300-910 Practice Test Free – 50 Questions to Test Your Knowledge
Are you preparing for the 300-910 certification exam? If so, taking a 300-910 practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 50 free 300-910 practice questions designed to help you test your skills and identify areas for improvement.
By taking a free 300-910 practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
50 Free 300-910 Practice Questions
Below, you will find 50 free 300-910 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
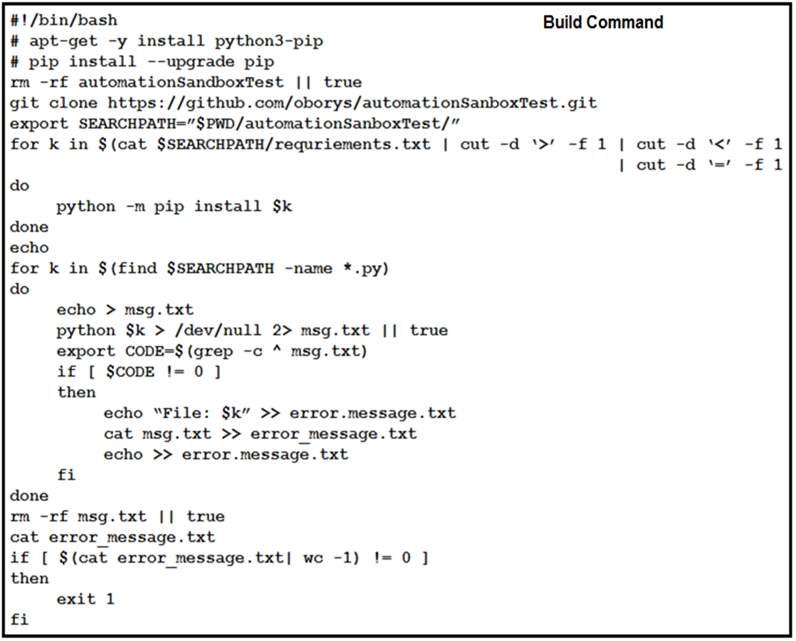
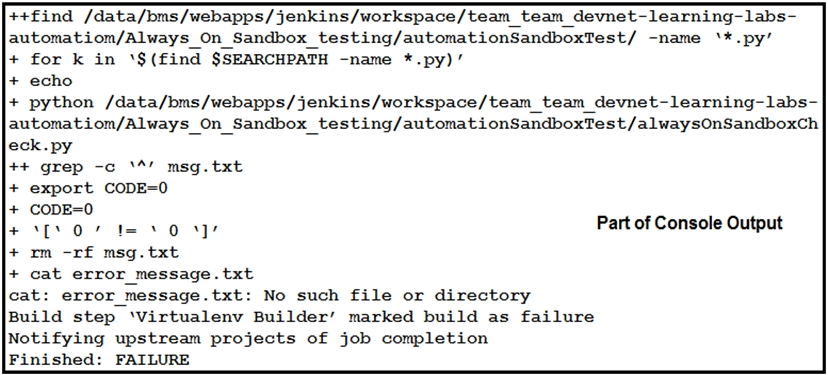
Refer to the exhibit. How should the Jenkins job be troubleshooted based on the error provided?A. Verify what the responding file created.
B. Update pip.
C. Install dependencies.
D. Place the code in a container and run the job again.
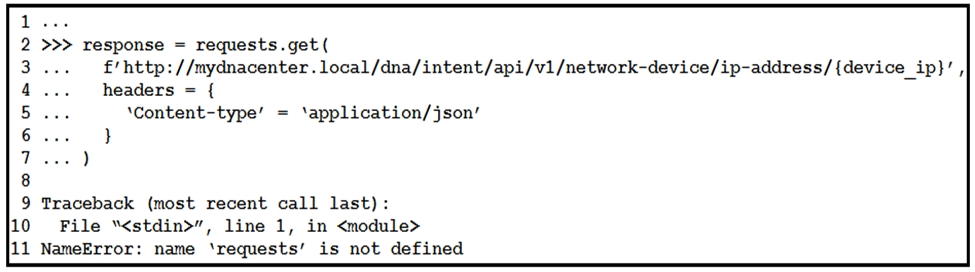
Refer to the exhibit. What is causing the requests code to fail?A. Rython3 is not compatible with requests.
B. The requests library is not imported.
C. The requests library is not installed.
D. The requests coming into stdin fail because device_ip cannot be parsed.
What are two benefits of Infrastructure as Code? (Choose two.)A. It enables continuous integration.
B. It allows for management control.
C. It ensures consistency.
D. It improves application monitoring.
E. It reduces risk.
A three-tier web application must be moved to containers. A webserver is already in place, and the middleware container can talk to a central database server. The hostname of the database server is known, but the name of the middleware server must be provided to the webserver.
In which file should the name of the middleware server be configured?A. Docker Service discovery daemon
B. Docker Swarm
C. Docker Compose
D. Dynamic Host Configuration Protocol
Microservices architecture pattern has been applied and the system has been architected as a set of services. Each service is deployed as a set of instances for throughput and availability. In which two ways are these services packaged and deployed? (Choose two.)A. Service instances must be isolated from one another.
B. Service must be independently deployable and scalable.
C. Service are written using the same languages, frameworks, and framework versions.
D. Service must be dependent, deployable, and scalable.
E. Service instances do not need to be isolated from one another.
Which two actions help limit the attack surface of your Docker container? (Choose two.)A. Run only a single service in each container.
B. Run all services in a single image.
C. Use version tags for base images and dependencies.
D. Use Kali Linux as a base image.
E. Download images over HTTPS supporting sites.
A company has experienced serious growth and the hosted applications are getting more and more hits. Based on the increased work load, applications have started to show signs of reduced performance, which is affecting the user experience.
Which two server metrics should be tracked to ensure that the customer experience remains within acceptable limits? (Choose two.)A. application feature sprawl
B. CPU peak usage
C. CPU average usage
D. microservices count
E. CPU frequency
A DevOps engineering wants to build an application implementation based on the CI/CD pipeline model. Which service should be used to provide hosted continuous service for open and private projects?A. Ansible
B. pyATS
C. Genie CLI
D. Travis CI
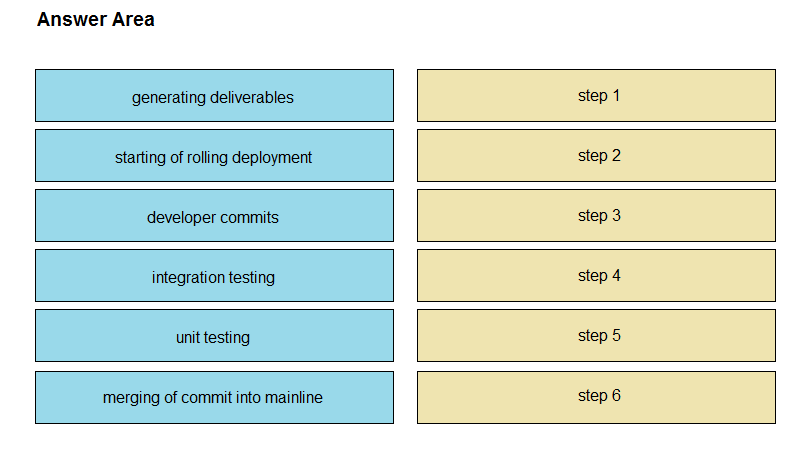
DRAG DROP -
Drag and drop the operations from the left into the correct order on the right when using CI/CD, assuming that there are no failures or conflicts.
Select and Place:
Which description of a canary deployment is true?A. deployment by accident
B. deployment that is rolled back automatically after a configurable amount of minutes
C. deployment relating to data mining development
D. deployment to a limited set of servers or users
A new version of an application is being released by creating a separate instance of the application that is running the new code. Only a small portion of the user base will be directed to the new instance until that version has been proven stable. Which deployment strategy is this example of?A. recreate
B. blue/green
C. rolling
D. canary
Configuration changes to the production network devices are performed by a CI/CD pipeline. The code repository and the CI tool are running on separate servers.
Some configuration changes are pushed to the code repository, but the pipeline did not start.
Why did the pipeline fail to start?A. The CI server was not configured as a Git remote for the repository.
B. The webhook call from the code repository did not reach the CI server.
C. Configuration changes must be sent to the pipeline, which then updates the repository.
D. The pipeline must be started manually after the code repository is updated.
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all of the modules in the source code that were developed using
TDD?A. soak testing
B. unit testing
C. load testing
D. volume testing
A CI/CD pipeline that builds infrastructure components using Terraform must be designed. A step in the pipeline is needed that checks for errors in any of the .tf files in the working directory. It also checks the existing state of the defined infrastructure.
Which command does the pipeline run to accomplish this goal?A. terraform plan
B. terraform check
C. terraform fmt
D. terraform validate
FILL BLANK -
Fill in the blank to complete the statement.
A user wants a Kubernetes deployment to run three separate pods of a web application at one time. In the deployment YAML, the user must configure the
__________ field in the _________ subsection.
Which two practices help make the security of an application a more integral part of the software development lifecycle? (Choose two.)A. Add a step to the CI/CD pipeline that runs a dynamic code analysis tool during the pipeline execution.
B. Add a step to the CI/CD pipeline that runs a static code analysis tool during the pipeline execution.
C. Use only software modules that are written by the internal team.
D. Add a step to the CI/CD pipeline to modify the release plan so that updated versions of the software are made available more often.
E. Ensure that the code repository server has enabled drive encryption and stores the keys on a Trusted Platform Module or Hardware Security Module.
FILL BLANK -
Fill in the blanks to complete the line of Python code that sends a message to a Webex Teams room or person.

A DevOps engineer must validate the working state of the network before implementing a CI/CD pipeline model. Which configuration management tool is designed to accomplish this?A. Jenkins
B. Genie CLI
C. Travis CI
D. Python YAML data libraries
What is the purpose of using a build tool in software development?A. It complies source code into binaries and executables.
B. It provides a way to edit source code using a graphical interface.
C. It is a manual process that is followed to build software.
D. It tracks bugs and incidents in a built application.
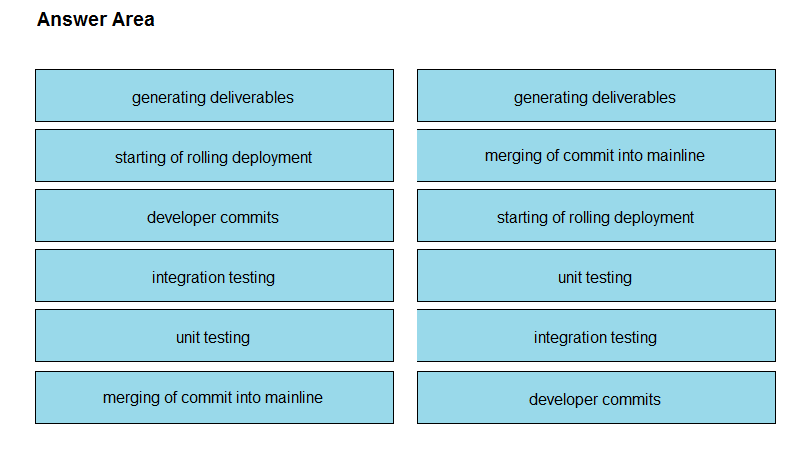
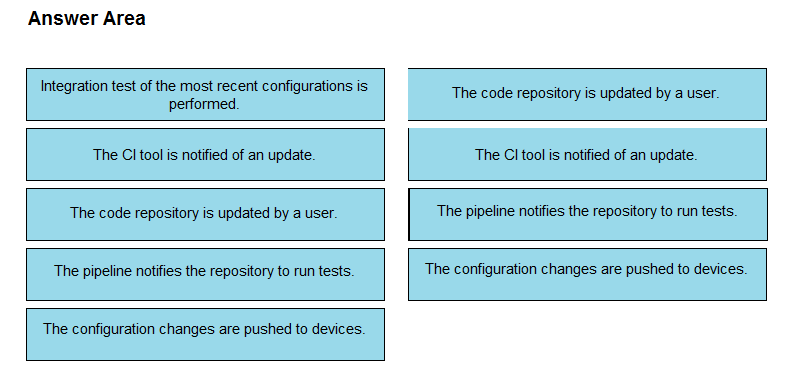
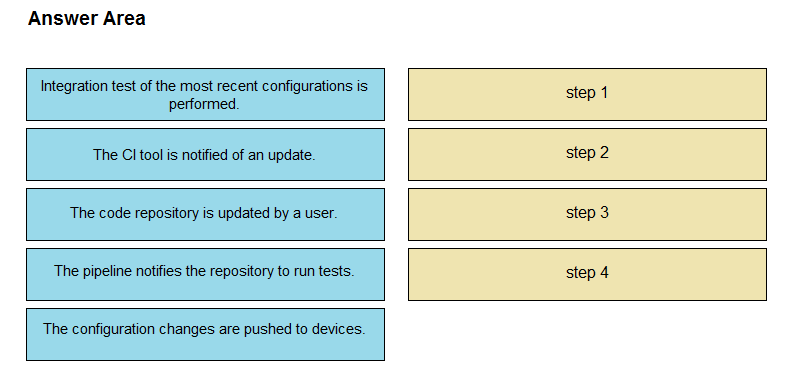
DRAG DROP -
The IaC configuration for an application is being deployed using a CI/CD pipeline. Drag and drop the steps for this pipeline from the left into the correct order that they would be executed on the right. Not all options are used.
Select and Place:
What are two reasons a Docker golden image should be updated? (Choose two.)A. when there is a change to a username or password in the Docker secrets
B. when the application has a new release
C. when a fix for a security vulnerability is released
D. when a change is needed to an environment variable in the Dockerfile
E. when the base image is nearing the end of life
Which method is a safe way to provide a username/password combination to an application running as a service in a Docker container?A. encode the value with base64 in a secure DNS CTEXT entry
B. as an environment variable in the Dockerfile
C. Docker environment variable
D. Docker secrets
Which Docker command is used to start an interactive Bash shell in a running container named "test"?A. docker attach -it test /bin/bash
B. docker run -it test /bin/bash
C. docker exec -it test /bin/bash
D. docker run test /bin/bash
A DevOps engineer has built a container to host a web-server and it must run as an executable. Which command must be configured in a Dockerfile to accomplish this goal?A. ENTRYPOINT
B. ENTRYPOINT ["/usr/sbin/apache2ctl", "-D", "FOREGROUND"]
C. ENTRYPOINT ["BACKGROUND", "-D", "/usr/sbin/apache2ctl"]
D. ENTRYPOINT {usr/sbin/apache2ctl}
A DevOps engineer has built a new container and must open port 8080 for intercontainer communication. Which command must be added in a Dockerfile to accomplish this goal?A. EXPOSE 8080
B. FIREWALL ADD-PORT 8080
C. PORT 8080
D. OPEN PORT 8080
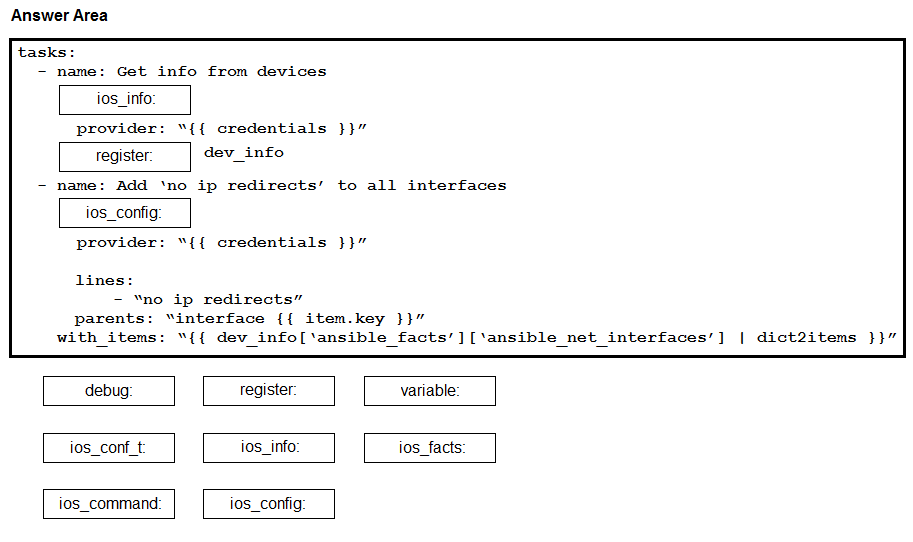
DRAG DROP -
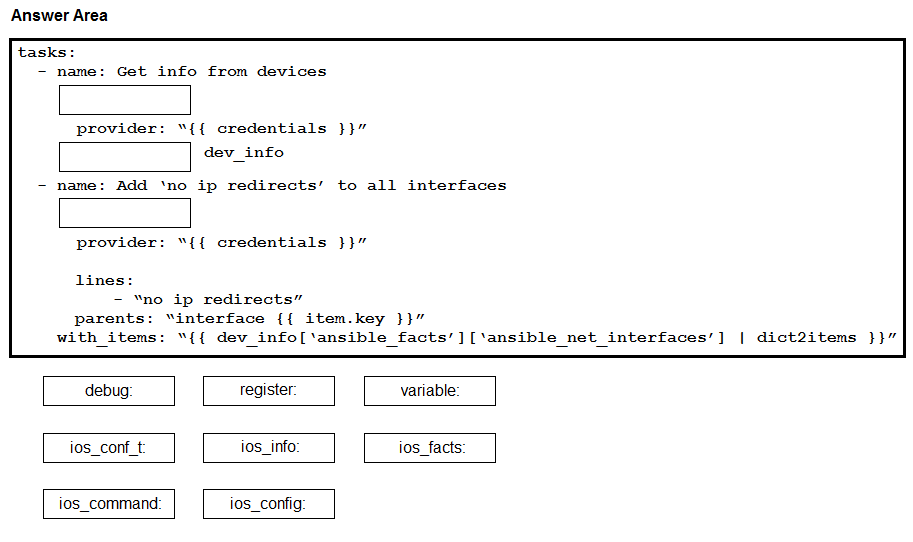
Construct an Ansible script to gather information about target routers and then use it to apply no ip redirects to every interface on each device. Drag and drop the code from the bottom onto the correct location in the exhibit to complete the tasks section of the Ansible playbook so that it accomplishes your goal.
Select and Place:
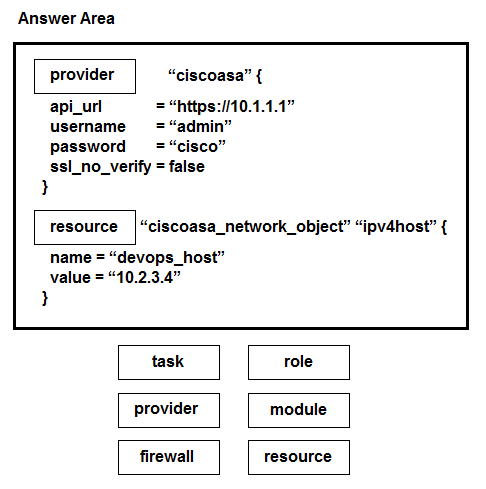
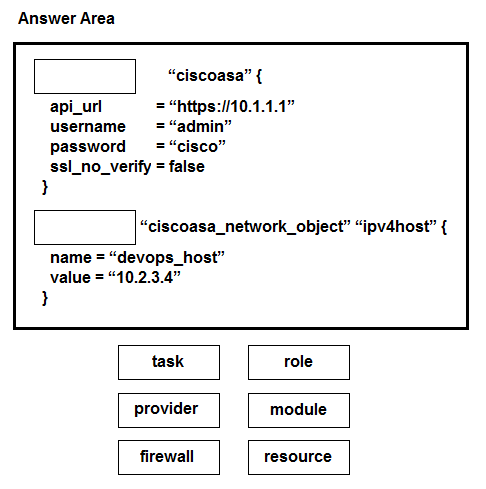
DRAG DROP -
Drag and drop the commands from the bottom onto the correct Terraform code in the exhibit to push a network object to a Cisco ASA Firewall device.
Select and Place:
An interface on a router as a Layer 3 link has been configured to another device by updating an Ansible playbook that is executed via a CI/CD pipeline. The
Ansible playbook was written to push the configuration change using the ios_config module. Which automated test validates that the interface is functioning as it should?A. Add a pipeline step that runs the playbook a second type. If it does not modify the device on the second run, then the interface is correctly configured.
B. Automated testing is already built in because the playbook execution is successful only after Ansible validates that it applied the change.
C. Add a pipeline step that captures and parses the packet flow for the interface.
D. Add a pipeline step that captures and parses the show ip interface output so that the operational state can be referenced.
Which two characteristics of a build tool that is used in an automated build pipeline? (Choose two.)A. It runs unit tests against code that is committed.
B. It builds your software on the production environment.
C. It builds your software when changes are committed.
D. It builds your software every 500 milliseconds.
E. It must have a plug-in for Puppet and Maven.
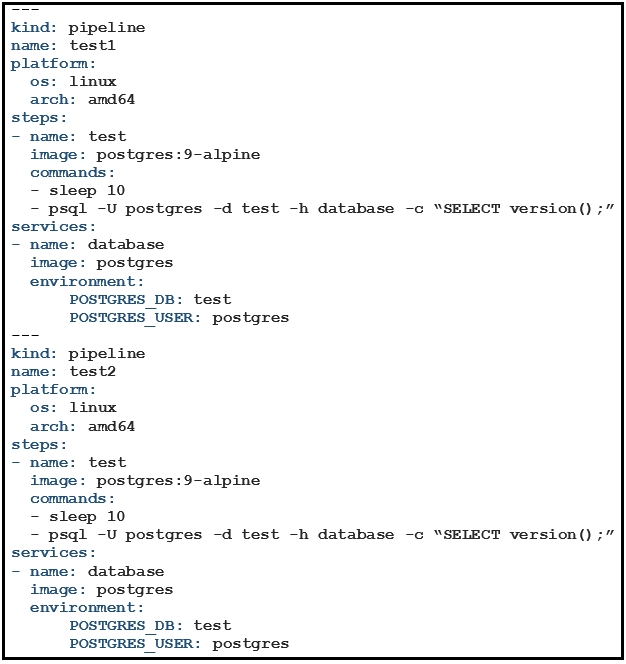
Refer to the exhibit. What is the user doing with Drone in this automated test?A. testing Alpine Linux versus Ubuntu Linux
B. testing a PostgreSQL DB against multiple architectures
C. testing only the amd64 architecture
D. testing PostgreSQL deployment in an Alpine Linux VM
A developer has created a deployment that should launch a pod to run their database service. The pod should launch with a metadata name of "Cisco-DB," and the developer has added it to the "Cisco" namespace in their deployment.
Which Kubernetes command confirms that the service is running and usable?A. kubectl -n Cisco get services | grep "Cisco-DB"
B. kubectl -n Cisco get pods | grep "Cisco-DB"
C. kubectl get pods | grep "Cisco-DB"
D. kubectl -n Cisco get service | grep "Cisco-DB"
What is the effective way to manage computing costs in a public cloud?A. Monitor data transfers to minimize cost.
B. Use dedicated hardware for all instances.
C. Select the largest instance option available in order to pay for only one instance.
D. Make use of elastic services and scale on demand.
What are two testing scenarios of the chaos engineering principle? (Choose two.)A. maxing out CPU cores on an Elasticsearch duster
B. removing all users from a version control system
C. executing routine in driver code to emulate I/O errors
D. blocking developers’ building access
E. unplugging a core switch device
ConfigMap keys have been mapped to different file names using the volumes.configMap.items field. What is the result if a wrong ConfigMap key is specified?A. The default path is not used.
B. The volume is not created.
C. The volume is created.
D. The volume is created with errors.
Which Kubernetes object is used to create a ClusterIP or NodePort?A. service
B. pod
C. deployment
D. loadbalancer
FILL BLANK -
Fill in the blanks to complete the statement.
When creating multiple containers, in order to allow communication with each other, you must create a __________ of type _________ .
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)A. Apply
B. Install
C. Deploy
D. Create
E. Expose
Refer to the exhibit. What is the reason for this error message?A. The required dependencies for the urllib3 module are not installed.
B. The requests module is not installed.
C. The required dependencies for the requests module are not installed.
D. The site-packages directory has been corrupted.
A DevOps engineer is supporting a containerized application with multiple components running across the Kubernetes cluster. Metrics from the container (CPU and memory) and application (requests per second and heap size) are being collected by Prometheus and displayed with Grafana. Users report transaction timeout problems with the application, but the metric graphs all look within normal levels.
Which type of failure would prevent the engineer from seeing the problem using the captured metrics?A. Grafana has lost connectivity to Prometheus, which causes graphs to display only the cached data.
B. CPU and memory metrics from Kubernetes nodes are not accurate due to the way that containers share resources.
C. Some containers are crashing regularly and being restarted automatically by Kubernetes.
D. The metricbeat agent has crashed and is no longer sending new data to Prometheus, so the metrics are not updating.
When static routes are added to a router in a network using a CI/CD pipeline, an Ansible playbook is used to make these changes. Which steps must be added to the pipeline to validate that the changes have the intended effect on the traffic flow?A. Add a step to run the debug ip routing command before the change, and add a step after the change to issue the no debug ip routing command.
B. Add a step to capture the routing table before the change, and add a step after the change to capture it again. Calculate the difference between the two for review.
C. Add a step to ping a host on each of the static routes before the change, and a step after to repeat the same check. Calculate the difference between the two checks for review.
D. Add a step to run the same playbook again with the debug option enabled and use grep on the log output to ensure that the commands are not applied again.
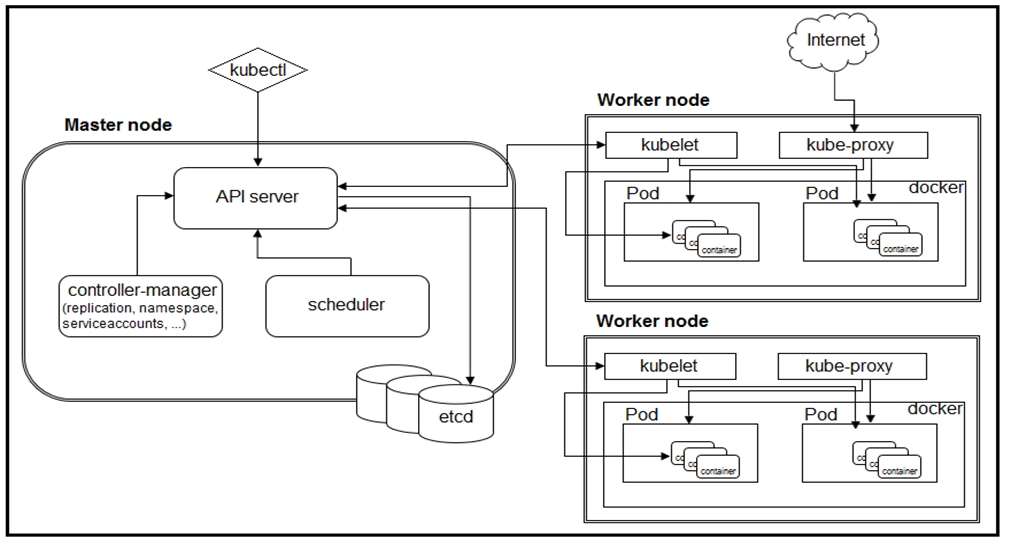
Refer to the exhibit. A developer needs to scale the existing pods within the worked nodes. Which object should be edited to achieve this goal?A. ReplicaSet
B. PriorityClass
C. Deployment
D. Pod
FILL BLANK -
Fill in the blanks to describe the concepts of extending DevOps practices to the network for NetDevOps.
NetDevOps builds and manages networks as a system that enables network services to be consumed in a DevOps approach. Organizations practicing
NetDevOps see changes in the _________ as routine and expected activities, with a well-defined and practiced process for _________ , testing, and __________ network changes. By making them routine, network changes can be small and simple.
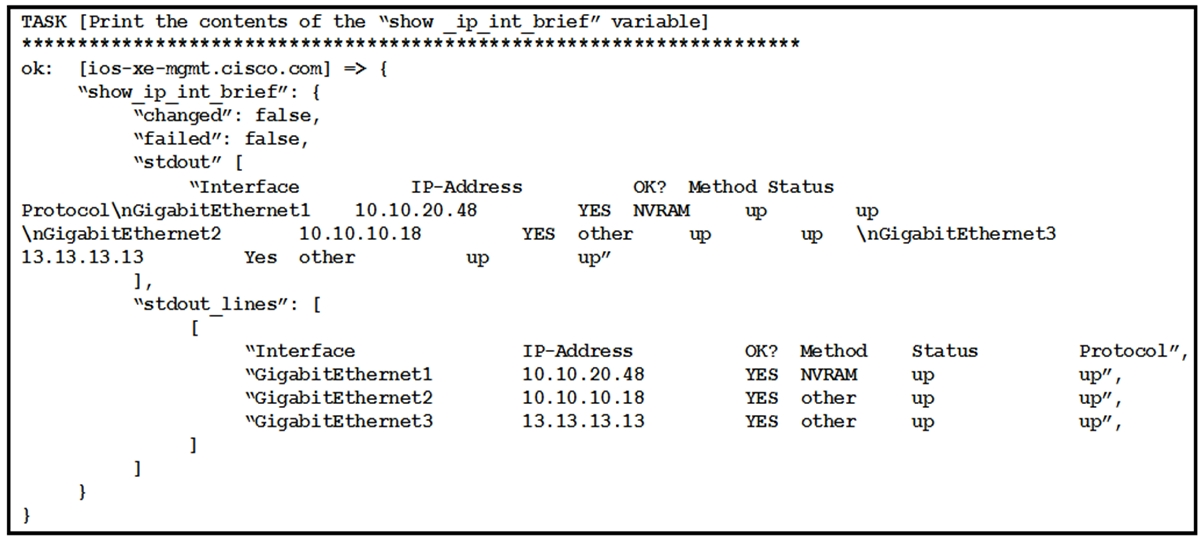
Refer to the exhibit. The exhibit shows the output of an Ansible task that prints the contents of the show_ip_int_brief variable that was registered in a different task in the playbook.
Which expression is used to print the output of the command without its header row?A. show_ip_int_brief["˜stdout_lines'][0]
B. show_ip_int_brief["˜stdout_lines'][1:]
C. show_ip_int_brief["˜stdout_lines'][0][1:]
D. show_ip_int_brief["˜stdout_lines']
Which two statements about Infrastructure as Code are true? (Choose two.)A. Test-driven development practices make use of Infrastructure as Code.
B. Infrastructure as Code refers to automated testing libraries.
C. DevOps builds upon Infrastructure as Code.
D. Infrastructure as Code is based on practices from software development.
E. Infrastructure as Code must use the same programming language as the application.
When DevOps practices are integrated into an existing organization, which two characteristics are positive indicators of DevOps maturity? (Choose two.)A. mean time between success
B. mean time to recover
C. cone testing
D. change lead time
E. age of codebase
AppDynamics is being used to monitor your distributed Python application. Each individual container of the application is instrumented with an AppD agent. Which two configuration variables uniquely determine the module being monitored? (Choose two.)A. node
B. app
C. agent
D. tier
E. event
What is a practice of infrastructure as code?A. Use multiple version control systems
B. Document as much as possible
C. Configure the deployment consistently
D. Test, integrate, and deploy once a day
To make logging searches more efficient and useful in Kibana, an Administrator wants to implement index patterns around the hostname of some software systems. Where should this be configured?A. Configure a new JSON object in Kibana.
B. Create a search index in Logstash.
C. Create an index pattern in Kibana.
D. Create a time filter on Kibana to look at time only.
A security team is running vulnerability scans against a CI/CD pipeline. The reports show that RDBMS secrets were found hardcoded in Ansible scripts. The RDBMS resides in the internal network but is accessible from a jump server that resides in a public network.
If an attacker gains access to the scripts, what is the risk exposure?A. The Automation server is at risk of being compromised.
B. The Ansible scripts run through encrypted SSH connections.
C. The internal network is at risk of being compromised.
D. The entire CI/CD-related infrastructure is at risk.
Which step must be taken to enable centralized logging in a Kubernetes environment?A. No steps need to be taken. The master node automatically aggregates logs from all worker nodes and stores them on the specified persistent volume.
B. Create a CustomResourceDefinition in each deployment that specifies the IP or names the log collector.
C. Deploy a sidecar node that aggregates logs from the entire cluster.
D. Create a DaemonSet that deploys a container with a logging agent on every node in the cluster.
Get More 300-910 Practice Questions
If you're looking for more 300-910 practice test free questions, click here to access the full 300-910 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 300-910 certification journey!