IT Exam Questions and Solutions Library
What are two benefits of adaptive multifactor authentication? (Choose two.) A. no need to remember passwords B. secure remote access C. contextual factor-based authentication D. improved access management E. managed encryption policies Suggested Answer: BC
The security team has installed a Cisco Secure Email Gateway. During setup, a large number of email messages containing the string "abcde1111111111" are being blocked. The security team wants to investigate and determine if the emails are part of a phishing or malware attack. Which configuration step must the security team apply? A. Implement a policy to only allow email from trusted to the network senders. B. Apply a policy to route all blocked emails to a separate quarantine folder. C. Configure sender domain reputation policy to check if sender email domain is known to be malicious. D. Configure a policy to disable spam filtering in order to expedite email delivery. Suggested Answer: B
Which two facts must be considered when deciding whether to deploy the Cisco Secure Web Appliance in Standard mode, Hybrid Web Security mode, or Cloud Web Security Connector mode? (Choose two.) A. External DLP is available only in Standard mode and Hybrid Web Security mode. B. The onsite web proxy is not supported in Cloud Web Security Connector mode. C. Standard mode and Hybrid Web Security mode perform the same actions in response to the application of an individual policy. D. Only Standard mode and Hybrid Web Security mode support Layer 4 traffic monitoring. E. ISE integration is available only in Standard mode and Hybrid Web Security mode. Suggested Answer: BD
What is a difference between an EPP solution and an EDR solution? A. EPP detects malicious activity on endpoints, and EDR only detects file-based malware on endpoints. B. EDR provides endpoint data loss prevention, and EPP remediates hosts to a preinfection state. C. EDR focuses on detecting network-level threats, and EPP focuses on detecting host-level threats. D. EPP contains a security incident at the network traffic level, and EDR contains a security incident at the endpoint. Suggested Answer: D
A company is planning to deploy an application to a secure cloud environment. The solution must meet these requirements: • A third-party must control the underlying cloud infrastructure. • The company must control the deployed applications. • A third-party must control networking components. Which cloud service model must be used? A. SaaS B. IaaS C. PaaS D. private cloud Suggested Answer: C
An organization plans to upgrade its current email security solutions, and an engineer must deploy Cisco Secure Email. The requirements for the upgrade are: • Implement Data Loss Prevention • Implement mail encryption • Integrate with an existing Cisco IronPort Secure Email Gateway solution Which Cisco Secure Email license needed to accomplish this task? A. Cisco Secure Email Domain Protection B. Cisco Secure Email Inbound Essentials C. Cisco Secure Email Outbound Essentials D. Cisco Secure Email Phishing Defense Suggested Answer: C
Which Cisco ISE service checks the state of all the endpoints connecting to a network for compliance with corporate security policies? A. Threat Centric NAC service B. posture service C. Cisco TrustSec D. compliance module Suggested Answer: B
What is a difference between an SQL injection and a cross-site scripting attack? A. SQL injection intercepts user information, and XSS causes false or unpredictable results. B. SQL injection modifies SQL queries, and XSS cloaks by encoding tags. C. SQL injection detects environments, and XSS cloaks by encoding tags. D. SQL injection modifies SQL queries, and XSS allows access to files beyond the root folder. Suggested Answer: B
DRAG DROP - Drag and drop the firewall capabilities from the left onto the corresponding firewall deployment modes on the right.Suggested Answer:

A network engineer must create an access control list on a Cisco Adaptive Security Appliance firewall to permit TCP DNS traffic to the internet from the organization’s inside network 192.168.1.0/24. Which IOS command must be used to implement the access control list?
A.
 B.
B.
 C.
C.
 D.
D.
 Suggested Answer: D
Suggested Answer: D
What is a capability of Cisco Secure Email Cloud Gateway compared to Cisco Secure Email Gateway? A. Secure Email Cloud Gateway is an add-on that is deployed to a web browser by using a group policy, and Secure Email Gateway requires a server infrastructure. B. Secure Email Cloud Gateway requires that a proxy be deployed to a web browser, and Secure Email Gateway requires a network reconfiguration. C. Secure Email Cloud Gateway protects email without having to deploy an infrastructure, and Secure Email Gateway requires a server infrastructure. D. Secure Email Cloud Gateway requires an ASA to redirect email by using WCCP, and Secure Email Gateway requires that the ASA be inline. Suggested Answer: C
An engineer must prevent communication with a cloud application being decrypted. The application database uses AES-256 with SHA-512 and web access to the application uses HTTPS with SSLv2 self-signed certificates. What must the engineer implement next? A. SSLV3 with self-signed certificates B. TLS 1.3 with signed certificates C. SSLv3 with signed certificates D. TLS 1.3 with self-signed certificates Suggested Answer: B
Which action blocks specific IP addresses whenever a computer with Cisco Secure Endpoint installed connects to the network? A. Create an application block list and add the IP addresses. B. Create an IP Block & Allow list and add the IP addresses. C. Create an advanced custom detection policy and add the IP addresses. D. Create a simple custom detection policy and add the IP addresses. Suggested Answer: B
An organization has had some malware infections recently and the management team wants to use Cisco Secure Firewall to enforce file policies to prevent malicious files from being downloaded. The SHA-256 hash value of all files traversing the firewall must be calculated and compared to the hash values of known malware code. Which file rule action is used to block only the files that are confirmed to be malware? A. Block Malware B. Detect Files C. Malware Cloud Lookup D. Block Files Suggested Answer: A
Which Cisco solution integrates industry-leading artificial intelligence and machine learning analytics and an assurance database to review the security posture and maintain visibility of an organizations cloud environment? A. Cisco Secure Workload B. Cisco CSR1000v C. Cisco DNA D. Cisco FTD Suggested Answer: A
An engineer is configuring cloud logging on Cisco ASA and needs events to compress. Which component must be configured to accomplish this goal? A. Cisco analytics B. CDO event viewer C. SWC service D. SDC VM Suggested Answer: D
When an assessment of cloud services and applications is conducted, which tool is used to show user activity and data usage across the applications? A. Cisco ASA B. Cisco CloudLock C. Cisco ISE D. Cisco AMP Private Cloud Suggested Answer: B
An engineer implements Cisco CloudLock to secure a Microsoft Office 365 application in the cloud. The engineer must configure protection for corporate files in case of any incidents. Which two actions must be taken to complete the implementation? (Choose two.) A. Remove all users as collaborators on the files. B. Transfer ownership of the files to a specified owner and folder. C. Expire the public share URL. D. Disable the ability for commenters and viewers to download and copy the files. E. Send Cisco Webex message to specified users when an incident is triggered. Suggested Answer: AC
Which common exploit method is TLS 1.3 designed to prevent? A. man-in-the-middle attack B. denial-of-service attack C. cross-site request forgery D. cross-site scripting Suggested Answer: A
Refer to the exhibit. A company named ABC has a Cisco Secure Email Gateway and an engineer must configure the incoming mail policy so that emails containing malware files are quarantined instead of dropped and to prevent an increase in false positives causing emails to be dropped erroneously. What must be configured on the Secure Email Gateway? A. Change the Policies Order. B. Open Default Policy, Malware File, and then Action Applied to Message. C. Delete usera1 policy. D. Open usera1 policy, Messages with Malware Attachments, and then Action Applied to Message. Suggested Answer: D
How does a Cisco Secure Web Appliance integrated with LDAP handle the permissions of a currently logged in Active Directory group member when the Active Directory administrator changes the permissions of the user's group mid session? A. If the Cisco Secure Client Mobility Client is configured on the endpoint to provide Active Directory updates, the Cisco Secure Web Appliance changes the user's permissions immediately when alerted by the client. B. If the Cisco Secure Web Appliance is configured to receive real-time updates from the Active Directory user agent, it changes the user's permissions immediately when the agent sends the update. C. The Cisco Secure Web Appliance terminates the current session and prompts the user to re-authenticate in order to update the effective permissions. D. The Cisco Secure Web Appliance continues to operate using the permissions that were in effect when the user logged in for the duration of the user's session. Suggested Answer: D
Refer to the exhibit. An engineer must forward all web traffic sent from Client-SiteA to the monitoring server to build a baseline of expected traffic once a new Cisco Secure Web Appliance is deployed. What must be configured on the switch to meet the requirement? A. ERSPAN B. RSPAN C. WCCP D. SPAN Suggested Answer: D
What is the difference between EPP and EDR? A. Having an EDR solution gives an engineer the capability to flag offending files at the first sign of malicious behavior. B. EPP focuses primarily on threats that have evaded front-line defenses that entered the environment. C. Having an EPP solution allows an engineer to detect, investigate, and remediate modern threats. D. EDR focuses solely on prevention at the perimeter. Suggested Answer: A
What is capability of EPP compared to EDR? A. EPP protects against malware that has already entered the environment, and EDR focuses on protecting against botnets. B. EDR protects against email attacks, and EPP focuses on detecting and monitoring phishing and ransomware email attacks. C. EDR protects against malicious email attacks, and EPP focuses on suspicious website attacks including DoS and DDoS attempts. D. EDR protects against malware that has already entered the environment, and EPP focuses on preventing malware from entering. Suggested Answer: D
What is considered a cloud data breach? A. cyber threats posing as authorized entities B. exploitation of cloud application access C. deprivation of computing resources D. leaked information that is private Suggested Answer: B
Which type of attack does multifactor authentication help protect against? A. cross-site scripting B. brute force C. SQL injection D. man-in-the-middle Suggested Answer: B
An engineer must use Cisco Secure Firewall Management Center to send Cisco Secure Firewall Threat Defense events to the cloud. The engineer performed these actions already: • FTD devices were added to FMC • FTD devices were assigned licenses Which action must be taken to complete Cisco Cloud Event Configuration? A. Register with Cisco Smart Licensing. B. Enable cloud event connector. C. Create a Cisco Cloud Region. D. Assign a Cloud Event License. Suggested Answer: B
What is a benefit of using Cisco AVC for application control? A. dynamic application scanning B. management of application sessions C. retrospective application analysis D. zero-trust approach Suggested Answer: B
What is the purpose of CA in a PKI? A. to generate a pkcs12 certificate from certificate key-pair B. to issue and revoke digital certificates C. to certify the ownership of a public key by the named subject D. to create the private key for a digital certificate Suggested Answer: B
An engineer is onboarding a teleworker to Cisco Umbrella. After the worker’s home network identity is configured, which additional action must be taken to complete the network registration? A. Change the public IP addresses from static to dynamic. B. Point the home modem DHCP to Cisco Umbrella DHCP. C. Set up a point-to-point VPN with the head-office. D. Point the home modem DNS to Cisco Umbrella DNS. Suggested Answer: D
What must be disabled on a Cisco Secure Web Appliance to ensure HTTPS traffic with a good reputation score bypasses decryption? A. Decrypt ACL B. Decrypt Policies C. Decrypt for End-User Acknowledgment D. Decrypt for End-User Notification Suggested Answer: A
A network engineer must use the Cisco DNA Center API to create a configuration template to provision a device. Which two method and endpoint pairs must be used to create the template? (Choose two.)
A.
 B.
B.
 C.
C.
 D.
D.
 E.
E.
 Suggested Answer: BD
Suggested Answer: BD
A network engineer must create an access control list on a Cisco Adaptive Security Appliance firewall. The access control list must permit HTTP traffic to the internet from the organization’s inside network 192.168.1.0/24. Which IOS command must be used to create the access control list?
A.
 B.
B.
 C.
C.
 D.
D.
 Suggested Answer: C
Suggested Answer: C
DRAG DROP - Drag and drop the security responsibilities from the left onto the corresponding cloud service models on the right.Suggested Answer:

An engineer must modify an existing remote access VPN using a Cisco AnyConnect Secure Mobility client solution and a Cisco Secure Firewall. Currently, all the traffic generated by the user is sent to the VPN tunnel and the engineer must now exclude some servers and access them directly instead. Which element must be modified to achieve this goal? A. NAT exemption B. encryption domain C. routing table D. group policy Suggested Answer: D
An engineer must configure a Cisco Secure Email Gateway to use DLP for a company. The company also wants to see the content of emails that violate the DLP policy. Which configuration must be modified in the Data Loss Prevention Settings section to meet the requirements? A. DLP Message Action B. Matched Content Logging C. Secure Reply All D. Secure Message Forwarding Suggested Answer: B
Which email security feature protects users from phishing attempts? A. anti-malware file scanning B. intrusion prevention C. reputation-based filtering D. malicious signature detection Suggested Answer: C
Refer to the exhibit. Which protocol should be used to encrypt a client connection that signs in to the router remotely to make common configuration changes? A. SSH B. FTPS C. SCP D. SFTP Suggested Answer: A
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements? A. Cisco Secure Workload B. Cisco Secure Network Analytics C. Cisco AMP D. Cisco Umbrella Suggested Answer: A
How does a Cisco Secure Firewall help to lower the risk of exfiltration techniques that steal customer data? A. blocking UDP port 53 B. blocking TCP port 53 C. inspecting the DNS traffic D. encrypting the DNS communication Suggested Answer: C
Refer to the exhibit. Which task is the Python script performing by using the Cisco Umbrella API? A. changing the disposition of domains that were previously malicious to clean B. checking the disposition of previously identified domains in bulk C. changing the disposition of domains that were previously clean to malicious D. checking the disposition of potentially malicious domains in bulk Suggested Answer: B
Refer to the exhibit. A network engineer must implement a new multidevice management solution and must retrieve information about all the Cisco devices that are directly attached to a Cisco IOS router. Which IOS command must the engineer use to display detailed information about the attached devices? A.
B.
C.
D.
Suggested Answer: A
Refer to the exhibit. Network access control is implemented on the LAN and an engineer must now configure the switch port level so that users with new corporate devices can connect to the corporate LAN without issues. What must be configured next? A. clear port-security dynamic B. shut and no shut C. errdisable recovery cause psesecure-violation D. authentication violation replace Suggested Answer: D
A network administrator has configured TACACS on a network device using the key Cisc0466974274 for authentication purposes. However, users are unable to authenticate. TACACS server is reachable, but authentication is falling. Which configuration step must the administrator complete? A. Configure the TACACS key on the server to match with the network device. B. Install a compatible operating system version on the TACACS server. C. Implement synchronized system clock on TACACS server that matches the network device. D. Apply an access control list on TACACS server to allow communication with the network device. Suggested Answer: A
How do the features of DMVPN compare to IPsec VPN? A. DMVPN supports high availability routing, and IPsec VPN supports stateless failover. B. DMVPN uses hub-and-spoke topology, and IPsec VPN uses on-demand spoke topology. C. DMVPN supports non-IP protocols, and IPsec VPN only supports IP protocols. D. DMVPN supports multiple vendors, and IPsec VPN only supports Cisco products. Suggested Answer: B
DRAG DROP - Drag and drop the Cisco Secure Email Gateway benefits from the left to the corresponding deployment options on the right.Suggested Answer:

What has driven an increase in the need for endpoint-based security? A. minimal endpoint-based security manual configuration and implementation B. increased data volumes and value in data center storage C. increased number of BYOD policies and hybrid remote worker D. stricter control mechanism requirements for enterprise access Suggested Answer: C
A security test performed on one of the applications shows that user input is not validated. Which security vulnerability is the application more susceptible to because of this lack of validation? A. man-in-the-middle B. cross-site request forgery C. SQL injection D. denial-of-service Suggested Answer: C
Which problem is solved by deploying a multicontext firewall? A. overlapping IP addressing plan B. resilient high availability design C. faster inspection D. more secure policy Suggested Answer: A
What must be configured on Cisco Secure Endpoint to create a custom detection file list to detect and quarantine future files? A. Create an advanced custom detection and upload the hash of each file. B. Add a network IP block allowed list to the configuration and add the blocked files. C. Use the simple custom detection feature and add each detection to the list. D. Configure an application control allowed applications list to block the files. Suggested Answer: C
Which Cisco solution provides a comprehensive view of internet domains, IP addresses, and autonomous systems to help pinpoint attackers and malicious infrastructures? A. Cisco Secure Workload Cloud B. Cisco Advanced Malware Investigate C. Cisco Threat Indication Database D. Cisco Umbrella Investigate Suggested Answer: D
An engineer must register a fixed network on a Cisco Umbrella platform. Which two actions must be performed when adding a new public IP address? (Choose two.) A. Enter a network public IP address. B. Install the Umbrella root certificate. C. Configure the DNS security settings. D. Point DNS to Umbrella platform DNS servers. E. Point DHCP to Umbrella platform DHCP servers. Suggested Answer: AD
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains, IPs, and files, and helps to pinpoint attackers’ infrastructures and predict future threat? A. Cisco Umbrella Investigate B. Cisco Secure Network Analytics C. Cisco pxGrid D. Cisco Secure Cloud Analytics Suggested Answer: A
Which action configures the iEEE 802.1X Flexible Authentication feature to support Layer 3 authentication mechanisms? A. Modify the Dot1x configuration on the VPN server to send Layer 3 authentications to an external authentication database. B. Identify the devices using this feature and create a policy that allows them to pass Layer 2 authentication. C. Add MAB into the switch to allow redirection to a Layer 3 device for authentication. D. Configure WebAuth so the hosts are redirected to a web page for authentication. Suggested Answer: C
Which API technology with SDN architecture is used to communicate with a controller and network devices such as routers and switches? A. rest APIs B. northbound APIs C. southbound APIs D. unprotected APIs Suggested Answer: C
Which solution should a network administrator deploy to protect a webserver from SQL injection attacks? A. IDS B. Secure Web Appliance C. ISE D. IPS Suggested Answer: B
What is a capability of Cisco AVC? A. application bandwidth enforcement on Cisco IOS platforms B. interoperates by using GET VPN on tunnel interfaces C. traffic filtering by using a Security Intelligence policy D. deep packet inspection on IPsec encapsulated traffic Suggested Answer: A
Which parameter must be set for an invalid certificate handling on a Cisco Seucure Web Appliance with a policy for HTTPS traffic? A. Decrypt B. Reject C. Accept D. Scan Suggested Answer: A
A networking team must harden an organization's network from VLAN hopping attacks. The team disables Dynamic Trunking Protocol and puts any unused ports in an unused VLAN. A trunk port is used as a trunk link. What must the team configure next to harden the network against VLAN hopping attacks? A. dedicated VLAN ID for all trunk ports B. disable STP on the network devices C. DHCP snooping on all the switches D. enable port-based network access control Suggested Answer: A
A network engineer configures a site-to-site VPN with a colleague. During testing, the engineer discovers that only phase 1 is up, and application traffic cannot pass. Which configuration parameter must be checked on each device? A. hash algorithm B. peer IP address C. encryption domain D. preshared key Suggested Answer: B
An engineer is deploying a Cisco Email Security Appliance and must configure a sender group that decides which mail policy will process the mail. The configuration must accept incoming mails and relay the outgoing mails from the internal server. Which component must be configured to accept the connection to the listener and meet these requirements on a Cisco Secure Email Gateway? A. access list B. HAT C. RAT D. sender list Suggested Answer: C
Refer to the exhibit. A network engineer wants to reduce the operational costs of SNMPv3 by using trapping instead of polling. Which code snippet completes the configuration to enable authentication for SNMPv3 trapping? A.
B.
C.
D.
Suggested Answer: B
What is the definition of phishing? A. malicious email spoofing attack that targets a specific organization or individual B. impersonation of an authorized website to deceive users into entering their credentials C. any kind of unwanted, unsolicited digital communication that gets sent out in bulk D. sending fraudulent communications that appear to come from a reputable source Suggested Answer: D
Which Cisco firewall solution supports configuration via Cisco Policy Language? A. NGFW B. CBAC C. IPS D. ZFW Suggested Answer: D
A network administrator has configured DHCP snooping on a Cisco switch to prevent unauthorized DHCP servers from assigning IP addresses. During configuration, a device with MAC address 04:66:96:79:0:AB received an IP address from an unauthorized DHCP server. Which configuration step must the network administrator take to accomplish the requirement? A. Apply DHCP option 82 to identify the trusted DHCP server. B. Configure each device on the network to use authorize DHCP server manually. C. Configure an access control list to only allow DHCP traffic from trusted DHCP server. D. Implement DHCP option 82 to relay DHCP requests to the trusted DHCP server. Suggested Answer: D
What are two examples of code injection vulnerabilities? (Choose two.) A. XML external entity injection B. cross-site scripting C. session hijacking D. SQL injection E. arbitrary command injection Suggested Answer: BD
What is the purpose of the certificate signing request when adding a new certificate for a server? A. It provides the certificate client information so the server can authenticate against it when installing. B. It provides the server information so a certificate can be created and signed. C. It is the password for the certificate that is needed to install it with. D. It is the certificate that will be loaded onto the server. Suggested Answer: B
Which Secure Email Gateway implementation method segregates inbound and outbound email? A. pair of logical listeners on a single physical interface with two unique logical IPv4 addresses and one IPv6 address B. pair of logical IPv4 listeners and a pair of IPv6 listeners on two physically separate interfaces C. one listener on one logical IPv4 address on a single logical interface D. one listener on a single physical interface Suggested Answer: B
What is a feature of an endpoint detection and response solution? A. ensuring the security of network devices by choosing which devices are allowed to reach the network B. capturing and clarifying data on email, endpoints, and servers to mitigate threats C. rapidly and consistently observing and examining data to mitigate threats D. preventing attacks by identifying harmful events with machine learning and conduct-based defense Suggested Answer: C
An engineer is deploying a Cisco Secure Email Gateway and must ensure it reaches the Cisco update servers to retrieve new rules. The engineer must now manually configure the Outbreak Filter rules on an AsyncOS for Cisco Secure Email Gateway. Only outdated rules must be replaced. Up-to-date rules must be retained. Which action must the engineer take next to complete the configuration? A. Use the outbreakconfig command in CLI. B. Select Outbreak Filters. C. Perform a backup/restore of the database. D. Click Update Rules Now. Suggested Answer: C
A website administrator wants to prevent SQL injection attacks against the company’s customer database, which is referenced by the web server. Which two methods help prevent SQL injection attacks? (Choose two.) A. using load balancers with NAT B. performing input validation C. enforcing TLS 1.3 only D. using SSL certificates E. using web application firewalls Suggested Answer: BE
An engineer is configuring DHCP on a Cisco switch and wants to ensure that a DHCP packet will be dropped. Under which condition will this occur? A. A packet from a DHCP server is received from inside the network or firewall. B. All packets are dropped until the administrator manually enters the approved servers into the DHCP snooping database. C. A packet is received on an untrusted interface, and the source MAC address and the DHCP client hardware address do not match. D. A DHCP relay agent forwards a DHCP packet that includes a relay-agent IP address that is 0.0.0.0. Suggested Answer: D
An engineer is configuring guest WLAN access using Cisco ISE and the Cisco WLC. Which action temporarily gives guest endpoints access dynamically while maintaining visibility into who or what connecting? A. Configure ISE and the WLC for quest redirection and services using a self-registered portal. B. Modify the WLC configuration to allow any endpoint to access an internet-only VLAN. C. Configure ISE and the WLC for guest redirection and services using a hotspot portal. D. Modify the WLC configuration to require local WLC logins for the authentication prompts. Suggested Answer: C
An engineer needs to configure cloud logging on Cisco ASA with SAL integration. Which parameter must be considered for this configuration? A. Events can be viewed only from one regional cloud. B. All CSM versions are supported. C. Onboard Cisco ASA device to CDO is needed. D. Required storage size can be allocated dynamically. Suggested Answer: C
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection? A. Cisco Secure Client B. Cisco ISE C. Cisco Secure Workload D. Cisco AMP for Network Suggested Answer: C
A network administrator has installed Secure Endpoint in the network. During setup it was noticed an endpoint has been exhibiting unusual behavior, including slow performance and unexpected network activity. Administrator discovers a suspicious file named abc0467145535.exe running in the background. Which step must the network administrator take to investigate and remediate the potential malware? A. Isolate the endpoint from the network. B. Reset the endpoint password and enable multi-factor authentication. C. Format and reinstall the operating system on the endpoint. D. Disable all non-essential processes running on the endpoint. Suggested Answer: A
What are two targets in cross-site scripting attacks? (Choose two.) A. footer B. cookie C. input D. header E. image Suggested Answer: DE
Which component performs the resolution between the tunnel address and mGRE address in DMVPN? A. GDOI B. NBMA C. NHRP D. NHS Suggested Answer: C
Refer to the exhibit. A network engineer must retrieve the interface configuration on a Cisco router by using the NETCONF API. The engineer uses a Python script to automate the activity. Which code snippet completes the script? A.
B.
C.
D.
Suggested Answer: C
What is a difference between encrypted passwords and hardcoded passwords? A. Encrypted passwords are easier to obtain, and hardcoded passwords are known only to developers. B. Encrypted passwords are generated by an application user, and hardcoded passwords are generated randomly. C. Encrypted passwords are used for frontend applications, and hardcoded passwords are used for backend applications. D. Encrypted passwords are stored in a database, and hardcoded passwords are embedded in the source code. Suggested Answer: D
Which action adds IOCs to customize detections for a new attack? A. Use the initiate Endpoint 1OC scan feature to gather the IOC information and push it to clients. B. Upload the 10Cs into the Installed Endpoint IOC feature within Cisco Secure Endpoint. C. Add a custom advanced detection to include the 1OCs needed within Cisco Secure Endpoint. D. Modify the base policy within Cisco Secure Endpoint to include simple custom detections. Suggested Answer: B
A network administrator received a critical message alert from a Cisco Secure Web Appliance stating that the log partition is at 107% capacity. How does a Cisco Secure Web Appliance respond when its logging partition is full? A. It overwrites the oldest log files. B. It suspends logging and reporting functions. C. It deletes logs older than a configurable age. D. It archives older logs in a compressed file to free space. Suggested Answer: B
What limits communication between applications or containers on the same node? A. container orchestration B. microservicing C. software-define access D. microsegmentation Suggested Answer: B
Refer to the exhibit. An administrator is configuring a VPN tunnel on a Cisco router. The information provided by the administrator of the remote end of the VPN tunnel was that IKEv1 is the tunnel protocol with a preshared key of C1$c0463835440!. The encryption for both phases is AES and the hash for both phases is SHA-256. The source subnet is 10.10.10.x/24 and the destination subnet is 10.10.20.x/24. The local device cannot establish a VPN tunnel and the debug message shown here is seen in the log file. What must be verified to correct the configuration? A. Ensure that the IKE version is identical on both ends B. Ensure that the ISAKMP policy configuration is identical on both ends C. Ensure that the preshared key is identical on both ends D. Ensure that the ACLs that define interesting traffic are symmetrical on both ends Suggested Answer: D
Which attack gives unauthorized access to files on the web server? A. DHCP snooping B. path traversal C. broadcast storm D. distributed DoS Suggested Answer: B
Which feature does the IaaS model provide? A. software-defined network segmentation B. granular control of data C. automatic updates and patching of software D. dedicated, restricted workstations Suggested Answer: A
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement? A. nextgeneration firewall B. web application firewall C. next generation intrusion prevention system D. intrusion detection system Suggested Answer: A
What is a benefit of using Cisco CWS compared to an on-premises Cisco Secure Web Appliance? A. CWS eliminates the need to backhaul traffic through headquarters for remote workers whereas Secure Web Appliance does not. B. Content scanning for SAAS cloud applications is available through CWS and not available through Secure Web Appliance. C. CWS minimizes the load on the internal network and security infrastructure as compared to Secure Web Appliance. D. URL categories are updated more frequently on CWS than they are on Secure Web Appliance. Suggested Answer: A
Which key feature of Cisco ZFW is unique among other Cisco IOS firewall solutions? A. SSL inspection B. security levels C. stateless inspection D. security zones Suggested Answer: D
Which Cisco solution secures the cloud users, data and applications with the cloud-native CASB and cloud cybersecurity platform? A. Cisco Appdynamics B. Cisco Umbrella C. Cisco CloudLock D. Cisco Secure Network Analytics Suggested Answer: C
What are the components of endpoint protection against social engineering attacks? A. Cisco Secure Email Gateway B. IPsec C. firewall D. IDS Suggested Answer: A
Which feature is used to restrict communication between interfaces on a Cisco ASA? A. VLAN subinterfaces B. traffic zones C. VxLAN interfaces D. security levels Suggested Answer: D
A network administrator is modifying a remote access VPN on an FTD managed by an FMC. The administrator wants to offload traffic to certain trusted domains. The administrator wants this traffic to go out of the client's local internet and send other internet-bound traffic over the VPN. Which feature must the administrator configure? A. reverse route injection B. dynamic access policies C. local LAN access D. dynamic split tunneling Suggested Answer: D
Refer to the exhibit. Logins from internal users to a Cisco Adaptive Security Appliance firewall must be performed by using a TACACS server. The firewall is already configured. Which additional configuration must be performed to configure the TACACS+ server group with a key of Cisco4512!? A.
B.
C.
D.
Suggested Answer: A
A network engineer must create a workflow to detect when a device joins a network and send the onboarding configuration to the device by using the Cisco DNA Center API. Which two method and endpoint pairs must be used to implement the workflow? (Choose two.)
A.
 B.
B.
 C.
C.
 D.
D.
 E.
E.
 Suggested Answer: AB
Suggested Answer: AB
Which IPsec mode must be used when encrypting data over a public network between two servers with RFC1918 IP addresses? A. main mode B. aggressive mode C. transport mode D. tunnel mode Suggested Answer: D
Which platform uses Cyber Threat Intelligence as its main source of information? A. EPP B. EDR C. Cisco ASA D. Cisco Secure Endpoint Suggested Answer: D
Refer to the exhibit. Which task is the Python script performing by using the Umbrella Enforcement API? A. importing malicious domains to Cisco Umbrella Enforcement for additional processing B. importing malicious domains to Cisco Umbrella Enforcement for blocking C. editing malicious domains in Cisco Umbrella Enforcement that have changed status D. editing malicious domains in Cisco Umbrella Enforcement that have changed IP address Suggested Answer: B
Which security mechanism is designed to protect against “offline brute-force” attacks? A. Token B. MFA C. Salt D. CAPTCHA Suggested Answer: C
What is the default action before identifying the URL during HTTPS inspection in Cisco Secure Firewall Threat Defense software? A. reset B. buffer C. drop D. pass Suggested Answer: B
Which method is used on a Cisco IOS router to redirect traffic to the Cisco Secure Web Appliance for URL inspection? A. WCCP B. route map C. PAC file D. WPAD Suggested Answer: A
Which two global commands must the network administrator implement to limit the attack surface of an internet-facing Cisco router? (Choose two.) A. service tcp-keepalives-in B. no service password-recovery C. no cdp run D. no ip http server E. ip ssh version 2 Suggested Answer: DE
Refer to the exhibit. An engineer created a policy named usera1 on a Cisco Secure Email Gateway to enable the antispam feature for an email address of usera1@cisco.com . Which configuration step must be performed next to apply the policy only to the usera1@cisco.com email address? A. Specify the user in Mail Policies > Mail Policies Settings B. Click the Policy Name usera1 Policy, and then click Add User. C. Set the user in Mail Policies > Exception Table. D. Click IronPort Anti-Spam, and then click Add User. Suggested Answer: B
What is the purpose of a denial-of-service attack? A. to prevent or limit access to data on a computer system by encrypting it B. to exploit a security vulnerability on a computer system to steal sensitive information C. to spread throughout a computer system by self-replicating to additional hosts D. to disrupt the normal operation of a targeted system by overwhelming it Suggested Answer: D
A security engineer must add destinations into a destination list in Cisco Umbrella. What describes the application of these changes? A. The changes are applied only after the configuration is saved in Cisco Umbrella. B. The user role of Block Page Bypass or higher is needed to perform these changes. C. The changes are applied immediately if the destination list is part of a policy. D. The destination list must be removed from the policy before changes are made to it. Suggested Answer: C
Which file type is supported when performing a bulk upload of destinations into a destination list on Cisco Umbrella? A. XLS B. RTF C. TXT D. CSV Suggested Answer: C
A company has 5000 Windows users on its campus. Which two precautions should IT take to prevent WannaCry ransomware from spreading to all clients? (Choose two.) A. Put all company users in the trusted segment of NGFW and put all servers to the DMZ segment of the Cisco NGFW. B. Segment different departments to different IP blocks and enable Dynamic ARP Inspection on all VLANs. C. Ensure that noncompliant endpoints are segmented off to contain any potential damage. D. Ensure that a user cannot enter the network of another department. E. Perform a posture check to allow only network access to those Windows devices that are already patched. Suggested Answer: CE
An engineer is configuring a Cisco Secure Email Cloud Gateway instance to send logs to an external server for auditing. For security purposes, a username and SSH key with the fingerprint d0:46:03:8e:d7:f1:bb:9b:33:13:94:60:49:da:9b:e3 has been generated on the remote log server that accepts only the SSHv2 protocol. Which log retrieval method must be configured in the log subscription? A. syslog push B. manually download C. SCP push D. FTP push Suggested Answer: C
What is a difference between GRE over IPsec and IPsec with crypto map? A. GRE provides its own encryption mechanism. B. Multicast traffic is supported by IPsec with crypto map. C. IPsec with crypto map offers better scalability. D. GRE over IPsec supports non-IP protocols. Suggested Answer: D
An engineer configured 802.1X authentication on a switch port but cannot authenticate. Which action must the engineer take to validate if the user credentials are correct? A. Check the logs of the authentication server for the username and authentication rejection logs. B. Check policy enforcement point for the authentication mechanism and credentials used. C. Check the supplicant logs for the username and password entered, then check the authentication provider. D. Check the authenticator and view the debug logs for the username and password. Suggested Answer: A
Which feature only implements on the Cisco ASA in the transparent mode? A. inspect application layer of the traffic sent between hosts B. stateful inspection C. inspect traffic between hosts in the same subnet D. inspect anycast traffic Suggested Answer: C
Which two devices support WCCP for traffic redirection? (Choose two.) A. Cisco IOS B. Cisco Secure Web Appliance C. Cisco IPS D. proxy server E. Cisco ASA Suggested Answer: AE
Which two types of connectors are used to generate telemetry data from IPFIX records in a Cisco Secure Workload implementation? (Choose two.) A. NetFlow B. Cisco Secure Workload C. Cisco ASA D. ERSPAN E. ADC Suggested Answer: AD
An engineer is configuring Cisco Secure Web Appliance and needs to deploy it in transparent mode. Which configuration component must be used to accomplish this goal? A. MDA on the router B. WCCP on switch C. PBR on Cisco Secure Web Appliance D. DNS resolution on Cisco Secure Web Appliance Suggested Answer: B
Which two algorithms must be used when an engineer is creating a connection that will have classified data across it? (Choose two.) A. RSA-3072 B. ECDSA-256 C. AES-256 D. RC4 E. SHA-384 Suggested Answer: CE
Which process is used to obtain a certificate from a CA? A. enrollment B. registration C. approval D. signing Suggested Answer: A
Which method must be used to connect Cisco Secure Workload to external orchestrators at a client site when the client does not allow incoming connections? A. destination NAT B. reverse tunnel C. source NAT D. GRE tunnel Suggested Answer: B
Which two methods are valid to be included in an authentication method list? (Choose two.) A. default B. login C. console D. line E. enable Suggested Answer: BE
A network administrator is shipping a Cisco ASA to a remote retail site. The administrator wants to ensure that the device configuration cannot be accessed by someone at the site with physical access and a console cable. Which command must be used to mitigate this risk? A. aaa authentication console B. config-register 0x00000041 C. no service password-recovery D. no service sw-reset-button Suggested Answer: C
Which Cisco platform provides an agentless solution to provide visibility across the network including encrypted traffic analytics to detect malware in encrypted traffic without the need for decryption? A. Cisco Secure Network Analytics B. Cisco ISE C. Cisco AMP D. Cisco Secure Client Suggested Answer: A
Which two products are used to forecast capacity needs accurately in real time? (Choose two.) A. Cisco Secure Workload B. Cisco Cloudlock C. Cisco Umbrella D. Cisco AppDynamics E. Cisco Workload Optimization Manager Suggested Answer: DE
A Cisco Secure Cloud Analytics administrator is setting up a private network monitor sensor to monitor an on-premises environment. Which two pieces of information from the sensor are used to link to the Secure Cloud Analytics portal? (Choose two.) A. private IP address B. unique service key C. SSL certificate D. public IP address E. NAT ID Suggested Answer: BD
A network administrator is setting up Cisco FMC to send logs to Cisco Security Analytics and Logging (SaaS). The network administrator is anticipating a high volume of logging events from the firewalls and wants to limit the strain on firewall resources. Which method must the administrator use to send these logs to Cisco Security Analytics and Logging? A. direct connection using SNMP traps B. HTTP POST using the Security Analytics FMC plugin C. syslog using the Secure Event Connector D. SFTP using the FMC CLI Suggested Answer: C
Refer to the exhibit.The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally? A. P2 and P3 only B. P5, P6, and P7 only C. P1, P2, P3, and P4 only D. P2, P3, and P6 only Suggested Answer: D
Which solution operates as a cloud-native CASB? A. Cisco Stealthwatch Cloud B. Cisco Umbrella C. Cisco pxGrid D. Cisco CloudLock Suggested Answer: B
Which entity is responsible for encrypting data in transit using an IaaS model versus a SaaS model? A. Cloud Application Developer for IaaS and Cloud SLA Manager for SaaS B. Cloud SLA Manager for IaaS and Cloud Application Developer for SaaS C. Cloud Service Provider for IaaS and Cloud Service Customer for SaaS D. Cloud Service Customer for IaaS and Cloud Service Provider for SaaS Suggested Answer: D
Which two aspects of the IaaS cloud service model are managed by the service provider? (Choose two.) A. virtual machines B. physical network C. applications D. hypervisors E. virtual network Suggested Answer: AB
For a given policy in Cisco Umbrella, how should a customer block websites based on a custom list? A. by adding the website IP addresses to the Cisco Umbrella blocklist B. by adding the websites to a blocked type destination list C. by specifying blocked domains in the policy settings D. by specifying the websites in a custom blocked category Suggested Answer: B
Which solution provides end-to-end visibility of applications and insights about application performance? A. Cisco AppDynamics B. Cisco Tetration C. Cisco Secure Cloud Analytics D. Cisco Cloudlock Suggested Answer: A
An administrator needs to be able to have a router securely communicate with a network management system. The connections must be authenticated but not encrypted. While meeting these requirements, which command will create a group that allows a user on the network management system access to the router? A. snmp-server group v3 auth B. snmp-server group v3 priv write C. snmp-server group v2c D. snmp-server group v2c write Suggested Answer: A
Refer to the exhibit. An engineer must enable secure SSH protocols and enters this configuration. What are two results of running this set of commands on a Cisco router? (Choose two.) A. generates RSA key pairs on the router B. enables SSHv1 on the router C. uses the FQDN with the label command D. labels the key pairs to be used for SSH E. generates AES key pairs on the router Suggested Answer: AD
Which algorithm does ISAKMP use to securely derive encryption and integrity keys? A. RSA B. AES C. 3DES D. Diffie-Hellman Suggested Answer: D
Which two activities are performed using Cisco DNA Center? (Choose two.) A. accounting B. design C. provision D. DNS E. DHCP Suggested Answer: BC
A network administrator is setting up a site-to-site VPN from a Cisco FTD to a cloud environment. After the administrator configures the VPN on both sides, they still cannot reach the cloud environment. Which command must the administrator run on the FTD to verify that the VPN is encrypting traffic in both directions? A. show crypto ipsec sa B. show crypto ipsec stats C. show vpn-sessiondb detail l2l D. show crypto isakmp sa Suggested Answer: A
Which two tasks are required when a decryption policy is implemented on a Cisco WSA? (Choose two.) A. Configure invalid certificate handling. B. Upload a root certificate and private key. C. Enable real-time revocation status checking. D. Enable HTTPS attack protection. E. Enable the HTTPS proxy. Suggested Answer: BE
An organization is using CSR1000v routers in their private cloud infrastructure. They must upgrade their code to address vulnerabilities within their running code version. Who is responsible for these upgrades? A. The organization must update the code for the devices they manage. B. The cloud vendor is responsible for updating all code hosted in the cloud. C. The cloud service provider must be asked to perform the upgrade. D. The CSR1000v is upgraded automatically as new code becomes available. Suggested Answer: A
An organization wants to reduce their attack surface for cloud applications. They want to understand application communications, detect abnormal application behavior, and detect vulnerabilities within the applications. Which action accomplishes this task? A. Configure Cisco Tetration to detect anomalies and vulnerabilities. B. Modify the Cisco Duo configuration to restrict access between applications. C. Use Cisco ISE to provide application visibility and restrict access to them. D. Implement Cisco Umbrella to control the access each application is granted. Suggested Answer: A
Which Cisco AnyConnect module is integrated with Splunk Enterprise to provide monitoring capabilities to administrators to allow them to view endpoint application usage? A. AMP Enabler B. Umbrella Roaming Security C. ISE Posture D. Network Visibility Suggested Answer: D
What describes the function of the crypto isakmp key C1$c451090787 address 0.0.0.0 0.0.0.0 command when configuring an IPsec VPN tunnel on a Cisco IOS router? A. It allows connections from any hosts using the defined preshared key. B. It defines that all data is going to be encrypted via the VPN. C. It configures the IP address and subnet mask of the VPN server. D. It drops spoofed VPN traffic using 0.0.0.0 as the source or destination IP address. Suggested Answer: A
Which common threat can be prevented by implementing port security on switch ports? A. VLAN hopping attacks B. spoofing attacks C. denial-of-service attacks D. eavesdropping attacks Suggested Answer: D
What is the ideal deployment mode to use when you need to manage separate security policies for multiple customers on a Cisco ASA device? A. spanned cluster mode B. IRB mode C. VRF mode D. multiple context mode Suggested Answer: D
In which cloud services model is the customer responsible for scanning for and mitigation of application vulnerabilities? A. VMaaS B. IaaS C. PaaS D. SaaS Suggested Answer: B
What is a benefit of a Cisco Secure Email Gateway Virtual as compared to a physical Secure Email Gateway? A. simplifies the distribution of software updates B. enables the allocation of additional resources C. provides an automated setup process D. provides faster performance Suggested Answer: B
Which metric is used by the monitoring agent to collect and output packet loss and jitter information? A. RTP performance B. TCP performance C. WSAv performance D. AVC performance Suggested Answer: A
DRAG DROP - Drag and drop the VPN functions from the left onto the descriptions on the right.Suggested Answer:

Which direction do attackers encode data in DNS requests during exfiltration using DNS tunneling? A. outbound B. north-south C. east-west D. inbound Suggested Answer: A
Which Cisco Firewall solution requires zone definition? A. CBAC B. Cisco AMP C. ZBFW D. Cisco ASA Suggested Answer: D
Which firewall deployment mode allows inspection of traffic between servers in the same IP subnet? A. routed B. multicontext C. virtual D. transparent Suggested Answer: D
What are two functionalities of SDN southbound APIs? (Choose two.) A. Southbound APIs from the interface between the SDN controller and business applications. B. Application layer programs communicate with the SDN controller through the southbound APIs. C. OpenFlow is a standardized southbound API protocol used between the SDN controller and the switch. D. Southbound APIs form the interface between the SDN controller and the network switches and routers. E. Southbound APIs provide a programmable interface for applications to configure the network. Suggested Answer: CD
How does Cisco AMP for Endpoints provide next-generation protection? A. It encrypts data on user endpoints to protect against ransomware. B. It utilizes Cisco pxGrid, which allows AMP for Endpoints to pull threat feeds from threat intelligence centers. C. It leverages an endpoint protection platform and endpoint detection and response. D. It integrates with Cisco FTD devices. Suggested Answer: C
When MAB is configured for use within the 802.1X environment, an administrator must create a policy that allows the devices onto the network. Which information is used for the username and password? A. The MAB uses the IP address as username and password. B. The MAB uses the Call-Station-ID as username and password. C. The MAB uses the MAC address as username and password. D. Each device must be set manually by the administrator. Suggested Answer: C
Which two VPN tunneling protocols support the use of IPsec to provide data integrity, authentication, and data encryption? (Choose two.) A. Secure Socket Tunneling Protocol B. OpenVPN C. Generic Routing Encapsulation Protocol D. Layer 2 Tunneling Protocol E. Point-to-Point Tunneling Protocol Suggested Answer: CD
DRAG DROP -Refer to the exhibit. An engineer must configure a Cisco switch to perform PPP authentication via a TACACS server located at IP address 10.1.1.10. Authentication must fall back to the local database using the username LocalUser and password C1$c0445915422! if TACACS server is unreachable. Drag and drop the commands from the left onto the corresponding configuration steps on the right.
Suggested Answer:

Which Cisco Umbrella package supports selective proxy for inspection of traffic from risky domains? A. DNS Security Advantage B. SIG Essentials C. DNS Security Essentials D. SIG Advantage Suggested Answer: A
What are the two distribution methods available to an administrator when performing a fresh rollout of the Cisco AnyConnect Secure Mobility Client? (Choose two.) A. web deploy B. SFTP C. TFTP D. cloud update E. predeploy Suggested Answer: AE
Which Cisco security solution integrates with cloud applications like Dropbox and Office 365 while protecting data from being exfiltrated? A. Cisco Stealthwatch Cloud B. Cisco Talos C. Cisco Umbrella Investigate D. Cisco Cloudlock Suggested Answer: D
An engineer must configure Cisco AMP for Endpoints so that it contains a list of files that should not be executed by users. These files must not be quarantined. Which action meets this configuration requirement? A. Modify the advanced custom detection list to include these files. B. Add a list for simple custom detection. C. Identify the network IPs and place them in a blocked list. D. Create an application control blocked applications list. Suggested Answer: D
What are two characteristics of the RESTful architecture used within Cisco DNA Center? (Choose two.) A. REST codes can be compiled with any programming language. B. REST uses HTTP to send a request to a web service. C. The POST action replaces existing data at the URL path. D. REST uses methods such as GET, PUT, POST, and DELETE. E. REST is a Linux platform-based architecture. Suggested Answer: BD
A security audit recently revealed that an administrator is using the same password of C1$c0448845217 for his personal account across multiple systems. What must be implemented by the company to reduce the chances of this happening again? A. centralized user authentication B. role based access control C. security awareness training D. strict password policies Suggested Answer: C
Which type of algorithm provides the highest level of protection against brute-force attacks? A. PFS B. MD5 C. HMAC D. SHA Suggested Answer: D
When a site-to-site VPN is configured in Cisco FMC, which topology is supported when crypto ACLs are used instead of protected networks to define interesting traffic? A. hub-and-spoke B. full mesh C. DMVPN D. point-to-point Suggested Answer: D
For Cisco IOS PKI, which two types of servers are used as a distribution point for CRLs? (Choose two.) A. subordinate CA B. HTTP C. SDP D. LDAP E. SCP Suggested Answer: BD
An engineer is implementing DHCP security mechanisms and needs the ability to add additional attributes to profiles that are created within Cisco ISE. Which action accomplishes this task? A. Use DHCP option 82 to ensure that the request is from a legitimate endpoint and send the information to Cisco ISE. B. Define MAC-to-IP address mappings in the switch to ensure that rogue devices cannot get an IP address. C. Modify the DHCP relay and point the IP address to Cisco ISE. D. Configure DHCP snooping on the switch VLANs and trust the necessary interfaces. Suggested Answer: D
Refer to the exhibit. Consider that any feature of DNS requests, such as the length of the domain name and the number of subdomains, can be used to construct models of expected behavior to which observed values can be compared. Which type of malicious attack are these values associated with? A. W32/AutoRun worm B. HeartBleed SSL Bug C. Eternal Blue Windows D. Spectre Worm Suggested Answer: A
An engineer is adding a Cisco router to an existing environment. NTP authentication is configured on all devices in the environment with the command ntp authentication-key 1 md5 Cisc433392759. There are two routers on the network that are configured as NTP servers for redundancy, 192.168.1.110 and 192.168.1.111. 192.168.1.110 is configured as the authoritative time source. What command must be configured on the new router to use 192.168.1.110 as its primary time source without the new router attempting to offer time to existing devices? A. ntp server 192.168.1.110 primary key 1 B. ntp server 192.168.1.110 key 1 prefer C. ntp peer 192.168.1.110 prefer key 1 D. ntp peer 192.168.1.110 key 1 primary Suggested Answer: B
Which function is included when Cisco AMP is added to web security? A. detailed analytics of the unknown file's behavior B. multifactor, authentication-based user identity C. threat prevention on an infected endpoint D. phishing detection on emails Suggested Answer: A
An organization is moving toward the zero-trust model. Which Cisco solution enables administrators to deploy and control microsegmentation of endpoints that are connected to a Cisco Data Center Virtual Edge, Cisco Application Virtual Switch, Microsoft vSwitch, and VMware vSphere Distributed Switch? A. Cisco Titration B. Cisco DCNM C. Cisco Stealthwatch D. Cisco ACI Suggested Answer: D
What is offered by an EPP solution but not an EDR solution? A. investigation B. containment C. sandboxing D. detection Suggested Answer: C
Which Cisco AMP feature allows an engineer to look back to trace past activities, such as file and process activity on an endpoint? A. endpoint isolation B. retrospective security C. advanced search D. advanced investigation Suggested Answer: B
Which feature is used in a push model to allow for session identification host reauthentication and session termination? A. CoA request B. carrier-grade NAT C. AAA attributes D. AV pair Suggested Answer: A
What is the term for the concept of limiting communication between applications or containers on the same node? A. software-defined access B. microservicing C. microsegmentation D. container orchestration Suggested Answer: C
An engineer is configuring Cisco WSA and needs to ensure end clients are protected against DNS spoofing attacks. Which deployment method accomplishes this goal? A. transparent mode B. Web Cache Communication Protocol C. explicit forward D. single-context mode Suggested Answer: A
Refer to the exhibit. What is the result of this Python script of the Cisco DNA Center API? A. adds a switch to Cisco DNA Center B. receives information about a switch C. deletes a switch from Cisco DNA Center D. adds authentication to a switch Suggested Answer: A
Which two configurations must be made on Cisco ISE and on Cisco TrustSec devices to force a session to be adjusted after a policy change is made? (Choose two.) A. posture assessment B. aaa authorization exec default local C. tacacs-server host 10.1.1.250 key password D. aaa server radius dynamic-author E. CoA Suggested Answer: DE
Which Cisco network security device supports contextual awareness? A. ISE B. Cisco IOS C. Cisco ASA D. Firepower Suggested Answer: A
When a next-generation endpoint security solution is selected for a company, what are two key deliverables that help justify the implementation? (Choose two.) A. signature-based endpoint protection on company endpoints B. email integration to protect endpoints from malicious content that is located in email C. real-time feeds from global threat intelligence centers D. macro-based protection to keep connected endpoints safe E. continuous monitoring of all files that are located on connected endpoints Suggested Answer: CE
A company recently discovered an attack propagating throughout their Windows network via a file named abc123456789xyz.exe. The malicious file was uploaded to a Simple Custom Detection list in the AMP for Endpoints Portal and the currently applied policy for the Windows clients was updated to reference the detection list. Verification testing scans on known infected systems shows that AMP for Endpoints is not detecting the presence of this file as an indicator of compromise. What must be performed to ensure detection of the malicious file? A. Check the box in the policy configuration to send the file to Cisco Threat Grid for dynamic analysis. B. Upload the malicious file to the Blocked Application Control List. C. Upload the SHA-256 hash for the file to the Simple Custom Detection List. D. Use an Advanced Custom Detection List instead of a Simple Custom Detection List. Suggested Answer: C
An engineer must set up 200 new laptops on a network and wants to prevent the users from moving their laptops around to simplify administration. Which switch port MAC address security setting must be used? A. aging B. static C. sticky D. maximum Suggested Answer: C
Which service allows a user export application usage and performance statistics with Cisco Application Visibility and Control? A. NetFlow B. SNORT C. SNMP D. 802.1X Suggested Answer: A
Which solution allows an administrator to provision, monitor, and secure mobile devices on Windows and Mac computers from a centralized dashboard? A. Cisco Stealthwatch B. Cisco Umbrella C. Cisco AMP for Endpoints D. Cisco ISE Suggested Answer: D
Which parameter is required when configuring a NetFlow exporter on a Cisco router? A. exporter name B. exporter description C. source interface D. DSCP value Suggested Answer: A
Which type of encryption uses a public key and a private key? A. nonlinear B. symmetric C. linear D. asymmetric Suggested Answer: D
Which two authentication protocols are supported by the Cisco WSA? (Choose two.) A. TLS B. LDAP C. SSL D. WCCP E. NTLM Suggested Answer: BE
Which two capabilities does an MDM provide? (Choose two.) A. manual identification and classification of client devices B. unified management of mobile devices, Macs, and PCs from a centralized dashboard C. delivery of network malware reports to an inbox in a schedule D. enforcement of device security policies from a centralized dashboard E. unified management of Android and Apple devices from a centralized dashboard Suggested Answer: BD
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.) A. Use Cisco Umbrella B. Use next generation firewalls. C. Block all 'TXT' DNS records. D. Use intrusion prevention system. E. Enforce security over port 53. Suggested Answer: AE
What is a capability of Cisco ASA NetFlow? A. It sends NetFlow data records from active and standby ASAs in an active-standby failover pair. B. It logs all event types only to the same collector. C. It filters NSEL events based on traffic. D. It generates NSEL events even if the MPF is not configured. Suggested Answer: C
Which Cisco ISE service checks the compliance of endpoints before allowing the endpoints to connect to the network? A. Threat Centric NAC B. Cisco TrustSec C. Posture D. Profiler Suggested Answer: C
What do tools like Jenkins, Octopus Deploy, and Azure DevOps provide in terms of application and infrastructure automation? A. cloud application security broker B. compile-time instrumentation C. container orchestration D. continuous integration and continuous deployment Suggested Answer: D
When a Cisco WSA checks a web request, what occurs if it is unable to match a user-defined policy? A. It applies the next identification profile policy. B. It applies the global policy. C. It applies the advanced policy. D. It blocks the request. Suggested Answer: B
What is a benefit of using Cisco ISE for device compliance? A. outbreak control B. retrospective analysis C. device analysis D. zero-trust approach Suggested Answer: D
Based on the NIST 800-145 guide, which cloud architecture is provisioned for exclusive use by a specific group of consumers from different organizations and may be owned, managed, and operated by one or more of those organizations? A. community cloud B. private cloud C. public cloud D. hybrid cloud Suggested Answer: A
DRAG DROP - Drag and drop the descriptions from the left onto the encryption algorithms on the right.Suggested Answer:

Which VMware platform does Cisco ACI integrate with to provide enhanced visibility, provide policy integration and deployment, and implement security policies with access lists? A. VMware horizons B. VMware vRealize C. VMware APIC D. VMware fusion Suggested Answer: B
A small organization needs to reduce the VPN bandwidth load on their headend Cisco ASA in order to ensure that bandwidth is available for VPN users needing access to corporate resources on the 10.0.0.0/24 local HQ network. How is this accomplished without adding additional devices to the network? A. Configure VPN load balancing to distribute traffic for the 10.0.0.0/24 network. B. Configure VPN load balancing to send non-corporate traffic straight to the internet. C. Use split tunneling to tunnel traffic for the 10.0.0.0/24 network only. D. Use split tunneling to tunnel all traffic except for the 10.0.0.0/24 network. Suggested Answer: C
An engineer is configuring cloud logging using a company-managed Amazon S3 bucket for Cisco Umbrella logs. What benefit does this configuration provide for accessing log data? A. It can grant third-party SIEM integrations write access to the S3 bucket. B. Data can be stored offline for 30 days. C. No other applications except Cisco Umbrella can write to the S3 bucket. D. It is included in the license cost for the multi-org console of Cisco Umbrella. Suggested Answer: A
Which algorithm is an NGE hash function? A. HMAC B. SHA-1 C. MD5 D. SHA-2 Suggested Answer: D
An organization is implementing AAA for their users. They need to ensure that authorization is verified for every command that is being entered by the network administrator. Which protocol must be configured in order to provide this capability? A. EAPOL B. SSH C. RADIUS D. TACACS+ Suggested Answer: D
In which two ways does the Cisco Advanced Phishing Protection solution protect users? (Choose two.) A. It prevents use of compromised accounts and social engineering. B. It automatically removes malicious emails from users' inbox. C. It secures all passwords that are shared in video conferences. D. It prevents trojan horse malware using sensors. E. It prevents all zero-day attacks coming from the Internet. Suggested Answer: AE
In which two customer environments is the Cisco WSAv connector traffic direction method selected? (Choose two.) A. Customer owns ASA Appliance and Virtual Form Factor is required. B. Customer does not own Cisco hardware and needs Explicit Proxy. C. Customer owns ASA Appliance and SSL Tunneling is required. D. Customer needs to support roaming users. E. Customer does not own Cisco hardware and needs Transparent Redirection (WCCP). Suggested Answer: AE
Which capability is provided by application visibility and control? A. data obfuscation B. deep packet inspection C. reputation filtering D. data encryption Suggested Answer: B
Which feature within Cisco ISE verifies the compliance of an endpoint before providing access to the network? A. pxGrid B. Profiling C. Posture D. MAB Suggested Answer: C
Which two fields are defined in the NetFlow flow? (Choose two.) A. destination port B. Layer 4 protocol type C. output logical interface D. class of service bits E. type of service byte Suggested Answer: AE
Which type of API is being used when a controller within a software-defined network architecture dynamically makes configuration changes on switches within the network? A. northbound API B. westbound API C. eastbound API D. southbound API Suggested Answer: D
Which solution detects threats across a private network, public clouds, and encrypted traffic? A. Cisco Encrypted Traffic Analytics B. Cisco Stealthwatch C. Cisco CTA D. Cisco Umbrella Suggested Answer: B
What is a benefit of using Cisco Tetration? A. It collects policy compliance data and process details. B. It collects near-real time data from servers and inventories the software packages that exist on servers. C. It collects enforcement data from servers and collects interpacket variation. D. It collects telemetry data from servers and then uses software sensors to analyze flow information. Suggested Answer: D
Which attack type attempts to shut down a machine or network so that users are not able to access it? A. bluesnarfing B. MAC spoofing C. smurf D. IP spoofing Suggested Answer: C
Which Cisco solution integrates Encrypted Traffic Analytics to perform enhanced visibility, promote compliance, shorten response times, and provide administrators with the information needed to provide educated and automated decisions to secure the environment? A. Cisco ISE B. Cisco SDN C. Cisco Security Compliance Solution D. Cisco DNA Center Suggested Answer: C
Which two components do southbound APIs use to communicate with downstream devices? (Choose two.) A. OpFlex B. applications running over the network C. OpenFlow D. services running over the network E. external application APIs Suggested Answer: AC
A network engineer has configured a NTP server on a Cisco ASA. The ASA has IP reachability to the NTP server and is not filtering any traffic. The show ntp association detail command indicates that the configured NTP server is unsynchronized and has a stratum of 16. What is the cause of this issue? A. An access list entry for UDP port 123 on the outside interface is missing. B. Resynchronization of NTP is not forced. C. NTP is not configured to use a working server. D. An access list entry for UDP port 123 on the inside interface is missing. Suggested Answer: C
Which API method and required attribute are used to add a device into Cisco DNA Center with the native API? A. GET and serialNumber B. userSudiSerlalNos and deviceInfo C. POST and name D. lastSyncTime and pid Suggested Answer: A
An engineer must deploy a network security management solution to provide the operations team with a unified view of the security environment. The company operates a hybrid cloud with an element of on-premises private hosting for critical applications and data. The operations team requires a single solution that will be used to manage and configure: • Firewalls • Intrusion Prevention System • Application control • URL filtering • Advanced malware protection Which Cisco solution must be deployed? A. Secure Firewall Threat Defense B. Adaptive Security Device Manager C. Next-Generation Firewall D. Secure Firewall Management Center Suggested Answer: D
What is the purpose of the Cisco Endpoint IoC feature? A. It is an incident response tool. B. It provides stealth threat prevention. C. It is a signature-based engine. D. It provides precompromise detection. Suggested Answer: A
What is a benefit of flexible NetFlow records? A. They have customized traffic identification. B. They are used for accounting. C. They are used for security. D. They monitor a packet from Layer 2 to Layer 5. Suggested Answer: A
DRAG DROP - Drag and drop the Cisco CWS redirection options from the left onto the capabilities on the right.Suggested Answer:

Which cryptographic process provides origin confidentiality, integrity, and origin authentication for packets? A. AH B. IKEv1 C. IKEv2 D. ESP Suggested Answer: D
What are two security benefits of an MDM deployment? (Choose two.) A. distributed dashboard B. distributed software upgrade C. privacy control checks D. on-device content management E. robust security policy enforcement Suggested Answer: DE
Which Cisco security solution stops exfiltration using HTTPS? A. Cisco CTA B. Cisco FTD C. Cisco AnyConnect D. Cisco ASA Suggested Answer: A
Which solution is made from a collection of secure development practices and guidelines that developers must follow to build secure applications? A. Radamsa B. Fuzzing Framework C. AFL D. OWASP Suggested Answer: D
An engineer is deploying Cisco Advanced Malware Protection (AMP) for Endpoints and wants to create a policy that prevents users from executing a file named abc123456789.exe without quarantining that file. What type of Outbreak Control list must the SHA-256 hash value for the file be added to in order to accomplish this? A. Advanced Custom Detection B. Simple Custom Detection C. Isolation D. Blocked Application Suggested Answer: D
What is the purpose of a NetFlow version 9 template record? A. It serves as a unique identification number to distinguish individual data records B. It defines the format of data records. C. It specifies the data format of NetFlow processes. D. It provides a standardized set of Information about an IP row. Suggested Answer: B
An organization is using DNS services for their network and want to help improve the security of the DNS infrastructure. Which action accomplishes this task? A. Use DNSSEC between the endpoints and Cisco Umbrella DNS servers. B. Modify the Cisco Umbrella configuration to pass queries only to non-DNSSEC capable zones. C. Integrate Cisco Umbrella with Cisco CloudLock to ensure that DNSSEC is functional. D. Configure Cisco Umbrella and use DNSSEC for domain authentication to authoritative servers. Suggested Answer: D
Which Cisco security solution provides patch management in the cloud? A. Cisco Umbrella B. Cisco ISE C. Cisco CloudLock D. Cisco Tetration Suggested Answer: C
Which solution is more secure than the traditional use of a username and password and encompasses at least two of the methods of authentication? A. RADIUS/LDAP authentication B. single-sign on C. Kerberos security solution D. multifactor authentication Suggested Answer: D
Which Talos reputation center allows for tracking the reputation of IP addresses for email and web traffic? A. IP Block List Center B. IP and Domain Reputation Center C. Cisco AMP Reputation Center D. File Reputation Center Suggested Answer: B
A switch with Dynamic ARP Inspection enabled has received a spoofed ARP response on a trusted interface. How does the switch behave in this situation? A. It drops the packet after validation by using the IP & MAC Binding Table. B. It forwards the packet without validation. C. It forwards the packet after validation by using the IP & MAC Binding Table. D. It drops the packet without validation. Suggested Answer: B
DRAG DROP - A network engineer is configuring NetFlow top talkers on a Cisco router. Drag and drop the steps in the process from the left into the sequence on the right.Suggested Answer:

Refer to the exhibit. Which command results in these messages when attempting to troubleshoot an IPsec VPN connection? A. debug crypto isakmp connection B. debug crypto ipsec C. debug crypto ipsec endpoint D. debug crypto isakmp Suggested Answer: B
Which technology provides a combination of endpoint protection, endpoint detection, and response? A. Cisco Threat Grid B. Cisco Umbrella C. Cisco Talos D. Cisco AMP Suggested Answer: D
DRAG DROP - Drag and drop the concepts from the left onto the descriptions on the right.Suggested Answer:

Which industry standard is used to integrate Cisco ISE and Cisco pxGrid to each other and with other interoperable security platforms? A. NIST B. ANSI C. IETF D. IEEE Suggested Answer: C
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client? A. AMP for Endpoints authenticates users and provides segmentation, and the Umbrella Roaming Client allows only for VPN connectivity. B. AMP for Endpoints stops and tracks malicious activity on hosts, and the Umbrella Roaming Client tracks only URL-based threats. C. The Umbrella Roaming Client authenticates users and provides segmentation, and AMP for Endpoints allows only for VPN connectivity. D. The Umbrella Roaming client stops and tracks malicious activity on hosts, and AMP for Endpoints tracks only URL-based threats. Suggested Answer: B
Which Cisco ISE feature helps to detect missing patches and helps with remediation? A. enabling probes B. profiling policy C. authentication policy D. posture assessment Suggested Answer: B
Which feature requires that network telemetry be enabled? A. Layer 2 device discovery B. per-interface stats C. central syslog system D. SNMP trap notification Suggested Answer: C
What is provided by the Secure Hash Algorithm in a VPN? A. authentication B. encryption C. integrity D. key exchange Suggested Answer: C
Refer to the exhibit. When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZ_inside zone once the configuration is deployed? A. No traffic will be allowed through to the DMZ_inside zone regardless of if it’s trusted or not. B. All traffic from any zone will be allowed to the DMZ_inside zone only after inspection. C. All traffic from any zone to the DMZ_inside zone will be permitted with no further inspection. D. No traffic will be allowed through to the DMZ_inside zone unless it's already trusted. Suggested Answer: C
A company identified a phishing vulnerability during a pentest. What are two ways the company can protect employees from the attack? (Choose two.) A. using an inline IPS/IDS in the network B. using Cisco Umbrella C. using Cisco ESA D. using Cisco ISE E. using Cisco FTD Suggested Answer: AE
What is the process in DevSecOps where all changes in the central code repository are merged and synchronized? A. EP B. CD C. CI D. QA Suggested Answer: B
What is a function of Cisco AMP for Endpoints? A. It protects against web-based attacks. B. It automates threat responses of an infected host. C. It detects DNS attacks. D. It blocks email-based attacks. Suggested Answer: B
What does endpoint isolation in Cisco AMP for Endpoints security protect from? A. an infection spreading across the LDAP or Active Directory domain from a user account B. a malware spreading across the user device C. an infection spreading across the network D. a malware spreading across the LDAP or Active Directory domain from a user account Suggested Answer: C
An engineer recently completed the system setup on a Cisco WSA. Which URL information does the system send to SensorBase Network servers? A. complete URL, without obfuscating the path segments B. URL information collected from clients that connect to the Cisco WSA using Cisco AnyConnect C. none because SensorBase Network Participation is disabled by default D. summarized server-name information and MD5-hashed path information Suggested Answer: A
Which Cisco DNA Center RESTful PNP API adds and claims a device into a workflow? A. api/v1/onboarding/workflow B. api/v1/onboarding/pnp-device/import C. api/v1/onboarding/pnp-device D. api/v1/file/config Suggested Answer: B
Which solution should be leveraged for secure access of a CI/CD pipeline? A. Duo Network Gateway B. Cisco FTD network gateway C. SSL WebVPN D. remote access client Suggested Answer: A
What is the purpose of CA in a PKI? A. to validate the authenticity of a digital certificate B. to issue and revoke digital certificates C. to certify the ownership of a public key by the named subject D. to create the private key for a digital certificate Suggested Answer: B
Which security solution is used for posture assessment of the endpoints in a BYOD solution? A. Cisco ISE B. Cisco FTD C. Cisco Umbrella D. Cisco ASA Suggested Answer: A
Which two commands are required when configuring a flow-export action on a Cisco ASA? (Choose two.) A. flow-export event-type B. policy-map C. access-list D. flow-export template timeout-rate 15 E. access-group Suggested Answer: AB
What are two trojan malware attacks? (Choose two.) A. frontdoor B. sync C. smurf D. rootkit E. backdoor Suggested Answer: DE
What are two benefits of using an MDM solution? (Choose two.) A. enhanced DNS security for endpoint devices B. on-device content management C. remote wipe capabilities to protect information on lost or stolen devices D. antimalware and antispyware functionality E. allows for mobile endpoints to be used for authentication methods Suggested Answer: BC
Which VPN provides scalability for organizations with many remote sites? A. DMVPN B. SSLVPN C. GRE over IPsec D. site-to-site IPsec Suggested Answer: A
For which type of attack is multifactor authentication an effective deterrent? A. syn flood B. phishing C. teardrop D. ping of death Suggested Answer: B
Which two cryptographic algorithms are used with IPsec? (Choose two.) A. HMAC-SHA/SHA2 B. AES-BAC C. Triple AMC-CBC D. AES-CBC E. AES-ABC Suggested Answer: AD Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnips/configuration/15-mt/sec-sec-for-vpns-w-ipsec-15-mt-book/sec-cfg-vpn-ipsec.html
Which Cisco security solution secures public, private, hybrid, and community clouds? A. Cisco ISE B. Cisco ASAv C. Cisco Cloudlock D. Cisco pxGrid Suggested Answer: C
A university policy must allow open access to resources on the Internet for research, but internal workstations are exposed to malware. Which Cisco AMP feature allows the engineering team to determine whether a file is installed on a selected few workstations? A. file prevalence B. file discovery C. file conviction D. file manager Suggested Answer: A
Which action must be taken in the AMP for Endpoints console to detect specific MD5 signatures on endpoints and then quarantine the files? A. Configure an advanced custom detection list. B. Configure an IP Block & Allow custom detection list C. Configure an application custom detection list D. Configure a simple custom detection list Suggested Answer: A
What is the target in a phishing attack? A. perimeter firewall B. IPS C. web server D. endpoint Suggested Answer: D
An engineer is trying to decide whether to use Cisco Umbrella. Cisco CloudLock. Cisco Stealthwatch. or Cisco AppDynamics Cloud Monitoring for visibility into data transfers as well as protection against data exfiltration. Which solution best meets these requirements? A. Cisco AppDynamics Cloud Monitoring B. Cisco CloudLock C. Cisco Stealthwatch D. Cisco Umbrella Suggested Answer: C
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments? A. Cisco Stealthwatch Cloud B. Cisco Umbrella C. Cisco AppDynamics D. Cisco CloudLock Suggested Answer: A
Which solution supports high availability in routed or transparent mode as well as in northbound and southbound deployments? A. Cisco FTD with Cisco ASDM B. Cisco Firepower NGFW Virtual appliance with Cisco FMC C. Cisco Firepower NGFW physical appliance with Cisco FMC D. Cisco FTD with Cisco FMC Suggested Answer: D
When choosing an algorithm to use. what should be considered about Diffie Heilman and RSA for key establishment? A. RSA is a symmetric key establishment algorithm intended to output asymmetric keys. B. DH is an asymmetric key establishment algorithm intended to output symmetric keys. C. DH is a symmetric key establishment algorithm intended to output asymmetric keys. D. RSA is an asymmetric key establishment algorithm intended to output symmetric keys. Suggested Answer: B
What provides total management for mobile and PC including managing inventory and device tracking, remote view, and live troubleshooting using the included native remote desktop support? A. mobile access management B. mobile content management C. mobile application management D. mobile device management Suggested Answer: D
With regard to RFC 5176 compliance, how many IETF attributes are supported by the RADIUS CoA feature? A. 3 B. 5 C. 10 D. 12 Suggested Answer: D
Which two protocols must be configured to authenticate end users to the Cisco WSA? (Choose two.) A. TACACS+ B. CHAP C. NTLMSSP D. RADIUS E. Kerberos Suggested Answer: AD
Which feature must be configured before implementing NetFlow on a router? A. syslog B. IP routing C. VRF D. SNMPv3 Suggested Answer: B
An engineer needs to detect and quarantine a file named abc123456789.zip based on the MD5 signature of the file using the Outbreak Control list feature within Cisco Advanced Malware Protection (AMP) for Endpoints. The configured detection method must work on files of unknown disposition. Which Outbreak Control list must be configured to provide this? A. Simple Custom Detection B. Blocked Application C. Advanced Custom Detection D. Android Custom Detection Suggested Answer: C
What is a characteristic of an EDR solution and not of an EPP solution? A. performs signature-based detection B. decrypts SSL traffic for better visibility C. stops all ransomware attacks D. retrospective analysis Suggested Answer: C
What is a benefit of using Cisco Umbrella? A. Files are scanned for viruses before they are allowed to run. B. All Internet traffic is encrypted. C. It prevents malicious inbound traffic. D. Attacks can be mitigated before the application connection occurs. Suggested Answer: D
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers and can be stopped by Cisco Umbrella? A. DNS hijacking B. cache poisoning C. DNS tunneling D. DNS flood attack Suggested Answer: C Reference: https://umbrella.cisco.com/blog/improvements-dns-tunneling-dns-exfiltration-detection
Client workstations are experiencing extremely poor response time. An engineer suspects that an attacker is eavesdropping and making independent connections while relaying messages between victims to make them think they are talking to each other over a private connection. Which feature must be enabled and configured to provide relief from this type of attack? A. Link Aggregation B. Reverse ARP C. private VLANs D. Dynamic ARP Inspection Suggested Answer: D
Which command is used to log all events to a destination collector 209.165.201.10? A. CiscoASA(config-pmap-c)# flow-export event-type all destination 209.165.201.10 B. CiscoASA(config-cmap)# flow-export event-type flow-update destination 209.165.201.10 C. CiscoASA(config-pmap-c)# flow-export event-type flow-update destination 209.165.201.10 D. CiscoASA(config-cmap)# flow-export event-type all destination 209.165.201.10 Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/monitor_nsel.html
An engineer is configuring IPsec VPN and needs an authentication protocol that is reliable and supports ACK and sequence. Which protocol accomplishes this goal? A. AES-256 B. IKEv1 C. ESP D. AES-192 Suggested Answer: C
An administrator is testing new configuration on a network device. The network device had a previously established association with the NTP server but is no longer processing time updates. What is the cause of this issue? A. The server changed its time source to stratum 1. B. The network device is sending the wrong password to the server. C. NTP authentication has been configured on the network device. D. NTP authentication has been configured on the NTP server. Suggested Answer: C
An engineer is configuring device-hardening on a router in order to prevent credentials from being seen if the router configuration was compromised. Which command should be used? A. service password-encryption B. usernameprivilege 15 password C. username password D. service password-recovery Suggested Answer: A
What is a feature of container orchestration? A. ability to deploy Kubernetes clusters in air-gapped sites B. automated daily updates C. ability to deploy Amazon ECS clusters by using the Cisco Container Platform data plane D. ability to deploy Amazon EKS clusters by using the Cisco Container Platform data plane Suggested Answer: A
During a recent security audit, a Cisco IOS router with a working IPSEC configuration using IKEv1 was flagged for using a wildcard mask with the crypto isakmp key command. The VPN peer is a SOHO router with a dynamically assigned IP address. Dynamic DNS has been configured on the SOHO router to map the dynamic IP address to the host name of vpn.sohoroutercompany.com. In addition to the command crypto isakmp key Cisc123456789 hostname vpn.sohoroutercompany.com, what other two commands are now required on the Cisco IOS router far the VPN to continue to function after the wildcard command is removed? (Choose two.) A. ip host vpn.sohoroutercompany.comB. crypto isakmp identity hostname C. Add the dynamic keyword to the existing crypto map command D. fqdn vpn.sohoroutercompany.com E. ip name-server Suggested Answer: BC
What does Cisco ISE use to collect endpoint attributes that are used in profiling? A. probes B. posture assessment C. Cisco AnyConnect Secure Mobility Client D. Cisco pxGrid Suggested Answer: A Reference: https://content.cisco.com/chapter.sjs?uri=/searchable/chapter/content/en/us/td/docs/security/ise/2-6/admin_guide/b_ise_admin_guide_26/ b_ise_admin_guide_26_chapter_010100.html.xml#:~:text=Network%20probe%20is%20a%20method,in%20the%20Cisco%20ISE%20database .
What are two functions of IKEv1 but not IKEv2? (Choose two.) A. IKEv1 conversations are initiated by the IKE_SA_INIT message. B. With IKEv1, aggressive mode negotiates faster than main mode. C. IKEv1 uses EAP for authentication. D. NAT-T is supported in IKEv1 but not in IKEv2. E. With IKEv1, when using aggressive mode, the initiator and responder identities are passed in cleartext. Suggested Answer: BE Reference: https://community.cisco.com/t5/routing/internet-key-exchange-ike-aggressive-mode/td-p/2081283
Which action controls the amount of URI text that is stored in Cisco WSA log files? A. Configure the advancedproxyconfig command with the HTTPS subcommand. B. Configure a small log-entry size. C. Configure the datasecurityconfig command. D. Configure a maximum packet size. Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_appendix_010.html
Where are individual sites specified to be black listed in Cisco Umbrella? A. security settings B. content categories C. destination lists D. application settings Suggested Answer: C To block a URL, simply enter it into a blocked destination list, or create a new blocked destination list just for URLs. To do this, navigate to Policies > Destination Lists, expand a Destination list, add a URL and then click Save. Reference: https://support.umbrella.com/hc/en-us/articles/115004518146-Umbrella-Dashboard-New-Features-Custom-blocked-URLs
What is the most commonly used protocol for network telemetry? A. NetFlow B. SNMP C. TFTP D. SMTP Suggested Answer: A
Which two Cisco ISE components enforce security policies on noncompliant endpoints by blocking network access? (Choose two.) A. Apex licensing B. TACACS+ C. profiling D. DHCP and SNMP probes E. posture agents Suggested Answer: CE
What is a difference between DMVPN and sVTI? A. DMVPN provides interoperability with other vendors, whereas sVTI does not. B. DMVPN supports static tunnel establishment, whereas sVTI does not. C. DMVPN supports dynamic tunnel establishment, whereas sVTI does not. D. DMVPN supports tunnel encryption, whereas sVTI does not. Suggested Answer: C
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains, IPs, and files, and helps to pinpoint attackers' infrastructures and predict future threat? A. Cisco Umbrella Investigate B. Cisco Stealthwatch C. Cisco pxGrid D. Cisco Stealthwatch Cloud Suggested Answer: A Reference: https://umbrella.cisco.com/products/umbrella-investigate
Which type of data does the Cisco Stealthwatch system collect and analyze from routers, switches, and firewalls? A. NTP B. SNMP C. syslog D. NetFlow Suggested Answer: D
Which threat intelligence standard contains malware hashes? A. advanced persistent threat B. open command and control C. structured threat information expression D. trusted automated exchange of indicator information Suggested Answer: C
How does Cisco Umbrella protect clients when they operate outside of the corporate network? A. by forcing DNS queries to the corporate name servers B. by modifying the registry for DNS lookups C. by using the Cisco Umbrella roaming client D. by using Active Directory group policies to enforce Cisco Umbrella DNS servers Suggested Answer: C Reference: https://www.cisco.com/c/en/us/products/security/umbrella/umbrella-roaming.html
DRAG DROP - Drag and drop the deployment models from the left onto the corresponding explanations on the right. Select and Place:Suggested Answer:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/ inline_sets_and_passive_interfaces_for_firepower_threat_defense.html#concept_835CD87FE5ED4CD9BAEE2118D588AC58
An administrator is configuring NTP on Cisco ASA via ASDM and needs to ensure that rogue NTP servers cannot insert themselves as the authoritative time source. Which two steps must be taken to accomplish this task? (Choose two.) A. Choose the interface for syncing to the NTP server. B. Specify the NTP version C. Set the NTP DNS hostname D. Set the authentication key. E. Configure the NTP stratum Suggested Answer: AD Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa98/asdm78/general/asdm-78-general-config/basic-hostname-pw.html
Which two capabilities of Integration APIs are utilized with Cisco DNA Center? (Choose two.) A. Upgrade software on switches and routers B. Third party reporting C. Connect to ITSM platforms D. Create new SSIDs on a wireless LAN controller E. Automatically deploy new virtual routers Suggested Answer: BC Reference: https://developer.cisco.com/docs/dna-center/#!cisco-dna-center-platform-overview/integration-api-westbound
What is the most common type of data exfiltration that organizations currently experience? A. encrypted SMTP B. SQL database injections C. HTTPS file upload site D. Microsoft Windows network shares Suggested Answer: D Reference: https://blogs.cisco.com/security/sensitive-data-exfiltration-and-the-insider
Which DoS attack uses fragmented packets in an attempt to crash a target machine? A. teardrop B. smurf C. LAND D. SYN flood Suggested Answer: A Reference: https://www.radware.com/security/ddos-knowledge-center/ddospedia/teardrop-attack/
DRAG DROP - Drag and drop the cryptographic algorithms for IPsec from the left onto the cryptographic processes on the right. Select and Place:Suggested Answer:
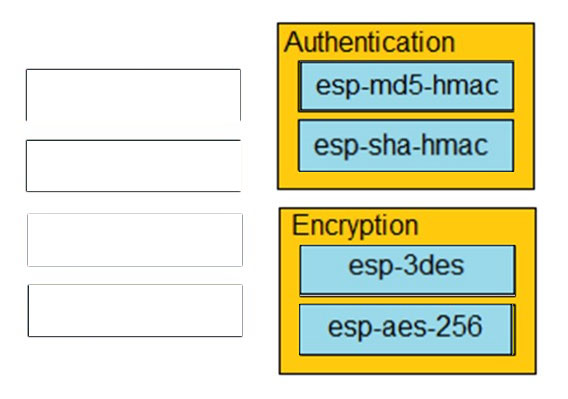
An organization has DHCP servers set up to allocate IP addresses to clients on the LAN. What must be done to ensure the LAN switches prevent malicious DHCP traffic while also distributing IP addresses to the correct endpoints? A. Configure Dynamic ARP inspection and add entries in the DHCP snooping database. B. Configure DHCP snooping and set trusted interfaces for all client connections. C. Configure Dynamic ARP inspection and antispoofing ACLs in the DHCP snooping database. D. Configure DHCP snooping and set a trusted interface for the DHCP server. Suggested Answer: B Reference: https://www.cisco.com/en/US/docs/switches/lan/catalyst3850/software/release/3.2_0_se/multibook/configuration_guide/ b_consolidated_config_guide_3850_chapter_0110101.html
DoS attacks are categorized as what? A. flood attacks B. virus attacks C. trojan attacks D. phishing attacks Suggested Answer: A
What is the process of performing automated static and dynamic analysis of files in an isolated environment against preloaded behavioral indicators for threat analysis? A. advanced sandboxing B. adaptive scanning C. deep visibility scan D. point-in-time checks Suggested Answer: A Reference: https://www.cisco.com/c/en_in/products/security/advanced-malware-protection/index.html
What are two benefits of Flexible NetFlow records? (Choose two.) A. They provide accounting and billing enhancements. B. They allow the user to configure flow information to perform customized traffic identification. C. They provide monitoring of a wider range of IP packet information from Layer2 to 4. D. They provide attack prevention by dropping the traffic. E. They converge multiple accounting technologies into one accounting mechanism. Suggested Answer: BE Reference: https://www.cisco.com/c/en/us/products/ios-nx-os-software/flexible-netflow/index.html
An engineer needs to configure a Cisco Secure Email Gateway (SEG) to prompt users to enter multiple forms of identification before gaining access to the SEG. The SEG must also join a cluster using the preshared key of cisc421555367. What steps must be taken to support this? A. Enable two-factor authentication through a RADIUS server, and then join the cluster via the SEG GUI. B. Enable two-factor authentication through a TACACS+ server, and then join the cluster via the SEG CLI. C. Enable two-factor authentication through a RADIUS server, and then join the cluster via the SEG CLI D. Enable two-factor authentication through a TACACS+ server, and then join the cluster via the SEG GUI. Suggested Answer: C Reference: https://www.cisco.com/c/en/us/td/docs/security/esa/esa11-0/user_guide_fs/b_ESA_Admin_Guide_11_0/b_ESA_Admin_Guide_chapter_00.pdf
Which characteristic is unique to a Cisco WSAv as compared to a physical appliance? A. requires an additional license B. performs transparent redirection C. supports SSL decryption D. supports VMware vMotion on VMware ESXi Suggested Answer: D
What are two workload security models? (Choose two.) A. SaaS B. PaaS C. off-premises D. on-premises E. IaaS Suggested Answer: CD
An engineer is configuring Dropbox integration with Cisco Cloudlock. Which action must be taken before granting API access in the Dropbox admin console? A. Add Dropbox to the Cloudlock Authentication and API section in the Cloudlock portal. B. Add Cloudlock to the Dropbox admin portal. C. Send an API request to Cloudlock from Dropbox admin portal. D. Authorize Dropbox within the Platform settings in the Cloudlock portal. Suggested Answer: D
Which CoA response code is sent if an authorization state is changed successfully on a Cisco IOS device? A. CoA-NAK B. CoA-NCL C. CoA-MAB D. CoA-ACK Suggested Answer: D Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_aaa/configuration/15-sy/sec-usr-aaa-15-sy-book/sec-rad-coa.html
DRAG DROP - Drag and drop the security solutions from the left onto the benefits they provide on the right. Select and Place:Suggested Answer:

What is a benefit of using GET VPN over FlexVPN within a VPN deployment? A. GET VPN supports Remote Access VPNs B. GET VPN uses multiple security associations for connections C. GET VPN natively supports MPLS and private IP networks. D. GET VPN interoperates with non-Cisco devices. Suggested Answer: C
Email security has become a high-priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (`"10.00 to `"6.00) on the Cisco ESA. Which action will the system perform to desirable any links in messages that match the filter? A. Defang B. FilterAction C. Quarantine D. ScreenAction Suggested Answer: C Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/esa-content-filters.pdf
Which cloud service offering allows customers to access a web application that is being hosted, managed, and maintained by a cloud service provider? A. IaC B. IaaS C. PaaS D. SaaS Suggested Answer: D Reference: https://www.ibm.com/cloud/learn/iaas-paas-saas
What is the recommendation in a zero-trust model before granting access to corporate applications and resources? A. to disconnect from the network when inactive B. to use multifactor authentication C. to use a wired network, not wireless D. to use strong passwords Suggested Answer: A
Which open source tool does Cisco use to create graphical visualizations of network telemetry on Cisco IOS XE devices? A. InfluxDB B. SNMP C. Grafana D. Splunk Suggested Answer: C Reference: https://blogs.cisco.com/developer/getting-started-with-model-driven-telemetry
Which CLI command is used to enable URL filtering support for shortened URLs on the Cisco ESA? A. websecurityadvancedconfig B. webadvancedconfig C. websecurityconfig D. outbreakconfig Suggested Answer: A Reference: https://www.cisco.com/c/en/us/support/docs/security/email-security-appliance/118775-technote-esa-00.html
What is a feature of NetFlow Secure Event Logging? A. It exports only records that indicate significant events in a flow. B. It supports v5 and v8 templates. C. It delivers data records to NSEL collectors through NetFlow over TCP only. D. It filters NSEL events based on the traffic and event type through RSVP. Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa91/asdm71/general/asdm_71_general_config/monitor_nsel.pdf
A network engineer entered the snmp-server user asmith myv7 auth sha cisco priv aes 256 cisc0123456789 command and needs to send SNMP information to a host at 10.255.255.1. Which command achieves this goal? A. snmp-server host inside 10.255.255.1 version 3 myv7 B. snmp-server host inside 10.255.255.1 snmpv3 myv7 C. snmp-server host inside 10.255.255.1 version 3 asmith D. snmp-server host inside 10.255.255.1 snmpv3 asmith Suggested Answer: D
Which standard is used to automate exchanging cyber threat information? A. MITRE B. TAXII C. IoC D. STIX Suggested Answer: B
Which endpoint protection and detection feature performs correlation of telemetry, files, and intrusion events that are flagged as possible active breaches? A. elastic search B. file trajectory C. indication of compromise D. retrospective detection Suggested Answer: C Reference: https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/advanced-malware-protection/solution-overview-c22-734228.html
When network telemetry is implemented, what is important to be enabled across all network infrastructure devices to correlate different sources? A. CDP B. syslog C. NTP D. DNS Suggested Answer: C
Which Cisco ASA deployment model is used to filter traffic between hosts in the same IP subnet using higher-level protocols without readdressing the network? A. multiple context mode B. single context mode C. routed mode D. transparent mode Suggested Answer: D Reference: https://grumpy-networkers-journal.readthedocs.io/en/latest/VENDOR/CISCO/FIREWALL/ASA/TRANSPARENTFW.html
Which RADIUS feature provides a mechanism to change the AAA attributes of a session after it is authenticated? A. Accounting B. Authorization C. Authentication D. CoA Suggested Answer: D
When NetFlow is applied to an interface, which component creates the flow monitor cache that is used to collect traffic based on the key and nonkey fields in the configured record? A. flow exporter B. records C. flow sampler D. flow monitor Suggested Answer: A
Which encryption algorithm provides highly secure VPN communications? A. AES 256 B. AES 128 C. 3DES D. DES Suggested Answer: A
What is the term for when an endpoint is associated to a provisioning WLAN that is shared with guest access, and the same guest portal is used as the BYOD portal? A. single-SSID BYOD B. dual-SSID BYOD C. streamlined access D. multichannel GUI Suggested Answer: B
DRAG DROP - Drag and drop the exploits from the left onto the type of security vulnerability on the right. Select and Place:Suggested Answer:
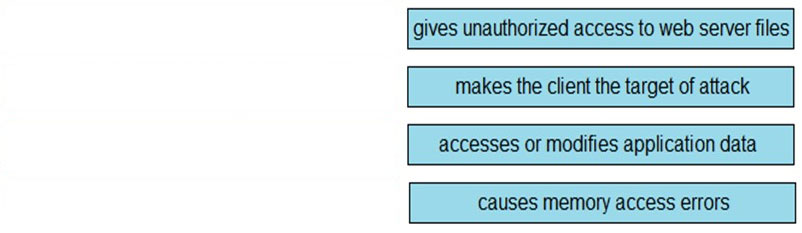
What is the function of the crypto isakmp key cisc123456789 address 192.168.50.1 255.255.255.255 command when establishing an IPsec VPN tunnel? A. It configures the pre-shared authentication key for host 192.168.50.1. B. It prevents 192.168.50.1 from connecting to the VPN server. C. It configures the local address for the VPN server 192.168.50.1. D. It defines the data destined to 192.168.50.1 is going to be encrypted. Suggested Answer: A
Which Cisco ASA Platform mode disables the threat detection features except for Advanced Threat Statistics? A. cluster B. multiple context C. routed D. transparent Suggested Answer: D
An engineer is configuring web filtering for a network using Cisco Umbrella Secure Internet Gateway. The requirement is that all traffic needs to be filtered. Using the SSL decryption feature, which type of certificate should be presented to the end-user to accomplish this goal? A. SubCA B. organization owned root C. self-signed D. third-party Suggested Answer: B
Which solution stops unauthorized access to the system if a user's password is compromised? A. MFA B. AMP C. VPN D. SSL Suggested Answer: A
An engineer needs to configure an access control policy rule to always send traffic for inspection without using the default action. Which action should be configured for this rule? A. monitor B. trust C. allow D. block Suggested Answer: A
Which benefit does DMVPN provide over GETVPN? A. DMVPN can be used over the public Internet, and GETVPN requires a private network. B. DMVPN is a tunnel-less VPN, and GETVPN is tunnel-based. C. DMVPN supports non-IP protocols, and GETVPN supports only IP protocols. D. DMVPN supports QoS, multicast, and routing, and GETVPN supports only QoS. Suggested Answer: A
Refer to the exhibit. Which configuration item makes it possible to have the AAA session on the network? A. aaa authentication enable default enable B. aaa authorization network default group ise C. aaa authentication login console ise D. aaa authorization exec default ise Suggested Answer: A
Which method of attack is used by a hacker to send malicious code through a web application to an unsuspecting user to request that the victim's web browser executes the code? A. cross-site scripting B. browser WGET C. buffer overflow D. SQL injection Suggested Answer: A Reference: https://owasp.org/www-community/attacks/xss/
Which two solutions help combat social engineering and phishing at the endpoint level? (Choose two.) A. Cisco ISE B. Cisco Duo Security C. Cisco DNA Center D. Cisco Umbrella E. Cisco TrustSec Suggested Answer: DE
An engineer is implementing Cisco CES in an existing Microsoft Office 365 environment and must route inbound email to Cisco CES addresses. Which DNS record must be modified to accomplish this task? A. CNAME B. DKIM C. MX D. SPF Suggested Answer: C Reference: https://www.cisco.com/c/en/us/support/docs/security/cloud-email-security/214812-configuring-office-365-microsoft-with.html
A large organization wants to deploy a security appliance in the public cloud to form a site-to-site VPN and link the public cloud environment to the private cloud in the headquarters data center. Which Cisco security appliance meets these requirements? A. Cisco Stealthwatch Cloud B. Cisco WSAv C. Cisco Cloud Orchestrator D. Cisco ASAv Suggested Answer: D
Refer to the exhibit. What are two indications of the Cisco Firepower Services Module configuration? (Choose two.) A. The module is operating in IDS mode. B. Traffic is blocked if the module fails. C. The module fails to receive redirected traffic. D. The module is operating in IPS mode. E. Traffic continues to flow if the module fails. Suggested Answer: DE
Which two parameters are used to prevent a data breach in the cloud? (Choose two.) A. DLP solutions B. complex cloud-based web proxies C. strong user authentication D. antispoofing programs E. encryption Suggested Answer: AC
What is the concept of continuous integration/continuous delivery pipelining? A. The project code is centrally maintained, and each code change should trigger an automated build and test sequence. B. The project is split into time-limited cycles, and focuses on pair programming for continuous code review. C. The project is split into several phases where one phase cannot start before the previous phase finishes successfully. D. Each project phase is independent from other phases to maintain adaptiveness and continual improvement. Suggested Answer: A
Which security solution uses NetFlow to provide visibility across the network, data center, branch offices, and cloud? A. Cisco Stealthwatch B. Cisco Encrypted Traffic Analytics C. Cisco Umbrella D. Cisco CTA Suggested Answer: A
Which two functions does the Cisco Advanced Phishing Protection solution perform in trying to protect from phishing attacks? (Choose two.) A. uses a static algorithm to determine malicious B. determines if the email messages are malicious C. provides a defense for on-premises email deployments D. blocks malicious websites and adds them to a block list E. does a real-time user web browsing behavior analysis Suggested Answer: BE
Which technology provides the benefit of Layer 3 through Layer 7 innovative deep packet inspection, enabling the platform to identify and output various applications within the network traffic flows? A. Cisco ASAv B. Account on Resolution C. Cisco NBAR2 D. Cisco Prime Infrastructure Suggested Answer: C
Which Cisco DNA Center Intent API action is used to retrieve the number of devices known to a DNA Center? A. GET https://fqdnOrlPofDnaCenterPlatform/dna/intent/api/v1/network-device/count B. GET https://fqdnOrlPofDnaCenterPlatform/dna/intent/api/v1/network-device?parameter1=value¶meter2=vale&... C. GET https://fqdnOrlPofDnaCenterPlatform/dna/intent/api/v1/network-device/startIndex/recordsToReturn D. GET https://fqdnOrlPofDnaCenterPlatform/dna/intent/api/v1/network-device Suggested Answer: A
Which function is performed by certificate authorities but is a limitation of registration authorities? A. CRL publishing B. certificate re-enrollment C. verifying user identity D. accepts enrollment requests Suggested Answer: C
A hacker initiated a social engineering attack and stole username and passwords of some users within a company. Which product should be used as a solution to this problem? A. Cisco Duo B. Cisco NGFW C. Cisco AnyConnect D. Cisco AMP for Endpoints Suggested Answer: A
An organization must add new firewalls to its infrastructure and wants to use Cisco ASA or Cisco FTD. The chosen firewalls must provide methods of blocking traffic that include offering the user the option to bypass the block for certain sites after displaying a warning page and to reset the connection. Which solution should the organization choose? A. Cisco FTD because it enables interactive blocking and blocking with reset natively, whereas Cisco ASA does not. B. Cisco ASA because it has an additional module that can be installed to provide multiple blocking capabilities, whereas Cisco FTD does not. C. Cisco ASA because it allows for interactive blocking and blocking with reset to be configured via the GUI, whereas FTD does not. D. Cisco FTD because it supports system rate level traffic blocking, whereas Cisco ASA does not. Suggested Answer: A
An email administrator is setting up a new Cisco ESA. The administrator wants to enable the blocking of greymail for the end user. Which feature must the administrator enable first? A. Intelligent Multi-Scan B. Anti-Virus Filtering C. IP Reputation Filtering D. File Analysis Suggested Answer: A
Why is it important for the organization to have an endpoint patching strategy? A. so the organization can identify endpoint vulnerabilities B. so the internal PSIRT organization is aware of the latest bugs C. so the network administrator is notified when an existing bug is encountered D. so the latest security fixes are installed on the endpoints Suggested Answer: D
Which technology enables integration between Cisco ISE and other platforms to gather and share network and vulnerability data and SIEM and location information? A. Cisco Talos B. SNMP C. pxGrid D. NetFlow Suggested Answer: C
An administrator needs to configure the Cisco ASA via ASDM such that the network management system can actively monitor the host using SNMPv3. Which two tasks must be performed for this configuration? (Choose two.) A. Add an SNMP USM entry. B. Specify an SNMP user group. C. Add an SNMP host access entry. D. Specify the SNMP manager and UDP port. E. Specify a community string. Suggested Answer: AB
How does a WCCP-configured router identify if the Cisco WSA is functional? A. If an ICMP ping fails three consecutive times between a router and the WSA, traffic is no longer transmitted to the router. B. If an ICMP ping fails three consecutive times between a router and the WSA, traffic is no longer transmitted to the WSA. C. The WSA-sends a Here-I-Am message every 10 seconds, and the router acknowledges with an I-See-You message. D. The router sends a Here-I-Am message every 10 seconds, and the WSA acknowledges with an I-See-You message. Suggested Answer: D
A network engineer must migrate a Cisco WSA virtual appliance from one physical host to another physical host by using VMware vMotion. What is a requirement for both physical hosts? A. The hosts must run Cisco AsyncOS 10.0 or greater. B. The hosts must run different versions of Cisco AsyncOS. C. The hosts must have access to the same defined network. D. The hosts must use a different datastore than the virtual appliance. Suggested Answer: C
An engineer must modify a policy to block specific addresses using Cisco Umbrella. The policy is created already and is actively used by devices, using many of the default policy elements. What else must be done to accomplish this task? A. Create a destination list for addresses to be allowed or blocked B. Use content categories to block or allow specific addresses C. Add the specified addresses to the identities list and create a block action D. Modify the application settings to allow only applications to connect to required addresses Suggested Answer: C
What must be enabled to secure SaaS-based applications? A. two-factor authentication B. end-to-end encryption C. application security gateway D. modular policy framework Suggested Answer: A
An engineer configures new features within the Cisco Umbrella dashboard and wants to identify and proxy traffic that is categorized as risky domains and may contain safe and malicious content. Which action accomplishes these objectives? A. Upload the threat intelligence database to Cisco Umbrella for the most current information on reputations and to have the destination lists block them B. Configure URL filtering within Cisco Umbrella to track the URLs and proxy the requests for those categories and below C. Create a new site within Cisco Umbrella to block requests from those categories so they can be sent to the proxy device D. Configure intelligent proxy within Cisco Umbrella to intercept and proxy the requests for only those categories Suggested Answer: D
An engineer is configuring Cisco Umbrella and has an identity that references two different policies. Which action ensures that the policy that the identity must use takes precedence over the second one? A. Place the policy with the most-specific configuration last in the policy order B. Configure the default policy to redirect the requests to the correct policy C. Make the correct policy first in the policy order D. Configure only the policy with the most recently changed timestamp Suggested Answer: C Reference: https://docs.umbrella.com/deployment-umbrella/docs/policy-precedence
A Cisco ISE engineer configures Central Web Authentication (CWA) for wireless guest access and must have the guest endpoints redirect to the guest portal for authentication and authorization. While testing the policy, the engineer notices that the device is not redirected and instead gets full guest access. What must be done for the redirect to work? A. Tag the guest portal in the CWA part of the Common Tasks section of the authorization profile for the authorization policy line that the unauthenticated devices hit. B. Create an advanced attribute setting of Cisco:cisco-gateway-id=guest within the authorization profile for the authorization policy line that the unauthenticated devices hit. C. Add the DACL name for the Airespace ACL configured on the WLC in the Common Tasks section of the authorization profile for the authorization policy line that the unauthenticated devices hit. D. Use the track movement option within the authorization profile for the authorization policy line that the unauthenticated devices hit. Suggested Answer: B
What is the intent of a basic SYN flood attack? A. to solicit DNS responses B. to flush the register stack to re-initiate the buffers C. to exceed the threshold limit of the connection queue D. to cause the buffer to overflow Suggested Answer: C Reference: https://www.cloudflare.com/en-in/learning/ddos/syn-flood-ddos-attack/
What is an advantage of network telemetry over SNMP pulls? A. security B. scalability C. accuracy D. encapsulation Suggested Answer: C
Which security solution protects users leveraging DNS-layer security? A. Cisco ISE B. Cisco Umbrella C. Cisco ASA D. Cisco FTD Suggested Answer: B
What are two functions of TAXII in threat intelligence sharing? (Choose two.) A. allows users to describe threat motivations and abilities B. determines how threat intelligence information is relayed C. determines the "what" of threat intelligence D. exchanges trusted anomaly intelligence information E. supports STIX information Suggested Answer: BD
What are two functionalities of SDN Northbound APIs? (Choose two.) A. OpenFlow is a standardized northbound API protocol B. Northbound APIs form the interface between the SDN controller and business applications C. Northbound APIs provide a programmable interface for applications to dynamically configure the network D. Northbound APIs form the interface between the SDN controller and the network switches or routers E. Northbound APIs use the NETCONF protocol to communicate with applications. Suggested Answer: BE
What is the result of the ACME-Router(config)#login block-for 100 attempts 4 within 60 command on a Cisco IOS router? A. If four failures occur in 60 seconds, the router goes to quiet mode for 100 seconds B. After four unsuccessful log in attempts the line is blocked for 100 seconds and only permit IP addresses are permitted in ACL 60 C. After four unsuccessful log in attempts the line is blocked for 60 seconds and only permit IP addresses are permitted in ACL 100 D. If four log in attempts fail in 100 seconds, wait for 60 seconds to next log in prompt Suggested Answer: A Reference: https://websistent.com/cisco-account-lockout-using-login-block-for/
What is a benefit of using a multifactor authentication strategy? A. It provides an easy, single sign-on experience against multiple applications B. It provides secure remote access for applications C. It protects data by enabling the use of a second validation of identity D. It provides visibility into devices to establish device trust Suggested Answer: C
Which endpoint solution protects a user from a phishing attack? A. Cisco AnyConnect with Network Access Manager module B. Cisco AnyConnect with Umbrella Roaming Security module C. Cisco Identity Services Engine D. Cisco AnyConnect with ISE Posture module Suggested Answer: B
Which role is a default guest type in Cisco ISE? A. Contractor B. Full-Time C. Monthly D. Yearly Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/1-4-1/admin_guide/b_ise_admin_guide_141/b_ise_admin_guide_141_chapter_01110.html
An engineer is trying to decide between using L2TP or GRE over IPsec for their site-to-site VPN implementation. What must be understood before choosing a solution? A. L2TP is an IP packet encapsulation protocol, and GRE over IPsec is a tunneling protocol B. GRE over IPsec cannot be used as a standalone protocol, and L2TP can C. L2TP uses TCP port 47 and GRE over IPsec uses UDP port 1701 D. GRE over IPsec adds its own header, and L2TP does not Suggested Answer: D
An administrator enables Cisco Threat Intelligence Director on a Cisco FMC. Which process uses STIX and allows uploads and downloads of block lists? A. editing B. sharing C. authoring D. consumption Suggested Answer: B
Why is it important to have a patching strategy for endpoints? A. so that patching strategies can assist with disabling nonsecure protocols in applications B. so that known vulnerabilities are targeted and having a regular patch cycle reduces risks C. so that functionality is increased on a faster scale when it is used D. to take advantage of new features released with patches Suggested Answer: B
Which two methods must be used to add switches into the fabric so that administrators can control how switches are added into DCNM for private cloud management? (Choose two.) A. Cisco Prime Infrastructure B. CDP AutoDiscovery C. Seed IP D. PowerOn Auto Provisioning E. Cisco Cloud Director Suggested Answer: BD Reference: https://www.cisco.com/c/en/us/td/docs/dcn/dcnm/1151/configuration/lanfabric/cisco-dcnm-lanfabric-configuration-guide-1151/control.html
Refer to the exhibit. All servers are in the same VLAN/Subnet DNS Server-1 and DNS Server-2 must communicate with each other and all servers must communicate with default gateway multilayer switch. Which type of private VLAN ports should be configured to prevent communication between DNS servers and the file server? A. Configure GigabitEthernet0/1 as community port, GigabitEthernet0/2 as promiscuous port, GigabitEthernet0/3 and GigabrtEthernet0/4 as isolated ports B. Configure GigabitEthernet0/1 as community port, GigabitEthernet0/2 as isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as promiscuous ports C. Configure GigabitEthernet0/1 as promiscuous port, GigabitEthernet0/2 as community port, and GigabitEthernet0/3 and GigabitEthernet0/4 as isolated ports D. Configure GigabitEthernet0/1 as promiscuous port, GigabitEthernet0/2 as isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as community ports Suggested Answer: B
Which system performs compliance checks and remote wiping? A. MDM B. ISE C. AMP D. OTP Suggested Answer: A
An engineer is configuring Cisco WSA and needs to enable a separated email transfer flow from the Internet and from the LAN. Which deployment mode must be used to accomplish this goal? A. single interface B. multi-context C. transparent D. two-interface Suggested Answer: D
A network engineer is tasked with configuring a Cisco ISE server to implement external authentication against Active Directory. What must be considered about the authentication requirements? (Choose two.) A. RADIUS communication must be permitted between the ISE server and the domain controller. B. The ISE account must be a domain administrator in Active Directory to perform JOIN operations. C. Active Directory only supports user authentication by using MSCHAPv2. D. LDAP communication must be permitted between the ISE server and the domain controller. E. Active Directory supports user and machine authentication by using MSCHAPv2. Suggested Answer: BC
Which configuration method provides the options to prevent physical and virtual endpoint devices that are in the same base EPG or uSeg from being able to communicate with each other with Vmware VDS or Microsoft vSwitch? A. inter-EPG isolation B. inter-VLAN security C. intra-EPG isolation D. placement in separate EPGs Suggested Answer: C Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/aci/apic/sw/4-x/virtualization/Cisco-ACI-Virtualization-Guide-42x/Cisco-ACI-Virtualization- Guide-421_chapter_0101.pdf
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.) A. Create an LDAP authentication realm and disable transparent user identification. B. Create NTLM or Kerberos authentication realm and enable transparent user identification. C. Deploy a separate Active Directory agent such as Cisco Context Directory Agent. D. The eDirectory client must be installed on each client workstation. E. Deploy a separate eDirectory server; the client IP address is recorded in this server. Suggested Answer: AC
Which baseline form of telemetry is recommended for network infrastructure devices? A. SDNS B. NetFlow C. passive taps D. SNMP Suggested Answer: D
In which scenario is endpoint-based security the solution? A. inspecting encrypted traffic B. device profiling and authorization C. performing signature-based application control D. inspecting a password-protected archive Suggested Answer: C
Refer to the exhibit. What is the result of the Python script? A. It uses the POST HTTP method to obtain a username and password to be used for authentication. B. It uses the POST HTTP method to obtain a token to be used for authentication. C. It uses the GET HTTP method to obtain a token to be used for authentication. D. It uses the GET HTTP method to obtain a username and password to be used for authentication Suggested Answer: B
Why is it important to patch endpoints consistently? A. Patching reduces the attack surface of the infrastructure. B. Patching helps to mitigate vulnerabilities. C. Patching is required per the vendor contract. D. Patching allows for creating a honeypot. Suggested Answer: B
Which two parameters are used for device compliance checks? (Choose two.) A. endpoint protection software version B. Windows registry values C. DHCP snooping checks D. DNS integrity checks E. device operating system version Suggested Answer: AB
Which Cisco cloud security software centrally manages policies on multiple platforms such as Cisco ASA, Cisco Firepower, Cisco Meraki, and AWS? A. Cisco Defense Orchestrator B. Cisco Configuration Professional C. Cisco Secureworks D. Cisco DNAC Suggested Answer: A
Which Cisco security solution determines if an endpoint has the latest OS updates and patches installed on the system? A. Cisco Endpoint Security Analytics B. Cisco AMP for Endpoints C. Endpoint Compliance Scanner D. Security Posture Assessment Service Suggested Answer: D
Which open standard creates a framework for sharing threat intelligence in a machine-digestible format? A. OpenIOC B. OpenC2 C. CybOX D. STIX Suggested Answer: A
What is a difference between Cisco AMP for Endpoints and Cisco Umbrella? A. Cisco AMP for Endpoints is a cloud-based service, and Cisco Umbrella is not B. Cisco AMP for Endpoints automatically researches indicators of compromise and confirms threats and Cisco Umbrella does not C. Cisco AMP for Endpoints prevents, detects, and responds to attacks before damage can be done, and Cisco Umbrella provides the first line of defense against Internet threats D. Cisco AMP for Endpoints prevents connections to malicious destinations, and Cisco Umbrella works at the file level to prevent the initial execution of malware Suggested Answer: C
What are two functionalities of northbound and southbound APIs within Cisco SDN architecture? (Choose two.) A. Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE B. Southbound APIs utilize CLI, SNMP, and RESTCONF C. Southbound APIs are used to define how SDN controllers integrate with applications D. Northbound interfaces utilize OpenFlow and OpFlex to integrate with network devices E. Southbound interfaces utilize device configurations such as VLANs and IP addresses Suggested Answer: AB Reference: https://www.cisco.com/c/dam/global/sr_rs/training-events/2016/cisco-day-2016/pdf/APIC-EM_Vedran_Hafner.pdf
Refer to the exhibit. What is the function of the Python script code snippet for the Cisco ASA REST API? A. changes the hostname of the Cisco ASA B. adds a global rule into policies C. deletes a global rule from policies D. obtains the saved configuration of the Cisco ASA firewall Suggested Answer: B
DRAG DROP - Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right. Select and Place:Suggested Answer:
Reference: https://www.cisco.com/c/dam/global/en_ca/assets/pdf/cisco_asa_with_firepower_services_ds.pdf
What are two functions of secret key cryptography? (Choose two.) A. utilization of less memory B. utilization of large prime number iterations C. utilization of different keys for encryption and decryption D. key selection without integer factorization E. provides the capability to only know the key on one side Suggested Answer: DE
Refer to the exhibit. When creating an access rule for URL filtering a network engineer adds certain categories and individual URLs to block. What is the result of the configuration? A. Only URLs for botnets with a reputation score of 3 will be allowed while the rest will be blocked. B. Only URLs for botnets with reputation scores of 1-3 will be blocked. C. Only URLs for botnets with reputation scores of 3-5 will be blocked. D. Only URLs for botnets with a reputation score of 3 will be blocked. Suggested Answer: B
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access? A. Cisco Container Controller B. Cisco Cloud Platform C. Cisco Container Platform D. Cisco Content Platform Suggested Answer: C
What are two things to consider when using PAC files with the Cisco WSA? (Choose two.) A. If the WSA host port is changed, the default port redirects web traffic to the correct port automatically. B. PAC files use if-else statements to determine whether to use a proxy or a direct connection for traffic between the PC and the host. C. The WSA hosts PAC files on port 9001 by default. D. The WSA hosts PAC files on port 6001 by default. E. By default, they direct traffic through a proxy when the PC and the host are on the same subnet. Suggested Answer: BC
Which IETF attribute is supported for the RADIUS CoA feature? A. 24 State B. 30 Calling-Station-ID C. 42 Acct-Session-ID D. 81 Message-Authenticator Suggested Answer: A
When a transparent authentication fails on the Web Security Appliance, which type of access does the end user get? A. guest B. limited Internet C. blocked D. full Internet Suggested Answer: C
What are two ways that Cisco Container Platform provides value to customers who utilize cloud service providers? (Choose two.) A. Allows developers to create code once and deploy to multiple clouds B. helps maintain source code for cloud deployments C. manages Docker containers D. manages Kubernetes clusters E. Creates complex tasks for managing code Suggested Answer: AE
DRAG DROP - Drag and drop the posture assessment flow actions from the left into a sequence on the right. Select and Place:Suggested Answer:
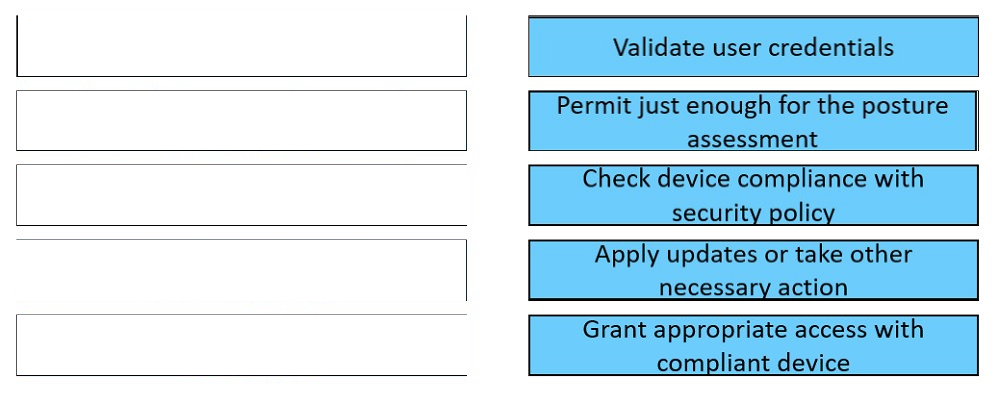
Refer to the exhibit. What does the API key do while working with https://api.amp.cisco.com/v1/computers? A. displays client ID B. HTTP authorization C. Imports requests D. HTTP authentication Suggested Answer: C
Which statement describes a serverless application? A. The application delivery controller in front of the server farm designates on which server the application runs each time. B. The application runs from an ephemeral, event-triggered, and stateless container that is fully managed by a cloud provider. C. The application is installed on network equipment and not on physical servers. D. The application runs from a containerized environment that is managed by Kubernetes or Docker Swarm. Suggested Answer: B
What is a description of microsegmentation? A. Environments deploy a container orchestration platform, such as Kubernetes, to manage the application delivery. B. Environments apply a zero-trust model and specify how applications on different servers or containers can communicate. C. Environments deploy centrally managed host-based firewall rules on each server or container. D. Environments implement private VLAN segmentation to group servers with similar applications. Suggested Answer: B
Which Cisco WSA feature supports access control using URL categories? A. transparent user identification B. SOCKS proxy services C. web usage controls D. user session restrictions Suggested Answer: A
Which technology limits communication between nodes on the same network segment to individual applications? A. serverless infrastructure B. microsegmentation C. SaaS deployment D. machine-to-machine firewalling Suggested Answer: B
An engineer enabled SSL decryption for Cisco Umbrella intelligent proxy and needs to ensure that traffic is inspected without alerting end-users. Which action accomplishes this goal? A. Restrict access to only websites with trusted third-party signed certificates. B. Modify the user's browser settings to suppress errors from Cisco Umbrella. C. Upload the organization root CA to Cisco Umbrella. D. Install the Cisco Umbrella root CA onto the user's device. Suggested Answer: D
What is the purpose of joining Cisco WSAs to an appliance group? A. All WSAs in the group can view file analysis results. B. The group supports improved redundancy C. It supports cluster operations to expedite the malware analysis process. D. It simplifies the task of patching multiple appliances. Suggested Answer: B
Why should organizations migrate to an MFA strategy for authentication? A. Single methods of authentication can be compromised more easily than MFA. B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily. C. MFA methods of authentication are never compromised. D. MFA does not require any piece of evidence for an authentication mechanism. Suggested Answer: A
Which technology should be used to help prevent an attacker from stealing usernames and passwords of users within an organization? A. RADIUS-based REAP B. fingerprinting C. Dynamic ARP Inspection D. multifactor authentication Suggested Answer: D
Which type of attack is MFA an effective deterrent for? A. ping of death B. phishing C. teardrop D. syn flood Suggested Answer: B
Which solution for remote workers enables protection, detection, and response on the endpoint against known and unknown threats? A. Cisco AMP for Endpoints B. Cisco AnyConnect C. Cisco Umbrella D. Cisco Duo Suggested Answer: A
Which two actions does the Cisco Identity Services Engine posture module provide that ensures endpoint security? (Choose two.) A. Assignments to endpoint groups are made dynamically, based on endpoint attributes. B. Endpoint supplicant configuration is deployed. C. A centralized management solution is deployed. D. Patch management remediation is performed. E. The latest antivirus updates are applied before access is allowed. Suggested Answer: AD
What is an advantage of the Cisco Umbrella roaming client? A. the ability to see all traffic without requiring TLS decryption B. visibility into IP-based threats by tunneling suspicious IP connections C. the ability to dynamically categorize traffic to previously uncategorized sites D. visibility into traffic that is destined to sites within the office environment Suggested Answer: C
Which Cisco platform provides an agentless solution to provide visibility across the network including encrypted traffic analytics to detect malware in encrypted traffic without the need for decryption? A. Cisco Advanced Malware Protection B. Cisco Stealthwatch C. Cisco Identity Services Engine D. Cisco AnyConnect Suggested Answer: B
Which two Cisco ISE components must be configured for BYOD? (Choose two.) A. local WebAuth B. central WebAuth C. null WebAuth D. guest E. dual Suggested Answer: AD
Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from Cisco and other vendors to share data and interoperate with each other? A. Platform Exchange Grid B. Multifactor Platform Integration C. Firepower Threat Defense D. Advanced Malware Protection Suggested Answer: A Reference: https://www.cisco.com/c/en/us/products/security/pxgrid.html
Which compliance status is shown when a configured posture policy requirement is not met? A. authorized B. compliant C. unknown D. noncompliant Suggested Answer: D
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements? A. Cisco Stealthwatch B. Cisco Tetration C. Cisco AMP D. Cisco Umbrella Suggested Answer: B
An organization has a Cisco Stealthwatch Cloud deployment in their environment. Cloud logging is working as expected, but logs are not being received from the on-premise network. What action will resolve this issue? A. Deploy a Cisco FTD sensor to send events to Cisco Stealthwatch Cloud. B. Deploy a Cisco Stealthwatch Cloud sensor on the network to send data to Cisco Stealthwatch Cloud. C. Configure security appliances to send syslogs to Cisco Stealthwatch Cloud. D. Configure security appliances to send NetFlow to Cisco Stealthwatch Cloud. Suggested Answer: B
A network engineer has been tasked with adding a new medical device to the network. Cisco ISE is being used as the NAC server, and the new device does not have a supplicant available. What must be done in order to securely connect this device to the network? A. Use 802.1X with posture assessment. B. Use MAB with profiling. C. Use 802.1X with profiling. D. Use MAB with posture assessment. Suggested Answer: B
Drag and drop the solutions from the left onto the solution's benefits on the right. Select and Place:Suggested Answer:
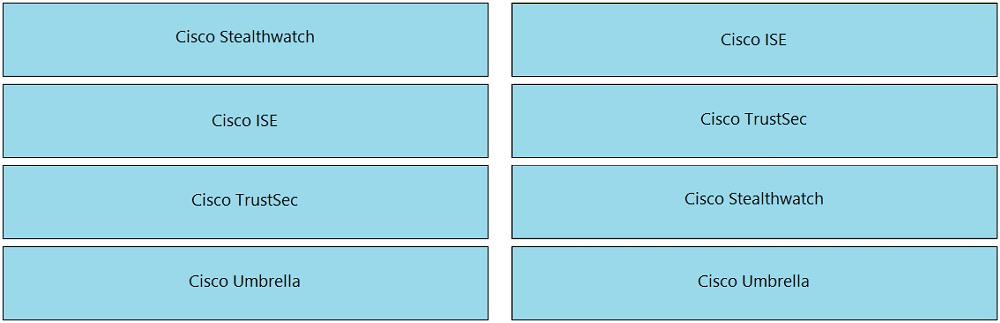
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this requirement, using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor? A. Deploy a Cisco FTD sensor to send network events to Cisco Stealthwatch Cloud. B. Configure a Cisco FMC to send syslogs to Cisco Stealthwatch Cloud. C. Deploy the Cisco Stealthwatch Cloud PNM sensor that sends data to Cisco Stealthwatch Cloud. D. Configure a Cisco FMC to send NetFlow to Cisco Stealthwatch Cloud. Suggested Answer: C
An organization wants to provide visibility and to identify active threats in its network using a VM. The organization wants to extract metadata from network packet flow while ensuring that payloads are not retained or transferred outside the network. Which solution meets these requirements? A. Cisco Umbrella Cloud B. Cisco Stealthwatch Cloud PNM C. Cisco Stealthwatch Cloud PCM D. Cisco Umbrella On-Premises Suggested Answer: B
What is a benefit of performing device compliance? A. providing multi-factor authentication B. verification of the latest OS patches C. providing attribute-driven policies D. device classification and authorization Suggested Answer: B
Which type of DNS abuse exchanges data between two computers even when there is no direct connection? A. malware installation B. network footprinting C. command-and-control communication D. data exfiltration Suggested Answer: D
How is data sent out to the attacker during a DNS tunneling attack? A. as part of the domain name B. as part of the UDP/53 packet payload C. as part of the TCP/53 packet header D. as part of the DNS response packet Suggested Answer: A Reference: https://www.infoblox.com/glossary/dns-tunneling/
Refer to the exhibit. A Cisco ISE administrator adds a new switch to an 802. 1X deployment and has difficulty with some endpoints gaining access. Most PCs and IP phones can connect and authenticate using their machine certificate credentials; however, printers and video cameras cannot. Based on the interface configuration provided, what must be done to get these devices onto the network using Cisco ISE for authentication and authorization while maintaining security controls? A. Configure authentication event fail retry 2 action authorize vlan 41 on the interface. B. Add mab to the interface configuration. C. Enable insecure protocols within Cisco ISE in the allowed protocols configuration. D. Change the default policy in Cisco ISE to allow all devices not using machine authentication. Suggested Answer: D
Cisco SensorBase gathers threat information from a variety of Cisco products and services and performs analytics to find pattern on threats. Which term describes this process? A. authoring B. consumption C. deployment D. sharing Suggested Answer: D Reference: https://www.cisco.com/c/en/us/td/docs/security/security_management/cisco_security_manager/security_manager/414/user/guide/CSMUserGuide/ ipsglobe.html
Refer to the exhibit. What will occur when this device tries to connect to the port? A. 802. 1X will not work, but MAB will start and allow the device on the network. B. 802. 1X will work and the device will be allowed on the network. C. 802. 1X will not work and the device will not be allowed network access. D. 802. 1X and MAB will both be used and ISE can use policy to determine the access level. Suggested Answer: D
Which telemetry data captures variations seen within the flow, such as the packets TTL, IP/TCP flags, and payload length? A. flow insight variation B. software package variation C. interpacket variation D. process details variation Suggested Answer: C
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view of activity? A. SNMP B. SMTP C. syslog D. model-driven telemetry Suggested Answer: D Reference: https://developer.cisco.com/docs/ios-xe/#!streaming-telemetry-quick-start-guide
What two mechanisms are used to redirect users to a web portal to authenticate to ISE for guest services? (Choose two.) A. TACACS+ B. central web auth C. single sign-on D. multiple factor auth E. local web auth Suggested Answer: BE Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_01110.html
Which ID store requires that a shadow user be created on Cisco ISE for the admin login to work? A. RSA SecureID B. Internal Database C. Active Directory D. LDAP Suggested Answer: C
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10. What must the administrator implement to ensure that all devices are compliant before they are allowed on the network? A. Cisco Identity Services Engine and AnyConnect Posture module B. Cisco Stealthwatch and Cisco Identity Services Engine integration C. Cisco ASA firewall with Dynamic Access Policies configured D. Cisco Identity Services Engine with PxGrid services enabled Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect46/administration/guide/b_AnyConnect_Administrator_Guide_4-6/ configure-posture.html
Using Cisco Cognitive Threat Analytics, which platform automatically blocks risky sites, and test unknown sites for hidden advanced threats before allowing users to click them? A. Cisco Identity Services Engine B. Cisco Enterprise Security Appliance C. Cisco Web Security Appliance D. Cisco Advanced Stealthwatch Appliance Suggested Answer: C
An organization configures Cisco Umbrella to be used for its DNS services. The organization must be able to block traffic based on the subnet that the endpoint is on, but sees only the requests from its public IP addresses instead of each internal IP address. What must be done to resolve this issue? A. Install the Microsoft Active Directory Connector to give IP address information stitched to the requests in the Cisco Umbrella dashboard. B. Use the tenant control features to identify each subnet being used and track the connections within the Cisco Umbrella dashboard. C. Configure an internal domain within Cisco Umbrella to help identify each address and create policy from the domains. D. Set up a Cisco Umbrella virtual appliance to internally field the requests and see the traffic of each IP address. Suggested Answer: D Reference: https://docs.umbrella.com/deployment-umbrella/docs/internal-networks-setup-guide
An engineer adds a custom detection policy to a Cisco AMP deployment and encounters issues with the configuration. The simple detection mechanism is configured, but the dashboard indicates that the hash is not 64 characters and is non-zero. What is the issue? A. The hash being uploaded is part of a set in an incorrect format. B. The engineer is attempting to upload a file instead of a hash. C. The file being uploaded is incompatible with simple detections and must use advanced detections. D. The engineer is attempting to upload a hash created using MD5 instead of SHA-256. Suggested Answer: D
What is the benefit of integrating Cisco ISE with a MDM solution? A. It provides compliance checks for access to the network. B. It provides the ability to update other applications on the mobile device. C. It provides the ability to add applications to the mobile device through Cisco ISE. D. It provides network device administration access. Suggested Answer: A
Which feature is leveraged by advanced antimalware capabilities to be an effective endpoint protection platform? A. blocklisting B. storm centers C. big data D. sandboxing Suggested Answer: D
A Cisco AMP for Endpoints administrator configures a custom detection policy to add specific MD5 signatures. The configuration is created in the simple detection policy section, but it does not work. What is the reason for this failure? A. The administrator must upload the file instead of the hash for Cisco AMP to use. B. The APK must be uploaded for the application that the detection is intended. C. The MD5 hash uploaded to the simple detection policy is in the incorrect format. D. Detections for MD5 signatures must be configured in the advanced custom detection policies. Suggested Answer: A
An administrator is adding a new Cisco ISE node to an existing deployment. What must be done to ensure that the addition of the node will be successful when inputting the FQDN? A. Change the IP address of the new Cisco ISE node to the same network as the others. B. Make the new Cisco ISE node a secondary PAN before registering it with the primary. C. Open port 8905 on the firewall between the Cisco ISE nodes. D. Add the DNS entry for the new Cisco ISE node into the DNS server. Suggested Answer: A
Which portion of the network do EPP solutions solely focus on and EDR solutions do not? A. East-West gateways B. server farm C. core D. perimeter Suggested Answer: D Reference: https://www.cisco.com/c/en/us/products/security/endpoint-security/what-is-endpoint-detection-response-edr.html
Which benefit does endpoint security provide the overall security posture of an organization? A. It streamlines the incident response process to automatically perform digital forensics on the endpoint. B. It allows the organization to mitigate web-based attacks as long as the user is active in the domain. C. It allows the organization to detect and respond to threats at the edge of the network. D. It allows the organization to detect and mitigate threats that the perimeter security devices do not detect. Suggested Answer: D
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation? A. Nexus B. Stealthwatch C. Firepower D. Tetration Suggested Answer: D Reference: https://www.cisco.com/c/en/us/solutions/security/secure-data-center-solution/index.html#~products
An engineer needs a solution for TACACS+ authentication and authorization for device administration. The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to use 802.1X, MAB, or WebAuth. Which product meets all of these requirements? A. Cisco Prime Infrastructure B. Cisco Identity Services Engine C. Cisco Stealthwatch D. Cisco AMP for Endpoints Suggested Answer: B
How does Cisco Stealthwatch Cloud provide security for cloud environments? A. It delivers visibility and threat detection. B. It prevents exfiltration of sensitive data. C. It assigns Internet-based DNS protection for clients and servers. D. It facilitates secure connectivity between public and private networks. Suggested Answer: A Reference: https://www.content.shi.com/SHIcom/ContentAttachmentImages/SharedResources/FBLP/Cisco/Cisco-091919-Simple-IT-Whitepaper.pdf
Which Cisco security solution protects remote users against phishing attacks when they are not connected to the VPN? A. Cisco Umbrella B. Cisco Firepower NGIPS C. Cisco Stealthwatch D. Cisco Firepower Suggested Answer: A
What must be used to share data between multiple security products? A. Cisco Platform Exchange Grid B. Cisco Rapid Threat Containment C. Cisco Stealthwatch Cloud D. Cisco Advanced Malware Protection Suggested Answer: A
Which two characteristics of messenger protocols make data exfiltration difficult to detect and prevent? (Choose two.) A. Messenger applications cannot be segmented with standard network controls B. Malware infects the messenger application on the user endpoint to send company data C. Traffic is encrypted, which prevents visibility on firewalls and IPS systems D. An exposed API for the messaging platform is used to send large amounts of data E. Outgoing traffic is allowed so users can communicate with outside organizations Suggested Answer: AE
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic? A. Cisco Security Intelligence B. Cisco Application Visibility and Control C. Cisco Model Driven Telemetry D. Cisco DNA Center Suggested Answer: B
What provides visibility and awareness into what is currently occurring on the network? A. CMX B. WMI C. Cisco Prime Infrastructure D. Telemetry Suggested Answer: D
How is ICMP used as an exfiltration technique? A. by flooding the destination host with unreachable packets B. by sending large numbers of ICMP packets with a targeted hosts source IP address using an IP broadcast address C. by encrypting the payload in an ICMP packet to carry out command and control tasks on a compromised host D. by overwhelming a targeted host with ICMP echo-request packets Suggested Answer: C
Refer to the exhibit. An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing? A. dot1x reauthentication B. cisp enable C. dot1x pae authenticator D. authentication open Suggested Answer: C
An engineer is configuring 802.1X authentication on Cisco switches in the network and is using CoA as a mechanism. Which port on the firewall must be opened to allow the CoA traffic to traverse the network? A. UDP 1700 B. TCP 6514 C. UDP 1812 D. TCP 49 Suggested Answer: A
What are two Detection and Analytics Engines of Cognitive Threat Analytics? (Choose two.) A. data exfiltration B. command and control communication C. intelligent proxy D. snort E. URL categorization Suggested Answer: AB Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cognitive-threat-analytics/at-a-glance-c45-736555.pdf
Which two risks is a company vulnerable to if it does not have a well-established patching solution for endpoints? (Choose two.) A. malware B. denial-of-service attacks C. ARP spoofing D. exploits E. eavesdropping Suggested Answer: AD
Which benefit is provided by ensuring that an endpoint is compliant with a posture policy configured in Cisco ISE? A. It adds endpoints to identity groups dynamically B. It allows the endpoint to authenticate with 802.1x or MAB C. It allows CoA to be applied if the endpoint status is compliant D. It verifies that the endpoint has the latest Microsoft security patches installed Suggested Answer: D
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which probe must be enabled for this type of profiling to work? A. SNMP B. NMAP C. DHCP D. NetFlow Suggested Answer: C
What is the benefit of installing Cisco AMP for Endpoints on a network? A. It enables behavioral analysis to be used for the endpoints B. It provides flow-based visibility for the endpoints' network connections. C. It protects endpoint systems through application control and real-time scanning. D. It provides operating system patches on the endpoints for security. Suggested Answer: C
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them? A. because defense-in-depth stops at the network B. because human error or insider threats will still exist C. to prevent theft of the endpoints D. to expose the endpoint to more threats Suggested Answer: B
What must be configured in Cisco ISE to enforce reauthentication of an endpoint session when an endpoint is deleted from an identity group? A. SNMP probe B. CoA C. external identity source D. posture assessment Suggested Answer: B
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint Protection Platform? A. when there is a need to have more advanced detection capabilities B. when there is no firewall on the network C. when there is a need for traditional anti-malware detection D. when there is no need to have the solution centrally managed Suggested Answer: A
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services Engine? (Choose two.) A. RADIUS B. TACACS+ C. DHCP D. sFlow E. SMTP Suggested Answer: AC Reference: https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_prof_pol.html
What are two reasons for implementing a multifactor authentication solution such as Cisco Duo Security provide to an organization? (Choose two.) A. single sign-on access to on-premises and cloud applications B. identification and correction of application vulnerabilities before allowing access to resources C. secure access to on-premises and cloud applications D. integration with 802.1x security using native Microsoft Windows supplicant E. flexibility of different methods of 2FA such as phone callbacks, SMS passcodes, and push notifications Suggested Answer: CE
What are the two most commonly used authentication factors in multifactor authentication? (Choose two.) A. biometric factor B. time factor C. confidentiality factor D. knowledge factor E. encryption factor Suggested Answer: AD
An MDM provides which two advantages to an organization with regards to device management? (Choose two.) A. asset inventory management B. allowed application management C. AD group policy management D. network device management E. critical device management Suggested Answer: AB
What is the purpose of the My Devices Portal in a Cisco ISE environment? A. to register new laptops and mobile devices B. to manage and deploy antivirus definitions and patches on systems owned by the end user C. to provision userless and agentless systems D. to request a newly provisioned mobile device Suggested Answer: A
Which Cisco platform ensures that machines that connect to organizational networks have the recommended antivirus definitions and patches to help prevent an organizational malware outbreak? A. Cisco Prime Infrastructure B. Cisco ESA C. Cisco WiSM D. Cisco ISE Suggested Answer: D
In which two ways does Easy Connect help control network access when used with Cisco TrustSec? (Choose two.) A. It integrates with third-party products to provide better visibility throughout the network. B. It allows for the assignment of Security Group Tags and does not require 802.1x to be configured on the switch or the endpoint. C. It creates a dashboard in Cisco ISE that provides full visibility of all connected endpoints. D. It allows for managed endpoints that authenticate to AD to be mapped to Security Groups (PassiveID). E. It allows multiple security products to share information and work together to enhance security posture in the network. Suggested Answer: BD Reference: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise-networks/trustsec/trustsec-with-easy-connect-configuration-guide.pdf
What does Cisco AMP for Endpoints use to help an organization detect different families of malware? A. Tetra Engine to detect malware when the endpoint is connected to the cloud B. ClamAV Engine to perform email scanning C. Spero Engine with machine learning to perform dynamic analysis D. Ethos Engine to perform fuzzy fingerprinting Suggested Answer: D Reference: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2016/pdf/BRKSEC-2139.pdf
What is a benefit of conducting device compliance checks? A. It validates if anti-virus software is installed. B. It scans endpoints to determine if malicious activity is taking place. C. It indicates what type of operating system is connecting to the network. D. It detects email phishing attacks. Suggested Answer: A
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details? A. Context Visibility B. Accounting Reports C. Adaptive Network Control Policy List D. RADIUS Live Logs Suggested Answer: D
What is the role of an endpoint in protecting a user from a phishing attack? A. Ensure that antivirus and antimalware software is up-to-date. B. Use machine learning models to help identify anomalies and determine expected sending behavior. C. Use Cisco Stealthwatch and Cisco ISE Integration. D. Utilize 802.1X network security to ensure unauthorized access to resources. Suggested Answer: A
Why is it important to implement MFA inside of an organization? A. To prevent brute force attacks from being successful. B. To prevent phishing attacks from being successful. C. To prevent DoS attacks from being successful. D. To prevent man-in-the-middle attacks from being successful. Suggested Answer: A
Which posture assessment requirement provides options to the client for remediation within a certain timeframe? A. audit B. mandatory C. visibility D. optional Suggested Answer: B Reference: https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_010111.html
A customer has various external HTTP resources available including Intranet, Extranet, and Internet, with a proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured to select when to connect direct or when to use proxy? A. Bridge mode B. Transparent mode C. .PAC file D. Forward file Suggested Answer: C
What is a benefit of using Cisco CWS compared to an on-premises Cisco WSA? A. Content scanning for SAAS cloud applications is available through Cisco CWS and not available through Cisco WSA. B. URL categories are updated more frequently on Cisco CWS than they are on Cisco WSA. C. Cisco CWS minimizes the load on the internal network and security infrastructure as compared to Cisco WSA. D. Cisco CWS eliminates the need to backhaul traffic through headquarters for remote workers whereas Cisco WSA does not. Suggested Answer: D Reference: https://www.cisco.com/c/en/us/products/collateral/security/web-security-appliance/guide-c07-742373.html
An engineer needs to add protection for data in transit and have headers in the email message. Which configuration is needed to accomplish this goal? A. Deploy an encryption appliance. B. Provision the email appliance. C. Map sender IP addresses to a host interface. D. Enable flagged message handling. Suggested Answer: B
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection? A. Cisco Tetration B. Cisco ISE C. Cisco AnyConnect D. Cisco AMP for Network Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/switches/datacenter/aci/apic/white_papers/Cisco-IT-Tetration-Deployment-Part-2-of-2.html
A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access. The Cisco ESA must also join a cluster machine using preshared keys. What must be configured to meet these requirements? A. Enable two-factor authentication through a RADIUS server and then join the cluster by using the Cisco ESA GUI. B. Enable two-factor authentication through a TACACS+ server and then join the cluster by using the Cisco ESA CLI. C. Enable two-factor authentication through a TACACS+ server and then join the cluster by using the Cisco ESA GUI. D. Enable two-factor authentication through a RADIUS server and then join the cluster by using the Cisco ESA CLI. Suggested Answer: A
Refer to the exhibit. How does Cisco Umbrella manage traffic that is directed toward risky domains? A. Traffic is managed by the application settings, unhandled and allowed. B. Traffic is managed by the security settings and blocked. C. Traffic is proxied through the intelligent proxy. D. Traffic is allowed but logged. Suggested Answer: B
An organization wants to improve its cybersecurity processes and to add intelligence to its data. The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA. What must be done to accomplish these objectives? A. Configure the integrations with Talos intelligence to take advantage of the threat intelligence that it provides. B. Download the threat intelligence feed from the IETF and import it into the Cisco FTD and Cisco WSA databases. C. Create an automated download of the Internet Storm Center intelligence feed into the Cisco FTD and Cisco WSA databases to tie to the dynamic access control policies. D. Create a Cisco pxGrid connection to NIST to import this information into the security products for policy use. Suggested Answer: A
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites but other sites are not accessible due to an error. Why is the error occurring? A. Client computers do not have an SSL certificate deployed from an internal CA server. B. Client computers do not have the Cisco Umbrella Root CA certificate installed. C. IP-Layer Enforcement is not configured. D. Intelligent proxy and SSL decryption is disabled in the policy. Suggested Answer: A
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic? A. File Analysis B. SafeSearch C. SSL Decryption D. Destination Lists Suggested Answer: C
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats? A. Application Control B. Security Category Blocking C. Content Category Blocking D. File Analysis Suggested Answer: B Reference: https://support.umbrella.com/hc/en-us/articles/115004563666-Understanding-Security-Categories
How is Cisco Umbrella configured to log only security events? A. per policy B. in the Reporting settings C. in the Security Settings section D. per network in the Deployments section Suggested Answer: A Reference: https://docs.umbrella.com/deployment-umbrella/docs/log-management
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious? A. Cisco AMP B. Cisco AnyConnect C. Cisco Dynamic DNS D. Cisco Talos Suggested Answer: D
What are two list types within Cisco AMP for Endpoints Outbreak Control? (Choose two.) A. blocked ports B. simple custom detections C. command and control D. allowed applications E. URL Suggested Answer: BD Reference: https://docs.amp.cisco.com/en/A4E/AMP%20for%20Endpoints%20User%20Guide.pdf chapter 2
For which two conditions can an endpoint be checked using ISE posture assessment? (Choose two.) A. computer identity B. Windows service C. user identity D. Windows firewall E. default browser Suggested Answer: BD
Which Cisco product provides proactive endpoint protection and allows administrators to centrally manage the deployment? A. NGFW B. AMP C. WSA D. ESA Suggested Answer: B
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.) A. Patch for cross-site scripting. B. Perform backups to the private cloud. C. Protect against input validation and character escapes in the endpoint. D. Install a spam and virus email filter. E. Protect systems with an up-to-date antimalware program. Suggested Answer: DE
An engineer used a posture check on a Microsoft Windows endpoint and discovered that the MS17-010 patch was not installed, which left the endpoint vulnerable to WannaCry ransomware. Which two solutions mitigate the risk of this ransomware infection? (Choose two.) A. Configure a posture policy in Cisco Identity Services Engine to install the MS17-010 patch before allowing access on the network. B. Set up a profiling policy in Cisco Identity Services Engine to check an endpoint patch level before allowing access on the network. C. Configure a posture policy in Cisco Identity Services Engine to check that an endpoint patch level is met before allowing access on the network. D. Configure endpoint firewall policies to stop the exploit traffic from being allowed to run and replicate throughout the network. E. Set up a well-defined endpoint patching strategy to ensure that endpoints have critical vulnerabilities patched in a timely fashion. Suggested Answer: AC
What is the primary difference between an Endpoint Protection Platform and an Endpoint Detection and Response? A. EPP focuses on prevention, and EDR focuses on advanced threats that evade perimeter defenses. B. EDR focuses on prevention, and EPP focuses on advanced threats that evade perimeter defenses. C. EPP focuses on network security, and EDR focuses on device security. D. EDR focuses on network security, and EPP focuses on device security. Suggested Answer: A Reference: https://www.cisco.com/c/en/us/products/security/endpoint-security/what-is-endpoint-detection-response-edr.html
An engineer is configuring AMP for endpoints and wants to block certain files from executing. Which outbreak control method is used to accomplish this task? A. device flow correlation B. simple detections C. application blocking list D. advanced custom detections Suggested Answer: C
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal? A. Port Bounce B. CoA Terminate C. CoA Reauth D. CoA Session Query Suggested Answer: C
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for analysis. The network is congested and is affecting communication. How will the Cisco ESA handle any files which need analysis? A. The ESA immediately makes another attempt to upload the file. B. The file upload is abandoned. C. AMP calculates the SHA-256 fingerprint, caches it, and periodically attempts the upload. D. The file is queued for upload when connectivity is restored Suggested Answer: B
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a recipient address. Which list contains the allowed recipient addresses? A. SAT B. BAT C. HAT D. RAT Suggested Answer: D
Why would a user choose an on-premises ESA versus the CES solution? A. Sensitive data must remain onsite. B. Demand is unpredictable. C. The server team wants to outsource this service. D. ESA is deployed inline. Suggested Answer: A
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware? (Choose two.) A. Sophos engine B. white list C. RAT D. outbreak filters E. DLP Suggested Answer: AD
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future? A. Modify web proxy settings. B. Modify outbound malware scanning policies. C. Modify identification profiles. D. Modify an access policy. Suggested Answer: A
An engineer has enabled LDAP accept queries on a listener. Malicious actors must be prevented from quickly identifying all valid recipients. What must be done on the Cisco ESA to accomplish this goal? A. Configure Directory Harvest Attack Prevention B. Bypass LDAP access queries in the recipient access table. C. Use Bounce Verification. D. Configure incoming content filters. Suggested Answer: A
In which two ways does a system administrator send web traffic transparently to the Cisco WSA? (Choose two.) A. use Web Cache Communication Protocol B. configure AD Group Policies to push proxy settings C. configure the proxy IP address in the web-browser settings D. configure policy-based routing on the network infrastructure E. reference a Proxy Auto Config file Suggested Answer: AD
What is the function of the Context Directory Agent? A. reads the AD logs to map IP addresses to usernames B. relays user authentication requests from Cisco WSA to AD C. maintains users' group memberships D. accepts user authentication requests on behalf of Cisco WSA for user identification Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/ibf/cda_10/Install_Config_guide/cda10/cda_oveviw.html
A network administrator is configuring a rule in an access control policy to block certain URLs and selects the `Chat and Instant Messaging` category. Which reputation score should be selected to accomplish this goal? A. 5 B. 10 C. 3 D. 1 Suggested Answer: D
A Cisco ESA network administrator has been tasked to use a newly installed service to help create policy based on the reputation verdict. During testing, it is discovered that the Cisco ESA is not dropping files that have an undetermined verdict. What is causing this issue? A. The policy was created to send a message to quarantine instead of drop. B. The file has a reputation score that is below the threshold. C. The file has a reputation score that is above the threshold. D. The policy was created to disable file analysis. Suggested Answer: B
An organization has a Cisco ESA set up with DLP policies and would like to customize the action assigned for violations. The organization wants a copy of the message to be delivered with a message added to flag it as a DLP violation. Which actions must be performed in order to provide this capability? A. deliver and add disclaimer text B. quarantine and send a DLP violation notification C. quarantine and alter the subject header with a DLP violation D. deliver and send copies to other recipients Suggested Answer: B Reference: https://www.cisco.com/c/en/us/support/docs/security/email-security-appliance/216086-best-practice-guide-for-data-loss-preven.html
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two.) A. Deploy the Cisco ESA in the DMZ. B. Use outbreak filters from SenderBase. C. Configure a recipient access table. D. Enable a message tracking service. E. Scan quarantined emails using AntiVirus signatures. Suggested Answer: BE
An organization has noticed an increase in malicious content downloads and wants to use Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web traffic. Which action will accomplish this task? A. Use destination block lists. B. Configure application block lists. C. Configure the intelligent proxy. D. Set content settings to High. Suggested Answer: C
Which attack is preventable by Cisco ESA but not by the Cisco WSA? A. SQL injection B. phishing C. buffer overflow D. DoS Suggested Answer: D
An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the organization to create a policy to control application specific activity. After enabling the AVC engine, what must be done to implement this? A. Use security services to configure the traffic monitor. B. Use URL categorization to prevent the application traffic. C. Use an access policy group to configure application control settings. D. Use web security reporting to validate engine functionality. Suggested Answer: C
What is the role of Cisco Umbrella Roaming when it is installed on an endpoint? A. to establish secure VPN connectivity to the corporate network B. to enforce posture compliance and mandatory software C. to ensure that assets are secure from malicious links on and off the corporate network D. to protect the endpoint against malicious file transfers Suggested Answer: C
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443. The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users. What must be done on the Cisco WSA to support these requirements? A. Use PAC keys to allow only the required network devices to send the traffic to the Cisco WSA. B. Configure transparent traffic redirection using WCCP in the Cisco WSA and on the network device. C. Configure active traffic redirection using WPAD in the Cisco WSA and on the network device. D. Use the Layer 4 setting in the Cisco WSA to receive explicit forward requests from the network device. Suggested Answer: B
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked? A. Configure the domain.com address in the block list. B. Configure the *.domain.com address in the block list. C. Configure the *.com address in the block list. D. Configure the *domain.com address in the block list. Suggested Answer: A
An organization wants to use Cisco FTD or Cisco ASA devices. Specific URLs must be blocked from being accessed via the firewall, which requires that the administrator input the bad URL categories that the organization wants blocked into the access policy. Which solution should be used to meet this requirement? A. Cisco FTD because it enables URL filtering and blocks malicious URLs by default, whereas Cisco ASA does not. B. Cisco ASA because it enables URL filtering and blocks malicious URLs by default, whereas Cisco FTD does not. C. Cisco ASA because it includes URL filtering in the access control policy capabilities, whereas Cisco FTD does not. D. Cisco FTD because it includes URL filtering in the access control policy capabilities, whereas Cisco ASA does not. Suggested Answer: D
Which component of Cisco Umbrella architecture increases reliability of the service? A. BGP route reflector B. anycast IP C. AMP Threat Grid D. Cisco Talos Suggested Answer: B
Which DevSecOps implementation process gives a weekly or daily update instead of monthly or quarterly in the applications? A. CI/CD pipeline B. container C. orchestration D. security Suggested Answer: A Reference: https://devops.com/how-to-implement-an-effective-ci-cd-pipeline/
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container? A. SDLC B. Lambda C. Contiv D. Docker Suggested Answer: D Reference: https://www.cisco.com/c/dam/global/es_es/pdfs/Cisco-cloudcenter-architecture-wp-c11-737224.pdf
An organization is selecting a cloud architecture and does not want to be responsible for patch management of the operating systems. Why should the organization select either Platform as a Service or Infrastructure as a Service for this environment? A. Infrastructure as a Service because the customer manages the operating system. B. Platform as a Service because the service provider manages the operating system. C. Infrastructure as a Service because the service provider manages the operating system. D. Platform as a Service because the customer manages the operating system. Suggested Answer: B Reference: https://www.cisco.com/c/en/us/solutions/cloud/what-is-cloud-computing.html#~cloud-computing-services
How does a cloud access security broker function? A. It is an authentication broker to enable single sign-on and multi-factor authentication for a cloud solution. B. It scans other cloud solutions being used within the network and identifies vulnerabilities. C. It integrates with other cloud solutions via APIs and monitors and creates incidents based on events from the cloud solution. D. It acts as a security information and event management solution and receives syslog from other cloud solutions. Suggested Answer: C Reference: https://www.cisco.com/c/en_in/products/security/cloudlock/index.html#~stickynav=2
An organization has a requirement to collect full metadata information about the traffic going through their AWS cloud services. They want to use this information for behavior analytics and statistics. Which two actions must be taken to implement this requirement? (Choose two.) A. Send syslog from AWS to Cisco Stealthwatch Cloud. B. Configure Cisco Stealthwatch Cloud to ingest AWS information. C. Send VPC Flow Logs to Cisco Stealthwatch Cloud. D. Configure Cisco Thousand Eyes to ingest AWS information. E. Configure Cisco ACI to ingest AWS information. Suggested Answer: AC Reference: https://www.cisco.com/c/en/us/products/collateral/security/stealthwatch-cloud/at-a-glance-c45-739850.html
An organization wants to implement a cloud-delivered and SaaS-based solution to provide visibility and threat detection across the AWS network. The solution must be deployed without software agents and rely on AWS VPC flow logs instead. Which solution meets these requirements? A. NetFlow collectors B. Cisco Cloudlock C. Cisco Stealthwatch Cloud D. Cisco Umbrella Suggested Answer: C Reference: https://www.cisco.com/c/en/us/products/security/stealthwatch-cloud/index.html
Where are individual sites specified to be blacklisted in Cisco Umbrella? A. application settings B. content categories C. security settings D. destination lists Suggested Answer: D
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed through the Cisco Umbrella network. Which action tests the routing? A. Ensure that the client computers are pointing to the on-premises DNS servers. B. Enable the Intelligent Proxy to validate that traffic is being routed correctly. C. Add the public IP address that the client computers are behind to a Core Identity. D. Browse to http://welcome.umbrella.com/ to validate that the new identity is working. Suggested Answer: D
How does Cisco Umbrella archive logs to an enterprise-owned storage? A. by using the Application Programming Interface to fetch the logs B. by sending logs via syslog to an on-premises or cloud-based syslog server C. by the system administrator downloading the logs from the Cisco Umbrella web portal D. by being configured to send logs to a self-managed AWS S3 bucket Suggested Answer: D Reference: https://docs.umbrella.com/deployment-umbrella/docs/log-management
Which API is used for Content Security? A. NX-OS API B. IOS XR API C. OpenVuln API D. AsyncOS API Suggested Answer: D Reference: https://www.cisco.com/c/en/us/td/docs/security/security_management/sma/sma12-0/api/b_SMA_API_12/test_chapter_01.html
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic? A. IP Block List Center B. File Reputation Center C. AMP Reputation Center D. IP and Domain Reputation Center Suggested Answer: D
What is the primary role of the Cisco Email Security Appliance? A. Mail Submission Agent B. Mail Transfer Agent C. Mail Delivery Agent D. Mail User Agent Suggested Answer: B
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.) A. DDoS B. antispam C. antivirus D. encryption E. DLP Suggested Answer: DE Reference: https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
An organization is receiving SPAM emails from a known malicious domain. What must be configured in order to prevent the session during the initial TCP communication? A. Configure the Cisco ESA to reset the TCP connection. B. Configure policies to stop and reject communication. C. Configure the Cisco ESA to drop the malicious emails. D. Configure policies to quarantine malicious emails. Suggested Answer: B
Refer to the exhibit. What is a result of the configuration? A. Traffic from the DMZ network is redirected. B. Traffic from the inside network is redirected. C. All TCP traffic is redirected. D. Traffic from the inside and DMZ networks is redirected. Suggested Answer: D
An organization received a large amount of SPAM messages over a short time period. In order to take action on the messages, it must be determined how harmful the messages are and this needs to happen dynamically. What must be configured to accomplish this? A. Configure the Cisco WSA to modify policies based on the traffic seen. B. Configure the Cisco ESA to modify policies based on the traffic seen. C. Configure the Cisco WSA to receive real-time updates from Cisco Talos. D. Configure the Cisco ESA to receive real-time updates from Cisco Talos. Suggested Answer: D
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two.) A. The Cisco WSA responds with its own IP address only if it is running in explicit mode. B. The Cisco WSA is configured in a web browser only if it is running in transparent mode. C. The Cisco WSA responds with its own IP address only if it is running in transparent mode. D. The Cisco WSA uses a Layer 3 device to redirect traffic only if it is running in transparent mode. E. When the Cisco WSA is running in transparent mode, it uses the WSA's own IP address as the HTTP request destination. Suggested Answer: AD
Which technology is used to improve web traffic performance by proxy caching? A. WSA B. Firepower C. FireSIGHT D. ASA Suggested Answer: A
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP? A. transparent B. redirection C. forward D. proxy gateway Suggested Answer: A Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117940-qa-wsa-00.html
What is the purpose of the Decrypt for Application Detection feature within the WSA Decryption options? A. It decrypts HTTPS application traffic for unauthenticated users. B. It alerts users when the WSA decrypts their traffic. C. It decrypts HTTPS application traffic for authenticated users. D. It provides enhanced HTTPS application detection for AsyncOS. Suggested Answer: D Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01011.html
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two.) A. middleware B. applications C. virtualization D. operating systems E. data Suggested Answer: BE
Which public cloud provider supports the Cisco Next Generation Firewall Virtual? A. Google Cloud Platform B. Red Hat Enterprise Virtualization C. Amazon Web Services D. VMware ESXi Suggested Answer: C
What is an attribute of the DevSecOps process? A. security scanning and theoretical vulnerabilities B. development security C. isolated security team D. mandated security controls and check lists Suggested Answer: B
On which part of the IT environment does DevSecOps focus? A. application development B. wireless network C. data center D. perimeter network Suggested Answer: A
In a PaaS model, which layer is the tenant responsible for maintaining and patching? A. hypervisor B. virtual machine C. network D. application Suggested Answer: D Reference: https://www.bmc.com/blogs/saas-vs-paas-vs-iaas-whats-the-difference-and-how-to-choose/
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.) A. Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS B. Cisco FTDv with one management interface and two traffic interfaces configured C. Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises D. Cisco FTDv with two management interfaces and one traffic interface configured E. Cisco FTDv configured in routed mode and IPv6 configured Suggested Answer: AC Reference: https://www.cisco.com/c/en/us/products/collateral/security/adaptive-security-virtual-appliance-asav/white-paper-c11-740505.html
DRAG DROP - Drag and drop the steps from the left into the correct order on the right to enable Cisco AppDynamics to monitor an EC2 instance in AWS. Select and Place:Suggested Answer:
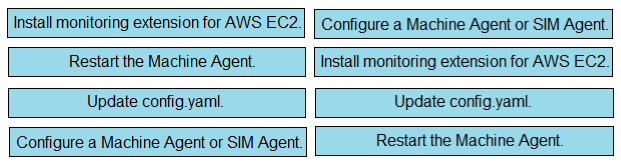
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway? A. Enable IP Layer enforcement. B. Activate the Cisco AMP license. C. Activate SSL decryption. D. Enable Intelligent Proxy. Suggested Answer: D
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The company needs to be able to protect sensitive data throughout the full environment. Which tool should be used to accomplish this goal? A. Cisco ISE B. Web Security Appliance C. Security Manager D. Cloudlock Suggested Answer: D
What are the two types of managed Intercloud Fabric deployment models? (Choose two.) A. Service Provider managed B. User managed C. Public managed D. Hybrid managed E. Enterprise managed Suggested Answer: AE
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with other cloud solutions via an API. Which solution should be used to accomplish this goal? A. CASB B. Cisco Cloudlock C. Adaptive MFA D. SIEM Suggested Answer: B
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally manage cloud policies across these platforms. Which software should be used to accomplish this goal? A. Cisco Defense Orchestrator B. Cisco Configuration Professional C. Cisco Secureworks D. Cisco DNA Center Suggested Answer: A Reference: https://www.cisco.com/c/en/us/products/collateral/security/defense-orchestrator/datasheet-c78-736847.html
Which factor must be considered when choosing the on-premise solution over the cloud-based one? A. With an on-premise solution, the provider is responsible for the installation and maintenance of the product, whereas with a cloud-based solution, the customer is responsible for it. B. With a cloud-based solution, the provider is responsible for the installation, but the customer is responsible for the maintenance of the product. C. With an on-premise solution, the provider is responsible for the installation, but the customer is responsible for the maintenance of the product. D. With an on-premise solution, the customer is responsible for the installation and maintenance of the product, whereas with a cloud-based solution, the provider is responsible for it. Suggested Answer: D
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users, data, and applications. There is a requirement to use the Cisco cloud-native CASB and cloud cybersecurity platform. What should be used to meet these requirements? A. Cisco NGFW B. Cisco Cloudlock C. Cisco Cloud Email Security D. Cisco Umbrella Suggested Answer: B
In an IaaS cloud services model, which security function is the provider responsible for managing? A. firewalling virtual machines B. Internet proxy C. hypervisor OS hardening D. CASB Suggested Answer: A
An organization wants to secure users, data, and applications in the cloud. The solution must be API-based on operate as a cloud-native CASB. Which solution must be used for this implementation? A. Cisco Cloud Email Security B. Cisco Cloudlock C. Cisco Umbrella D. Cisco Firepower Nest-Generation Firewall Suggested Answer: B
DRAG DROP - Drag and drop the cloud security assessment components from the left onto the definitions on the right. Select and Place:Suggested Answer:
An organization wants to secure data in a cloud environment. Its security model requires that all users be authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and data. There is also a need to allow certain application traffic and deny all other traffic by default. Which technology must be used to implement these requirements? A. virtual routing and forwarding B. access control policy C. virtual LAN D. microsegmentation Suggested Answer: D
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group? A. community B. private C. public D. hybrid Suggested Answer: A
How does Cisco Workload Optimization Manager help mitigate application performance issues? A. It automates resource resizing. B. It sets up a workload forensic score. C. It optimizes a flow path. D. It deploys an AWS Lambda system. Suggested Answer: A
An engineer is configuring their router to send NetfFow data to Stealthwatch which has an IP address of 1.1.1.1 using the flow record Stealthwatch406143794 command. Which additional command is required to complete the flow record? A. cache timeout active 60 B. destination 1.1.1.1 C. match ipv4 ttl D. transport udp 2055 Suggested Answer: C Reference: https://www.cisco.com/c/dam/en/us/td/docs/security/stealthwatch/netflow/config-trouble-netflow-stealth.pdf
An engineer is adding a Cisco DUO solution to the current TACACS+ deployment using Cisco ISE. The engineer wants to authenticate users using their account when they log into network devices. Which action accomplishes this task? A. Configure Cisco DUO with the external Active Directory connector and tie it to the policy set within Cisco ISE. B. Install and configure the Cisco DUO Authentication Proxy and configure the identity source sequence within Cisco ISE. C. Modify the current policy with the condition MFA: SourceSequence_DUO=true in the authorization conditions within Cisco ISE. D. Create an identity policy within Cisco ISE to send all authentication requests to Cisco DUO. Suggested Answer: B Reference: https://duo.com/docs/authproxy-reference
What is the function of the crypto isakmp key cisc406143794 address 0.0.0.0 0.0.0.0 command when establishing an IPsec VPN tunnel? A. It prevents all IP addresses from connecting to the VPN server. B. It configures the pre-shared authentication key. C. It configures the local address for the VPN server. D. It defines what data is going to be encrypted via the VPN. Suggested Answer: B This command is used to configure pre-shared-key for IPsec remote acess users on the Cisco router. Address is mentioned as 0.0.0.0 0.0.0.0 because the users will be connecting from random ip addresses and it is almost impossible to mention all the ip addresses. Hence, 0.0.0.0 0.0.0.0 is used to allow all public ip addresses.
An administrator is adding a new switch onto the network and has configured AAA for network access control. When testing the configuration, the RADIUS authenticates to Cisco ISE but is being rejected. Why is the ip radius source-interface command needed for this configuration? A. Only requests that originate from a configured NAS IP are accepted by a RADIUS server. B. The RADIUS authentication key is transmitted only from the defined RADIUS source interface. C. RADIUS requests are generated only by a router if a RADIUS source interface is defined. D. Encrypted RADIUS authentication requires the RADIUS source interface be defined. Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/ios/12_2/security/command/reference/srfrad.html#wp1027454
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true? A. To view bandwidth usage for NetFlow records, the QoS feature must be enabled. B. A sysopt command can be used to enable NSEL on a specific interface. C. NSEL can be used without a collector configured. D. A flow-export event type must be defined under a policy. Suggested Answer: D
Which feature requires a network discovery policy on the Cisco Firepower NGIPS? A. security intelligence B. impact flags C. health monitoring D. URL filtering Suggested Answer: B
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention System? A. correlation B. intrusion C. access control D. network discovery Suggested Answer: D
What is a characteristic of traffic storm control behavior? A. Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval. B. Traffic storm control cannot determine if the packet is unicast or broadcast. C. Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval. D. Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast. Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/routers/7600/ios/12-1E/configuration/guide/storm.html
DRAG DROP - Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right. Select and Place:Suggested Answer:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
Refer to the exhibit. Which statement about the authentication protocol used in the configuration is true? A. The authentication request contains only a password B. The authentication request contains only a username C. The authentication and authorization requests are grouped in a single packet. D. There are separate authentication and authorization request packets. Suggested Answer: C
Which deployment model is the most secure when considering risks to cloud adoption? A. public cloud B. hybrid cloud C. community cloud D. private cloud Suggested Answer: D
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective? A. It allows the administrator to quarantine malicious files so that the application can function, just not maliciously. B. It discovers and controls cloud apps that are connected to a company's corporate environment. C. It deletes any application that does not belong in the network. D. It sends the application information to an administrator to act on. Suggested Answer: B Reference: https://www.cisco.com/c/en/us/products/security/cloudlock/index.html#~features
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries? A. DNS tunneling B. DNSCrypt C. DNS security D. DNSSEC Suggested Answer: A Reference: https://learn-umbrella.cisco.com/cloud-security/dns-tunneling
Which technology reduces data loss by identifying sensitive information stored in public computing environments? A. Cisco SDA B. Cisco Firepower C. Cisco HyperFlex D. Cisco Cloudlock Suggested Answer: D Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cloudlock/cisco-cloudlock-cloud-data-security-datasheet.pdf
In which cloud services model is the tenant responsible for virtual machine OS patching? A. IaaS B. UCaaS C. PaaS D. SaaS Suggested Answer: A Reference: https://www.cmswire.com/cms/information-management/cloud-service-models-iaas-saas-paas-how-microsoft-office-365-azure-fit-in-021672.php
What is the function of Cisco Cloudlock for data security? A. data loss prevention B. controls malicious cloud apps C. detects anomalies D. user and entity behavior analytics Suggested Answer: A Reference: https://umbrella.cisco.com/products/casb
Which feature is supported when deploying Cisco ASAv within AWS public cloud? A. multiple context mode B. user deployment of Layer 3 networks C. IPv6 D. clustering Suggested Answer: B Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa96/asav/quick-start-book/asav-96-qsg/asav-aws.html
Which cloud service model offers an environment for cloud consumers to develop and deploy applications without needing to manage or maintain the underlying cloud infrastructure? A. PaaS B. XaaS C. IaaS D. SaaS Suggested Answer: A
Which risk is created when using an Internet browser to access cloud-based service? A. misconfiguration of Infra, which allows unauthorized access B. intermittent connection to the cloud connectors C. vulnerabilities within protocol D. insecure implementation of API Suggested Answer: C
What is the Cisco API-based broker that helps reduce compromises, application risks, and data breaches in an environment that is not on-premise? A. Cisco AppDynamics B. Cisco Cloudlock C. Cisco Umbrella D. Cisco AMP Suggested Answer: B
When configuring ISAKMP for IKEv1 Phase 1 on a Cisco IOS router, an administrator needs to input the command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the IP address in this command is used for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4? A. The key server that is managing the keys for the connection will be at 1.2.3.4. B. The address that will be used as the crypto validation authority. C. All IP addresses other than 1.2.3.4 will be allowed. D. The remote connection will only be allowed from 1.2.3.4. Suggested Answer: D
A network administrator is configuring SNMPv3 on a new router. The users have already been created, however an additional configuration is needed to facilitate access to the SNMP views. What must the administrator do to accomplish this? A. define the encryption algorithm to be used by SNMPv3 B. set the password to be used for SNMPv3 authentication C. map SNMPv3 users to SNMP views D. specify the UDP port used by SNMP Suggested Answer: C
DRAG DROP - Drag and drop the NetFlow export formats from the left onto the descriptions on the right. Select and Place:Suggested Answer:
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2015/pdf/BRKNMS-3132.pdf
Refer to the exhibit. When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine certificates. Which configuration item must be modified to allow this? A. Method B. SAML Server C. AAA Server Group D. Group Policy Suggested Answer: C
An administrator is trying to determine which applications are being used in the network but does not want the network devices to send metadata to Cisco Firepower. Which feature should be used to accomplish this? A. Network Discovery B. Access Control C. Packet Tracer D. NetFlow Suggested Answer: D
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392481137. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however is unable to do so. Which command is required to enable the client to accept the server's authentication key? A. ntp server 1.1.1.2 key 1 B. ntp peer 1.1.1.2 key 1 C. ntp server 1.1.1.1 key 1 D. ntp peer 1.1.1.1 key 1 Suggested Answer: C Reference: https://www.oreilly.com/library/view/cisco-ios-cookbook/0596527225/ch14s13.html
Due to a traffic storm on the network, two interfaces were error-disabled, and both interfaces sent SNMP traps. Which two actions must be taken to ensure that interfaces are put back into service? (Choose two.) A. Enable the snmp-server enable traps command and wait 300 seconds. B. Use EEM to have the ports return to service automatically in less than 300 seconds C. Ensure that interfaces are configured with the error-disable detection and recovery feature. D. Have Cisco Prime Infrastructure issue an SNMP set command to re-enable the ports after the preconfigured interval. E. Enter the shutdown and no shutdown commands on the interfaces. Suggested Answer: CE
Refer to the exhibit. An administrator is adding a new Cisco FTD device to their network and wants to manage it with Cisco FMC. The Cisco FTD uses a registration key of Cisc392481137 and is not behind a NAT device. Which command is needed to enable this on the Cisco FTD? A. configure manager add
16 B. configure manager add DONTRESOLVE FTD123 C. configure manager add D. configure manager add DONTRESOLVE Suggested Answer: C Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config-guide-v62/firepower_command_line_reference.html#ID- 2201-000004b4
A network administrator needs to find out what assets currently exist on the network. Third-party systems need to be able to feed host data into Cisco Firepower. What must be configured to accomplish this? A. a Network Analysis policy to receive NetFlow data from the host B. a File Analysis policy to send file data into Cisco Firepower C. a Network Discovery policy to receive data from the host D. a Threat Intelligence policy to download the data from the host Suggested Answer: C
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users? A. file access from a different user B. user login suspicious behavior C. privilege escalation D. interesting file access Suggested Answer: A
Which attribute has the ability to change during the RADIUS CoA? A. authorization B. NTP C. accessibility D. membership Suggested Answer: A
An administrator configures new authorization policies within Cisco ISE and has difficulty profiling the devices. Attributes for the new Cisco IP phones that are profiled based on the RADIUS authentication are seen; however, the attributes for CDP or DHCP are not. What should the administrator do to address this issue? A. Configure a service template within the switch to standardize the port configurations so that the correct information is sent to Cisco ISE. B. Configure the ip dhcp snooping trust command on the DHCP interfaces to get the information to Cisco ISE. C. Configure the authentication port-control auto feature within Cisco ISE to identify the devices that are trying to connect. D. Configure the device sensor feature within the switch to send the appropriate protocol information. Suggested Answer: D
An organization deploys multiple Cisco FTD appliances and wants to manage them using one centralized solution. The organization does not have a local VM but does have existing Cisco ASA that must migrate over to Cisco FTDs. Which solution meets the needs of the organization? A. Cisco FMC B. CDO C. CSM D. Cisco FDM Suggested Answer: B
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes? A. Telemetry uses push and pull, which makes it more secure than SNMP. B. Telemetry uses push and pull, which makes it more scalable than SNMP. C. Telemetry uses a push method, which makes it faster than SNMP. D. Telemetry uses a pull method, which makes it more reliable than SNMP. Suggested Answer: C
Refer to the exhibit. A network engineer is testing NTP authentication and realizes that any device synchronizes time with this router and that NTP authentication is not enforced. What is the cause of this issue? A. The hashing algorithm that was used was MD5, which is unsupported. B. The key was configured in plain text. C. NTP authentication is not enabled. D. The router was not rebooted after the NTP configuration updated. Suggested Answer: C
An engineer has been tasked with configuring a Cisco FTD to analyze protocol fields and detect anomalies in the traffic from industrial systems. What must be done to meet these requirements? A. Enable traffic analysis in the Cisco FTD. B. Implement pre-filter policies for the CIP preprocessor. C. Configure intrusion rules for the DNP3 preprocessor. D. Modify the access control policy to trust the industrial traffic. Suggested Answer: C
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices. The default management port conflicts with other communications on the network and must be changed. What must be done to ensure that all devices can communicate together? A. Change the management port on Cisco FMC so that it pushes the change to all managed Cisco FTD devices. B. Set the sftunnel port to 8305. C. Manually change the management port on Cisco FMC and all managed Cisco FTD devices. D. Set the sftunnel to go through the Cisco FTD. Suggested Answer: C
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router. The organization needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of 172.19.20.24. Which command on the hub will allow the administrator to accomplish this? A. crypto isakmp identity address 172.19.20.24 B. crypto ca identity 172.19.20.24 C. crypto enrollment peer address 172.19.20.24 D. crypto isakmp key Cisco0123456789 172.19.20.24 Suggested Answer: D
A Cisco FTD engineer is creating a newIKEv2 policy called s2s00123456789 for their organization to allow additional protocols to terminate network devices with. They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy. What should be done in order to support this? A. Change the encryption to AES* to support all AES algorithms in the primary policy. B. Make the priority for the primary policy 10 and the new policy 1. C. Change the integrity algorithms to SHA* to support all SHA algorithms in the primary policy. D. Make the priority for the new policy 5 and the primary policy 1. Suggested Answer: D
What is a functional difference between a Cisco ASA and Cisco IOS router with Zone-Based Policy Firewall? A. The Cisco ASA can be configured for high availability, whereas the Cisco IOS router with Zone-Based Policy Firewall cannot. B. The Cisco IOS router with Zone-Based Policy Firewall can be configured for high availability, whereas the Cisco ASA cannot. C. The Cisco ASA denies all traffic by default, whereas the Cisco IOS router with Zone-Based Policy Firewall starts out by allowing all traffic, even on untrusted interfaces. D. The Cisco IOS router with Zone-Based Policy Firewall denies all traffic by default, whereas Cisco ASA starts out by allowing traffic until rules are added. Suggested Answer: C
What can be integrated with Cisco Threat Intelligence Director to provide information about security threats, which allows the SOC to proactively automate responses to those threats? A. Cisco Umbrella B. External Threat Feeds C. Cisco Threat Grid D. Cisco Stealthwatch Suggested Answer: B
Which Cisco command enables authentication, authorization, and accounting globally so that CoA is supported on the device? A. aaa server radius dynamic-author B. auth-type all C. aaa new-model D. ip device-tracking Suggested Answer: A
What is a characteristic of Firepower NGIPS inline deployment mode? A. ASA with Firepower module cannot be deployed B. It cannot take actions such as blocking traffic C. It is out-of-band from traffic D. It must have inline interface pairs configured Suggested Answer: D
A mall provides security services to customers with a shared appliance. The mall wants separation of management on the shared appliance. Which ASA deployment mode meets these needs? A. routed mode B. multiple zone mode C. multiple context mode D. transparent mode Suggested Answer: C
What is managed by Cisco Security Manager? A. Cisco WLC B. Cisco ESA C. Cisco WSA D. Cisco ASA Suggested Answer: D
An organization is trying to improve their Defense in Depth by blocking malicious destinations prior to a connection being established. The solution must be able to block certain applications from being used within the network. Which product should be used to accomplish this goal? A. Cisco Firepower B. Cisco Umbrella C. Cisco ISE D. Cisco AMP Suggested Answer: A
An engineer notices traffic interruptions on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network. What must be configured, based on a predefined threshold, to address this issue? A. Storm Control B. embedded event monitoring C. access control lists D. Bridge Protocol Data Unit guard Suggested Answer: A
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs? A. Multiple NetFlow collectors are supported. B. Advanced NetFlow v9 templates and legacy v5 formatting are supported. C. Secure NetFlow connectors are optimized for Cisco Prime Infrastructure D. Flow-create events are delayed. Suggested Answer: A
What is a key difference between Cisco Firepower and Cisco ASA? A. Cisco Firepower provides identity based access control while Cisco ASA does not. B. Cisco AS provides access control while Cisco Firepower does not. C. Cisco ASA provides SSL inspection while Cisco Firepower does not. D. Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA does not. Suggested Answer: D
DRAG DROP - Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right. Select and Place:Suggested Answer:
What is a benefit of using Cisco FMC over Cisco ASDM? A. Cisco FMC uses Java while Cisco ASDM uses HTML5. B. Cisco FMC provides centralized management while Cisco ASDM does not. C. Cisco FMC supports pushing configurations to devices while Cisco ASDM does not. D. Cisco FMC supports all firewall products whereas Cisco ASDM only supports Cisco ASA devices. Suggested Answer: B
Which product allows Cisco FMC to push security intelligence observable to its sensors from other products? A. Threat Intelligence Director B. Encrypted Traffic Analytics. C. Cognitive Threat Analytics. D. Cisco Talos Intelligence Suggested Answer: A
A Cisco FirePower administrator needs to configure a rule to allow a new application that has never been seen on the network. Which two actions should be selected to allow the traffic to pass without inspection? (Choose two.) A. permit B. allow C. reset D. trust E. monitor Suggested Answer: BD
What is a characteristic of a bridge group in a Cisco ASA Firewall running in transparent mode? A. It has an IP address on its BVI interface and is used for management traffic. B. It allows ARP traffic with a single access rule. C. It includes multiple interfaces and access rules between interfaces are customizable. D. It is a Layer 3 segment and includes one port and customizable access rules. Suggested Answer: C
While using Cisco Firepower's Security Intelligence policies, which two criteria is blocking based upon? (Choose two.) A. IP addresses B. URLs C. port numbers D. protocol IDs E. MAC addresses Suggested Answer: AB
What features does Cisco FTDv provide over Cisco ASAv? A. Cisco FTDv provides 1GB of firewall throughput while Cisco ASAv does not. B. Cisco FTDv runs on VMware while Cisco ASAv does not. C. Cisco FTDv runs on AWS while Cisco ASAv does not. D. Cisco FTDv supports URL filtering while Cisco ASAv does not. Suggested Answer: D Reference: https://www.ciscolive.com/c/dam/r/ciscolive/apjc/docs/2018/pdf/BRKSEC-2064.pdf
A network engineer is deciding whether to use stateful or stateless failover when configuring two Cisco ASAs for high availability. What is the connection status in both cases? A. need to be reestablished with stateful failover and preserved with stateless failover B. preserved with both stateful and stateless failover C. need to be reestablished with both stateful and stateless failover D. preserved with stateful failover and need to be reestablished with stateless failover Suggested Answer: D
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos? A. authoring B. consumption C. sharing D. analysis Suggested Answer: B
An administrator is configuring a DHCP server to better secure their environment. They need to be able to rate-limit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished? A. Set a trusted interface for the DHCP server. B. Set the DHCP snooping bit to 1. C. Enable ARP inspection for the required VLAN. D. Add entries in the DHCP snooping database. Suggested Answer: A
What is a prerequisite when integrating a Cisco ISE server and an AD domain? A. Configure a common administrator account. B. Place the Cisco ISE server and the AD server in the same subnet. C. Synchronize the clocks of the Cisco ISE server and the AD server. D. Configure a common DNS server. Suggested Answer: C Reference: https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/215233-identity-service-engine-ise-and-active.html#anc1
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256 cisc0383320506 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal? A. snmp-server host inside 10.255.254.1 snmpv3 andy B. snmp-server host inside 10.255.254.1 version 3 myv3 C. snmp-server host inside 10.255.254.1 snmpv3 myv3 D. snmp-server host inside 10.255.254.1 version 3 andy Suggested Answer: D Reference: https://www.cisco.com/c/m/en_us/techdoc/dc/reference/cli/nxos/commands/sm/snmp-server-host.html
An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA. Which Cisco ASA command must be used? A. flow exporterB. ip flow-export destination 1.1.1.1 2055 C. flow-export destination inside 1.1.1.1 2055 D. ip flow monitor input Suggested Answer: C Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/special/netflow/guide/asa_netflow.html
Which two tasks allow NetFlow on a Cisco ASA 5500 Series firewall? (Choose two.) A. Define a NetFlow collector by using the flow-export command B. Create a class map to match interesting traffic C. Create an ACL to allow UDP traffic on port 9996 D. Enable NetFlow Version 9 E. Apply NetFlow Exporter to the outside interface in the inbound direction Suggested Answer: AB
Refer to the exhibit. A network administrator configures command authorization for the admin5 user. What is the admin5 user able to do on HQ_Router after this configuration? A. set the IP address of an interface B. add subinterfaces C. complete no configurations D. complete all configurations Suggested Answer: C
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0383320506 address 0.0.0.0 command on host A. The tunnel is not being established to host B. What action is needed to authenticate the VPN? A. Change the password on host A to the default password B. Enter the command with a different password on host B C. Enter the same command on host B D. Change isakmp to ikev2 in the command on host A Suggested Answer: C
How many interfaces per bridge group does an ASA bridge group deployment support? A. up to 16 B. up to 2 C. up to 4 D. up to 8 Suggested Answer: C
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all users on that switch are unable to communicate with any destination. The network administrator checks the Interface status of all interfaces, and there is no err-disabled interface. What is causing this problem? A. DHCP snooping has not been enabled on all VLANs B. Dynamic ARP inspection has not been enabled on all VLANs C. The ip arp inspection limit command is applied on all interfaces and is blocking the traffic of all users D. The no ip arp inspection trust command is applied on all user host interfaces Suggested Answer: D
What is a difference between FlexVPN and DMVPN? A. DMVPN uses only IKEv1. FlexVPN uses only IKEv2 B. FlexVPN uses IKEv2. DMVPN uses IKEv1 or IKEv2 C. DMVPN uses IKEv1 or IKEv2. FlexVPN only uses IKEv1 D. FlexVPN uses IKEv1 or IKEv2. DMVPN uses only IKEv2 Suggested Answer: B
DRAG DROP - Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right. Select and Place:Suggested Answer:

An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization's public cloud to send telemetry using the cloud provider's mechanisms to a security device. Which mechanism should the engineer configure to accomplish this goal? A. sFlow B. NetFlow C. mirror port D. VPC flow logs Suggested Answer: D
An engineer is trying to securely connect to a router and wants to prevent insecure algorithms from being used. However, the connection is failing. Which action should be taken to accomplish this goal? A. Generate the RSA key using the crypto key generate rsa command. B. Configure the port using the ip ssh port 22 command. C. Enable the SSH server using the ip ssh server command. D. Disable telnet using the no ip telnet command. Suggested Answer: A
Refer to the exhibit. Which type of authentication is in use? A. POP3 authentication B. SMTP relay server authentication C. external user and relay mail authentication D. LDAP authentication for Microsoft Outlook Suggested Answer: D
Refer to the exhibit. An organization is using DHCP Snooping within their network. A user on VLAN 41 on a new switch is complaining that an IP address is not being obtained. Which command should be configured on the switch interface in order to provide the user with network connectivity? A. ip dhcp snooping limit 41 B. ip dhcp snooping verify mac-address C. ip dhcp snooping trust D. ip dhcp snooping vlan 41 Suggested Answer: C
Refer to the exhibit. Traffic is not passing through IPsec site-to-site VPN on the Firepower Threat Defense appliance. What is causing this issue? A. Site-to-site VPN preshared keys are mismatched. B. Site-to-site VPN peers are using different encryption algorithms. C. No split-tunnel policy is defined on the Firepower Threat Defense appliance. D. The access control policy is not allowing VPN traffic in. Suggested Answer: D
Refer to the exhibit. A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output? A. interesting traffic was not applied B. encryption algorithm mismatch C. authentication key mismatch D. hashing algorithm mismatch Suggested Answer: C
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment? A. group policy B. access control policy C. device management policy D. platform settings policy Suggested Answer: D Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/622/configuration/guide/fpmc-config-guide-v622/ platform_settings_policies_for_managed_devices.pdf
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the ASA be added on the Cisco UC Manager platform? A. Certificate Trust List B. Endpoint Trust List C. Enterprise Proxy Service D. Secured Collaboration Proxy Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/special/unified-communications/guide/unified-comm/unified-comm-tlsproxy.html
Which two application layer preprocessors are used by Firepower Next Generation Intrusion Prevention System? (Choose two.) A. SIP B. inline normalization C. SSL D. packet decoder E. modbus Suggested Answer: AC Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Application_Layer_Preprocessors.html
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center? A. quality of service B. time synchronization C. network address translations D. intrusion policy Suggested Answer: B
Which information is required when adding a device to Firepower Management Center? A. username and password B. encryption method C. device serial number D. registration key Suggested Answer: D Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Device_Management_Basics.html#ID-2242- 0000069d
What is a difference between an XSS attack and an SQL injection attack? A. SQL injection is a hacking method used to attack SQL databases, whereas XSS attack can exist in many different types of applications. B. XSS attacks are used to steal information from databases, whereas SQL injection attacks are used to redirect users to websites where attackers can steal data from them. C. XSS is a hacking method used to attack SQL databases, whereas SQL injection attacks can exist in many different types of applications. D. SQL injection attacks are used to steal information from databases, whereas XSS attacks are used to redirect users to websites where attackers can steal data from them. Suggested Answer: D
What is a difference between a DoS attack and DDos attack? A. A DoS attack is where a computer is used to flood a server with TCP packets, whereas DDoS attack is where a computer is used to flood a server with UDP packets. B. A DoS attack is where a computer is used to flood a server with UDP packets, whereas DDoS attack is where a computer is used to flood a server with TCP packets. C. A DoS attack is where a computer is used to flood a server with TCP and UDP packets, whereas DDoS attack is where a computer is used to flood multiple servers that are distributed over a LAN. D. A DoS attack is where a computer is used to flood a server with TCP and UDP packets, whereas DDoS attack is where multiple systems target a single system with a DoS attack. Suggested Answer: D
What are two advantages of using Cisco AnyConnect over DMVPN? (Choose two.) A. It provides spoke-to-spoke communications without traversing the hub. B. It enables VPN access for individual users from their machines. C. It allows multiple sites to connect to the data center. D. It allows different routing protocols to work over the tunnel. E. It allows customization of access policies based on user identity. Suggested Answer: BE Cisco Anyconnect is a Remote access VPN client based solution where users can install the client on their machines and can connect to the respective VPN devices (ASA/FTD/Router). In order to secure connectivity for Anyconnect Users, one can also create custom access policies to ensure proper conditions are met before access is granted to the VPN user.
What is the difference between a vulnerability and an exploit? A. A vulnerability is a weakness that can be exploited by an attacker. B. A vulnerability is a hypothetical event for an attacker to exploit. C. An exploit is a hypothetical event that causes a vulnerability in the network. D. An exploit is a weakness that can cause a vulnerability in the network. Suggested Answer: A Reference: https://debricked.com/blog/what-is-security-weakness/#:~:text=A%20vulnerability%20is%20a%20weakness,when%20it%20can%20be% 20exploited.&text=This%20is%20a%20%E2%80%9Ccommunity%2Ddeveloped,of%20common%20software%20security%20weaknesses%E2%80%9D .
What is the term for having information about threats and threat actors that helps mitigate harmful events that would otherwise compromise networks or systems? A. threat intelligence B. Indicators of Compromise C. trusted automated exchange D. The Exploit Database Suggested Answer: A Reference: https://en.wikipedia.org/wiki/Cyber_threat_intelligence
Refer to the exhibit. An engineer is implementing a certificate based VPN. What is the result of the existing configuration? A. Only an IKEv2 peer that has an OU certificate attribute set to MANGLER establishes an IKEv2 SA successfully. B. The OU of the IKEv2 peer certificate is used as the identity when matching an IKEv2 authorization policy. C. The OU of the IKEv2 peer certificate is set to MANGLER. D. The OU of the IKEv2 peer certificate is encrypted when the OU is set to MANGLER. Suggested Answer: B
Which kind of API that is used with Cisco DNA Center provisions SSIDs, QoS policies, and update software versions on switches? A. event B. intent C. integration D. multivendor Suggested Answer: B Cisco is moving towards intent based networking and DNA center is a new addition to the solution offerings from Cisco.
A network engineer needs to select a VPN type that provides the most stringent security, multiple security associations for the connections, and efficient VPN establishment with the least bandwidth consumption. Why should the engineer select either FlexVPN or DMVPN for this environment? A. DMVPN because it uses multiple SAs and FlexVPN does not. B. DMVPN because it supports IKEv2 and FlexVPN does not. C. FlexVPN because it supports IKEv2 and DMVPN does not. D. FlexVPN because it uses multiple SAs and DMVPN does not. Suggested Answer: D Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_ike2vpn/configuration/xe-16-12/sec-flex-vpn-xe-16-12-book/sec-cfg-flex-serv.html
Refer to the exhibit. Which command was used to generate this output and to show which ports are authenticating with dot1x or mab? A. show authentication registrations B. show authentication method C. show dot1x all D. show authentication sessions Suggested Answer: D
Refer to the exhibit. What does the number 15 represent in this configuration? A. privilege level for an authorized user to this router B. access list that identifies the SNMP devices that can access the router C. interval in seconds between SNMPv3 authentication attempts D. number of possible failed attempts until the SNMPv3 user is locked out Suggested Answer: B
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command? A. authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX B. authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX C. authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX D. secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX Suggested Answer: B Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/a1/sec-a1-cr-book/sec-cr-c4.html#wp6039879000
Which command enables 802.1X globally on a Cisco switch? A. dot1x system-auth-control B. dot1x pae authenticator C. authentication port-control auto D. aaa new-model Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/routers/nfvis/switch_command/b-nfvis-switch-command-reference/802_1x_commands.html
What is a characteristic of Dynamic ARP Inspection? A. DAI determines the validity of an ARP packet based on valid IP to MAC address bindings from the DHCP snooping binding database. B. In a typical network, make all ports as trusted except for the ports connecting to switches, which are untrusted. C. DAI associates a trust state with each switch. D. DAI intercepts all ARP requests and responses on trusted ports only. Suggested Answer: A
Which statement about IOS zone-based firewalls is true? A. An unassigned interface can communicate with assigned interfaces B. Only one interface can be assigned to a zone. C. An interface can be assigned to multiple zones. D. An interface can be assigned only to one zone. Suggested Answer: D Reference: https://www.cisco.com/c/en/us/support/docs/security/ios-firewall/98628-zone-design-guide.html
When wired 802.1X authentication is implemented, which two components are required? (Choose two.) A. authentication server: Cisco Identity Service Engine B. supplicant: Cisco AnyConnect ISE Posture module C. authenticator: Cisco Catalyst switch D. authenticator: Cisco Identity Services Engine E. authentication server: Cisco Prime Infrastructure Suggested Answer: AC Reference: https://www.lookingpoint.com/blog/ise-series-802.1x
Which SNMPv3 configuration must be used to support the strongest security possible? A. asa-host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv des ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy B. asa-host(config)#snmp-server group myv3 v3 noauth asa-host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy C. asa-host(config)#snmp-server group myv3 v3 noauth asa-host(config)#snmp-server user andy myv3 auth sha cisco priv 3des ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy D. asa-host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy Suggested Answer: D
Under which two circumstances is a CoA issued? (Choose two.) A. A new authentication rule was added to the policy on the Policy Service node. B. An endpoint is deleted on the Identity Service Engine server. C. A new Identity Source Sequence is created and referenced in the authentication policy. D. An endpoint is profiled for the first time. E. A new Identity Service Engine server is added to the deployment with the Administration persona. Suggested Answer: BD Reference: https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_prof_pol.html
Which ASA deployment mode can provide separation of management on a shared appliance? A. DMZ multiple zone mode B. transparent firewall mode C. multiple context mode D. routed mode Suggested Answer: C
Refer to the exhibit. Which command was used to display this output? A. show dot1x all B. show dot1x C. show dot1x all summary D. show dot1x interface gi1/0/12 Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/xe-3se/3850/sec-user-8021x-xe-3se-3850-book/config-ieee-802x- pba.html
What is a characteristic of Cisco ASA NetFlow v9 Secure Event Logging? A. It tracks flow-create, flow-teardown, and flow-denied events. B. It provides stateless IP flow tracking that exports all records of a specific flow. C. It tracks the flow continuously and provides updates every 10 seconds. D. Its events match all traffic classes in parallel. Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa92/configuration/general/asa-general-cli/monitor-nsel.html
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI? A. ASDM B. NetFlow C. API D. desktop client Suggested Answer: C
What is a function of 3DES in reference to cryptography? A. It encrypts traffic. B. It creates one-time use passwords. C. It hashes files. D. It generates private keys. Suggested Answer: A
Which two activities can be done using Cisco DNA Center? (Choose two.) A. DHCP B. design C. accounting D. DNS E. provision Suggested Answer: BE Reference: https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/dna-center/1-2-1/user_guide/ b_dnac_ug_1_2_1/b_dnac_ug_1_2_chapter_00.pdf
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also provides an option to specify HTTP/TFTP commands to perform file retrieval from the server? A. terminal B. selfsigned C. url D. profile Suggested Answer: D
Which type of API is being used when a security application notifies a controller within a software-defined network architecture about a specific security threat? A. southbound API B. westbound API C. eastbound API D. northbound API Suggested Answer: D
An organization has two machines hosting web applications. Machine 1 is vulnerable to SQL injection while machine 2 is vulnerable to buffer overflows. What action would allow the attacker to gain access to machine 1 but not machine 2? A. sniffing the packets between the two hosts B. sending continuous pings C. overflowing the buffer's memory D. inserting malicious commands into the database Suggested Answer: D
What is the function of SDN southbound API protocols? A. to allow for the static configuration of control plane applications B. to enable the controller to use REST C. to enable the controller to make changes D. to allow for the dynamic configuration of control plane applications Suggested Answer: C
DRAG DROP - Drag and drop the threats from the left onto examples of that threat on the right. Select and Place:Suggested Answer:
What is the difference between Cross-site Scripting and SQL Injection attacks? A. Cross-site Scripting is when executives in a corporation are attacked, whereas SQL Injection is when a database is manipulated. B. Cross-site Scripting is an attack where code is executed from the server side, whereas SQL Injection is an attack where code is executed from the client side. C. Cross-site Scripting is a brute force attack targeting remote sites, whereas SQL Injection is a social engineering attack. D. Cross-site Scripting is an attack where code is injected into a database, whereas SQL Injection is an attack where code is injected into a browser. Suggested Answer: B
DRAG DROP - Drag and drop the common security threats from the left onto the definitions on the right. Select and Place:Suggested Answer:
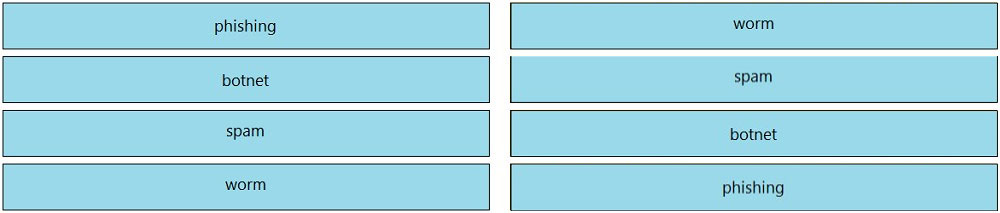
Which type of dashboard does Cisco DNA Center provide for complete control of the network? A. distributed management B. service management C. application management D. centralized management Suggested Answer: D
Refer to the exhibit. What will happen when this Python script is run? A. The list of computers, policies, and connector statuses will be received from Cisco AMP. B. The list of computers and their current vulnerabilities will be received from Cisco AMP. C. The compromised computers and malware trajectories will be received from Cisco AMP. D. The compromised computers and what compromised them will be received from Cisco AMP. Suggested Answer: A
Refer to the exhibit. What will happen when the Python script is executed? A. The hostname will be printed for the client in the client ID field. B. The hostname will be translated to an IP address and printed. C. The script will pull all computer hostnames and print them. D. The script will translate the IP address to FQDN and print it. Suggested Answer: C
With which components does a southbound API within a software-defined network architecture communicate? A. applications B. controllers within the network C. appliances D. devices such as routers and switches Suggested Answer: D
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to network resources? A. BYOD onboarding B. MAC authentication bypass C. client provisioning D. Simple Certificate Enrollment Protocol Suggested Answer: D
What are two characteristics of Cisco DNA Center APIs? (Choose two.) A. They are Cisco proprietary. B. They do not support Python scripts. C. They view the overall health of the network. D. They quickly provision new devices. E. Postman is required to utilize Cisco DNA Center API calls. Suggested Answer: CD
A company discovered an attack propagating through their network via a file. A custom file detection policy was created in order to track this in the future and ensure no other endpoints execute to infected file. In addition, it was discovered during testing that the scans are not detecting the file as an indicator of compromise. What must be done in order to ensure that the policy created is functioning as it should? A. Create an IP block list for the website from which the file was downloaded. B. Block the application that the file was using to open. C. Upload the hash for the file into the policy. D. Send the file to Cisco Threat Grid for dynamic analysis. Suggested Answer: C
Refer to the exhibit. What does the Python script accomplish? A. It authenticates to a Cisco ISE server using the username or ersad. B. It lists the LDAP users from the external identity store configured on Cisco ISE. C. It authenticates to a Cisco ISE with an SSH connection. D. It allows authentication with TLSv1 SSL protocol. Suggested Answer: A
What is a difference between GETVPN and IPsec? A. GETVPN is used to build a VPN network with multiple sites without having to statically configure all devices. B. GETVPN is based on IKEv2 and does not support IKEv1. C. GETVPN provides key management and security association management. D. GETVPN reduces latency and provides encryption over MPLS without the use of a central hub. Suggested Answer: D
Which algorithm provides asymmetric encryption? A. 3DES B. RC4 C. AES D. RSA Suggested Answer: D
How does DNS Tunneling exfiltrate data? A. An attacker registers a domain that a client connects to based on DNS records and sends malware through that connection. B. An attacker opens a reverse DNS shell to get into the client's system and install malware on it. C. An attacker sends an email to the target with hidden DNS resolvers in it to redirect them to a malicious domain. D. An attacker uses a non-standard DNS port to gain access to the organization's DNS servers in order to poison the resolutions. Suggested Answer: A
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system's applications. Which vulnerability allows the attacker to see the passwords being transmitted in clear text? A. unencrypted links for traffic B. weak passwords for authentication C. improper file security D. software bugs on applications Suggested Answer: A
A user has a device in the network that is receiving too many connection requests from multiple machines. Which type of attack is the device undergoing? A. SYN flood B. slowloris C. phishing D. pharming Suggested Answer: A
Which two preventive measures are used to control cross-site scripting? (Choose two.) A. Enable client-side scripts on a per-domain basis. B. Incorporate contextual output encoding/escaping. C. Disable cookie inspection in the HTML inspection engine. D. Run untrusted HTML input through an HTML sanitization engine. E. SameSite cookie attribute should not be used. Suggested Answer: BD
Which threat involves software being used to gain unauthorized access to a computer system? A. ping of death B. HTTP flood C. NTP amplification D. virus Suggested Answer: D
Which two capabilities does TAXII support? (Choose two.) A. exchange B. pull messaging C. binding D. correlation E. mitigating Suggested Answer: AB
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.) A. Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically. B. The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device. C. The IPsec configuration that is set up on the active device must be duplicated on the standby device. D. Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically. E. The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device. Suggested Answer: CE Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/15-mt/sec-vpn-availability-15-mt-book/sec-state-fail-ipsec.html
Which algorithm provides encryption and authentication for data plane communication? A. AES-GCM B. SHA-96 C. AES-256 D. SHA-384 Suggested Answer: A
DRAG DROP - Drag and drop the capabilities from the left onto the correct technologies on the right. Select and Place:Suggested Answer:
Which two key and block sizes are valid for AES? (Choose two.) A. 64-bit block size, 112-bit key length B. 64-bit block size, 168-bit key length C. 128-bit block size, 192-bit key length D. 128-bit block size, 256-bit key length E. 192-bit block size, 256-bit key length Suggested Answer: CD Reference: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Which two descriptions of AES encryption are true? (Choose two.) A. AES is less secure than 3DES. B. AES is more secure than 3DES. C. AES can use a 168-bit key for encryption. D. AES can use a 256-bit key for encryption. E. AES encrypts and decrypts a key three times in sequence. Suggested Answer: BD Reference: https://gpdb.docs.pivotal.io/43190/admin_guide/topics/ipsec.html
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol? A. STIX B. XMPP C. pxGrid D. SMTP Suggested Answer: A Reference: https://www.cisco.com/c/en/us/td/docs/security/web_security/scancenter/administrator/guide/b_ScanCenter_Administrator_Guide/ b_ScanCenter_Administrator_Guide_chapter_0100011.pdf
DRAG DROP - Drag and drop the descriptions from the left onto the correct protocol versions on the right. Select and Place:Suggested Answer:
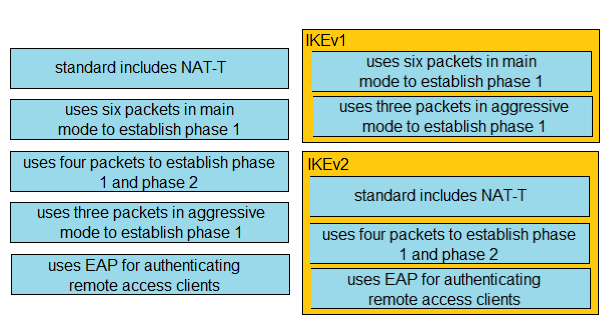
Which VPN technology can support a multivendor environment and secure traffic between sites? A. SSL VPN B. GET VPN C. FlexVPN D. DMVPN Suggested Answer: C Reference: https://www.cisco.com/c/en/us/products/collateral/routers/asr-1000-series-aggregation-services-routers/data_sheet_c78-704277.html
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity? A. DMVPN B. FlexVPN C. IPsec DVTI D. GET VPN Suggested Answer: D
What is a commonality between DMVPN and FlexVPN technologies? A. FlexVPN and DMVPN use the new key management protocol, IKEv2 B. FlexVPN and DMVPN use IS-IS routing protocol to communicate with spokes C. IOS routers run the same NHRP code for DMVPN and FlexVPN D. FlexVPN and DMVPN use the same hashing algorithms Suggested Answer: C Reference: https://packetpushers.net/cisco-flexvpn-dmvpn-high-level-design/#:~:text=In%20its%20essence%2C%20FlexVPN%20is,both%20are%20Cisco's% 20proprietary%20technologies .
Which protocol provides the strongest throughput performance when using Cisco AnyConnect VPN? A. DTLSv1 B. TLSv1 C. TLSv1.1 D. TLSv1.2 Suggested Answer: A Reference: https://www.cisco.com/c/en/us/support/docs/security/anyconnect-secure-mobility-client/215331-anyconnect-implementation-and-performanc.html
Which group within Cisco writes and publishes a weekly newsletter to help cybersecurity professionals remain aware of the ongoing and most prevalent threats? A. Talos B. PSIRT C. SCIRT D. DEVNET Suggested Answer: A
When Cisco and other industry organizations publish and inform users of known security findings and vulnerabilities, which name is used? A. Common Vulnerabilities, Exploits and Threats B. Common Vulnerabilities and Exposures C. Common Exploits and Vulnerabilities D. Common Security Exploits Suggested Answer: B
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two.) A. accounting B. assurance C. automation D. authentication E. encryption Suggested Answer: BC Reference: https://www.cisco.com/c/en/us/products/cloud-systems-management/dna-center/index.html
Which functions of an SDN architecture require southbound APIs to enable communication? A. SDN controller and the network elements B. management console and the SDN controller C. management console and the cloud D. SDN controller and the cloud Suggested Answer: A
Which two request methods of REST API are valid on the Cisco ASA Platform? (Choose two.) A. put B. options C. get D. push E. connect Suggested Answer: AC Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/api/qsg-asa-api.html
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a network? A. SDN controller and the cloud B. management console and the SDN controller C. management console and the cloud D. SDN controller and the management solution Suggested Answer: D
What is a feature of the open platform capabilities of Cisco DNA Center? A. application adapters B. domain integration C. intent-based APIs D. automation adapters Suggested Answer: C
Refer to the exhibit. What does the API do when connected to a Cisco security appliance? A. create an SNMP pull mechanism for managing AMP B. gather network telemetry information from AMP for endpoints C. get the process and PID information from the computers in the network D. gather the network interface information about the computers AMP sees Suggested Answer: D
Which form of attack is launched using botnets? A. TCP flood B. DDOS C. DOS D. virus Suggested Answer: B
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed? A. smurf B. distributed denial of service C. cross-site scripting D. rootkit exploit Suggested Answer: C
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities? A. user input validation in a web page or web application B. Linux and Windows operating systems C. database D. web page images Suggested Answer: A Reference: https://tools.cisco.com/security/center/resources/sql_injection
What is the difference between deceptive phishing and spear phishing? A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role. B. A spear phishing campaign is aimed at a specific person versus a group of people. C. Spear phishing is when the attack is aimed at the C-level executives of an organization. D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage. Suggested Answer: B
Which two behavioral patterns characterize a ping of death attack? (Choose two.) A. The attack is fragmented into groups of 16 octets before transmission. B. The attack is fragmented into groups of 8 octets before transmission. C. Short synchronized bursts of traffic are used to disrupt TCP connections. D. Malformed packets are used to crash systems. E. Publicly accessible DNS servers are typically used to execute the attack. Suggested Answer: BD Reference: https://en.wikipedia.org/wiki/Ping_of_death
Which two mechanisms are used to control phishing attacks? (Choose two.) A. Enable browser alerts for fraudulent websites. B. Define security group memberships. C. Revoke expired CRL of the websites. D. Use antispyware software. E. Implement email filtering techniques. Suggested Answer: AE
Which attack is commonly associated with C and C++ programming languages? A. cross-site scripting B. water holing C. DDoS D. buffer overflow Suggested Answer: D Reference: https://en.wikipedia.org/wiki/Buffer_overflow
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two.) A. Check integer, float, or Boolean string parameters to ensure accurate values. B. Use prepared statements and parameterized queries. C. Secure the connection between the web and the app tier. D. Write SQL code instead of using object-relational mapping libraries. E. Block SQL code execution in the web application database login. Suggested Answer: AB Reference: https://en.wikipedia.org/wiki/SQL_injection
Which two kinds of attacks are prevented by multifactor authentication? (Choose two.) A. phishing B. brute force C. man-in-the-middle D. DDOS E. tear drop Suggested Answer: AB
What are two rootkit types? (Choose two.) A. registry B. buffer mode C. user mode D. bootloader E. virtual Suggested Answer: CD
How is DNS tunneling used to exfiltrate data out of a corporate network? A. It leverages the DNS server by permitting recursive lookups to spread the attack to other DNS servers B. It encodes the payload with random characters that are broken into short strings and the DNS server rebuilds the exfiltrated data C. It redirects DNS requests to a malicious server used to steal user credentials, which allows further damage and theft on the network D. It corrupts DNS servers by replacing the actual IP address with a rogue address to collect information or start other attacks Suggested Answer: B
Which type of attack is social engineering? A. trojan B. MITM C. phishing D. malware Suggested Answer: C
What are two DDoS attack categories? (Choose two.) A. protocol B. source-based C. database D. sequential E. volume-based Suggested Answer: AE
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other? A. man-in-the-middle B. LDAP injection C. insecure API D. cross-site scripting Suggested Answer: A
How does Cisco Advanced Phishing Protection protect users? A. It utilizes sensors that send messages securely. B. It uses machine learning and real-time behavior analytics. C. It validates the sender by using DKIM. D. It determines which identities are perceived by the sender. Suggested Answer: B