312-38 Practice Test Free – 50 Questions to Test Your Knowledge
Are you preparing for the 312-38 certification exam? If so, taking a 312-38 practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 50 free 312-38 practice questions designed to help you test your skills and identify areas for improvement.
By taking a free 312-38 practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
50 Free 312-38 Practice Questions
Below, you will find 50 free 312-38 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
FILL BLANK -
Fill in the blank with the appropriate term. ________________________ is the complete network configuration and information toolkit that uses multi-threaded and multi-connection technologies in order to be very fast and efficient.
Which of the following analyzes network traffic to trace specific transactions and can intercept and log traffic passing over a digital network? Each correct answer represents a complete solution. Choose all that apply.A. Wireless sniffer
B. Spectrum analyzer
C. Protocol analyzer
D. Performance Monitor
John works as a C programmer. He develops the following C program:
His program is vulnerable to a __________ attack.A. SQL injection
B. Denial-of-Service
C. Buffer overflow
D. Cross site scripting
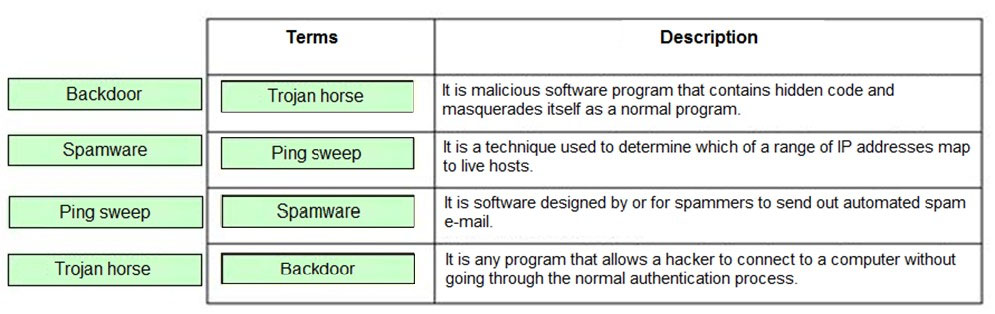
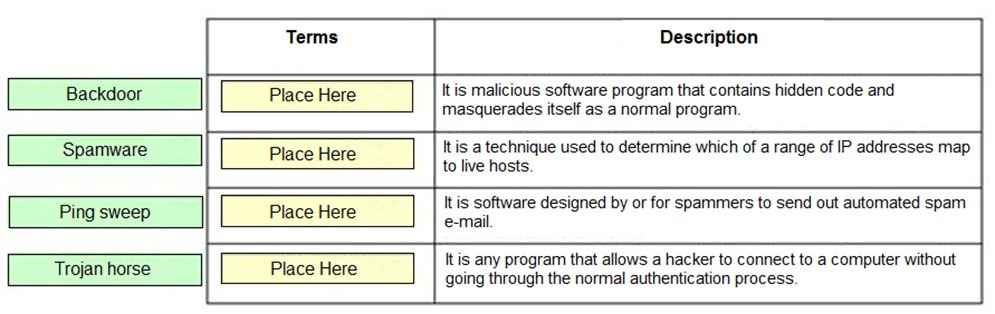
DRAG DROP -
Drag and drop the terms to match with their descriptions.
Select and Place:
Which of the following refers to the exploitation of a valid computer session to gain unauthorized access to information or services in a computer system?A. Spoofing
B. Smurf
C. Session hijacking
D. Phishing
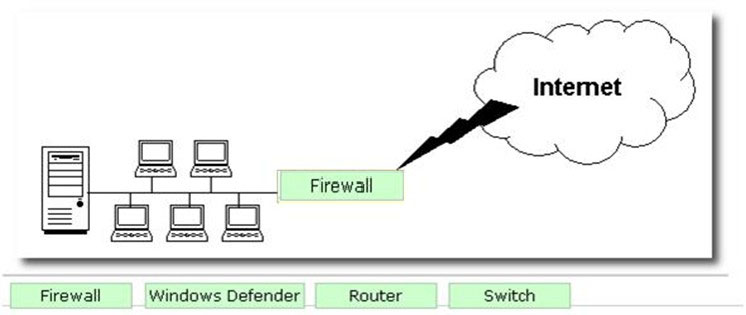
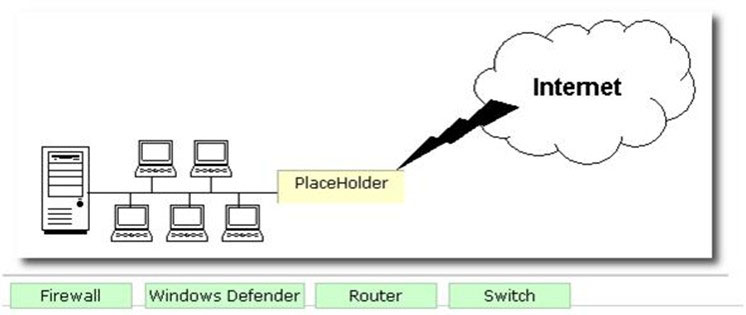
DRAG DROP -
George works as a Network Administrator for Blue Soft Inc. The company uses Windows Vista operating system. The network of the company is continuously connected to the Internet. What will George use to protect the network of the company from intrusion?
Select and Place:
Which of the following representatives of the incident response team takes forensic backups of systems that are the focus of an incident?A. Technical representative
B. Lead investigator
C. Information security representative
D. Legal representative
Which of the following honeypots provides an attacker access to the real operating system without any restriction and collects a vast amount of information about the attacker?A. High-interaction honeypot
B. Medium-interaction honeypot
C. Honeyd
D. Low-interaction honeypot
Which of the following is a tool that runs on the Windows OS and analyzes iptables log messages to detect port scans and other suspicious traffic?A. Nmap
B. Hping
C. NetRanger
D. PSAD
How many layers are present in the TCP/IP model?A. 10
B. 5
C. 4
D. 7
Which of the following is a 16-bit field that identifies the source port number of the application program in the host that is sending the segment?A. Sequence Number
B. Header Length
C. Acknowledgment Number
D. Source Port Address
What is the range for registered ports?A. 1024 through 49151
B. 0 through 1023
C. Above 65535
D. 49152 through 65535
Which of the following cables is made of glass or plastic and transmits signals in the form of light?A. Coaxial cable
B. Twisted pair cable
C. Plenum cable
D. Fiber optic cable
Which of the following statements are true about an IPv6 network? Each correct answer represents a complete solution. Choose all that apply.A. For interoperability, IPv4 addresses use the last 32 bits of IPv6 addresses.
B. It increases the number of available IP addresses.
C. It uses longer subnet masks than those used in IPv4.
D. It provides improved authentication and security.
E. It uses 128-bit addresses.
In which of the following conditions does the system enter ROM monitor mode? Each correct answer represents a complete solution. Choose all that apply.A. The router does not have a configuration file.
B. There is a need to set operating parameters.
C. The user interrupts the boot sequence.
D. The router does not find a valid operating system image.
Which of the following is a tool that runs on the Windows OS and analyzes iptables log messages to detect port scans and other suspicious traffic?A. PSAD
B. Hping
C. NetRanger
D. Nmap
FILL BLANK -
Fill in the blank with the appropriate term. A _______________device is used for uniquely recognizing humans based upon one or more intrinsic physical or behavioral traits.
Which of the following IP class addresses are not allotted to hosts? Each correct answer represents a complete solution. Choose all that apply.A. Class C
B. Class D
C. Class A
D. Class B
E. Class E
Which of the following statements are true about a wireless network?
Each correct answer represents a complete solution. Choose all that apply.A. Data can be shared easily between wireless devices.
B. It provides mobility to users to access a network.
C. Data can be transmitted in different ways by using Cellular Networks, Mobitex, DataTAC, etc.
D. It is easy to connect.
Which of the following steps of the OPSEC process examines each aspect of the planned operation to identify OPSEC indicators that could reveal critical information and then compare those indicators with the adversary's intelligence collection capabilities identified in the previous action?A. Analysis of Threats
B. Application of Appropriate OPSEC Measures
C. Identification of Critical Information
D. Analysis of Vulnerabilities
E. Assessment of Risk
Which of the following steps will NOT make a server fault tolerant? Each correct answer represents a complete solution. (Choose two.)A. Adding a second power supply unit
B. Performing regular backup of the server
C. Adding one more same sized disk as mirror on the server
D. Implementing cluster servers' facility
E. Encrypting confidential data stored on the server
You have just set up a wireless network for customers at a coffee shop. Which of the following are good security measures to implement? Each correct answer represents a complete solution. (Choose two.)A. Using WPA encryption
B. Not broadcasting SSID
C. Using WEP encryption
D. MAC filtering the router
Which of the following fields in the IPv6 header is decremented by 1 for each router that forwards the packet?A. Flow label
B. Next header
C. Traffic class
D. Hop limit
Which of the following layers of TCP/IP model is used to move packets between the Internet Layer interfaces of two different hosts on the same link?A. Application layer
B. Internet layer
C. Link layer
D. Transport Layer
E. None
How many layers are present in the OSI layer model?A. 5
B. 4
C. 7
D. 9
Which of the following encryption techniques do digital signatures use?A. MD5
B. RSA
C. Blowfish
D. IDEA
Which of the following protocols is used for inter-domain multicast routing?A. BGP
B. RPC
C. VoIP
D. RADIUS
Which of the following tools is used to ping a given range of IP addresses and resolve the host name of the remote system?A. SuperScan
B. Netscan
C. Hping
D. Nmap
Which of the following IEEE standards defines a physical bus topology?A. 802.4
B. 802.5
C. 802.6
D. 802.3
Which of the following is a mandatory password-based and key-exchange authentication protocol?A. PPP
B. CHAP
C. VRRP
D. DH-CHAP
CSMA/CD is specified in which of the following IEEE standards?A. 802.3
B. 802.2
C. 802.1
D. 802.15
Which of the following commands is used for port scanning?A. nc -t
B. nc -z
C. nc -v
D. nc -d
In which of the following transmission modes is communication uni-directional?A. Root mode
B. Full-duplex mode
C. Half-duplex mode
D. Simplex mode
Which of the following is a term to describe the use of inert gases and chemical agents to extinguish a fire?A. Gaseous fire suppression
B. Fire alarm system
C. Fire sprinkler
D. Fire suppression system
Which of the following is also known as slag code?A. Trojan
B. Logic bomb
C. Worm
D. IRC bot
Which of the following UTP cables supports transmission up to 20MHz?A. Category 2
B. Category 5e
C. Category 4
D. Category 1
Which of the following IEEE standards provides specifications for wireless ATM systems?A. 802.1
B. 802.5
C. 802.3
D. 802.11a
Which of the following is a session layer protocol?A. RPC
B. SLP
C. RDP
D. ICMP
Which of the following is a presentation layer protocol?A. TCP
B. RPC
C. BGP
D. LWAPP
Which of the following layers provides communication session management between host computers?A. Application layer
B. Internet layer
C. Transport layer
D. Link layer
What is the range for private ports?A. 49152 through 65535
B. 1024 through 49151
C. Above 65535
D. 0 through 1023
Which of the following TCP/IP state transitions represents no connection state at all?A. Closed
B. Closing
C. Close-wait
D. Fin-wait-1
Token Ring is standardized by which of the following IEEE standards?A. 802.2
B. 802.4
C. 802.3
D. 802.1
Which of the following layers of the OSI model provides physical addressing?A. Application layer
B. Network layer
C. Physical layer
D. Data link layer
Which of the following steps OPSEC process examines every aspect of the proposed operation to identify the OPSEC indicators that can reveal important information and then compare them with indicators of the opponent's intelligence collection capabilities identified in the previous activity?A. Identification of Critical Information
B. analysis weakness
C. risk assessment
D. Appropriate OPSEC measures
E. analysis of threats
Which of the following protocols is used for E-mail?A. TELNET
B. MIME
C. SSH
D. SMTP
Which of the following IP addresses is not reserved for the hosts? Each correct answer represents a complete solution. Choose all that apply.A. E-Class
B. class D
C. class A
D. B-
You are Network Administrator Investment Bank. You're worried about people breeching network and can steal information before you can detect and shut down access. Which of the following is the best way to deal with this issue?A. To implement a strong firewall.
B. Implement a honey pot.
C. To implement a strong password policy.
D. None
E. To implement the network is based on antivirus.
Which of the following conditions cannot enter the system ROM monitor mode? Each correct answer represents a complete solution. Choose all that apply.A. The router does not find a valid operating system image.
B. The router does not have the configuration file.
C. The user interrupts the boot sequence.
D. It is necessary to set the operating parameters.
Which of the following firewalls are used to monitor the status of active connections, and configure the network packets to pass through the firewall? Each correct answer represents a complete solution. Choose all that apply.A. Farm owner
B. Proxy server
C. Dynamic packet filtering
D. The circuit gateway
Get More 312-38 Practice Questions
If you're looking for more 312-38 practice test free questions, click here to access the full 312-38 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 312-38 certification journey!