areas for improvement.
By taking a free 300-635 practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
46 Free 300-635 Practice Questions
Below, you will find 46 free 300-635 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
What are two main guiding principles of REST? (Choose two.)A. cacheable
B. trackable
C. stateless
D. single-layer system
E. stateful
Which two statements about gRPC are true? (Choose two.)A. It is an IETF draft.
B. It is an IETF standard.
C. It runs over SSH.
D. It is an open source initiative.
E. It runs over HTTPS.
Which statement about synchronous and asynchronous API calls is true?A. Synchronous API calls wait to return until a response has been received.
B. Synchronous communication is harder to follow and troubleshoot.
C. Synchronous API calls must always use a proxy server.
D. Asynchronous communication uses more overhead for client authentication.
A set of automation scripts work with no issue from a local machine, but an experiment needs to take place with a new package found online.
How is this new package isolated from the main code base?A. Add the new package to your requirements.txt file.
B. Create a new virtual machine and perform a pip install of the new package.
C. Perform a pip install of the new package when logged into your local machine as root.
D. Create a new virtual environment and perform a pip install of the new package.
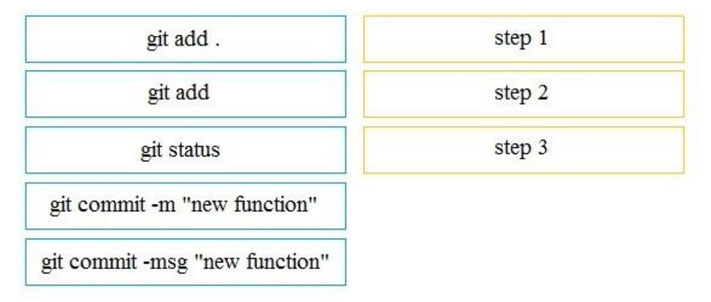
DRAG DROP -
A file named myfunc.py has been edited. Drag and drop the steps from the left that ensure that this file is committed to the local Git repository and verify its status into the correct order on the right. Not all options are used.
Select and Place:
Which two benefits of using network configuration tools such as Ansible and Puppet to automate data center platforms are valid? (Choose two.)A. consistency of systems configuration
B. automation of repetitive tasks
C. ability to create device and interface groups
D. ability to add VLANs and routes per device
E. removal of network protocols such as Spanning Tree
When should the API Inspector be used?A. to send an API request to the APIC
B. to learn or identify the sequence of API calls for a specific operation in the APIC GUI
C. to verify the XML structure of an object based on a specific operation in the APIC GUI
D. to launch an Ansible playbook
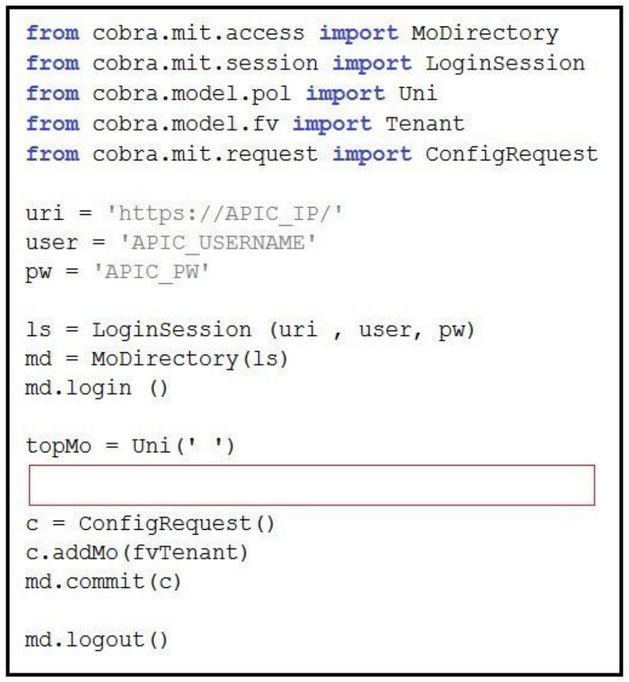
Refer to the exhibit.
Which action does the execution of this ACI Cobra Python code perform?A. It prints all LLDP neighbor MAC and IP addresses.
B. It prints all Cisco Discovery Protocol neighbor MAC and IP addresses.
C. It prints all endpoint MAC and IP addresses.
D. It prints all APIC MAC and IP addresses.
Refer to the exhibit.
The code should create a new tenant named Cisco via the Cobra SDK, which shows up after the execution of this script in the APIC dashboard.
Which code must he inserted into the red box to create this tenant?A. fvTenant = NewTenant(name='Cisco')
B. tenant = Tenant(topMo. name='Cisco')
C. fvTenant = Tenant(topMo, name='Cisco')
D. fvTenant = Tenant('Cisco')
What is a key characteristic of an ACI policy model?A. Logical and concrete domains are separated.
B. All configuration is carried out against concrete entities.
C. It allows communications with newly connected devices.
D. Network administrators configure logical and physical system resources directly.
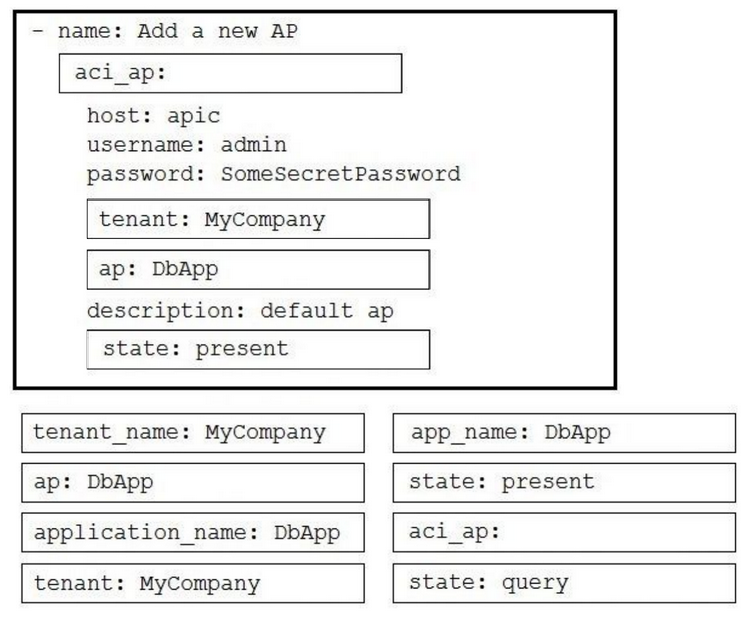
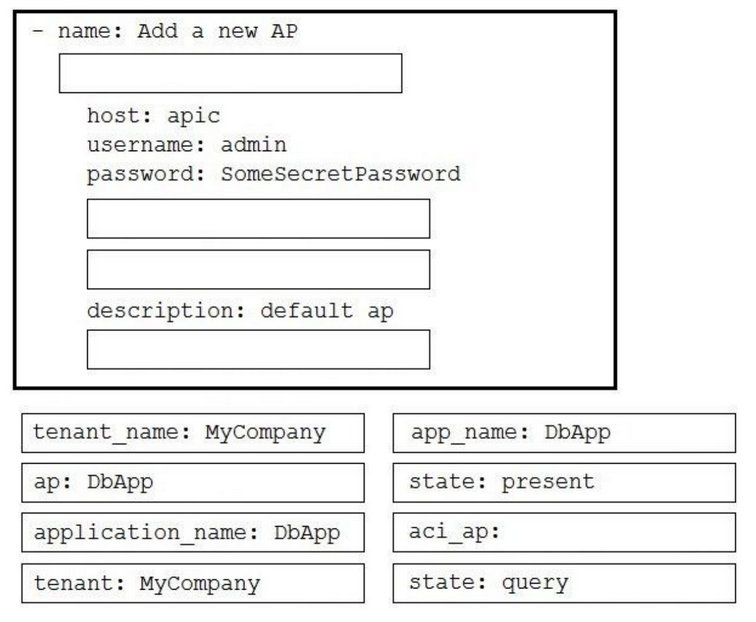
DRAG DROP -
Drag and drop the correct YAML components from the bottom onto the correct blanks within the Ansible playbook to create a new application profile called
"DbApp" using the Ansible ACI module. Not all options are used.
Select and Place:
What is the default data encoding for the response output of the ACI APIC API inspector?A. CSV
B. JSON
C. XML
D. YAML
Which Kubernetes container network interface provides intent-based networking from the same pane of glass that VMs and bare-metal servers are managed?A. ACI CNI plug-in
B. Contiv CNI plug-in
C. Ingress CNI plug-in
D. Calico CNI plug-in
Which Python code creates a VRF in an ACI tenant using the Cobra SDK?A. Vrf(fvTenant(uniMo, 'CustA'), 'CustA_VRF')
B. Ctx(Tenant(uniMo, 'CustA'), 'CustA_VRF')
C. Vrf(Tenant(uniMo, 'CustA'), 'CustA_VRF')
D. Ctx(fvTenant(uniMo, 'CustA'), 'CustA_VRF')
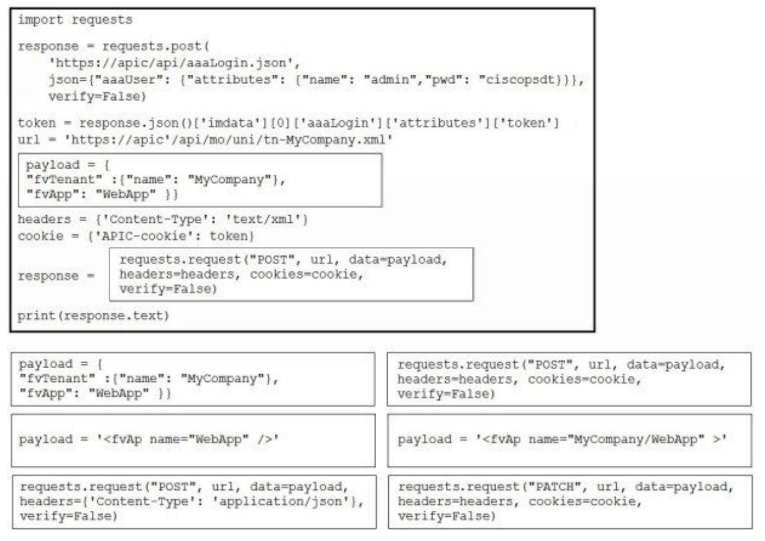
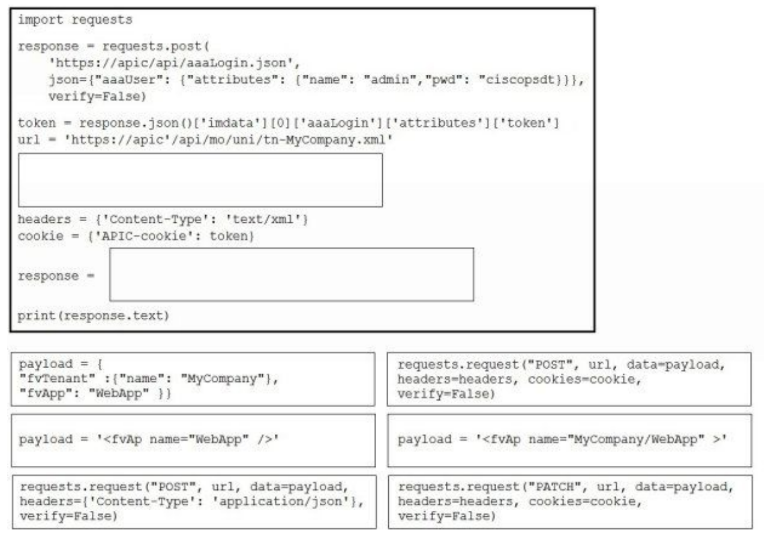
DRAG DROP -
Drag and drop the correct code snippets into the Python code to create a new application profile "WebApp" using the ACI REST API. Not all options are used.
Select and Place:
How should the Kubernetes manifests be modified to allow Kubernetes environment integration with Cisco ACI?A. The metadata section must contain the Cisco APIC management IP.
B. The manifest does not have to be changed, but the Kubernetes object is not discovered by Cisco ACI if this is not defined in the manifest.
C. The manifests must include ACI EPG reference.
D. No change is needed to perform this action.
Which two components are attributes of an ACI MIT managed object? (Choose two.)A. MO
B. RN
C. UNI
D. DN
E. URL
Which two items are types of application isolation options available when Kubernetes is deployed with the ACI CNI plug-in? (Choose two.)A. VM Isolation
B. Cluster Isolation
C. Server Isolation
D. Process Isolation
E. Namespace Isolation
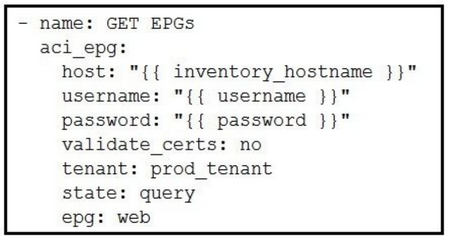
Refer to the exhibit.
Which two statements are true about this API GET request to the ACI APIC? (Choose two.)A. The API call creates a new 10G interface in the APIC.
B. The API call reads information from a managed object.
C. The API response is encoded in JSON.
D. The API call reads information from an object class.
E. The API response is encoded in XML.
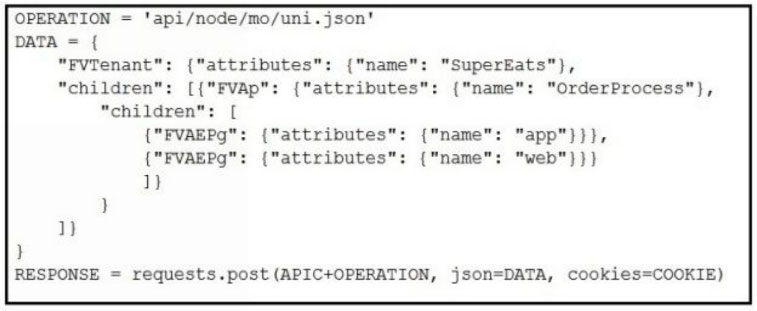
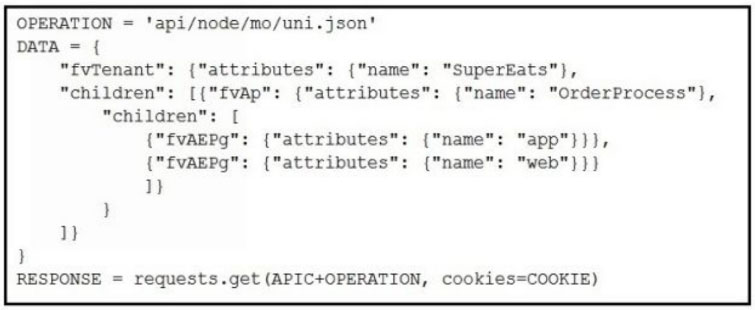
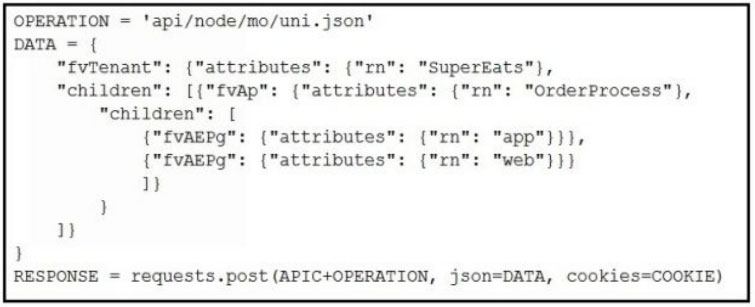
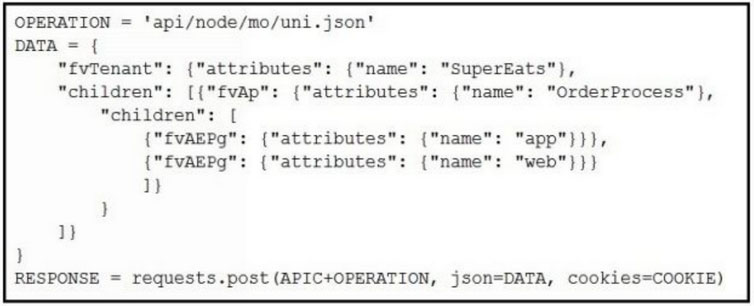
Which Python snippets create an application policy named OrderProcess that contains two application endpoint groups under Tenant SuperEats using direct calls to the ACI REST API? Assume that authentication and library imports are correct.
A.
B.
C.
D.
What is the network bootstrap program used by Cisco NX-OS iPXE?A. NETBOOT
B. NX-OS iPXE
C. iPXE-POAP
D. Mini-OS
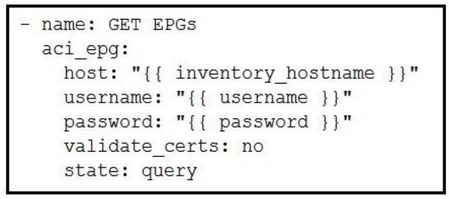
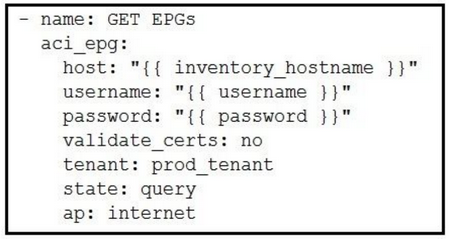
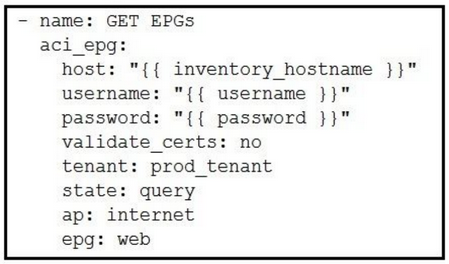
Which Ansible playbook fragment returns the fewest queried ACI endpoint groups?
A.
B.
C.
D.
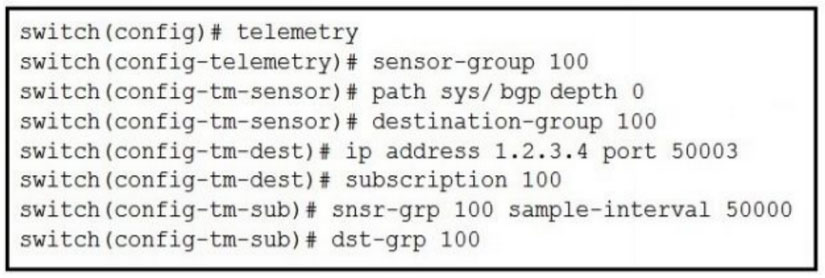
Refer to the exhibit.
How often is the subscription stream for sys/bgp going to be sent?A. 5 sec
B. 5 msec
C. 5000 sec
D. 5 min
How is an ACI class name composed?A. :Method
B. ClassName:Method
C. Package:ClassName
D. MitName:Method
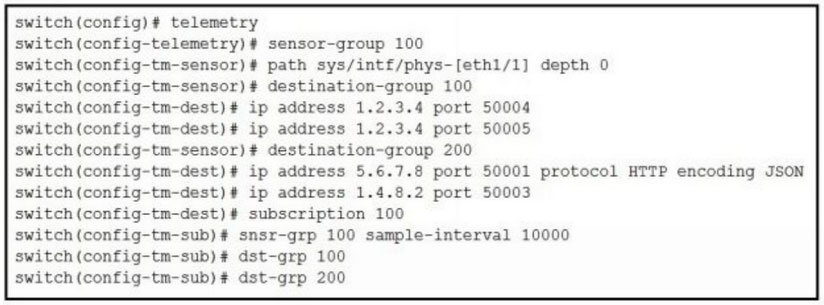
Refer to the exhibit.
Where and how often does the subscription stream data for Ethernet port 1/1?A. to four different destinations every 10000 microseconds
B. to four different destinations every 100 milliseconds
C. to four different destinations every 10 seconds
D. to four different destinations every 10000 seconds
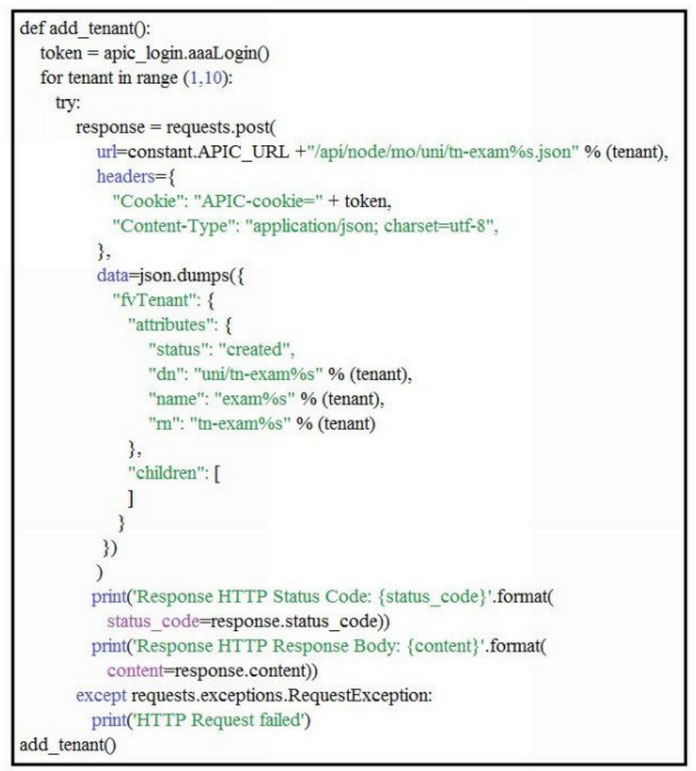
Refer to the exhibit.
Assuming a new ACI instance, what is the result when this script is run?A. Ten objects are created and subsequently deleted.
B. Nine objects are created.
C. An exception is thrown.
D. Ten objects are created.
Which two statements describe the authentication method used with Cisco Intersight REST API Requests? (Choose two.)A. The REST API request contains a base64-encoded signature of the message content and headers.
B. The REST API request message body is encoded as a SHA384 hash and then signed with the API Key ID.
C. The Cisco Intersight Web service verifies the signature of incoming request with the RSA public key for the API Key ID.
D. The incoming REST API request is challenged by the Cisco Intersight Web service with a request for the RSA private key.
E. The message body is encoded as a SHA256 hash if the message body is not empty and then signed with the API Key ID.
Which authentication method is used when the REST API of the Cisco UCS Director is accessed?A. Bearer ((Bearer Token))
B. HTTP Basic Auth
C. RestAuth: ((User's Auth Token))
D. X-Cloupia-Request-Key: ((User's Auth Token))
Which two components are required from the Cisco Intersight REST API Authentication? (Choose two.)A. SHA256 hash of the message body and message headers.
B. SHA256 hash of the message body, including empty message bodies.
C. RSA private key with a key size of 2048.
D. RSA private key with a key size of 1024.
E. SHA384 hash of the message body, excluding empty message bodies.
Which two capabilities apply to the DCNM API? (Choose two.)A. DCNM provides an XML-based SOAP API.
B. DCNM requires a license to use the API.
C. Some features of DCNM must be configured through the GUI.
D. All API operations can be performed using the DCNM GUI.
E. DCNM provides a REST-based API.
What are two capabilities of the DCNM REST API? (Choose two.)A. uses the dcnm-token header for requests authentication after initial basic authentication
B. uses basic authentication without encoding for username and password
C. supports HTTP until release 11.0(1)
D. uses bearer key authorization
E. is separated into Classic LAN, LAN Fabric, Media Controller, and SAN Management categories
During the process of starting a Python network telemetry collector, which command starts the Cisco bigmuddy-network-telemetry-collector from GitHub?A. model driven telemetry
B. telemetry_receiver.py --ip-address --port
C. telemetry_receiver.py --destination --url
D. streaming telemetry
When the Cisco bigmuddy-network-telemetry-collector from GitHub is used, which command displays only the message headers?A. --print
B. --all
C. --brief
D. --print-all
Refer to the exhibit.
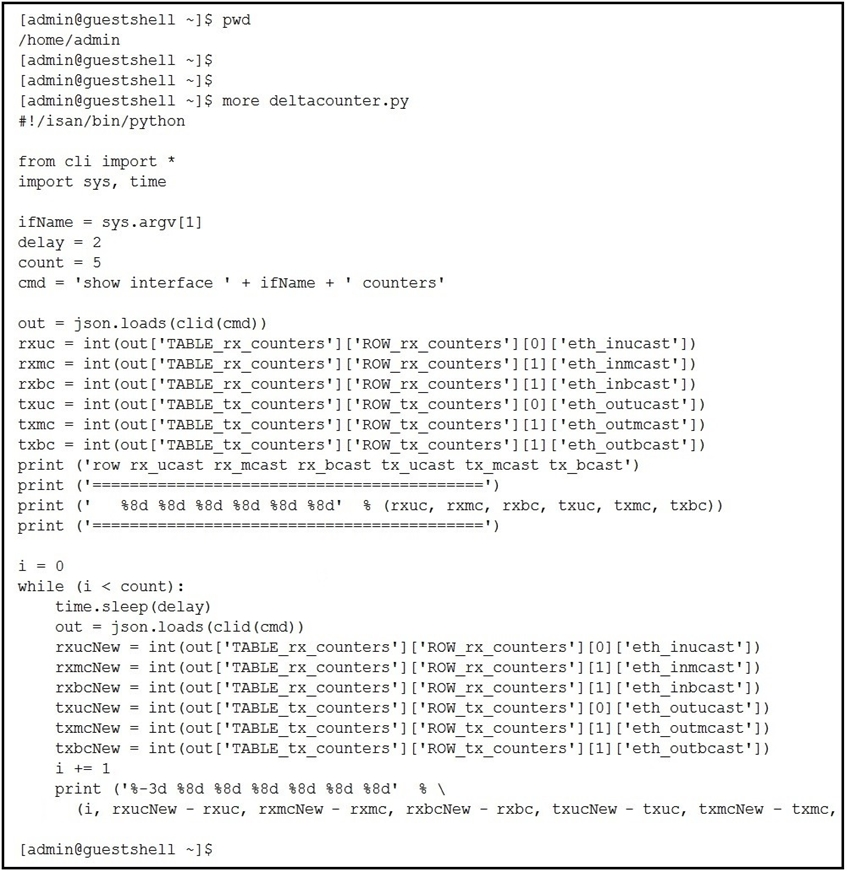
The script is called deltacounters.py and it is currently inside a Guest Shell container running inside a Cisco NX-OS switch.
Which Cisco NX-OS command results in a successful execution of this script?A. python /home/admin/bootflash:deltacounters.py ethemet1/1
B. show python bootflash:deltacounters.py ethernet1/1
C. guestshell run python /home/admin/deltacounter.py ethernet1/1
D. guestshell execute python /home/admin/deltacounter.py ethernet1/1
Which NX-API request queries the MAC address table?
A.
B.
C.
D.

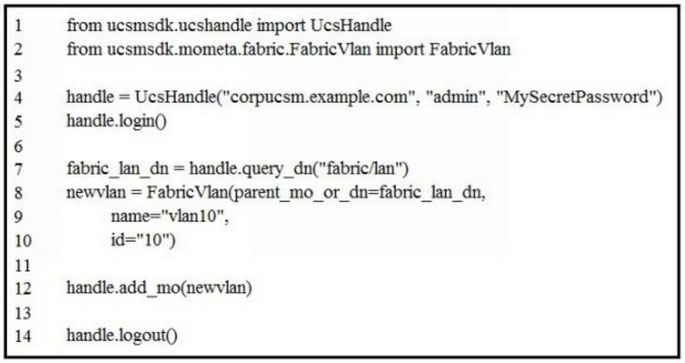
Refer to the exhibit.
Which change allows the code to configure VLAN 10 in the Cisco UCS?A. Lines 8 and 9 should have a line continuation at the end.
B. Line 13 should include "handle.commit()".
C. Line 4 should include transport 443 option.
D. Line 3 should add an import for query_dn.
Using the NX-API CLI JSON-RPC interface, which two Python data structure and requests call create an SVI? (Choose two.)
A.
B.
C.
D.
E.

Which procedure accesses the REST API browser within Cisco UCS Director?A. Send an HTTP GET request to https://[UCS Director IP]/api/get_resources/.
B. Log in as the user REST/user to access the REST API interface.
C. Enable the Developer menu. Select Orchestration in the UI, then select the REST API browser tab.
D. Select the API browser from the Cisco UCS Director End User Portal catalog of services.
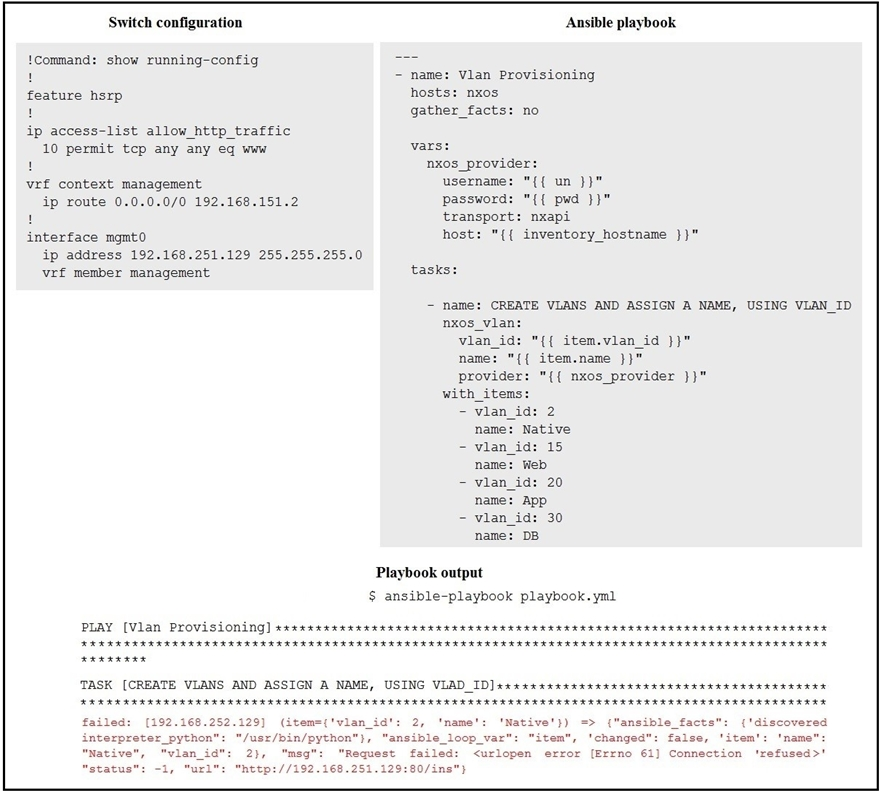
Refer to the exhibit.
The exhibit shows a Cisco NX-OS switch configuration, an Ansible playbook, and the output of running this playbook. The playbook failed due to error "msg'
'Request failed ', 'status' -1, "url" "http://192.168.251.129:80/ins".
Which Cisco NX-OS configuration command resolves this failure?A. feature nxapi
B. http-server enabled
C. interface mgmt0; ip access-group allow_http_traffic in
D. feature http
Which programming language are the Cisco UCS Director custom workflow tasks written in?A. C++
B. Python
C. Java
D. Cloupia Script
Which two bootstrap technologies are supported by Cisco NX-OS platforms? (Choose two.)A. iPXE
B. PNP
C. POAP
D. BOOTP
E. DHCP
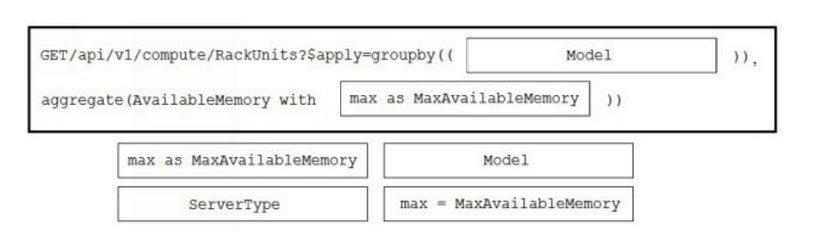
DRAG DROP -
A co-worker is using Cisco Intersight to determine the maximum available memory per server for their company's data center. Drag and drop the code to complete the Cisco Intersight API call that provides the desired results. Not all options are used.
Select and Place:

Which action allows Docker daemon persistence during switchover on the Cisco Nexus 9500 Series Switches running Cisco NX-OS?A. Change the Docker configuration to include the live restore option.
B. Copy the dockerpart file manually to the standby supervisor after performing the switchover.
C. Copy the dockerpart file manually to the standby supervisor before performing the switchover.
D. The system takes automatic action.
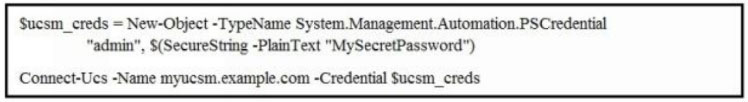
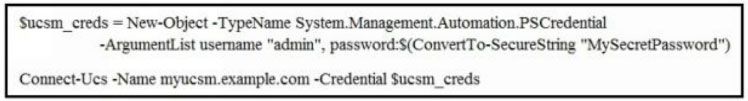
Which Cisco UCS PowerTool commands initiate a Cisco UCS Manager connection?
A.
B.
C.
D.

Which two statements apply to authentication when using the Cisco Intersight API? (Choose two.)A. Each API Key can be assigned specific roles but not privileges.
B. Secret Key is only available at API Key creation time.
C. An API Key is composed of a Key ID and Secret Key.
D. The user credentials for the cisco.com accounts are shared with the Cisco Intersight Web Service.
E. An API Key is composed of a keyId and sessionCookie.
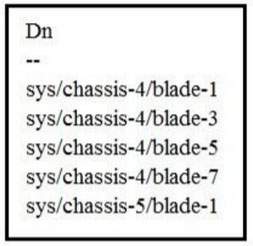
Refer to the exhibit.
Which two Cisco UCS PowerTool commands provide this output? (Choose two.)A. Get-UcsServer | Select-Object Dn
B. Get-UcsRack Systems | Select-Object Dn
C. Get-UcsBlade | Select-Object Dn
D. Get-UcsRackUnit | Select-Object Dn
E. Get-UcsSystems | Select-Object Dn
Get More 300-635 Practice Questions
If you're looking for more 300-635 practice test free questions, click here to access the full 300-635 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 300-635 certification journey!