312-50V9 Practice Test Free – 50 Questions to Test Your Knowledge
Are you preparing for the 312-50V9 certification exam? If so, taking a 312-50V9 practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 50 free 312-50V9 practice questions designed to help you test your skills and identify areas for improvement.
By taking a free 312-50V9 practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
50 Free 312-50V9 Practice Questions
Below, you will find 50 free 312-50V9 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
After trying multiple exploits, you've gained root access to a Centos 6 server. To ensure you maintain access, what would you do first?A. Create User Account
B. Disable Key Services
C. Disable IPTables
D. Download and Install Netcat
Jimmy is standing outside a secure entrance to a facility. He is pretending to have a tense conversation on his cell phone as an authorized employee badges in.
Jimmy, while still on the phone, grabs the door as it begins to close.
What just happened?A. Piggybacking
B. Masqurading
C. Phishing
D. Whaling
Under the "Post-attack Phase and Activities", it is the responsibility of the tester to restore the systems to a pre-test state.
Which of the following activities should not be included in this phase? (see exhibit)
Exhibit:

A. III
B. IV
C. III and IV
D. All should be included.
Which of the following statements is TRUE?A. Sniffers operate on Layer 2 of the OSI model
B. Sniffers operate on Layer 3 of the OSI model
C. Sniffers operate on both Layer 2 & Layer 3 of the OSI model.
D. Sniffers operate on the Layer 1 of the OSI model.
You have successfully gained access to your client's internal network and successfully comprised a Linux server which is part of the internal IP network. You want to know which Microsoft Windows workstations have file sharing enabled.
Which port would you see listening on these Windows machines in the network?A. 445
B. 3389
C. 161
D. 1433
What does a firewall check to prevent particular ports and applications from getting packets into an organization?A. Transport layer port numbers and application layer headers
B. Presentation layer headers and the session layer port numbers
C. Network layer headers and the session layer port numbers
D. Application layer port numbers and the transport layer headers
It is a short-range wireless communication technology intended to replace the cables connecting portable of fixed devices while maintaining high levels of security.
It allows mobile phones, computers and other devices to connect and communicate using a short-range wireless connection.
Which of the following terms best matches the definition?A. Bluetooth
B. Radio-Frequency Identification
C. WLAN
D. InfraRed
You are the Systems Administrator for a large corporate organization. You need to monitor all network traffic on your local network for suspicious activities and receive notifications when an attack is occurring. Which tool would allow you to accomplish this goal?A. Network-based IDS
B. Firewall
C. Proxy
D. Host-based IDS
A company's security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?A. Attempts by attackers to access Web sites that trust the Web browser user by stealing the user's authentication credentials.
B. Attempts by attackers to access the user and password information stored in the company's SQL database.
C. Attempts by attackers to access passwords stored on the user's computer without the user's knowledge.
D. Attempts by attackers to determine the user's Web browser usage patterns, including when sites were visited and for how long.
Which of the following tools can be used for passive OS fingerprinting?A. tcpdump
B. nmap
C. ping
D. tracert
Which of the following is considered the best way to protect Personally Identifiable Information (PII) from Web application vulnerabilities?A. Use cryptographic storage to store all PII
B. Use encrypted communications protocols to transmit PII
C. Use full disk encryption on all hard drives to protect PII
D. Use a security token to log into all Web applications that use PII
The security concept of "separation of duties" is most similar to the operation of which type of security device?A. Firewall
B. Bastion host
C. Intrusion Detection System
D. Honeypot
A network administrator discovers several unknown files in the root directory of his Linux FTP server. One of the files is a tarball, two are shell script files, and the third is a binary file is named "nc." The FTP server's access logs show that the anonymous user account logged in to the server, uploaded the files, and extracted the contents of the tarball and ran the script using a function provided by the FTP server's software. The ps command shows that the nc file is running as process, and the netstat command shows the nc process is listening on a network port.
What kind of vulnerability must be present to make this remote attack possible?A. File system permissions
B. Privilege escalation
C. Directory traversal
D. Brute force login A
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible breach of security. When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up.
What is the most likely cause?A. The network devices are not all synchronized.
B. Proper chain of custody was not observed while collecting the logs.
C. The attacker altered or erased events from the logs.
D. The security breach was a false positive.
Which of the following parameters describe LM Hash (see exhibit):
Exhibit:

A. I, II, and III
B. I
C. II
D. I and II
Which of the following is the successor of SSL?A. TLS
B. RSA
C. GRE
D. IPSec
Using Windows CMD, how would an attacker list all the shares to which the current user context has access?A. NET USE
B. NET CONFIG
C. NET FILE
D. NET VIEW
You've gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your tool kit you have an Ubuntu 9.10 Linux LiveCD. Which Linux based tool has the ability to change any user's password or to activate disabled Windows accounts?A. CHNTPW
B. Cain & Abel
C. SET
D. John the Ripper
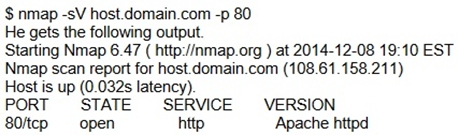
An attacker tries to do banner grabbing on a remote web server and executes the following command.
Service detection performed. Please report any incorrect results at http://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 6.42 seconds
What did the hacker accomplish?A. nmap can't retrieve the version number of any running remote service.
B. The hacker successfully completed the banner grabbing.
C. The hacker should've used nmap -O host.domain.com.
D. The hacker failed to do banner grabbing as he didn't get the version of the Apache web server.
Jack was attempting to fingerprint all machines in the network using the following Nmap syntax: invictus@victim_server:~$ nmap -T4 -0 10.10.0.0/24
TCP/IP fingerprinting (for OS scan) xxxxxxx xxxxxx xxxxxxxxx. QUITTING!
Obviously, it is not going through. What is the issue here?A. OS Scan requires root privileges
B. The nmap syntax is wrong.
C. The outgoing TCP/IP fingerprinting is blocked by the host firewall
D. This is a common behavior for a corrupted nmap application
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet-filtering of the firewall.A. Firewalking
B. Session hijacking
C. Network sniffing
D. Man-in-the-middle attack
While performing online banking using a Web browser, Kyle receives an email that contains an image of a well-crafted art. Upon clicking the image, a new tab on the web browser opens and shows an animated GIF of bills and coins being swallowed by a crocodile. After several days, Kyle noticed that all his funds on the bank was gone. What Web browser-based security vulnerability got exploited by the hacker?A. Clickjacking
B. Web Form Input Validation
C. Cross-Site Request Forgery
D. Cross-Site Scripting
A hacker has managed to gain access to a Linux host and stolen the password file from /etc/passwd. How can he use it?A. The password file does not contain the passwords themselves.
B. He can open it and read the user ids and corresponding passwords.
C. The file reveals the passwords to the root user only.
D. He cannot read it because it is encrypted.
Which of the following is the BEST way to protect Personally Identifiable Information (PII) from being exploited due to vulnerabilities of varying web applications?A. Use cryptographic storage to store all PII
B. Use full disk encryption on all hard drives to protect PII
C. Use encrypted communications protocols to transmit PII
D. Use a security token to log into all Web applications that use PII
Which of the following statements regarding ethical hacking is incorrect?A. Ethical hackers should never use tools or methods that have the potential of exploiting vulnerabilities in an organization's systems.
B. Testing should be remotely performed offsite.
C. An organization should use ethical hackers who do not sell vendor hardware/software or other consulting services.
D. Ethical hacking should not involve writing to or modifying the target systems.
You’ve just gained root access to a Centos 6 server after days of trying. What tool should you use to maintain access?A. Disable Key Services
B. Create User Account
C. Download and Install Netcat
D. Disable IPTables
Which of the following types of firewalls ensures that the packets are part of the established session?A. Stateful inspection firewall
B. Circuit-level firewall
C. Application-level firewall
D. Switch-level firewall
While doing a technical assessment to determine network vulnerabilities, you used the TCP XMAS scan. What would be the response of all open ports?A. The port will send an ACK
B. The port will send a SYN
C. The port will ignore the packets
D. The port will send an RST
The chance of a hard drive failure is known to be once every four years. The cost of a new hard drive is $500. EF (Exposure Factor) is about 0.5. Calculate for the
Annualized Loss Expectancy (ALE).A. $62.5
B. $250
C. $125
D. $65.2
TCP/IP stack fingerprinting is the passive collection of configuration attributes from a remote device during standard layer 4 network communications. Which of the following tools can be used for passive OS fingerprinting?A. nmap
B. ping
C. tracert
D. tcpdump D
Which among the following is a Windows command that a hacker can use to list all the shares to which the current user context has access?A. NET FILE
B. NET USE
C. NET CONFIG
D. NET VIEW
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in-bounds checking mechanism?
Output:
Segmentation fault -A. C#
B. Python
C. Java
D. C++
What is the approximate cost of replacement and recovery operation per year of a hard drive that has a value of $300 given that the technician who charges $10/ hr would need 10 hours to restore OS and Software and needs further 4 hours to restore the database from the last backup to the new hard disk? Calculate the
SLE, ARO, and ALE. Assume the EF = 1 (100%).A. $440
B. $100
C. $1320
D. $146
If there is an Intrusion Detection System (IDS) in intranet, which port scanning technique cannot be used?A. Spoof Scan
B. TCP Connect scan
C. TCP SYN
D. Idle Scan
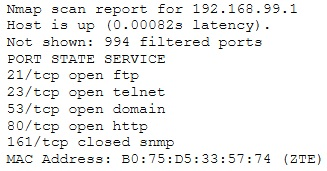
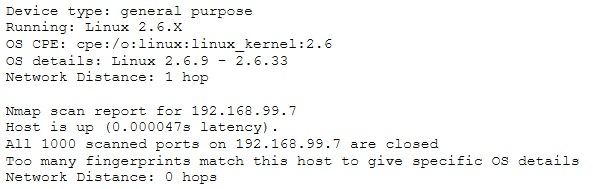
Emil uses nmap to scan two hosts using this command.
nmap -sS -T4 -O 192.168.99.1 192.168.99.7
He receives this output:
What is his conclusion?A. Host 192.168.99.7 is an iPad.
B. He performed a SYN scan and OS scan on hosts 192.168.99.1 and 192.168.99.7.
C. Host 192.168.99.1 is the host that he launched the scan from.
D. Host 192.168.99.7 is down. B
Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries.) More generally, it is about constructing and analyzing protocols that overcome the influence of adversaries and that are related to various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation. Modern cryptography intersects the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.
Basic example to understand how cryptography works is given below:
Which of the following choices is true about cryptography?A. Algorithm is not the secret, key is the secret.
B. Symmetric-key algorithms are a class of algorithms for cryptography that use the different cryptographic keys for both encryption of plaintext and decryption of ciphertext.
C. Secure Sockets Layer (SSL) use the asymmetric encryption both (public/private key pair) to deliver the shared session key and to achieve a communication way.
D. Public-key cryptography, also known as asymmetric cryptography, public key is for decrypt, private key is for encrypt.
When purchasing a biometric system, one of the considerations that should be reviewed is the processing speed. Which of the following best describes what it is meant by processing?A. The amount of time it takes to convert biometric data into a template on a smart card.
B. The amount of time and resources that are necessary to maintain a biometric system.
C. The amount of time it takes to be either accepted or rejected form when an individual provides Identification and authentication information.
D. How long it takes to setup individual user accounts. C
Sid is a judge for a programming contest. Before the code reaches him it goes through a restricted OS and is tested there. If it passes, then it moves onto Sid.
What is this middle step called?A. Fuzzy-testing the code
B. Third party running the code
C. Sandboxing the code
D. String validating the code
You are attempting to crack LM Manager hashed from Windows 2000 SAM file. You will be using LM Brute force hacking tool for decryption. What encryption algorithm will you be decrypting?A. MD4
B. DES
C. SHA
D. SSL
A hacker was able to easily gain access to a website. He was able to log in via the frontend user login form of the website using default or commonly used credentials. This exploitation is an example of what Software design flaw?A. Insufficient security management
B. Insufficient database hardening
C. Insufficient input validation
D. Insufficient exception handling
What tool can crack Windows SMB passwords simply by listening to network traffic?A. This is not possible
B. Netbus
C. NTFSDOS
D. L0phtcrack
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?A. har.txt
B. SAM file
C. wwwroot
D. Repair file
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?A. USER, NICK
B. LOGIN, NICK
C. USER, PASS
D. LOGIN, USER
Which DNS resource record can indicate how long any "DNS poisoning" could last?A. MX
B. SOA
C. NS
D. TIMEOUT
You have the SOA presented below in your Zone.
Your secondary servers have not been able to contact your primary server to synchronize information. How long will the secondary servers attempt to contact the primary server before it considers that zone is dead and stops responding to queries? collegae.edu.SOA, cikkye.edu ipad.college.edu. (200302028 3600 3600 604800 3600)A. One day
B. One hour
C. One week
D. One month
MX record priority increases as the number increases. (True/False.)A. True
B. False
Which of the following statements about a zone transfer is correct? (Choose three.)A. A zone transfer is accomplished with the DNS
B. A zone transfer is accomplished with the nslookup service
C. A zone transfer passes all zone information that a DNS server maintains
D. A zone transfer passes all zone information that a nslookup server maintains
E. A zone transfer can be prevented by blocking all inbound TCP port 53 connections
F. Zone transfers cannot occur on the Internet
One of your team members has asked you to analyze the following SOA record. What is the version?
Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.) (Choose four.)A. 200303028
B. 3600
C. 604800
D. 2400
E. 60
F. 4800
One of your team members has asked you to analyze the following SOA record.
What is the TTL? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)A. 200303028
B. 3600
C. 604800
D. 2400
E. 60
F. 4800
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs:
From the above list identify the user account with System Administrator privileges.A. John
B. Rebecca
C. Sheela
D. Shawn
E. Somia
F. Chang
G. Micah F
Get More 312-50V9 Practice Questions
If you're looking for more 312-50V9 practice test free questions, click here to access the full 312-50V9 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 312-50V9 certification journey!