SC-200 Practice Test Free – 50 Questions to Test Your Knowledge
Are you preparing for the SC-200 certification exam? If so, taking a SC-200 practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 50 free SC-200 practice questions designed to help you test your skills and identify areas for improvement.
By taking a free SC-200 practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
50 Free SC-200 Practice Questions
Below, you will find 50 free SC-200 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
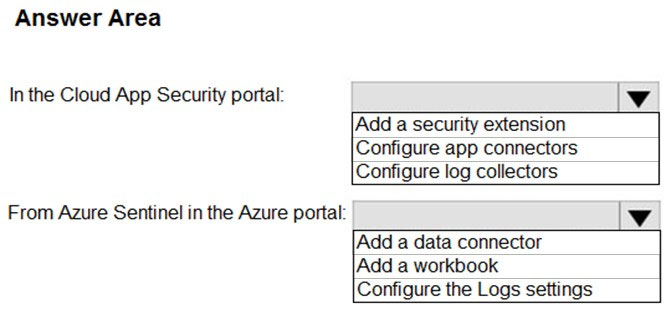
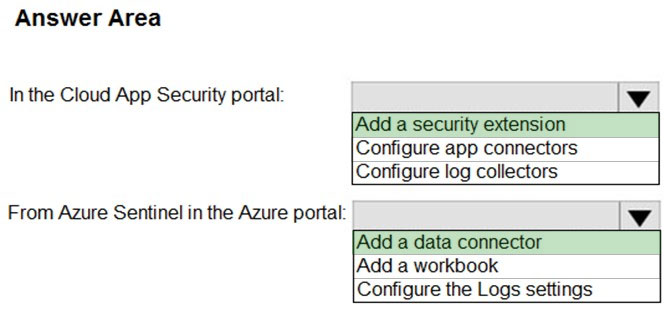
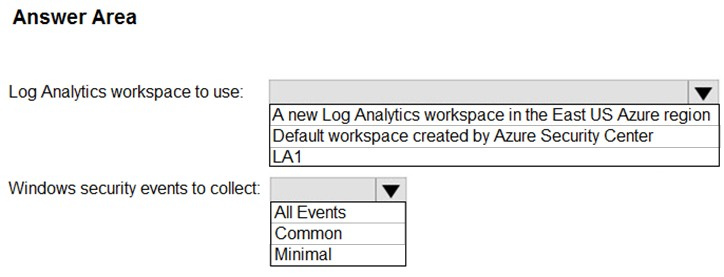
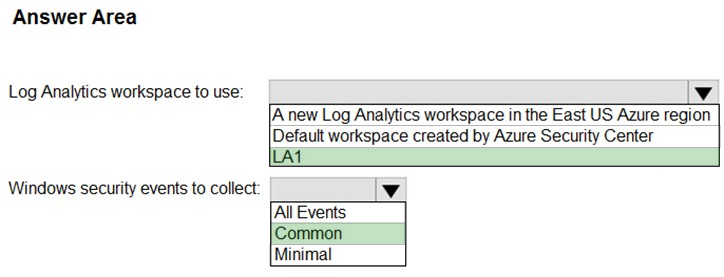
HOTSPOT - You need to configure the Azure Sentinel integration to meet the Azure Sentinel requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
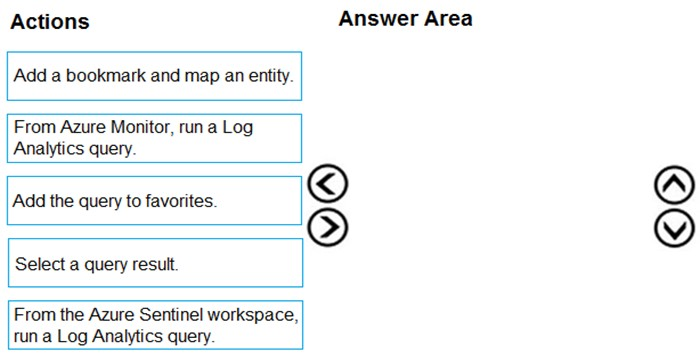
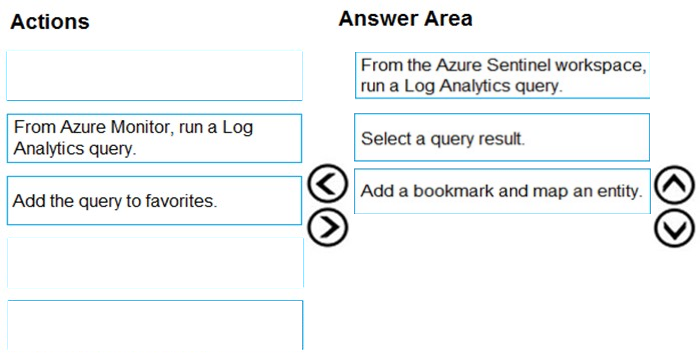
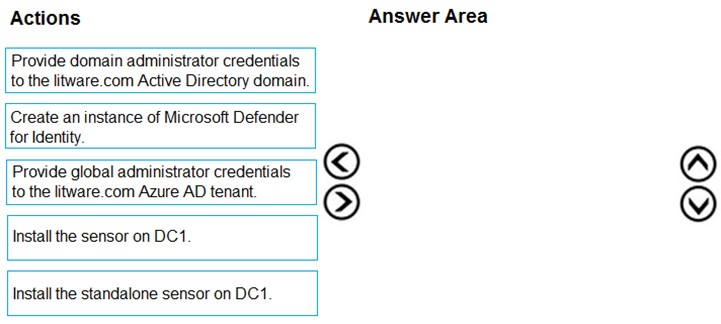
DRAG DROP - You need to add notes to the events to meet the Azure Sentinel requirements. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order. Select and Place:
You need to restrict cloud apps running on CLIENT1 to meet the Microsoft Defender for Endpoint requirements. Which two configurations should you modify? Each correct answer present part of the solution. NOTE: Each correct selection is worth one point.
A. the Onboarding settings from Device management in Microsoft Defender Security Center
B. Cloud App Security anomaly detection policies
C. Advanced features from Settings in Microsoft Defender Security Center
D. the Cloud Discovery settings in Cloud App Security
You have a playbook in Azure Sentinel. When you trigger the playbook, it sends an email to a distribution group. You need to modify the playbook to send the email to the owner of the resource instead of the distribution group. What should you do?
A. Add a parameter and modify the trigger.
B. Add a custom data connector and modify the trigger.
C. Add a condition and modify the action.
D. Add an alert and modify the action.
HOTSPOT - You have an Azure DevOps organization that contains an Azure Repos repository named Repo1 and is onboarded to Microsoft Defender for DevOps. You create infrastructure as code (IaC) files and store them in Repo1. The IaC files are formatted as Bicep files and Helm charts. You need to configure Defender for DevOps to identify misconfigurations in the IaC files. Which scanning tool should you use for each type of files? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to remediate active attacks to meet the technical requirements. What should you include in the solution?
A. Azure Automation runbooks
B. Azure Logic Apps
C. Azure Functions
D. Azure Sentinel livestreams
You have an Azure subscription that contains a resource group named RG1. RG1 contains a Microsoft Sentinel workspace. The subscription is linked to a Microsoft Entra tenant that contains a user named User1. You need to ensure that User1 can deploy and customize Microsoft Sentinel workbook templates. The solution must follow the principle of least privilege. Which role should you assign to User1 for RG1?
A. Microsoft Sentinel Contributor
B. Workbook Contributor
C. Microsoft Sentinel Automation Contributor
D. Contributor
You need to complete the query for failed sign-ins to meet the technical requirements. Where can you find the column name to complete the where clause?
A. Security alerts in Azure Security Center
B. Activity log in Azure
C. Azure Advisor
D. the query windows of the Log Analytics workspace
You have 500 on-premises Windows 11 devices that use Microsoft Defender for Endpoint. You enable Network device discovery. You need to create a hunting query that will identify discovered network devices and return the identity of the onboarded device that discovered each network device. Which built-in function should you use?
A. SeenBy()
B. DeviceFromIP()
C. next()
D. current_cluster_endpoint()
HOTSPOT - You need to create the analytics rule to meet the Azure Sentinel requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft Sentinel workspace that contains a custom workbook named Workbook1. You need to create a visual in Workbook1 that will display the logon count for accounts that have logon event IDs of 4624 and 4634. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Which rule setting should you configure to meet the Azure Sentinel requirements?
A. From Set rule logic, turn off suppression.
B. From Analytics rule details, configure the tactics.
C. From Set rule logic, map the entities.
D. From Analytics rule details, configure the severity.
HOTSPOT - You have a Microsoft Sentinel workspace that contains a custom workbook. You need to query for a summary of security events. The solution must meet the following requirements: • Identify the number of security events ingested during the past week. • Display the count of events by day in a chart. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to assign a role-based access control (RBAC) role to admin1 to meet the Azure Sentinel requirements and the business requirements. Which role should you assign?
A. Automation Operator
B. Automation Runbook Operator
C. Azure Sentinel Contributor
D. Azure Sentinel Responder
HOTSPOT - You have a Microsoft Sentinel workspace. You plan to visualize data from Microsoft SharePoint Online and OneDrive sites. You need to create a KQL query for the visual. The solution must meet the following requirements: • Select all workloads as a single operation. • Include two parameters named Operations and Users. • In the results, exclude empty values for the site URLs. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a macOS device named Device1. You need to investigate a Defender for Endpoint agent alert on Device1. The solution must meet the following requirements: • Identify all the active network connections on Device1. • Identify all the running processes on Device1. • Retrieve the login history of Device1. • Minimize administrative effort. What should you do first from the Microsoft Defender portal?
A. From Devices, click Collect investigation package for Device1.
B. From Advanced features in Endpoints, enable Live Response unsigned script execution.
C. From Devices, initiate a live response session on Device1.
D. From Advanced features in Endpoints, disable Authenticated telemetry.
HOTSPOT - You have a Microsoft 365 subscription. You need to identify all the security principals that submitted requests to change or delete groups. How should you complete the KQL query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your on-premises network contains an Active Directory Domain Services (AD DS) forest. You have a Microsoft Entra tenant that uses Microsoft Defender for Identity. The AD DS forest syncs with the tenant. You need to create a hunting query that will identify LDAP simple binds to the AD DS domain controllers. Which table should you query?
A. AADServicePrincipalRiskEvents
B. AADDomainServicesAccountLogon
C. SigninLogs
D. IdentityLogonEvents
DRAG DROP - You have a Microsoft Sentinel workspace named SW1. In SW1, you enable User and Entity Behavior Analytics (UEBA). You need to use KQL to perform the following tasks: • View the entity data that has fields for each type of entity. • Assess the quality of rules by analyzing how well a rule performs. Which table should you use in KQL for each task? To answer, drag the appropriate tables to the correct tasks. Each table may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
HOTSPOT - You have an Azure subscription that contains a user named User1 and a Microsoft Sentinel workspace named WS1. You need to ensure that User1 can enable User and Entity Behavior Analytics (UEBA) for WS1. The solution must follow the principle of least privilege. Which roles should you assign to User1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a solution to meet the technical requirements for the Azure virtual machines. What should you include in the recommendation?
A. just-in-time (JIT) access
B. Azure Defender
C. Azure Firewall
D. Azure Application Gateway
HOTSPOT - You have an Azure subscription that contains a user named User1 and a Microsoft Sentinel workspace named WS1. You deploy Advanced Security Information Model (ASIM) authentication parsers to WS1. You need to use the parsers to query the authentication events generated by User1 during the last 24 hours. The solution must maximize the performance of the query. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
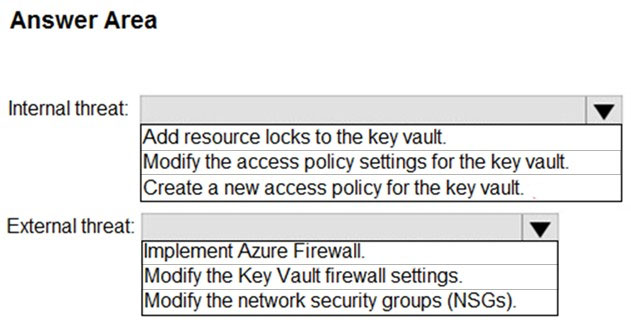
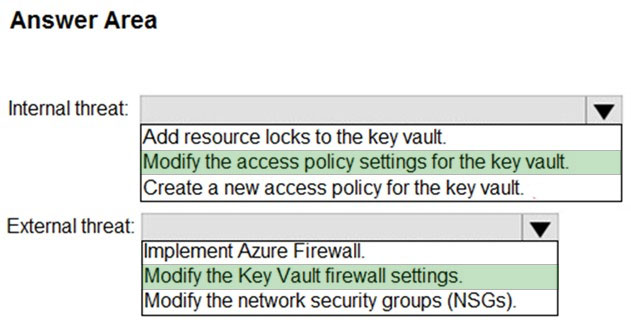
HOTSPOT - You need to recommend remediation actions for the Azure Defender alerts for Fabrikam. What should you recommend for each threat? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
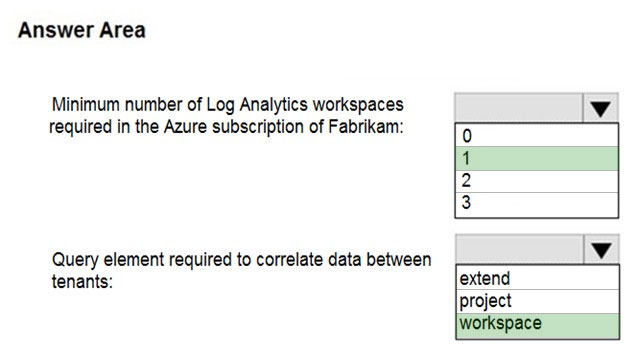
HOTSPOT - You need to implement Azure Sentinel queries for Contoso and Fabrikam to meet the technical requirements. What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
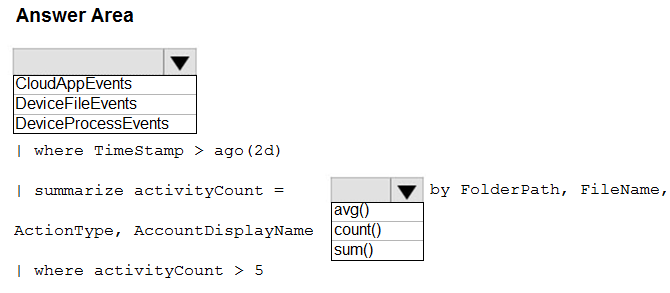
HOTSPOT - You need to create an advanced hunting query to investigate the executive team issue. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a Windows device named Device1. Twenty files on Device1 are quarantined by custom indicators as part of an investigation. You need to release the 20 files from quarantine. How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 subscription that uses Microsoft Defender XDR. You need to create a custom detection rule that will identify devices that had more than five antivirus detections within the last 24 hours. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and contains a Windows device named Device1. You investigate Device1 for malicious activity and discover a suspicious file named File1.exe. You collect an investigation package from Device1. You need to review the following forensic data points: • Is an attacker currently accessing Device1 remotely? • When was File1.exe first executed? Which folder in the investigation package should you review for each data point? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that uses Microsoft Defender XDR. From the Microsoft Defender portal, you perform an audit search and export the results as a file named File1.csv that contains 10,000 rows. You use Microsoft Excel to perform Get & Transform Data operations to parse the AuditData column from File1.csv. The operations fail to generate columns for specific JSON properties. You need to ensure that Excel generates columns for the specific JSON properties in the audit search results. Solution: From Defender, you modify the search criteria of the audit search to reduce the number of returned records, and then you export the results. From Excel, you perform the Get & Transform Data operations by using the new export. Does this meet the requirement?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that uses Microsoft Defender XDR. From the Microsoft Defender portal, you perform an audit search and export the results as a file named File1.csv that contains 10,000 rows. You use Microsoft Excel to perform Get & Transform Data operations to parse the AuditData column from File1.csv. The operations fail to generate columns for specific JSON properties. You need to ensure that Excel generates columns for the specific JSON properties in the audit search results. Solution: From Excel, you apply filters to the existing columns in File1.csv to reduce the number of rows, and then you perform the Get & Transform Data operations to parse the AuditData column. Does this meet the requirement?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that uses Microsoft Defender XDR. From the Microsoft Defender portal, you perform an audit search and export the results as a file named File1.csv that contains 10,000 rows. You use Microsoft Excel to perform Get & Transform Data operations to parse the AuditData column from File1.csv. The operations fail to generate columns for specific JSON properties. You need to ensure that Excel generates columns for the specific JSON properties in the audit search results. Solution: From Defender, you modify the search criteria of the audit search to increase the number of returned records, and then you export the results. From Excel, you perform the Get & Transform Data operations by using the new export. Does this meet the requirement?
A. Yes
B. No
HOTSPOT - You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a Windows device named Device1. You initiated a live response session on Device1. You need to run a command that will download a 250-MB file named File1.exe from the live response library to Device1. The solution must ensure that File1.exe is downloaded as a background process. How should you complete the live response command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains 1,000 Windows devices. You have a PowerShell script named Script1.ps1 that is signed digitally. You need to ensure that you can run Script1.ps1 in a live response session on one of the devices. What should you do first from the live response session?
A. Run the library command.
B. Upload Script1.ps1 to the library.
C. Run the putfile command.
D. Modify the PowerShell execution policy of the device.
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint and contains a Windows device named Device1. You need to investigate a suspicious executable file detected on Device1. The solution must meet the following requirements: • Identify the image file path of the file. • Identify when the file was first detected on Device1. What should you review from the timeline of the detection event? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 subscription that uses Microsoft Defender XDR and contains a Windows device named Device1. You investigate a suspicious process named Prod on Device1 by using a live response session. You need to perform the following actions: • Stop Prod. • Send Prod for further review. Which live response command should you run for each action? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have an Azure subscription that contains a Log Analytics workspace named Workspace1. You configure Azure activity logs and Microsoft Entra ID logs to be forwarded to Workspace1. You need to identify which Azure resources have been queried or modified by risky users. How should you complete the KQL query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an on-premises network. You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Identity. From the Microsoft Defender portal, you investigate an incident on a device named Device1 of a user named User1. The incident contains the following Defender for Identity alert. Suspected identity theft (pass-the-ticket) (external ID 2018) You need to contain the incident without affecting users and devices. The solution must minimize administrative effort. What should you do?
A. Disable User1 only.
B. Quarantine Device1 only.
C. Reset the password for all the accounts that previously signed in to Device1.
D. Disable User1 and quarantine Device1.
E. Disable User1, quarantine Device1, and reset the password for all the accounts that previously signed in to Device1.
You have an Azure subscription that contains a user named User1 and a Microsoft Sentinel workspace named WS1. WS1 uses Microsoft Defender for Cloud. You have the Microsoft security analytics rules shown in the following table.User1 performs an action that matches Rule1, Rule2, Rule3, and Rule4. How many incidents will be created in WS1?
A. 1
B. 2
C. 3
D. 4
You have an Azure subscription that uses Microsoft Sentinel. You need to minimize the administrative effort required to respond to the incidents and remediate the security threats detected by Microsoft Sentinel. Which two features should you use? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Microsoft Sentinel workbooks
B. Azure Automation runbooks
C. Microsoft Sentinel automation rules
D. Microsoft Sentinel playbooks
E. Azure Functions apps
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. You need to identify all the entities affected by an incident. Which tab should you use in the Microsoft Defender portal?
A. Investigations
B. Assets
C. Evidence and Response
D. Alerts
HOTSPOT - You have an Azure subscription that contains a Microsoft Sentinel workspace named WS1. You need to ensure that the incidents in WS1 include a list of actions that must be performed. The solution must meet the following requirements: • Ensure that you can build a tailored list of actions for each type of incident. • Minimize administrative effort. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender XDR and contains a Windows device named Device1. The timeline of Device1 includes three files named File1.ps1, File2.exe, and File3.dll. You need to submit files for deep analysis in Microsoft Defender XDR. Which files can you submit?
A. File1.ps1 only
B. File2.exe only
C. File3.dll only
D. File2.exe and File3.dll only
E. File1.ps1 and File2.exe only
F. File1.ps1, File2.exe, and File3.dll
DRAG DROP - You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online. You need to identify phishing email messages. Which three cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
You have a Microsoft 365 E5 subscription. Automated investigation and response (AIR) is enabled in Microsoft Defender for Office 365 and devices use full automation in Microsoft Defender for Endpoint. You have an incident involving a user that received malware-infected email messages on a managed device. Which action requires manual remediation of the incident?
A. soft deleting the email message
B. hard deleting the email message
C. isolating the device
D. containing the device
HOTSPOT - You need to implement Azure Defender to meet the Azure Defender requirements and the business requirements. What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that contains a device named Device1. Device1 is enrolled in Microsoft Defender for Endpoint. Device1 reports an incident that includes a file named File1.exe as evidence. You initiate the Collect Investigation Package action and download the ZIP file. You need to identify the first and last time File1.exe was executed. What should you review in the investigation package?
A. Processes
B. Autoruns
C. Security event log
D. Scheduled tasks
E. Prefetch files
You have 500 on-premises devices. You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365. You onboard 100 devices to Microsoft Defender 365. You need to identify any unmanaged on-premises devices. The solution must ensure that only specific onboarded devices perform the discovery. What should you do first?
A. Create a device group.
B. Create an exclusion.
C. Set Discovery mode to Basic.
D. Create a tag.
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft 365 Defender for Endpoint. You need to ensure that you can initiate remote shell connections to Windows servers by using the Microsoft 365 Defender portal. What should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have an Azure DevOps organization that uses Microsoft Defender for DevOps. The organization contains an Azure DevOps repository named Repo1 and an Azure Pipelines pipeline named Pipeline1. Pipeline1 is used to build and deploy code stored in Repo1. You need to ensure that when Pipeline1 runs, Microsoft Defender for Cloud can perform secret scanning of the code in Repo1. What should you install in the organization, and what should you add to the YAML file of Pipeline1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
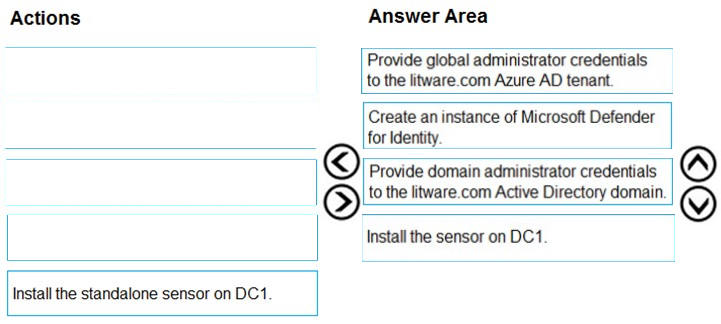
DRAG DROP - You need to configure DC1 to meet the business requirements. Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
Get More SC-200 Practice Questions
If you’re looking for more SC-200 practice test free questions, click here to access the full SC-200 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your SC-200 certification journey!