CS0-002 Practice Test Free – 50 Questions to Test Your Knowledge
Are you preparing for the CS0-002 certification exam? If so, taking a CS0-002 practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 50 free CS0-002 practice questions designed to help you test your skills and identify areas for improvement.
By taking a free CS0-002 practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
50 Free CS0-002 Practice Questions
Below, you will find 50 free CS0-002 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
A security analyst discovers the following firewall log entries during an incident:Which of the following is MOST likely occurring?
A. Banner grabbing
B. Port scanning
C. Beaconing
D. Data exfiltration
An analyst receives artifacts from a recent intrusion and is able to pull a domain, IP address, email address, and software version. Which of the following points of the Diamond Model of Intrusion Analysis does this intelligence represent?
A. Infrastructure
B. Capabilities
C. Adversary
D. Victims
A development team has asked users to conduct testing to ensure an application meets the needs of the business. Which of the following types of testing does this describe?
A. Acceptance testing
B. Stress testing
C. Regression testing
D. Penetration testing
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:Follow TCP stream:
Which of the following describes what has occurred?
A. The host attempted to download an application from utoftor.com.
B. The host downloaded an application from utoftor.com.
C. The host attempted to make a secure connection to utoftor.com.
D. The host rejected the connection from utoftor.com.
A security team implemented a SIEM as part of its security-monitoring program. There is a requirement to integrate a number of sources into the SIEM to provide better context relative to the events being processed. Which of the following BEST describes the result the security team hopes to accomplish by adding these sources?
A. Data enrichment
B. Continuous integration
C. Machine learning
D. Workflow orchestration
During an incident response procedure, a security analyst collects a hard drive to analyze a possible vector of compromise. There is a Linux swap partition on the hard drive that needs to be checked. Which of the following should the analyst use to extract human-readable content from the partition?
A. strings
B. head
C. fsstat
D. dd
A security analyst is revising a company's MFA policy to prohibit the use of short message service (SMS) tokens. The Chief Information Officer has questioned this decision and asked for justification. Which of the following should the analyst provide as justification for the new policy?
A. SMS relies on untrusted, third-party carrier networks.
B. SMS tokens are limited to eight numerical characters.
C. SMS is not supported on all handheld devices in use.
D. SMS is a cleartext protocol and does not support encryption.
Following a recent security breach, a company decides to investigate account usage to ensure privileged accounts are only being utilized during typical business hours. During the investigation, a security analyst determines an account was consistently utilized in the middle of the night. Which of the following actions should the analyst take NEXT?
A. Disable the privileged account.
B. Initiate the incident response plan.
C. Report the discrepancy to human resources.
D. Review the activity with the user.
An internally developed file-monitoring system identified the following excerpt as causing a program to crash often: char filedata[100]; fp = fopen(`access.log`, `r`); srtcopy (filedata, fp); printf (`%sn`, filedata); Which of the following should a security analyst recommend to fix the issue?
A. Open the access.log file in read/write mode.
B. Replace the strcpy function.
C. Perform input sanitization.
D. Increase the size of the file data butter.
An IT security analyst has received an email alert regarding a vulnerability within the new fleet of vehicles the company recently purchased. Which of the following attack vectors is the vulnerability MOST likely targeting?
A. SCADA
B. CAN bus
C. Modbus
D. IoT
Which of the following is the software development process by which function, usability, and scenarios are tested against a known set of base requirements?
A. Security regression testing
B. Code review
C. User acceptance testing
D. Stress testing
A security analyst is performing a Diamond Model analysis of an incident the company had last quarter. A potential benefit of this activity is that it can identify:
A. detection and prevention capabilities to improve.
B. which systems were exploited more frequently.
C. possible evidence that is missing during forensic analysis.
D. which analysts require more training.
E. the time spent by analysts on each of the incidents.
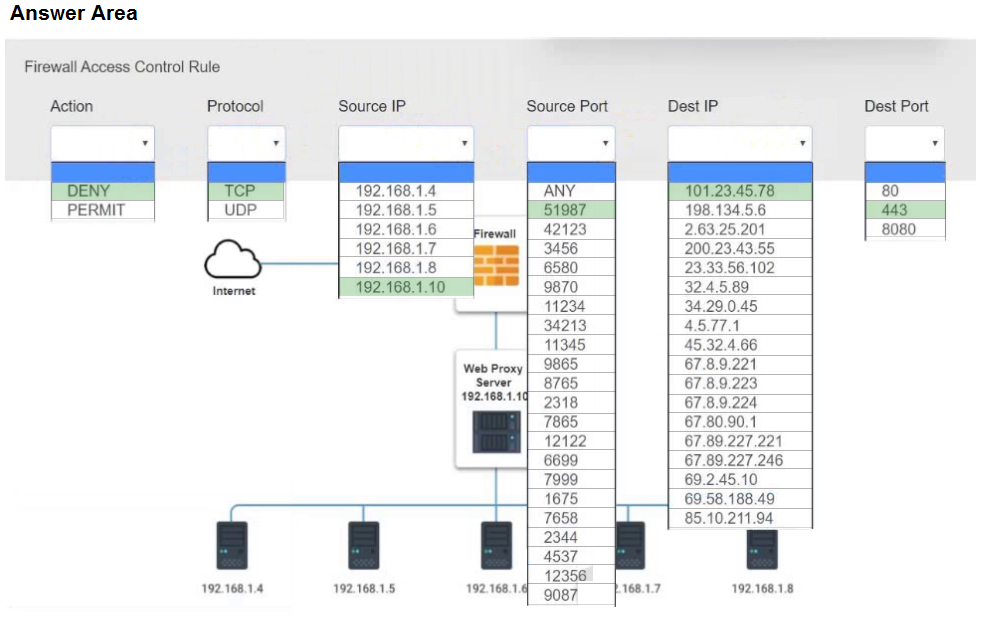
SIMULATION - You are a penetration tester who is reviewing the system hardening guidelines for a company's distribution center. The company's hardening guidelines indicate the following: ✑ There must be one primary server or service per device. ✑ Only default ports should be used. ✑ Non-secure protocols should be disabled. ✑ The corporate Internet presence should be placed in a protected subnet. INSTRUCTIONS - Using the tools available, discover devices on the corporate network and the services that are running on these devices. You must determine: ✑ The IP address of each device. ✑ The primary server or service of each device. ✑ The protocols that should be disabled based on the hardening guidelines. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.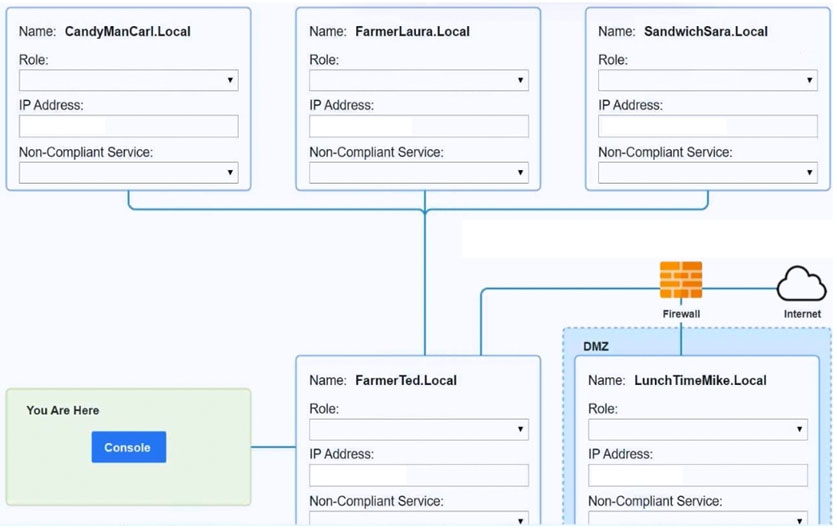
While reviewing incident reports from the previous night, a security analyst notices the corporate websites were defaced with political propaganda. Which of the following BEST describes this type of actor?
A. Hacktivist
B. Nation-state
C. Insider threat
D. Organized crime
A consultant is evaluating multiple threat intelligence feeds to assess potential risks for a client. Which of the following is the BEST approach for the consultant to consider when modeling the client's attack surface?
A. Ask for external scans from industry peers, look at the open ports, and compare information with the client.
B. Discuss potential tools the client can purchase to reduce the likelihood of an attack.
C. Look at attacks against similar industry peers and assess the probability of the same attacks happening.
D. Meet with the senior management team to determine if funding is available for recommended solutions.
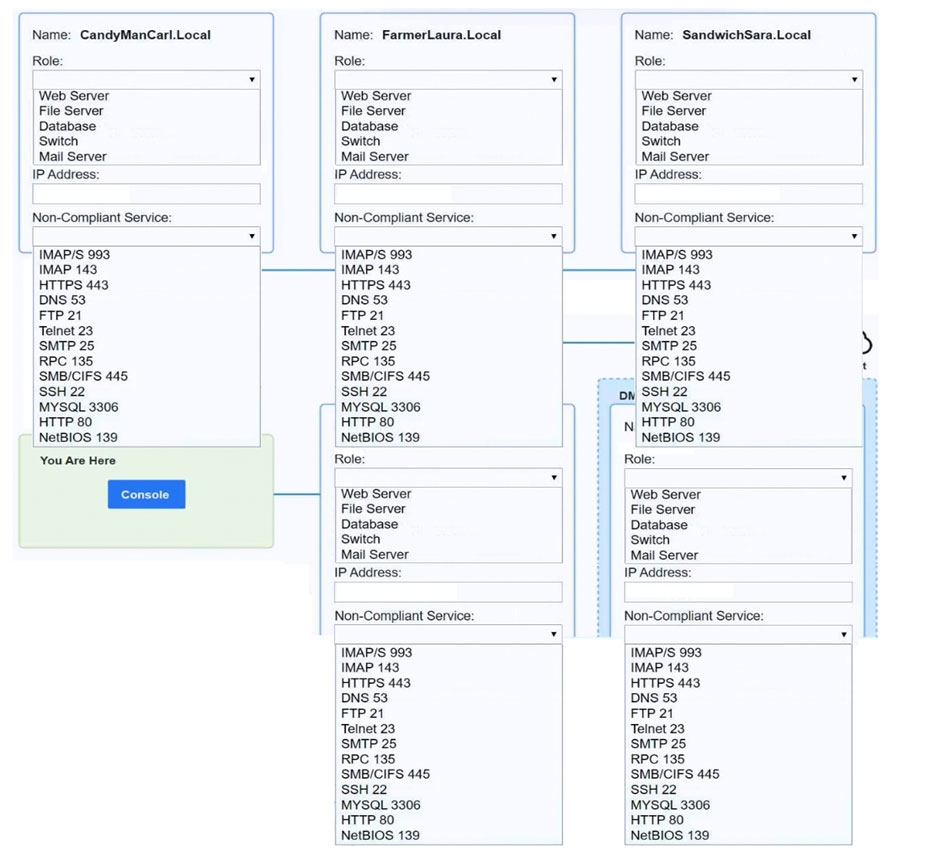
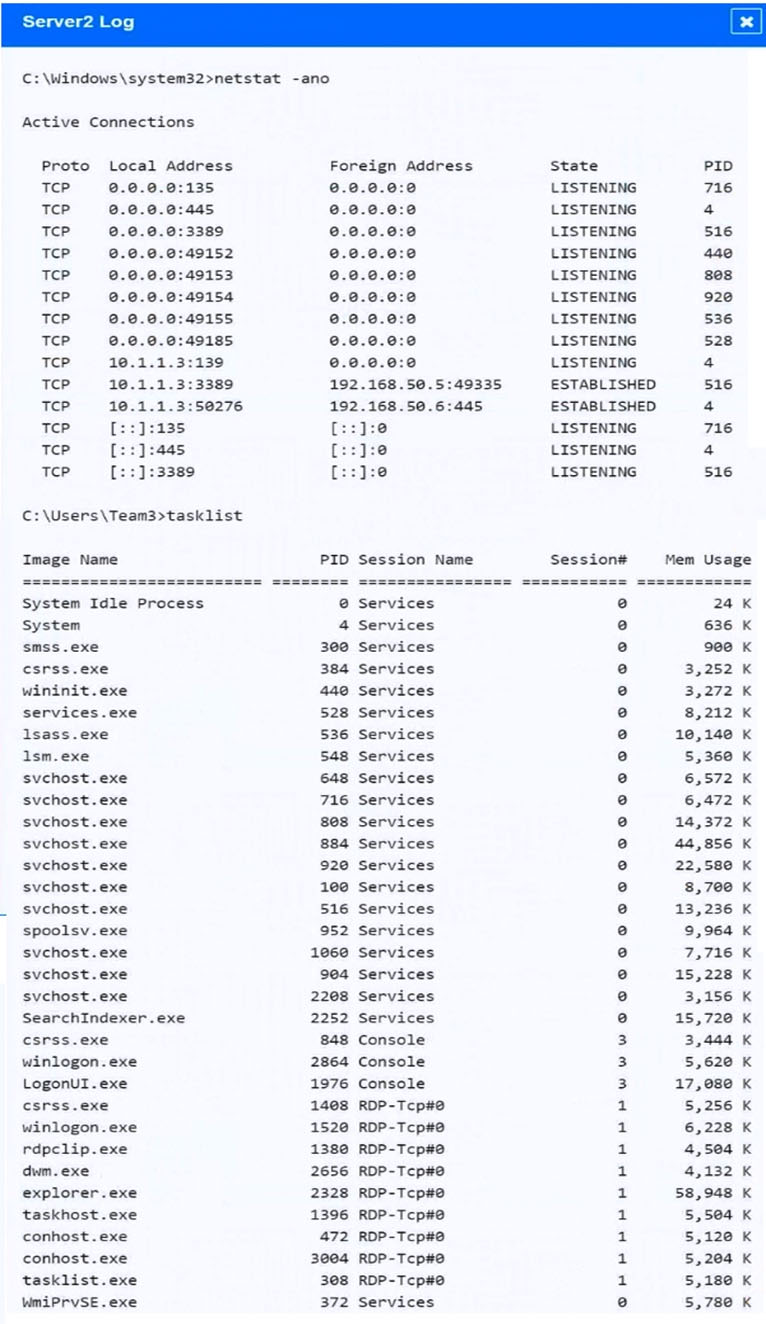
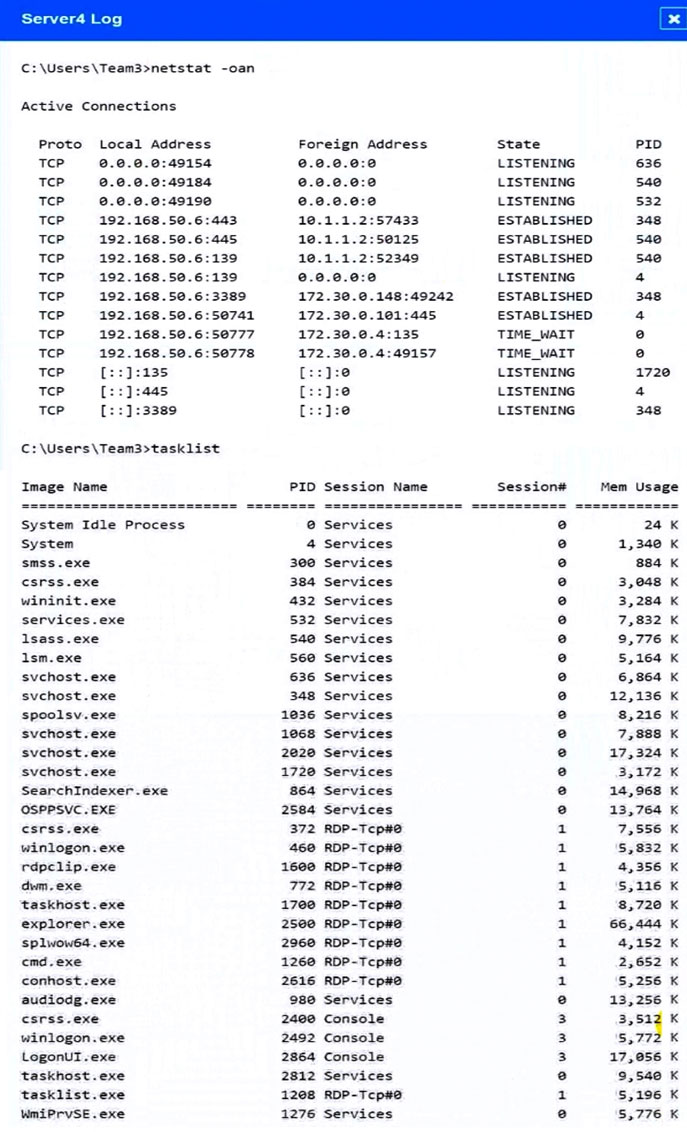
SIMULATION - Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. INSTRUCTIONS - Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.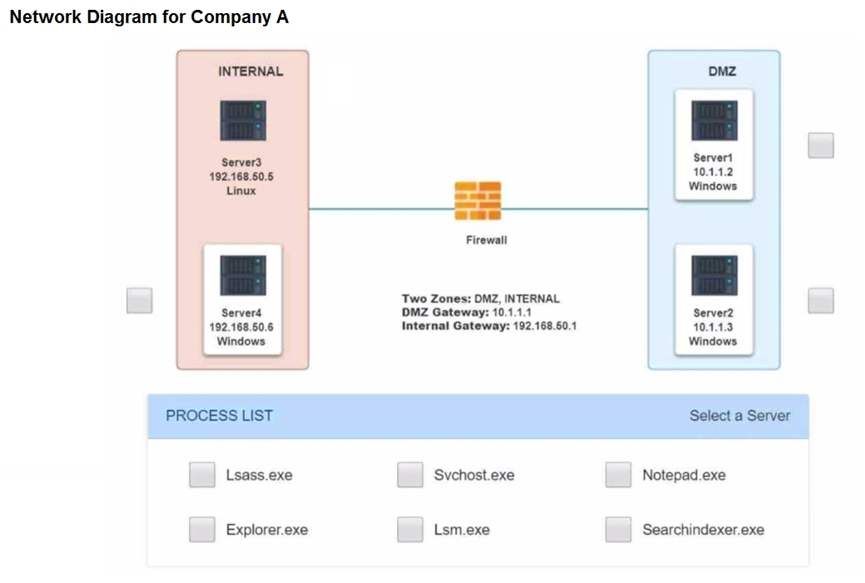
An organization is upgrading its network and all of its workstations. The project will occur in phases, with infrastructure upgrades each month and workstation installs every other week. The schedule should accommodate the enterprise-wide changes, while minimizing the impact to the network. Which of the following schedules BEST addresses these requirements?
A. Monthly vulnerability scans, biweekly topology scans, daily host discovery scans
B. Monthly topology scans, biweekly host discovery scans, monthly vulnerability scans
C. Monthly host discovery scans, biweekly vulnerability scans, monthly topology scans
D. Monthly topology scans, biweekly host discovery scans, weekly vulnerability scans
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:Which of the following ports should be closed?
A. 21
B. 80
C. 443
D. 1433
Which of the following is a difference between SOAR and SCAP?
A. SOAR can be executed faster and with fewer false positives than SCAP because of advanced heuristics.
B. SOAR has a wider breadth of capability using orchestration and automation, while SCAP is more limited in scope.
C. SOAR is less expensive because process and vulnerability remediation is more automated than what SCAP does.
D. SOAR eliminates the need for people to perform remediation, while SCAP relies heavily on security analysts.
A company's blocklist has outgrown the current technologies in place. The ACLs are at maximum, and the IPS signatures only allow a certain amount of space for domains to be added, creating the need for multiple signatures. Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
A. Implement a host-file-based solution that will use a list of all domains to deny for all machines on the network.
B. Create an IDS for the current blocklist to determine which domains are showing activity and may need to be removed.
C. Review the current blocklist and prioritize it based on the level of threat severity. Add the domains with the highest severity to the blocklist and remove the lower-severity threats from it.
D. Review the current blocklist to determine which domains can be removed from the list and then update the ACLs and IPS signatures.
A Chief Executive Officer (CEO) is concerned the company will be exposed to data sovereignty issues as a result of some new privacy regulations. To help mitigate this risk, the Chief Information Security Officer (CISO) wants to implement an appropriate technical control. Which of the following would meet the requirement?
A. Data masking procedures
B. Enhanced encryption functions
C. Regular business impact analysis functions
D. Geographic access requirements
While conducting a network infrastructure review, a security analyst discovers a laptop that is plugged into a core switch and hidden behind a desk. The analyst sees the following on the laptop's screen: [*] [NBT-NS] Poisoned answer sent to 192.169.23.115 for name FILE-SHARE-A (service: File Server) [*] [LLMNR] Poisoned answer sent to 192.168.23.115 for name FILE-SHARE-A [*] [LLMNR] Poisoned answer sent to 192.168.23.115 for name FILE-SHARE-A [SMBv2] NTLMv2-SSP Client : 192.168.23.115 [SMBv2] NTLMv2-SSP Username : CORPjsmith [SMBv2] NTLMv2-SSP Hash : F5DBF769CFEA7... [*] [NBT-NS] Poisoned answer sent to 192.169.23.24 for name FILE-SHARE-A (service: File Server) [*] [LLMNR] Poisoned answer sent to 192.168.23.24 for name FILE-SHARE-A [*] [LLMNR] Poisoned answer sent to 192.168.23.24 for name FILE-SHARE-A [SMBv2] NTLMv2-SSP Client : 192.168.23.24 [SMBv2] NTLMv2-SSP Username : CORPprogers [SMBv2] NTLMv2-SSP Hash : 6D093BE2FDD70A... Which of the following is the BEST action for the security analyst to take?
A. Force all users in the domain to change their passwords at the next login.
B. Disconnect the laptop and ask the users jsmith and progers to log out.
C. Take the FILE-SHARE-A server offline and scan it for viruses.
D. Initiate a scan of devices on the network to find password-cracking tools.
Which of the following is MOST dangerous to the client environment during a vulnerability assessment/penetration test?
A. There is a longer period of time to assess the environment.
B. The testing is outside the contractual scope.
C. There is a shorter period of time to assess the environment.
D. No status reports are included with the assessment.
A vulnerability assessment solution is hosted in the cloud. This solution will be used as an accurate inventory data source for both the configuration management database and the governance, risk, and compliance tool. An analyst has been asked to automate the data acquisition. Which of the following would be the BEST way to acquire the data?
A. CSV export
B. SOAR
C. API
D. Machine learning
A team of network security analysts is examining network traffic to determine if sensitive data was exfiltrated. Upon further investigation, the analysts believe confidential data was compromised. Which of the following capabilities would BEST defend against this type of sensitive data exfiltration?
A. Deploy an edge firewall.
B. Implement DLP.
C. Deploy EDR.
D. Encrypt the hard drives.
After a series of Group Policy Object updates, multiple services stopped functioning. The systems administrator believes the issue resulted from a Group Policy Object update but cannot validate which update caused the issue. Which of the following security solutions would resolve this issue?
A. Privilege management
B. Group Policy Object management
C. Change management
D. Asset management
A help desk technician inadvertently sent the credentials of the company's CRM in cleartext to an employee's personal email account. The technician then reset the employee's account using the appropriate process and the employee's corporate email, and notified the security team of the incident. According to the incident response procedure, which of the following should the security team do NEXT?
A. Contact the CRM vendor.
B. Prepare an incident summary report.
C. Perform postmortem data correlation.
D. Update the incident response plan.
A security analyst inspects the header of an email that is presumed to be malicious and sees the following:Which of the following is inconsistent with the rest of the header and should be treated as suspicious?
A. The use of a TLS cipher
B. The sender’s email address
C. The destination email server
D. The subject line
Which of the following organizational initiatives would be MOST impacted by data sovereignty issues?
A. Moving to a cloud-based environment
B. Migrating to locally hosted virtual servers
C. Implementing non-repudiation controls
D. Encrypting local database queries
A financial organization has offices located globally. Per the organization's policies and procedures, all executives who conduct business overseas must have their mobile devices checked for malicious software or evidence of tampering upon their return. The information security department oversees this process, and no executive has had a device compromised. The Chief Information Security Officer wants to implement an additional safeguard to protect the organization's data. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
A. Implement a mobile device wiping solution for use if a device is lost or stolen.
B. Install a DLP solution to track data flow.
C. Install an encryption solution on all mobile devices.
D. Train employees to report a lost or stolen laptop to the security department immediately.
A company's legal and accounting teams have decided it would be more cost-effective to offload the risks of data storage to a third party. The IT management team has decided to implement a cloud model and has asked the security team for recommendations. Which of the following will allow all data to be kept on the third-party network?
A. VDI
B. SaaS
C. CASB
D. FaaS
A software development team asked a security analyst to review some code for security vulnerabilities. Which of the following would BEST assist the security analyst while performing this task?
A. Static analysis
B. Dynamic analysis
C. Regression testing
D. User acceptance testing
In response to an audit finding, a company's Chief Information Officer (CIO) instructed the security department to increase the security posture of the vulnerability management program. Currently, the company's vulnerability management program has the following attributes: ✑ It is unauthenticated. ✑ It is at the minimum interval specified by the audit framework. ✑ It only scans well-known ports. Which of the following would BEST increase the security posture of the vulnerability management program?
A. Expand the ports being scanned to include all ports. Increase the scan interval to a number the business will accept without causing service interruption. Enable authentication and perform credentialed scans.
B. Expand the ports being scanned to include all ports. Keep the scan interval at its current level. Enable authentication and perform credentialed scans.
C. Expand the ports being scanned to include all ports. Increase the scan interval to a number the business will accept without causing service interruption. Continue unauthenticated scanning.
D. Continue scanning the well-known ports. Increase the scan interval to a number the business will accept without causing service interruption. Enable authentication and perform credentialed scans.
Which of the following are reasons why consumer IoT devices should be avoided in an enterprise environment? (Choose two.)
A. Message queuing telemetry transport does not support encryption.
B. The devices may have weak or known passwords.
C. The devices may cause a dramatic increase in wireless network traffic.
D. The devices may utilize unsecure network protocols.
E. Multiple devices may interfere with the functions of other IoT devices.
F. The devices are not compatible with TLS 1.2.
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's single Internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT department?
A. Require the guest machines to install the corporate-owned EDR solution
B. Configure NAC to only allow machines on the network that are patched and have active antivirus
C. Place a firewall in between the corporate network and the guest network
D. Configure the IPS with rules that will detect common malware signatures traveling from the guest network
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year. Below is the incident register for the organization:Which of the following should the organization consider investing in FIRST due to the potential impact of availability?
A. Hire a managed service provider to help with vulnerability management
B. Build a warm site in case of system outages
C. Invest in a failover and redundant system, as necessary
D. Hire additional staff for the IT department to assist with vulnerability management and log review
A company is experiencing a malware attack within its network. A security engineer notices many of the impacted assets are connecting outbound to a number of remote destinations and exfiltrating data. The security engineer also sees that deployed, up-to-date antivirus signatures are ineffective. Which of the following is the BEST approach to prevent any impact to the company from similar attacks in the future?
A. IDS signatures
B. Data loss prevention
C. Port security
D. Sinkholing
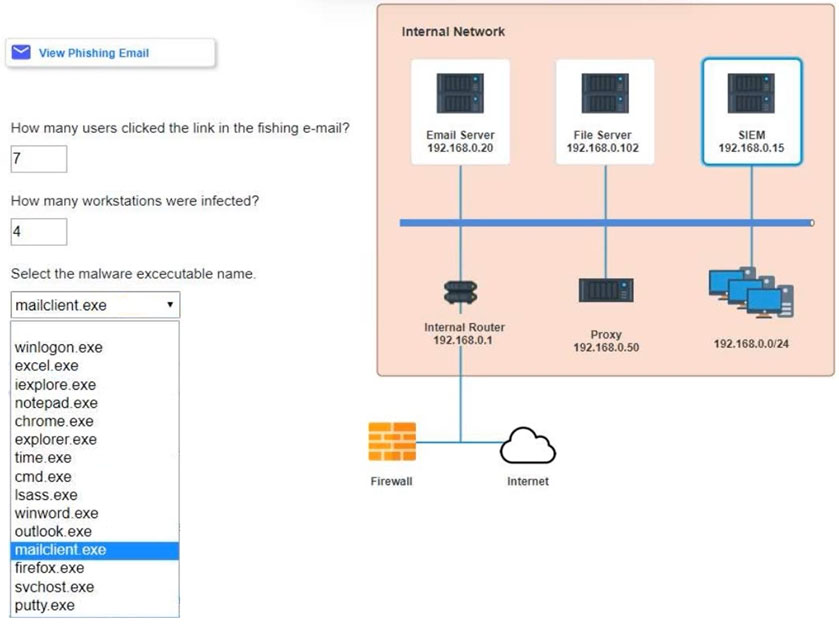
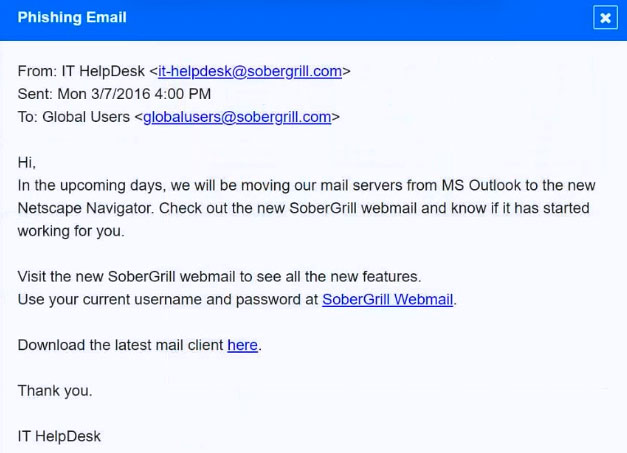
SIMULATION - Approximately 100 employees at your company have received a phishing email. As a security analyst, you have been tasked with handling this situation. INSTRUCTIONS - Review the information provided and determine the following: 1. How many employees clicked on the link in the phishing email? 2. On how many workstations was the malware installed? 3. What is the executable file name of the malware? If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.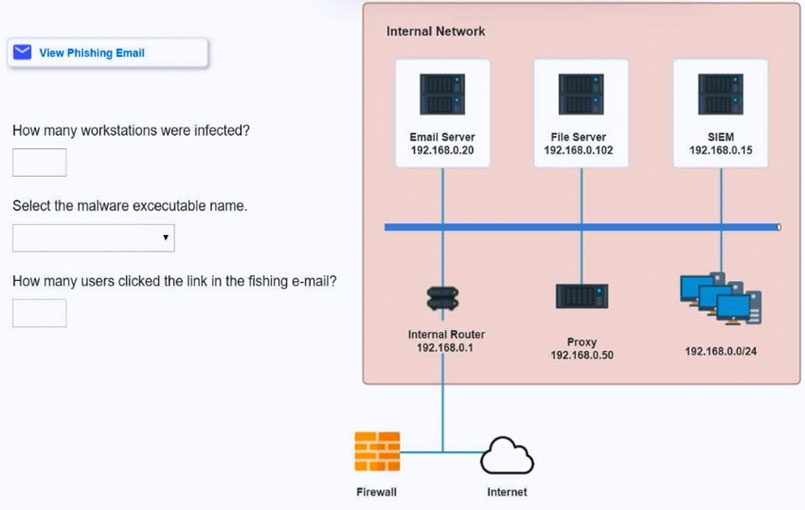
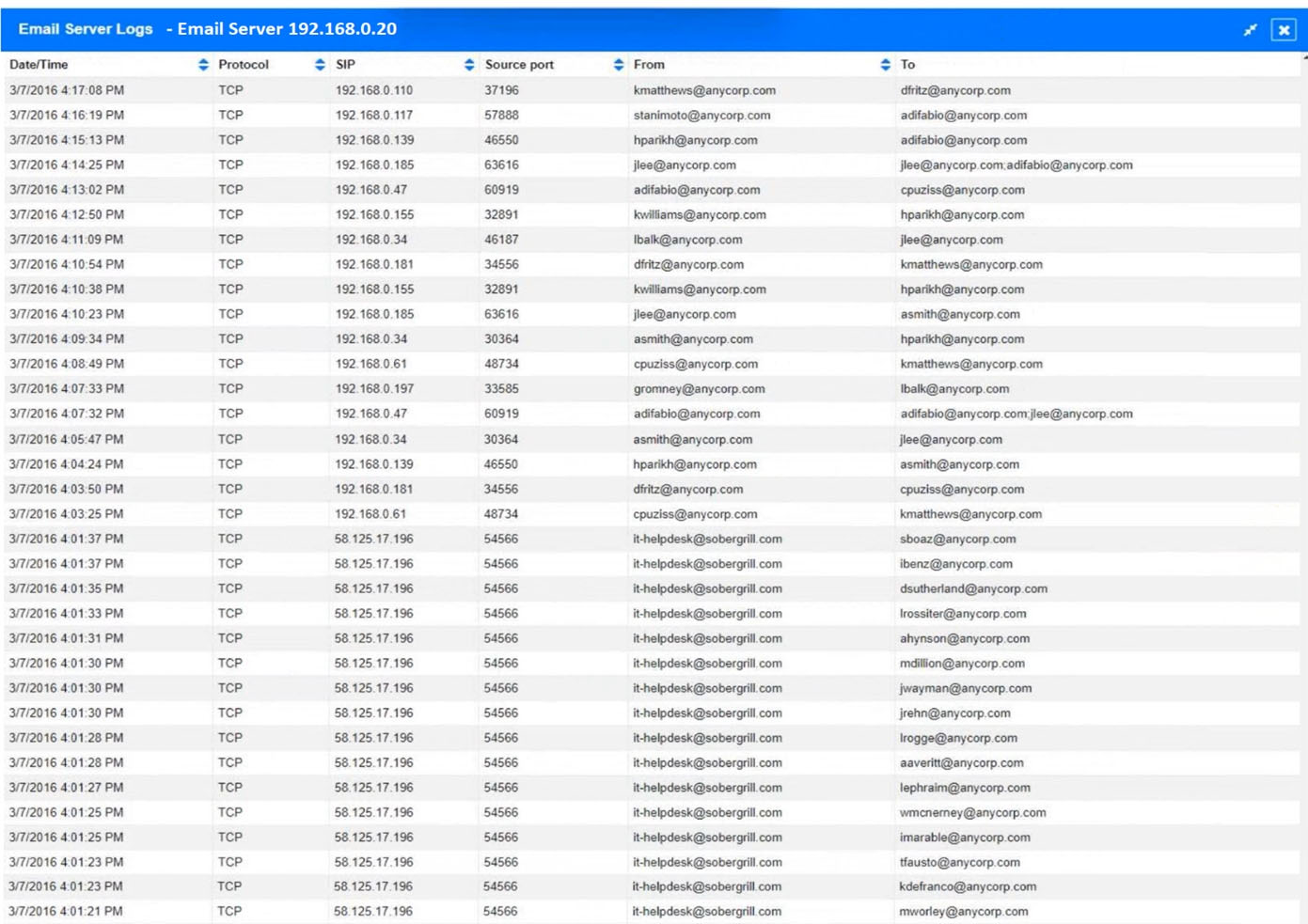
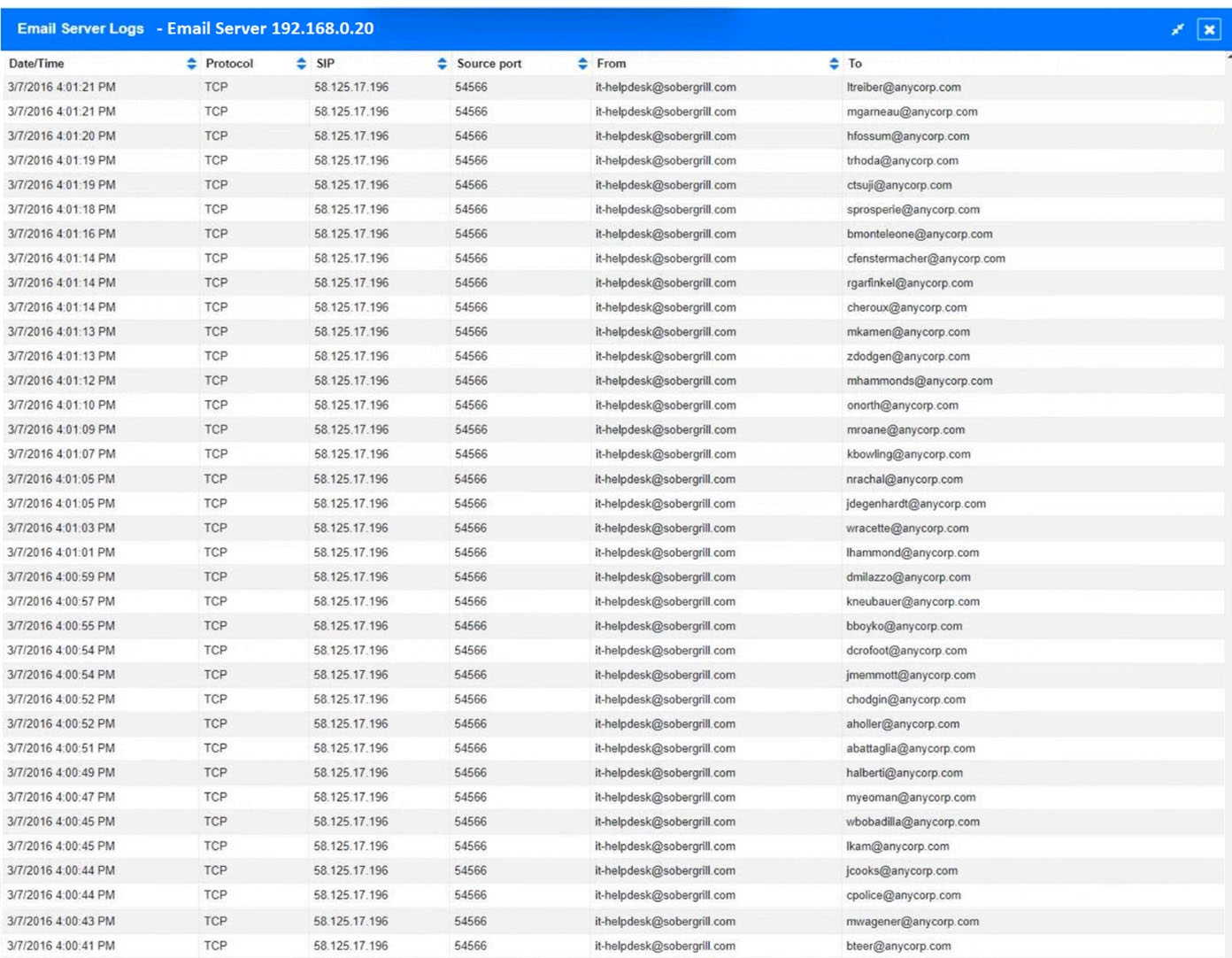
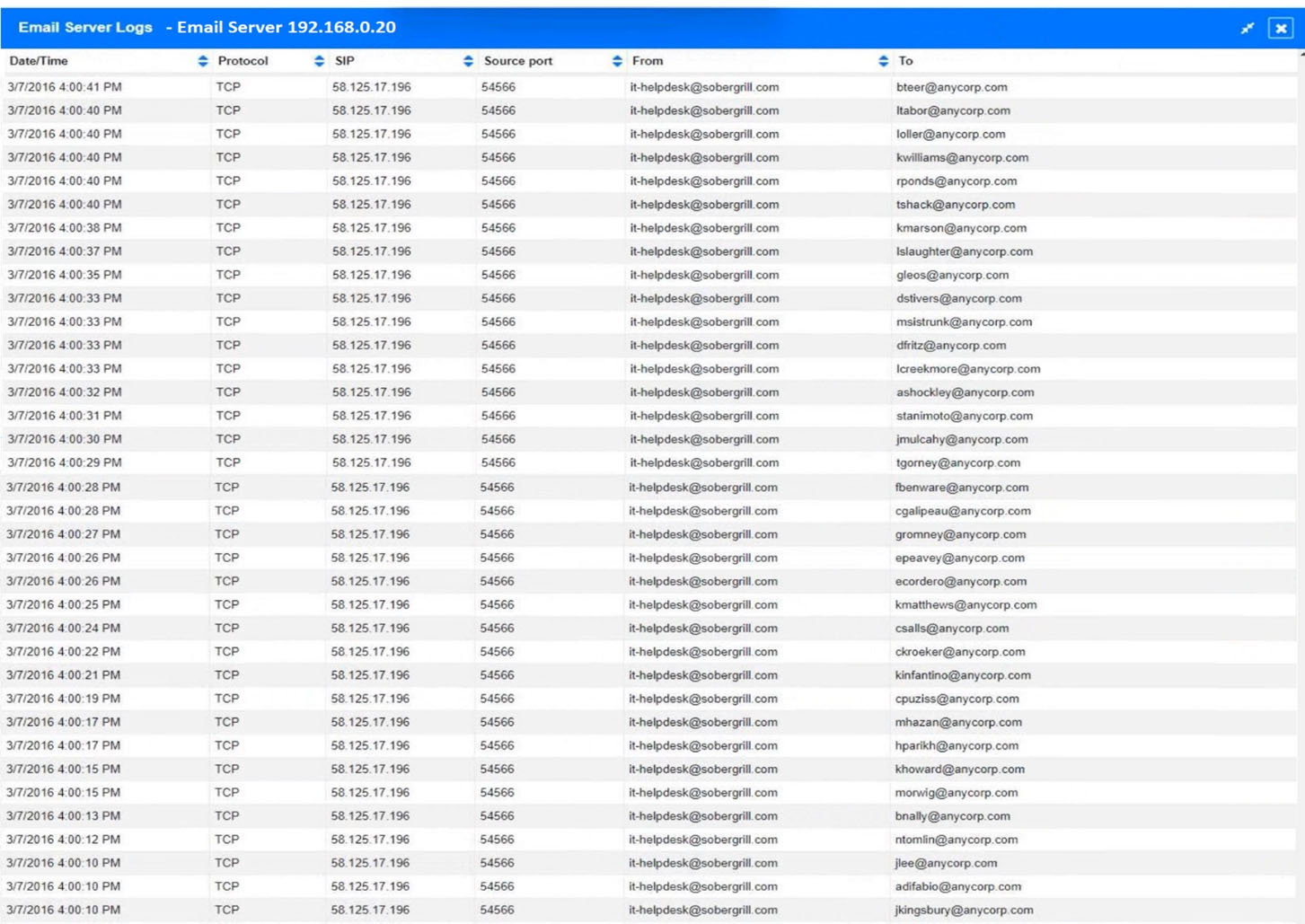
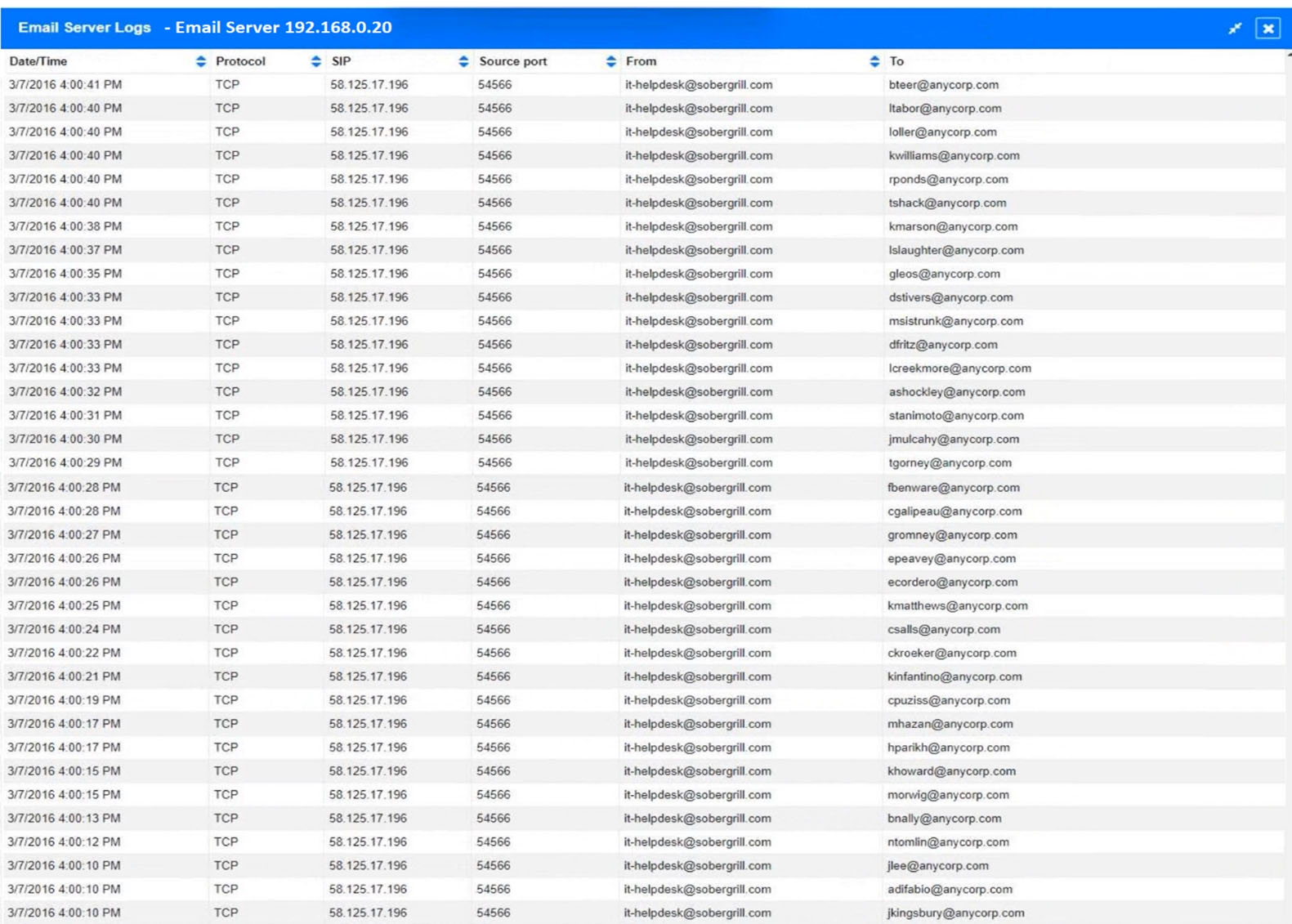

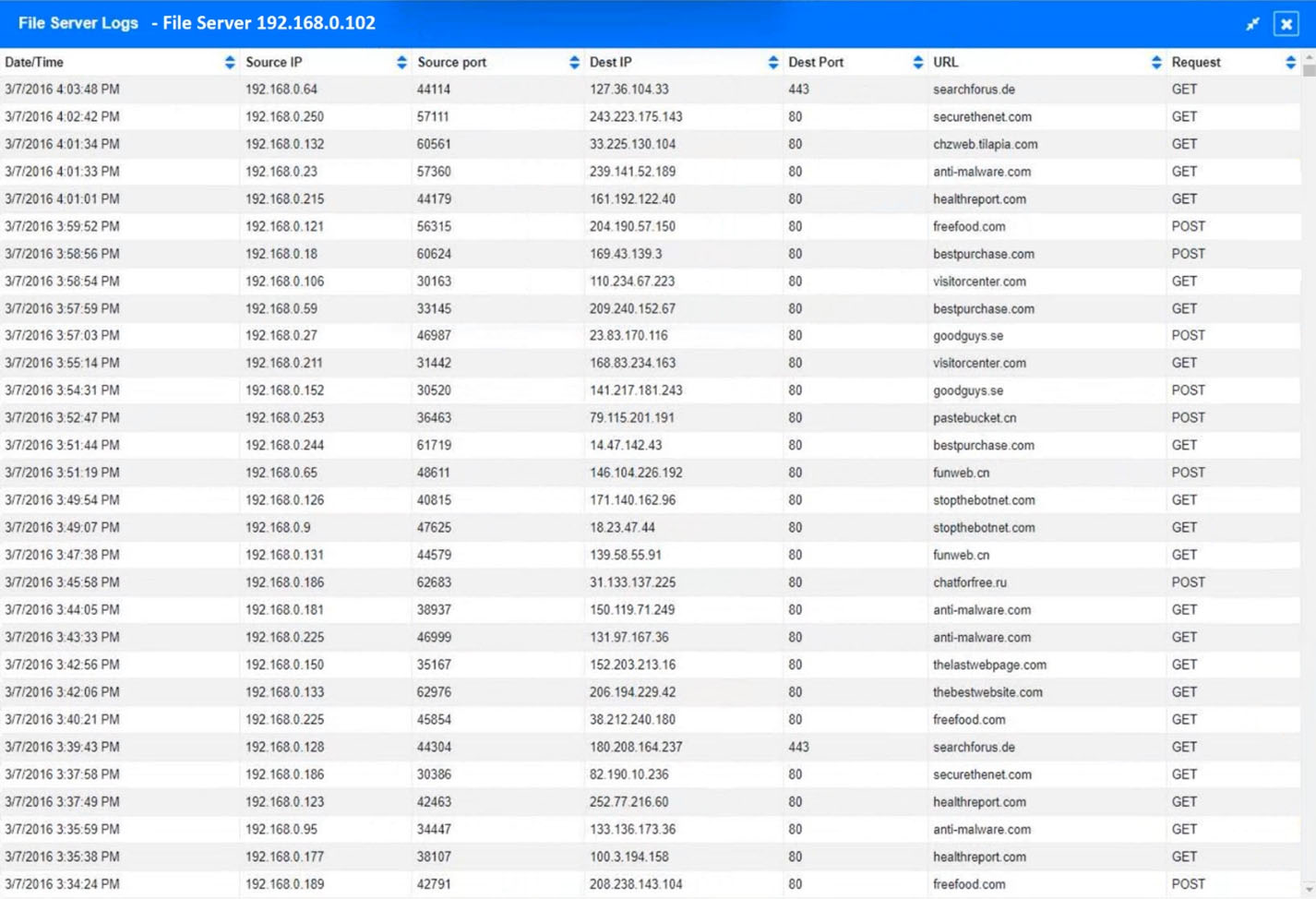
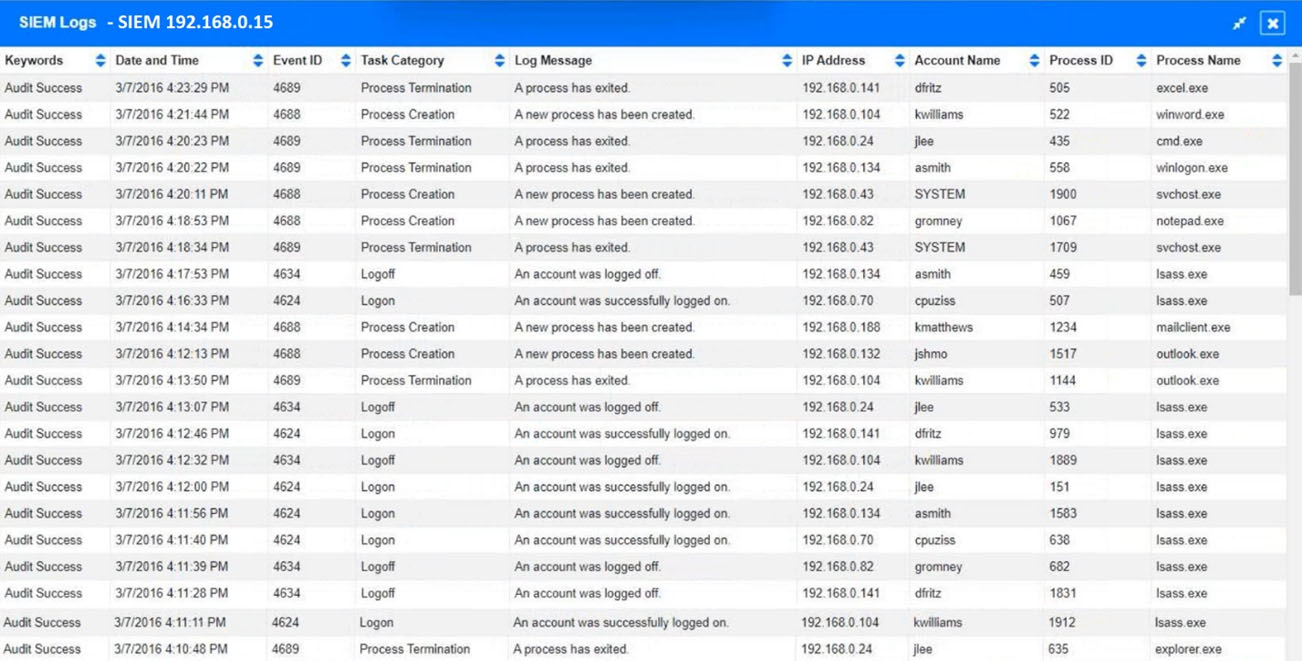
An organization recently discovered that spreadsheet files containing sensitive financial data were improperly stored on a web server. The management team wants to find out if any of these files were downloaded by public users accessing the server. The results should be written to a text file and should include the date, time, and IP address associated with any spreadsheet downloads. The web server's log file is named webserver.log, and the report file name should be accessreport.txt. Following is a sample of the web server's log file:Which of the following commands should be run if an analyst only wants to include entries in which a spreadsheet was successfully downloaded?
A. more webserver.log | grep *.xls > accessreport.txt
B. more webserver.log > grep ג€*xlsג€ | egrep ג€”E ‘success’ > accessreport.txt
C. more webserver.log | grep ג€”E ג€return=200 | xlsג€ > accessreport.txt
D. more webserver.log | grep ג€”A *.xls < accessreport.txt
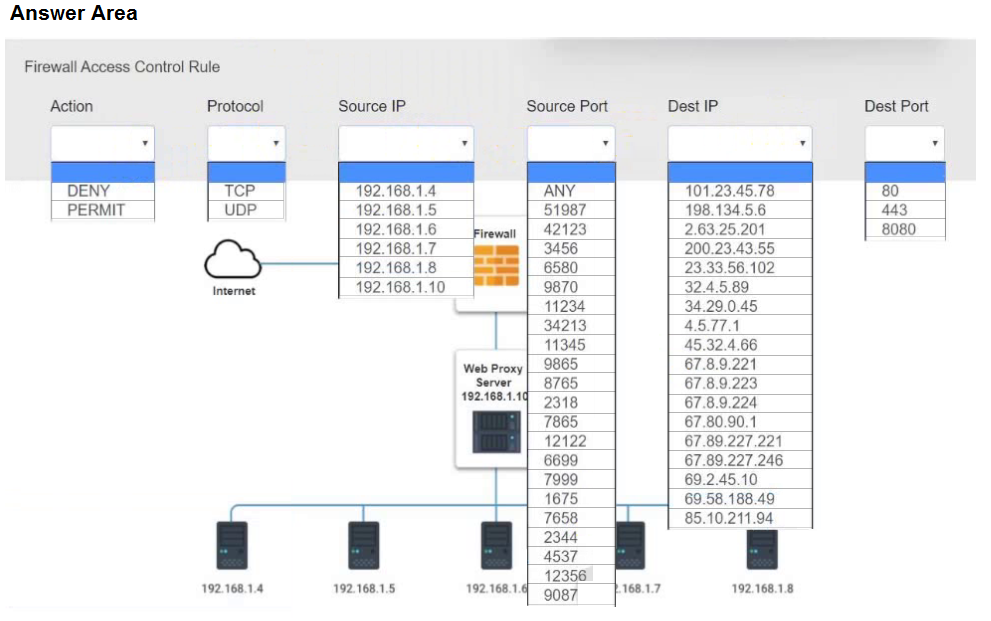
HOTSPOT - A security analyst suspects that a workstation may be beaconing to a command and control server. Inspect the logs from the company's web proxy server and the firewall to determine the best course of action to take in order to neutralize the threat with minimum impact to the organization. INSTRUCTIONS - Modify the Firewall Access Control rule to mitigate the issue. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.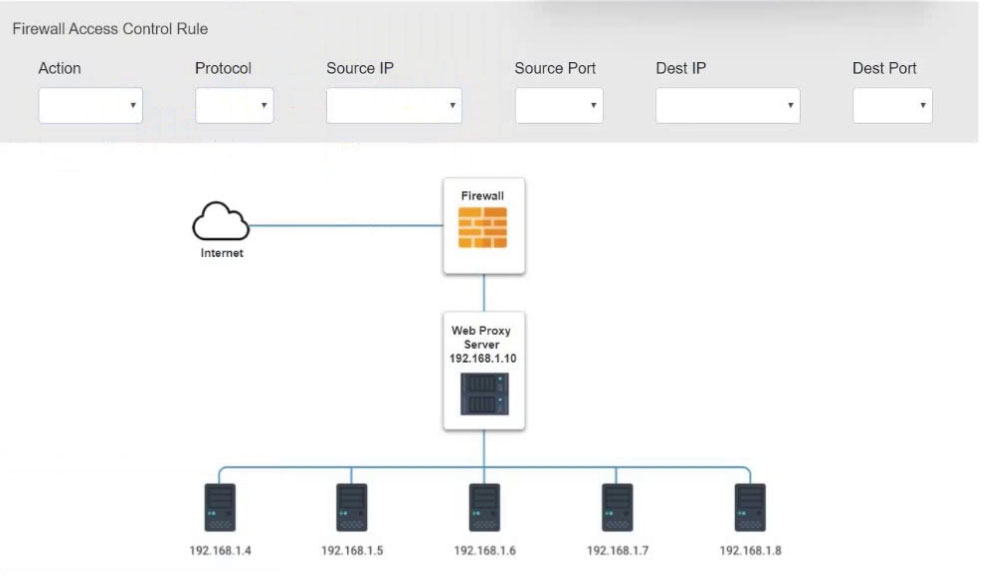

Hot Area:
Which of the following is MOST closely related to the concept of privacy?
A. The implementation of confidentiality, integrity, and availability
B. A system’s ability to protect the confidentiality of sensitive information
C. An individual’s control over personal information
D. A policy implementing strong identity management processes
An organization is adopting IoT devices at an increasing rate and will need to account for firmware updates in its vulnerability management programs. Despite the number of devices being deployed, the organization has only focused on software patches so far, leaving hardware-related weaknesses open to compromise. Which of the following best practices will help the organization to track and deploy trusted firmware updates as part of its vulnerability management programs?
A. Utilize threat intelligence to guide risk evaluation activities and implement critical updates after proper testing.
B. Apply all firmware updates as soon as they are released to mitigate the risk of compromise.
C. Sign up for vendor emails and create firmware update change plans for affected devices.
D. Implement an automated solution that detects when vendors release firmware updates and immediately deploy updates to production.
A small organization has proprietary software that is used internally. The system has not been well maintained and cannot be updated with the rest of the environment. Which of the following is the BEST solution?
A. Virtualize the system and decommission the physical machine.
B. Remove it from the network and require air gapping.
C. Implement privileged access management for identity access.
D. Implement MFA on the specific system.
Which of the following describes the main difference between supervised and unsupervised machine-learning algorithms that are used in cybersecurity applications?
A. Supervised algorithms can be used to block attacks, while unsupervised algorithms cannot.
B. Supervised algorithms require security analyst feedback, while unsupervised algorithms do not.
C. Unsupervised algorithms are not suitable for IDS systems, while supervised algorithms are.
D. Unsupervised algorithms produce more false positives than supervised algorithms.
A company has a cluster of web servers that is critical to the business. A systems administrator installed a utility to troubleshoot an issue, and the utility caused the entire cluster to go offline. Which of the following solutions would work BEST prevent to this from happening again?
A. Change management
B. Application whitelisting
C. Asset management
D. Privilege management
An analyst must review a new cloud-based SIEM solution. Which of the following should the analyst do FIRST prior to discussing the company's needs?
A. Check industry news feeds for product reviews.
B. Ensure a current non-disclosure agreement is on file.
C. Perform a vulnerability scan against a test instance.
D. Download the product security white paper.
Which of the following incident response components can identify who is the liaison between multiple lines of business and the public?
A. Red-team analysis
B. Escalation process and procedures
C. Triage and analysis
D. Communications plan
Which of the following sources will provide the MOST relevant threat intelligence data to the security team of a dental care network?
A. H-ISAC
B. Dental forums
C. Open threat exchange
D. Dark web chatter
Which of the following threat classifications would MOST likely use polymorphic code?
A. Known threat
B. Zero-day threat
C. Unknown threat
D. Advanced persistent threat
As part of an intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several domains and reputational information that suggest the company's employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for intelligence gathering?
A. Update the whitelist.
B. Develop a malware signature.
C. Sinkhole the domains.
D. Update the blacklist.
Get More CS0-002 Practice Questions
If you’re looking for more CS0-002 practice test free questions, click here to access the full CS0-002 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your CS0-002 certification journey!