PCCET Practice Test Free – 50 Questions to Test Your Knowledge
Are you preparing for the PCCET certification exam? If so, taking a PCCET practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 50 free PCCET practice questions designed to help you test your skills and identify areas for improvement.
By taking a free PCCET practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
50 Free PCCET Practice Questions
Below, you will find 50 free PCCET practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
A. connectors and interfaces
B. infrastructure and containers
C. containers and developers
D. data center and UPS
A native hypervisor runs:
A. with extreme demands on network throughput
B. only on certain platforms
C. within an operating system’s environment
D. directly on the host computer’s hardware
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
A. Dynamic
B. Pre-exploit protection
C. Bare-metal
D. Static
Which characteristic of serverless computing enables developers to quickly deploy application code?
A. Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
B. Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
C. Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
D. Using Container as a Service (CaaS) to deploy application containers to run their code.
Which key component is used to configure a static route?
A. router ID
B. enable setting
C. routing protocol
D. next hop IP address
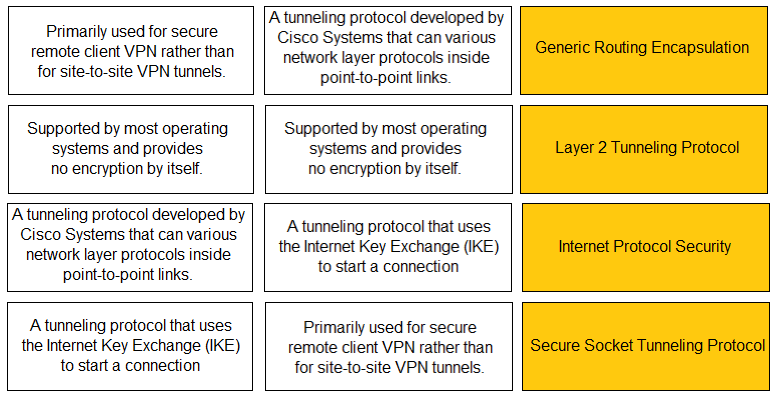
DRAG DROP - Match the description with the VPN technology. Select and Place:
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
A. Global Protect
B. WildFire
C. AutoFocus
D. STIX
Which technique changes protocols at random during a session?
A. use of non-standard ports
B. port hopping
C. hiding within SSL encryption
D. tunneling within commonly used services
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
A. control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
B. control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
C. control and protect inter-host traffic by using IPv4 addressing
D. control and protect inter-host traffic using physical network security appliances
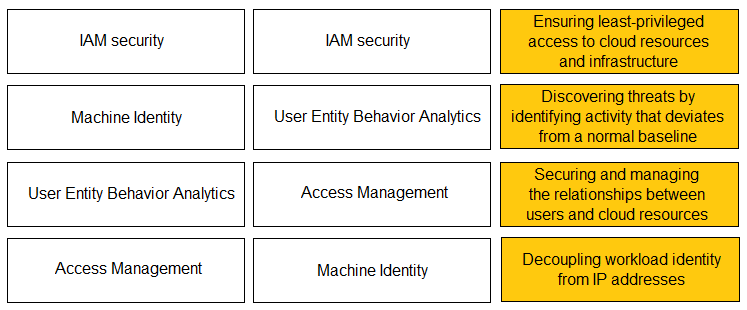
DRAG DROP - Match the Identity and Access Management (IAM) security control with the appropriate definition. Select and Place:
On an endpoint, which method should you use to secure applications against exploits?
A. endpoint-based firewall
B. strong user passwords
C. full-disk encryption
D. software patches
Which endpoint product from Palo Alto Networks can help with SOC visibility?
A. STIX
B. Cortex XDR
C. WildFire
D. AutoFocus
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
A. MineMeld
B. AutoFocus
C. WildFire
D. Cortex XDR
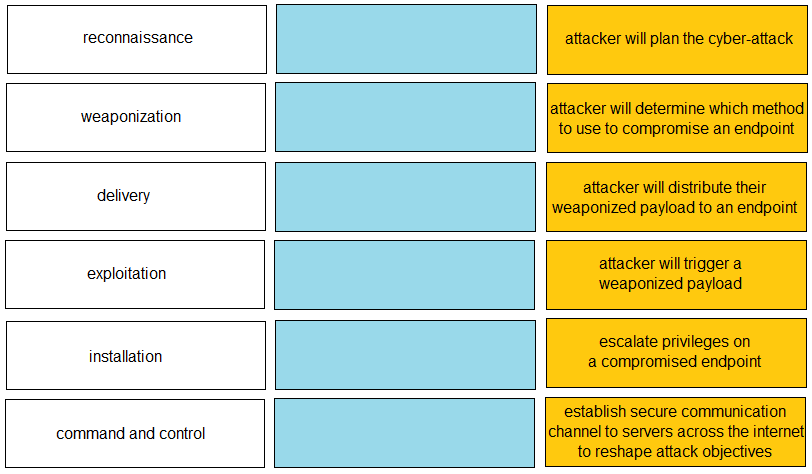
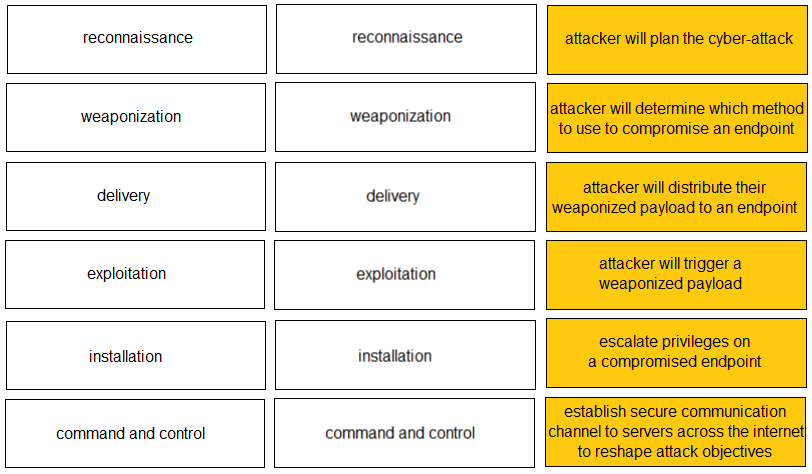
DRAG DROP - Given the graphic, match each stage of the cyber-attack lifecycle to its description.Select and Place:
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
A. NetOps
B. SecOps
C. SecDevOps
D. DevOps
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
A. North-South traffic
B. Intrazone traffic
C. East-West traffic
D. Interzone traffic
Which type of Wi-Fi attack depends on the victim initiating the connection?
A. Evil twin
B. Jasager
C. Parager
D. Mirai
Which endpoint tool or agent can enact behavior-based protection?
A. AutoFocus
B. Cortex XDR
C. DNS Security
D. MineMeld
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
A. Cortex XSOAR
B. Prisma Cloud
C. AutoFocus
D. Cortex XDR
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
A. weaponization
B. reconnaissance
C. exploitation
D. delivery
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
A. is hardened against cyber attacks
B. runs without any vulnerability issues
C. runs within an operating system
D. allows multiple, virtual (or guest) operating systems to run concurrently on a single physical host computer
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
A. DNS Security
B. URL Filtering
C. WildFire
D. Threat Prevention
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
A. an intranet-accessed contractor’s system that was compromised
B. exploitation of an unpatched security vulnerability
C. access by using a third-party vendor’s password
D. a phishing scheme that captured a database administrator’s password
Which TCP/IP sub-protocol operates at the Layer7 of the OSI model?
A. UDP
B. MAC
C. SNMP
D. NFS
Which IPsec feature allows device traffic to go directly to the Internet?
A. Split tunneling
B. Diffie-Hellman groups
C. d.Authentication Header (AH)
D. IKE Security Association
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
A. Shortest Path
B. Hop Count
C. Split Horizon
D. Path Vector
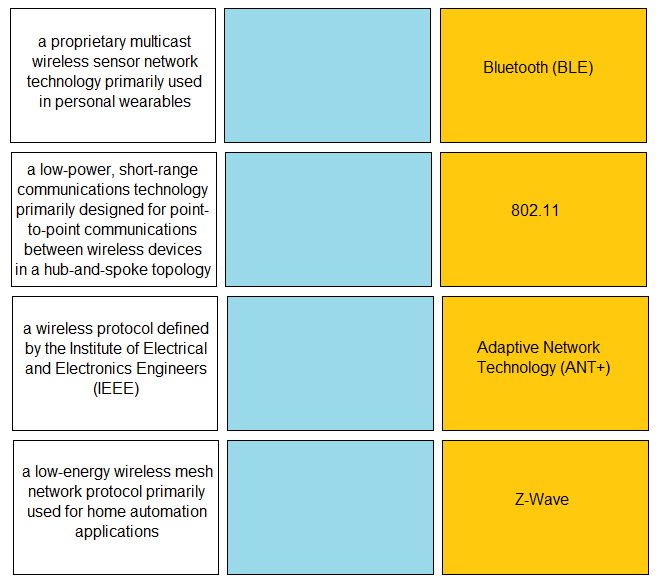
DRAG DROP - Match the IoT connectivity description with the technology. Select and Place:
Which option describes the `selective network security virtualization` phase of incrementally transforming data centers?
A. during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
B. during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
C. during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
D. during the selective network security virtualization phase, all intra-host traffic is load balanced
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
A. cybercriminals
B. state-affiliated groups
C. hacktivists
D. cyberterrorists
Which option is an example of a North-South traffic flow?
A. Lateral movement within a cloud or data center
B. An internal three-tier application
C. Client-server interactions that cross the edge perimeter
D. Traffic between an internal server and internal user
What does SIEM stand for?
A. Security Infosec and Event Management
B. Security Information and Event Management
C. Standard Installation and Event Media
D. Secure Infrastructure and Event Monitoring
Which core component is used to implement a Zero Trust architecture?
A. VPN Concentrator
B. Content Identification
C. Segmentation Platform
D. Web Application Zone
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
A. XDR
B. STEP
C. SOAR
D. SIEM
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
A. Frame
B. Segment
C. Packet
D. Data
Which activities do local organization security policies cover for a SaaS application?
A. how the data is backed up in one or more locations
B. how the application can be used
C. how the application processes the data
D. how the application can transit the Internet
Which tool supercharges security operations center (SOC) efficiency with the world's most comprehensive operating platform for enterprise security?
A. Prisma SAAS
B. WildFire
C. Cortex XDR
D. Cortex XSOAR
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next-generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
A. Threat Prevention
B. DNS Security
C. WildFire
D. URL Filtering
How does adopting a serverless model impact application development?
A. costs more to develop application code because it uses more compute resources
B. slows down the deployment of application code, but it improves the quality of code development
C. reduces the operational overhead necessary to deploy application code
D. prevents developers from focusing on just the application code because you need to provision the underlying infrastructure to run the code
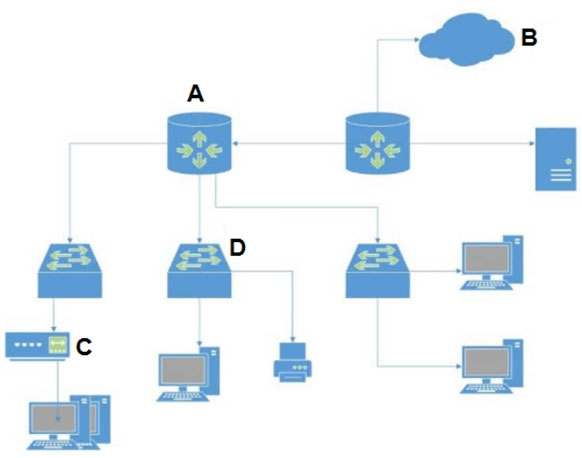
In the attached network diagram, which device is the switch?
A. A
B. B
C. C
D. D
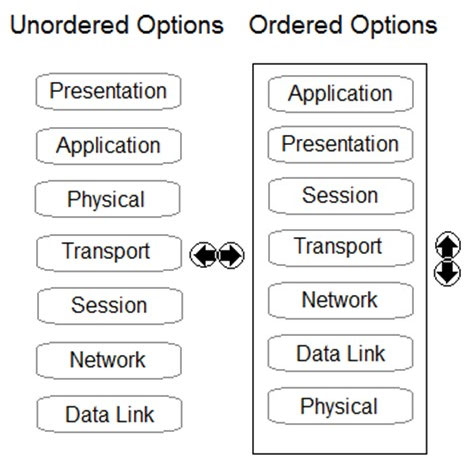
DRAG DROP - Order the OSI model with Layer7 at the top and Layer1 at the bottom. Select and Place:
Which subnet does the host 192.168.19.36/27 belong?
A. 192.168.19.0
B. 192.168.19.16
C. 192.168.19.64
D. 192.168.19.32
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
A. Group policy
B. Stateless
C. Stateful
D. Static packet-filter
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
A. Expedition
B. AutoFocus
C. MineMeld
D. Cortex XDR
DRAG DROP - Match each description to a Security Operating Platform key capability. Select and Place:
Which statement describes DevOps?
A. DevOps is its own separate team
B. DevOps is a set of tools that assists the Development and Operations teams throughout the software delivery process
C. DevOps is a combination of the Development and Operations teams
D. DevOps is a culture that unites the Development and Operations teams throughout the software delivery process
Which pillar of Prisma Cloud application security addresses ensuring that your cloud resources and SaaS applications are correctly configured?
A. visibility, governance, and compliance
B. network protection
C. dynamic computing
D. compute security
Which option is a Prisma Access security service?
A. Compute Security
B. Firewall as a Service (FWaaS)
C. Virtual Private Networks (VPNs)
D. Software-defined wide-area networks (SD-WANs)
What does Palo Alto Networks Cortex XDR do first when an endpoint is asked to run an executable?
A. run a static analysis
B. check its execution policy
C. send the executable to WildFire
D. run a dynamic analysis
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
A. operating system patches
B. full-disk encryption
C. periodic data backups
D. endpoint-based firewall
Which IoT connectivity technology is provided by satellites?
A. 4G/LTE
B. VLF
C. L-band
D. 2G/2.5G
Get More PCCET Practice Questions
If you’re looking for more PCCET practice test free questions, click here to access the full PCCET practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your PCCET certification journey!