IT Exam Questions and Solutions Library
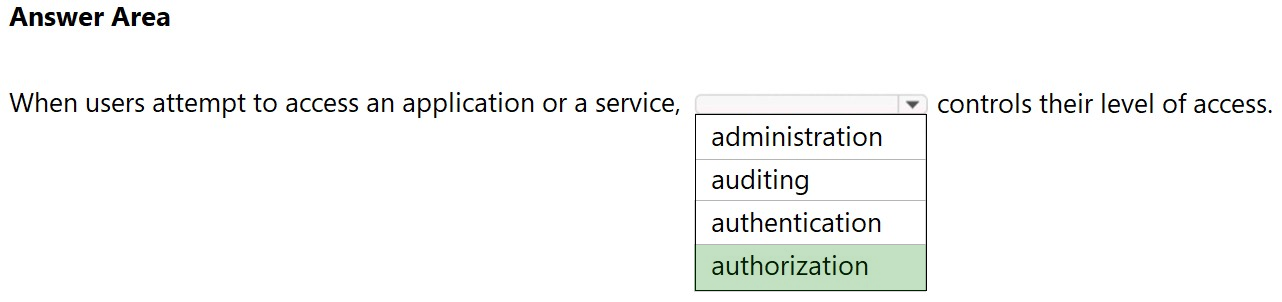
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/security/fundamentals/customer-lockbox-overview
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
In the shared responsibility model for an Azure deployment, what is Microsoft solely responsible for managing? A. the management of mobile devices B. the permissions for the user data stored in Azure C. the creation and management of user accounts D. the management of the physical hardware Suggested Answer: D
Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International Organization for Standardization (ISO)? A. the Microsoft Endpoint Manager admin center B. Azure Cost Management + Billing C. Microsoft Service Trust Portal D. the Azure Active Directory admin center Suggested Answer: C The Microsoft Service Trust Portal contains details about Microsoft's implementation of controls and processes that protect our cloud services and the customer data therein. Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-worldwide
Which score measures an organization's progress in completing actions that help reduce risks associated to data protection and regulatory standards? A. Microsoft Secure Score B. Productivity Score C. Secure score in Azure Security Center D. Compliance score Suggested Answer: D Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - System updates reduces security vulnerabilities, and provide a more stable environment for end users. Not applying updates leaves unpatched vulnerabilities and results in environments that are susceptible to attacks. Box 2: Yes - Box 3: Yes - If you only use a password to authenticate a user, it leaves an attack vector open. With MFA enabled, your accounts are more secure. Reference: https://docs.microsoft.com/en-us/azure/security-center/secure-score-security-controls
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
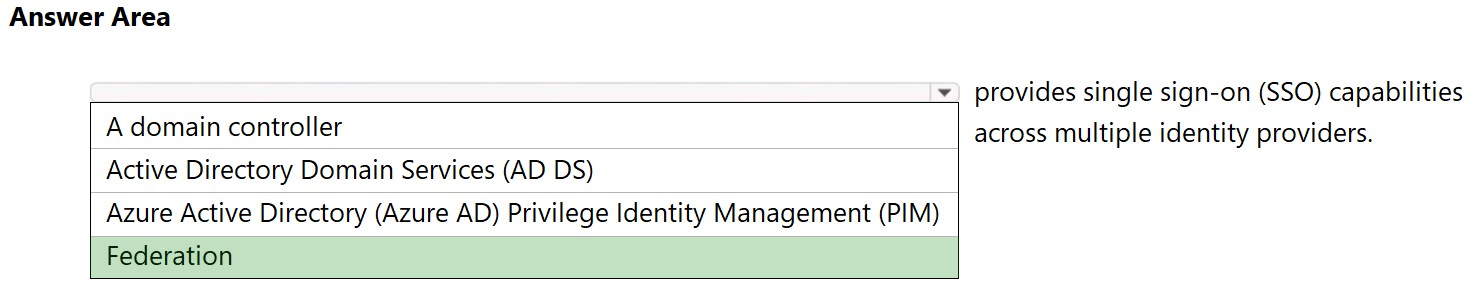
Federation is a collection of domains that have established trust. Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-fed
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/get-started/
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/app-service/overview-authentication-authorization
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Plan B. Manage C. Adopt D. Govern E. Define Strategy Suggested Answer: AE Reference: https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/overview
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/external-identities/what-is-b2b
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - A certificate is required that provides a private and a public key. Box 2: Yes - The public key is used to validate the private key that is associated with a digital signature. Box 3: Yes - The private key, or rather the password to the private key, validates the identity of the signer. Reference: https://support.microsoft.com/en-us/office/obtain-a-digital-certificate-and-create-a-digital-signature-e3d9d813-3305-4164-a820-2e063d86e512 https://docs.microsoft.com/en-us/dynamics365/fin-ops-core/fin-ops/organization-administration/electronic-signature-overview
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
What can you use to provide a user with a two-hour window to complete an administrative task in Azure? A. Azure Active Directory (Azure AD) Privileged Identity Management (PIM) B. Azure Multi-Factor Authentication (MFA) C. Azure Active Directory (Azure AD) Identity Protection D. conditional access policies Suggested Answer: D Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-policy-common
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
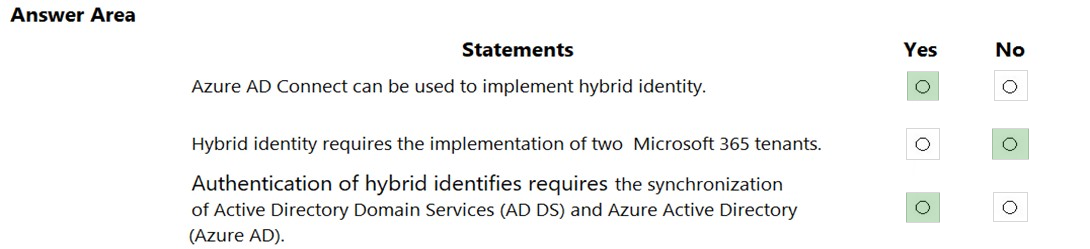
In a hybrid identity model, what can you use to sync identities between Active Directory Domain Services (AD DS) and Azure Active Directory (Azure AD)? A. Active Directory Federation Services (AD FS) B. Microsoft Sentinel C. Azure AD Connect D. Azure AD Privileged Identity Management (PIM) Suggested Answer: C Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-azure-ad-connect
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Reference: https://privacy.microsoft.com/en-US/
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
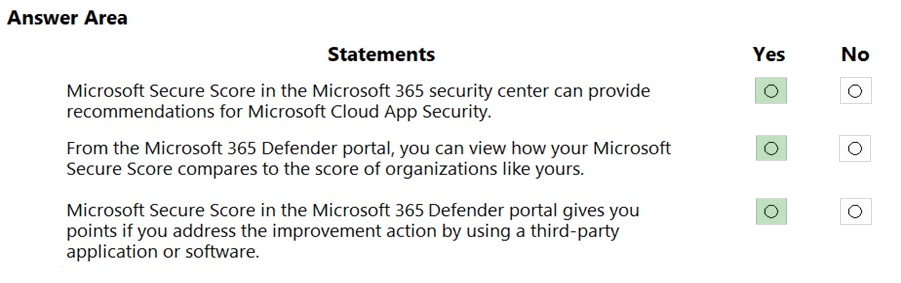
Box 1: Yes - Microsoft Secure Score has updated improvement actions to support security defaults in Azure Active Directory, which make it easier to help protect your organization with pre-configured security settings for common attacks. If you turn on security defaults, you'll be awarded full points for the following improvement actions: Ensure all users can complete multi-factor authentication for secure access (9 points) Require MFA for administrative roles (10 points) Enable policy to block legacy authentication (7 points) Box 2: Yes - Each improvement action is worth 10 points or less, and most are scored in a binary fashion. If you implement the improvement action, like create a new policy or turn on a specific setting, you get 100% of the points. For other improvement actions, points are given as a percentage of the total configuration. Note: Following the Secure Score recommendations can protect your organization from threats. From a centralized dashboard in the Microsoft 365 Defender portal, organizations can monitor and work on the security of their Microsoft 365 identities, apps, and devices. Box 3: Yes - Microsoft Secure Score is a measurement of an organization's security posture, with a higher number indicating more improvement actions taken. Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/microsoft-secure-score
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - Box 2: Yes - Box 3: No - The Zero Trust model does not assume that everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originated from an uncontrolled network. Reference: https://docs.microsoft.com/en-us/security/zero-trust/
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Sign in to Compliance Manager - 1. Go to the Microsoft Purview compliance portal and sign in with your Microsoft 365 global administrator account. 2. Select Compliance Manager on the left navigation pane. You'll arrive at your Compliance Manager dashboard. The direct link to access Compliance Manager is https://compliance.microsoft.com/compliancemanager Note: Microsoft 365 compliance is now called Microsoft Purview and the solutions within the compliance area have been rebranded. Reference:https://compliance.microsoft.com/compliancemanager Note: Microsoft 365 compliance is now called Microsoft Purview and the solutions within the compliance area have been rebranded. Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager-setup
What do you use to provide real-time integration between Azure Sentinel and another security source? A. Azure AD Connect B. a Log Analytics workspace C. Azure Information Protection D. a connector Suggested Answer: D To on-board Azure Sentinel, you first need to connect to your security sources. Azure Sentinel comes with a number of connectors for Microsoft solutions, including Microsoft 365 Defender solutions, and Microsoft 365 sources, including Office 365, Azure AD, Microsoft Defender for Identity, and Microsoft Cloud App Security, etc. Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
HOTSPOT - Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/security-center/secure-score-access-and-track
DRAG DROP - You are evaluating the compliance score in Compliance Manager. Match the compliance score action subcategories to the appropriate actions. To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:Suggested Answer:
Box 1: Preventative - Preventative actions address specific risks. For example, protecting information at rest using encryption is a preventative action against attacks and breaches. Separation of duties is a preventative action to manage conflict of interest and guard against fraud. Box 2: Detective - Detective actions actively monitor systems to identify irregular conditions or behaviors that represent risk, or that can be used to detect intrusions or breaches. Examples include system access auditing and privileged administrative actions. Regulatory compliance audits are a type of detective action used to find process issues. Box 3: Corrective - Corrective actions try to keep the adverse effects of a security incident to a minimum, take corrective action to reduce the immediate effect, and reverse the damage if possible. Privacy incident response is a corrective action to limit damage and restore systems to an operational state after a breach. Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation
Which three statements accurately describe the guiding principles of Zero Trust? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Define the perimeter by physical locations. B. Use identity as the primary security boundary. C. Always verify the permissions of a user explicitly. D. Always assume that the user system can be breached. E. Use the network as the primary security boundary. Suggested Answer: BCD Reference: https://docs.microsoft.com/en-us/security/zero-trust/
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/cloud-services-security-baseline
What is an example of encryption at rest? A. encrypting communications by using a site-to-site VPN B. encrypting a virtual machine disk C. accessing a website by using an encrypted HTTPS connection D. sending an encrypted email Suggested Answer: B Reference: https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-atrest
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:

Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require membership in a group? A. access reviews B. managed identities C. conditional access policies D. Azure AD Identity Protection Suggested Answer: A Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. Reference: https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
When security defaults are enabled for an Azure Active Directory (Azure AD) tenant, which two requirements are enforced? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. All users must authenticate from a registered device. B. Administrators must always use Azure Multi-Factor Authentication (MFA). C. Azure Multi-Factor Authentication (MFA) registration is required for all users. D. All users must authenticate by using passwordless sign-in. E. All users must authenticate by using Windows Hello. Suggested Answer: BC Security defaults make it easy to protect your organization with the following preconfigured security settings: ✑ Requiring all users to register for Azure AD Multi-Factor Authentication. ✑ Requiring administrators to do multi-factor authentication. ✑ Blocking legacy authentication protocols. ✑ Requiring users to do multi-factor authentication when necessary. ✑ Protecting privileged activities like access to the Azure portal. Reference: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
What is the purpose of Azure Active Directory (Azure AD) Password Protection? A. to control how often users must change their passwords B. to identify devices to which users can sign in without using multi-factor authentication (MFA) C. to encrypt a password by using globally recognized encryption standards D. to prevent users from using specific words in their passwords Suggested Answer: D Azure AD Password Protection detects and blocks known weak passwords and their variants, and can also block additional weak terms that are specific to your organization. With Azure AD Password Protection, default global banned password lists are automatically applied to all users in an Azure AD tenant. To support your own business and security needs, you can define entries in a custom banned password list. Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad-on-premises
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Biometrics templates are stored locally on a device. Reference: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
You have an Azure subscription. You need to implement approval-based, time-bound role activation. What should you use? A. Windows Hello for Business B. Azure Active Directory (Azure AD) Identity Protection C. access reviews in Azure Active Directory (Azure AD) D. Azure Active Directory (Azure AD) Privileged Identity Management (PIM) Suggested Answer: D Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
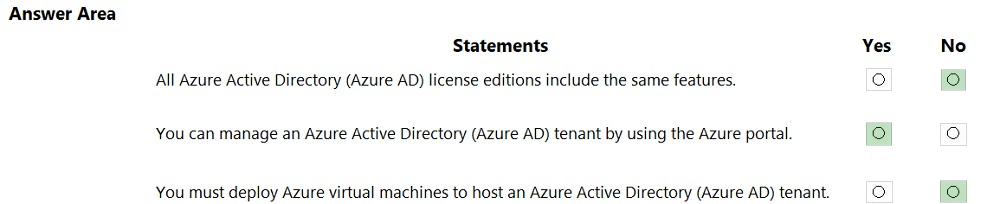
Box 1: No - Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service. Box 2: Yes - Microsoft 365 uses Azure Active Directory (Azure AD). Azure Active Directory (Azure AD) is included with your Microsoft 365 subscription. Box 3: Yes - Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service. Reference: https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. fingerprint B. facial recognition C. PIN D. email verification E. security question Suggested Answer: ABC Reference: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-how-it-works-authentication
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - Azure AD supports custom roles. Box 2: Yes - Global Administrator has access to all administrative features in Azure Active Directory. Box 3: No - Reference: https://docs.microsoft.com/en-us/azure/active-directory/roles/concept-understand-roles https://docs.microsoft.com/en-us/azure/active-directory/roles/permissions-reference
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
When you register an application through the Azure portal, an application object and service principal are automatically created in your home directory or tenant. Reference: https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - Conditional access policies can be applied to all users Box 2: No - Conditional access policies are applied after first-factor authentication is completed. Box 3: Yes - Users with devices of specific platforms or marked with a specific state can be used when enforcing Conditional Access policies. Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization? A. sensitivity label policies B. Customer Lockbox C. information barriers D. Privileged Access Management (PAM) Suggested Answer: C Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-barriers
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. text message (SMS) B. Microsoft Authenticator app C. email verification D. phone call E. security question Suggested Answer: ABD Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-methods
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
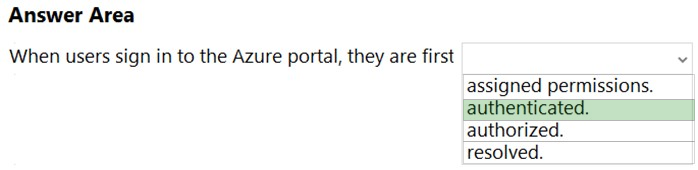
Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service. Reference: https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
Which Azure Active Directory (Azure AD) feature can you use to provide just-in-time (JIT) access to manage Azure resources? A. conditional access policies B. Azure AD Identity Protection C. Azure AD Privileged Identity Management (PIM) D. authentication method policies Suggested Answer: C Azure AD Privileged Identity Management (PIM) provides just-in-time privileged access to Azure AD and Azure resources Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Microsoft Defender for Identity is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Reference: https://docs.microsoft.com/en-us/defender-for-identity/what-is
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/defender-for-identity/what-is
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identification, such as to enter a code on their cellphone or to provide a fingerprint scan. Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - Box 2: No - Conditional Access policies are enforced after first-factor authentication is completed. Box 3: Yes - Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
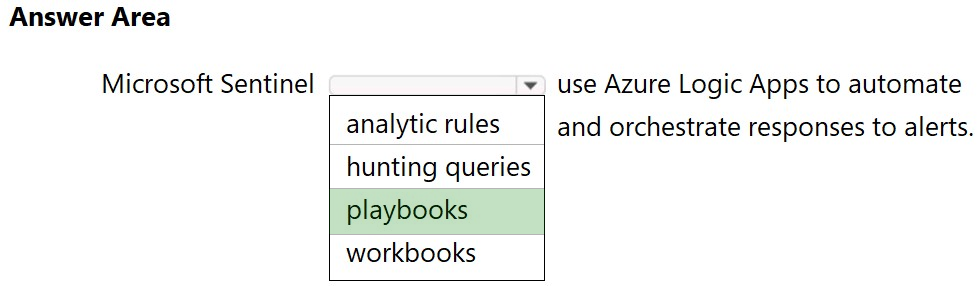
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-admin-mfa
What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface? A. automated remediation B. automated investigation C. advanced hunting D. network protection Suggested Answer: D Network protection helps protect devices from Internet-based events. Network protection is an attack surface reduction capability. Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/bastion/bastion-overview https://docs.microsoft.com/en-us/azure/bastion/tutorial-create-host-portal
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol. Reference: https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
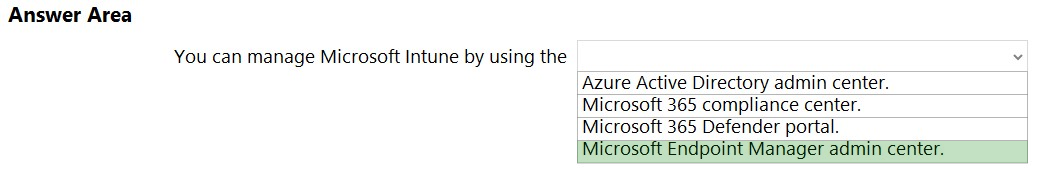
Reference: https://docs.microsoft.com/en-us/mem/intune/fundamentals/what-is-intune https://docs.microsoft.com/en-us/mem/intune/fundamentals/what-is-device-management
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/threat-analytics?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - Microsoft Defender for Cloud provides security alerts and advanced threat protection for virtual machines, SQL databases, containers, web applications, your network, your storage, and more Box 2: Yes - Cloud security posture management (CSPM) is available for free to all Azure users. Box 3: Yes - Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud - whether they're in Azure or not - as well as on premises. Reference: https://docs.microsoft.com/en-us/azure/security-center/azure-defender https://docs.microsoft.com/en-us/azure/security-center/defender-for-storage-introduction https://docs.microsoft.com/en-us/azure/security-center/security-center-introduction
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution. Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
What are two capabilities of Microsoft Defender for Endpoint? Each correct selection presents a complete solution. NOTE: Each correct selection is worth one point. A. automated investigation and remediation B. transport encryption C. shadow IT detection D. attack surface reduction Suggested Answer: AD Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint?view=o365-worldwide
DRAG DROP - Match the Azure networking service to the appropriate description. To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:Suggested Answer:
Box 1: Azure Firewall - Azure Firewall provide Source Network Address Translation and Destination Network Address Translation. Box 2: Azure Bastion - Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. Box 3: Network security group (NSG) You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. Reference: https://docs.microsoft.com/en-us/azure/networking/fundamentals/networking-overview https://docs.microsoft.com/en-us/azure/bastion/bastion-overview https://docs.microsoft.com/en-us/azure/firewall/features https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Managed identities provide an identity for applications to use when connecting to resources that support Azure Active Directory (Azure AD) authentication. Here are some of the benefits of using managed identities: You don't need to manage credentials. Credentials aren't even accessible to you. You can use managed identities to authenticate to any resource that supports Azure AD authentication, including your own applications. Reference: https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/incidents-overview?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: No - The Microsoft Authenticator app helps you sign in to your accounts when you're using two-factor verification. Two-factor verification helps you to use your accounts more securely because passwords can be forgotten, stolen, or compromised. Two-factor verification uses a second factor like your phone to make it harder for other people to break in to your account. Box 2: Yes - In Windows 10, Windows Hello for Business replaces passwords with strong two-factor authentication on devices. This authentication consists of a new type of user credential that is tied to a device and uses a biometric or PIN. Box 3: No - Windows Hello credentials are based on certificate or asymmetrical key pair. Windows Hello credentials can be bound to the device, and the token that is obtained using the credential is also bound to the device. Reference: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
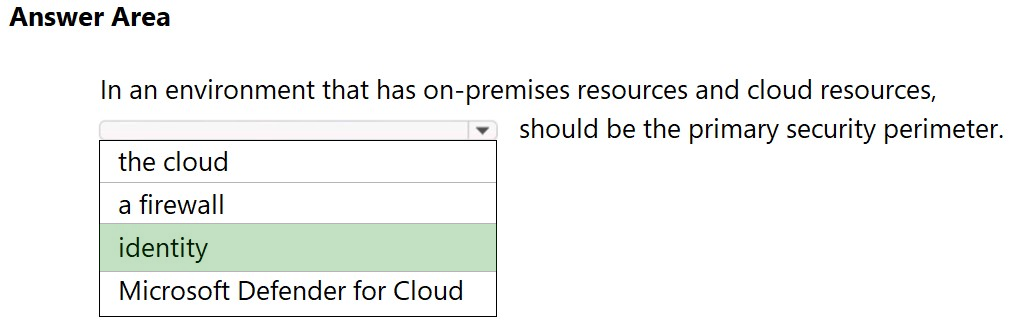
You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure. Which security methodology does this represent? A. threat modeling B. identity as the security perimeter C. defense in depth D. the shared responsibility model Suggested Answer: C Reference: https://docs.microsoft.com/en-us/learn/modules/secure-network-connectivity-azure/2-what-is-defense-in-depth
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Box 1: know - Multifactor authentication combines two or more independent credentials: what the user knows, such as a password; what the user has, such as a security token; and what the user is, by using biometric verification methods. Reference: https://www.techtarget.com/searchsecurity/definition/multifactor-authentication-MFA
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:

Which three tasks can be performed by using Azure Active Directory (Azure AD) Identity Protection? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Configure external access for partner organizations. B. Export risk detection to third-party utilities. C. Automate the detection and remediation of identity based-risks. D. Investigate risks that relate to user authentication. E. Create and automatically assign sensitivity labels to data. Suggested Answer: CDE
Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Azure virtual machines B. Azure Active Directory (Azure AD) users C. Microsoft Exchange Online inboxes D. Azure virtual networks E. Microsoft SharePoint Online sites Suggested Answer: DE
Which type of identity is created when you register an application with Active Directory (Azure AD)? A. a user account B. a user-assigned managed identity C. a system-assigned managed identity D. a service principal Suggested Answer: D When you register an application through the Azure portal, an application object and service principal are automatically created in your home directory or tenant. Reference: https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal
You need to connect to an Azure virtual machine by using Azure Bastion. What should you use? A. PowerShell remoting B. the Azure portal C. the Remote Desktop Connection client D. an SSH client Suggested Answer: C You can create an RDP connection to a Windows VM using Azure Bastion. Reference: https://docs.microsoft.com/en-us/azure/bastion/bastion-connect-vm-rdp-windows
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Box 1: vulnerabilities - Microsoft 365 Defender portal is the new home for monitoring and managing security across your identities, data, devices, and apps, you will need to access various portals for certain specialized tasks. It used to monitor and respond to threat activity and strengthen security posture across your identities, email, data, endpoints, and apps with Microsoft 365 Defender - Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/portals
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. to discover and control the use of shadow IT B. to provide secure connections to Azure virtual machines C. to protect sensitive information hosted anywhere in the cloud D. to provide pass-through authentication to on-premises applications E. to prevent data leaks to noncompliant apps and limit access to regulated data Suggested Answer: ACE Reference: https://docs.microsoft.com/en-us/defender-cloud-apps/what-is-defender-for-cloud-apps
You have a Microsoft 365 E3 subscription. You plan to audit user activity by using the unified audit log and Basic Audit. For how long will the audit records be retained? A. 15 days B. 30 days C. 90 days D. 180 days Suggested Answer: C
What should you use in the Microsoft 365 Defender portal to view security trends and track the protection status of identities? A. Attack simulator B. Reports C. Hunting D. Incidents Suggested Answer: B Reference: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/reports-and-insights-in-security-and-compliance?view=o365-worldwide
To which type of resource can Azure Bastion provide secure access? A. Azure Files B. Azure SQL Managed Instances C. Azure virtual machines D. Azure App Service Suggested Answer: C Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. Reference: https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/ddos-protection/ddos-protection-overview
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/cloud-app-security/what-is-cloud-app-security
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources? A. network security groups (NSGs) B. Azure AD Privileged Identity Management (PIM) C. conditional access policies D. resource locks Suggested Answer: C
What can you use to deploy Azure resources across multiple subscriptions in a consistent manner? A. Microsoft Defender for Cloud B. Azure Blueprints C. Microsoft Sentinel D. Azure Policy Suggested Answer: B Reference: https://docs.microsoft.com/en-us/azure/governance/blueprints/overview
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - The MailItemsAccessed event is a mailbox auditing action and is triggered when mail data is accessed by mail protocols and mail clients. Box 2: No - Basic Audit retains audit records for 90 days. Advanced Audit retains all Exchange, SharePoint, and Azure Active Directory audit records for one year. This is accomplished by a default audit log retention policy that retains any audit record that contains the value of Exchange, SharePoint, or AzureActiveDirectory for the Workload property (which indicates the service in which the activity occurred) for one year. Box 3: yes - Advanced Audit in Microsoft 365 provides high-bandwidth access to the Office 365 Management Activity API. Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/advanced-audit?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/compliance/auditing-solutions-overview?view=o365-worldwide#licensing-requirements https://docs.microsoft.com/en-us/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/ microsoft-365-security-compliance-licensing-guidance#advanced-audit
What can you use to provide threat detection for Azure SQL Managed Instance? A. Microsoft Secure Score B. application security groups C. Microsoft Defender for Cloud D. Azure Bastion Suggested Answer: C
What is a use case for implementing information barrier policies in Microsoft 365? A. to restrict unauthenticated access to Microsoft 365 B. to restrict Microsoft Teams chats between certain groups within an organization C. to restrict Microsoft Exchange Online email between certain groups within an organization D. to restrict data sharing to external email recipients Suggested Answer: C Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-barriers-policies?view=o365-worldwide
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel? A. integration with the Microsoft 365 compliance center B. support for threat hunting C. integration with Microsoft 365 Defender D. support for Azure Monitor Workbooks Suggested Answer: C Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/eval-overview?view=o365-worldwide
Which two Azure resources can a network security group (NSG) be associated with? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. a virtual network subnet B. a network interface C. a resource group D. a virtual network E. an Azure App Service web app Suggested Answer: AB Association of network security groups You can associate a network security group with virtual machines, NICs, and subnets, depending on the deployment model you use. Reference: https://aviatrix.com/learn-center/cloud-security/create-network-security-groups-in-azure/
What can you use to scan email attachments and forward the attachments to recipients only if the attachments are free from malware? A. Microsoft Defender for Office 365 B. Microsoft Defender Antivirus C. Microsoft Defender for Identity D. Microsoft Defender for Endpoint Suggested Answer: A Reference: https://docs.microsoft.com/en-us/office365/servicedescriptions/office-365-advanced-threat-protection-service-description
Which service includes the Attack simulation training feature? A. Microsoft Defender for Cloud Apps B. Microsoft Defender for Identity C. Microsoft Defender for SQL D. Microsoft Defender for Office 365 Suggested Answer: D Attack simulation training in Microsoft Defender for Office 365 Plan 2 or Microsoft 365 E5 lets you run benign cyberattack simulations in your organization. These simulations test your security policies and practices, as well as train your employees to increase their awareness and decrease their susceptibility to attacks. Reference: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulation-training
Which type of alert can you manage from the Microsoft 365 Defender portal? A. Microsoft Defender for Storage B. Microsoft Defender for SQL C. Microsoft Defender for Endpoint D. Microsoft Defender for IoT Suggested Answer: C The Alerts queue shows the current set of alerts. You get to the alerts queue from Incidents & alerts > Alerts on the quick launch of the Microsoft 365 Defender portal. Alerts from different Microsoft security solutions like Microsoft Defender for Endpoint, Microsoft Defender for Office 365, and Microsoft 365 Defender appear here. Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/investigate-alerts
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: No - Microsoft Sentinel data connectors are available for non-Microsoft services like Amazon Web Services. Box 2: Yes - Once you have connected your data sources to Microsoft Sentinel, you can visualize and monitor the data using the Microsoft Sentinel adoption of Azure Monitor Workbooks, which provides versatility in creating custom dashboards. While the Workbooks are displayed differently in Microsoft Sentinel, it may be useful for you to see how to create interactive reports with Azure Monitor Workbooks. Microsoft Sentinel allows you to create custom workbooks across your data, and also comes with built-in workbook templates to allow you to quickly gain insights across your data as soon as you connect a data source. Box 3: Yes - To help security analysts look proactively for new anomalies that weren't detected by your security apps or even by your scheduled analytics rules, Microsoft Sentinel's built-in hunting queries guide you into asking the right questions to find issues in the data you already have on your network. Reference: https://docs.microsoft.com/en-us/azure/sentinel/data-connectors-reference https://docs.microsoft.com/en-us/azure/sentinel/monitor-your-data https://docs.microsoft.com/en-us/azure/sentinel/hunting
What can you specify in Microsoft 365 sensitivity labels? A. how long files must be preserved B. when to archive an email message C. which watermark to add to files D. where to store files Suggested Answer: C Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
What can you protect by using the information protection solution in the Microsoft 365 compliance center? A. computers from zero-day exploits B. users from phishing attempts C. files from malware and viruses D. sensitive data from being exposed to unauthorized users Suggested Answer: D Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
Which Microsoft portal provides information about how Microsoft manages privacy, compliance, and security? A. Microsoft Service Trust Portal B. Compliance Manager C. Microsoft 365 compliance center D. Microsoft Support Suggested Answer: A Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-worldwide
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/security/fundamentals/customer-lockbox-overview
In a Core eDiscovery workflow, what should you do before you can search for content? A. Create an eDiscovery hold. B. Run Express Analysis. C. Configure attorney-client privilege detection. D. Export and download results. Suggested Answer: A Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-core-ediscovery?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/azure/governance/policy/overview
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers? A. retention policies B. data loss prevention (DLP) policies C. conditional access policies D. information barriers Suggested Answer: B Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
DRAG DROP - Match the Microsoft 365 insider risk management workflow step to the appropriate task. To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/insider-risk-management?view=o365-worldwide
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/microsoft-365-compliance-center?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: No - Compliance Manager tracks Microsoft managed controls, customer-managed controls, and shared controls. Box 2: Yes - Box 3: Yes - Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
Which Microsoft 365 compliance center feature can you use to identify all the documents on a Microsoft SharePoint Online site that contain a specific key word? A. Audit B. Compliance Manager C. Content Search D. Alerts Suggested Answer: C The Content Search tool in the Security & Compliance Center can be used to quickly find email in Exchange mailboxes, documents in SharePoint sites and OneDrive locations, and instant messaging conversations in Skype for Business. The first step is to starting using the Content Search tool to choose content locations to search and configure a keyword query to search for specific items. Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/search-for-content?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: No - Phishing scams are external threats. Box 2: Yes - Insider risk management is a compliance solution in Microsoft 365. Box 3: Yes - Insider risk management helps minimize internal risks from users. These include: ✑ Leaks of sensitive data and data spillage ✑ Confidentiality violations ✑ Intellectual property (IP) theft ✑ Fraud ✑ Insider trading ✑ Regulatory compliance violations Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/insider-risk-management?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/compliance/microsoft-365-compliance-center?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: No - Box 2: Yes - Leaked Credentials indicates that the user's valid credentials have been leaked. Box 3: Yes - Multi-Factor Authentication can be required based on conditions, one of which is user risk. Reference: https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-risks https://docs.microsoft.com/en-us/azure/active-directory/authentication/tutorial-risk-based-sspr-mfa
Which Microsoft 365 compliance feature can you use to encrypt content automatically based on specific conditions? A. Content Search B. sensitivity labels C. retention policies D. eDiscovery Suggested Answer: B Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: Yes - You can use sensitivity labels to provide protection settings that include encryption of emails and documents to prevent unauthorized people from accessing this data. Box 2: Yes - You can use sensitivity labels to mark the content when you use Office apps, by adding watermarks, headers, or footers to documents that have the label applied. Box 3: Yes - You can use sensitivity labels to mark the content when you use Office apps, by adding headers, or footers to email that have the label applied. Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation?view=o365-worldwide#how-compliance-manager-continuously- assesses-controls
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
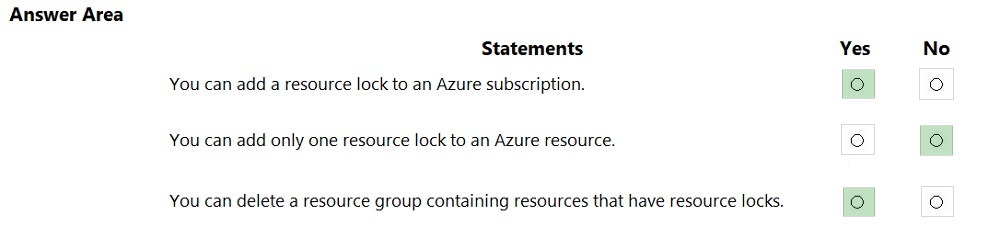
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
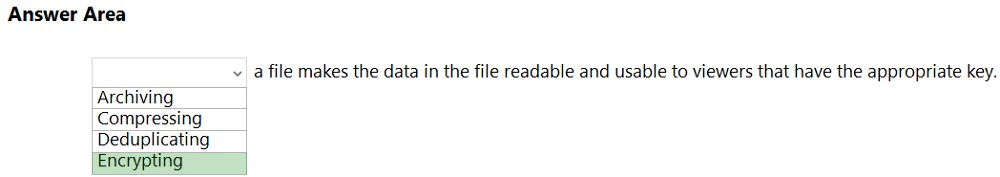
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-sensitivity-labels?view=o365-worldwide
Which two tasks can you implement by using data loss prevention (DLP) policies in Microsoft 365? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Display policy tips to users who are about to violate your organization's policies. B. Enable disk encryption on endpoints. C. Protect documents in Microsoft OneDrive that contain sensitive information. D. Apply security baselines to devices. Suggested Answer: AC Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
Box 1: No - Advanced Audit helps organizations to conduct forensic and compliance investigations by increasing audit log retention. Box 2: No - Box 3: Yes - Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/advanced-audit?view=o365-worldwide
You need to create a data loss prevention (DLP) policy. What should you use? A. the Microsoft 365 Compliance center B. the Microsoft Endpoint Manager admin center C. the Microsoft 365 admin center D. the Microsoft 365 Defender portal Suggested Answer: C
DRAG DROP - Match the types of compliance score actions to the appropriate tasks. To answer, drag the appropriate action type from the column on the left to its task on the right. Each type may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.Suggested Answer:

You need to keep a copy of all files in a Microsoft SharePoint site for one year, even if users delete the files from the site. What should you apply to the site? A. a retention policy B. an insider risk policy C. a data loss prevention (DLP) policy D. a sensitivity label policy Suggested Answer: A
DRAG DROP - Match the pillars of Zero Trust to the appropriate requirements. To answer, drag the appropriate pillar from the column on the left to its requirement on the right. Each pillar may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.Suggested Answer:

What should you use to ensure that the members of an Azure Active Directory group use multi-factor authentication (MFA) when they sign in? A. Azure role-based access control (Azure RBAC) B. Azure Active Directory (Azure AD) Privileged Identity Management (PIM) C. Azure Active Directory (Azure AD) Identity Protection D. a conditional access policy Suggested Answer: D
Which compliance feature should you use to identify documents that are employee resumes? A. pre-trained classifiers B. Activity explorer C. eDiscovery D. Content explorer Suggested Answer: A
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:
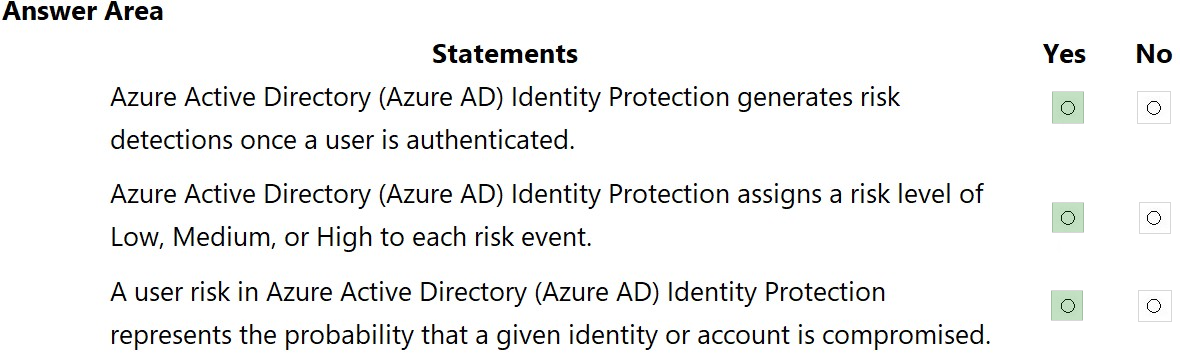
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Which two cards are available in the Microsoft 365 Defender portal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. Devices at risk B. Compliance Score C. Service Health D. User Management E. Users at risk Suggested Answer: AE A: The Devices at risk card includes a View details button. Selecting that button takes us to the Device inventory page, as shown in the following imageE: The Microsoft 365 Defender portal cards fall into these categories: Identities- Monitor the identities in your organization and keep track of suspicious or risky behaviors. Here you can find the Users at risk card. Data - Help track user activity that could lead to unauthorized data disclosure. Devices - Get up-to-date information on alerts, breach activity, and other threats on your devices. Apps - Gain insight into how cloud apps are being used in your organization. Incorrect: Not C: The Service Health card can be reached from the Microsoft 365 admin center. Reference: alt="Reference Image" /> E: The Microsoft 365 Defender portal cards fall into these categories: Identities- Monitor the identities in your organization and keep track of suspicious or risky behaviors. Here you can find the Users at risk card. Data - Help track user activity that could lead to unauthorized data disclosure. Devices - Get up-to-date information on alerts, breach activity, and other threats on your devices. Apps - Gain insight into how cloud apps are being used in your organization. Incorrect: Not C: The Service Health card can be reached from the Microsoft 365 admin center. Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-business/mdb-respond-mitigate-threats
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
What does Conditional Access evaluate by using Azure Active Directory (Azure AD) Identity Protection? A. user actions B. group membership C. device compliance D. user risk Suggested Answer: C
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
Which statement represents a Microsoft privacy principle? A. Microsoft manages privacy settings for its customers. B. Microsoft respects the local privacy laws that are applicable to its customers. C. Microsoft uses hosted customer email and chat data for targeted advertising. D. Microsoft does not collect any customer data. Suggested Answer: A
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:Suggested Answer:
What are customers responsible for when evaluating security in a software as a service (SaaS) cloud services model? A. operating systems B. network controls C. applications D. accounts and identities Suggested Answer: C
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:Suggested Answer:

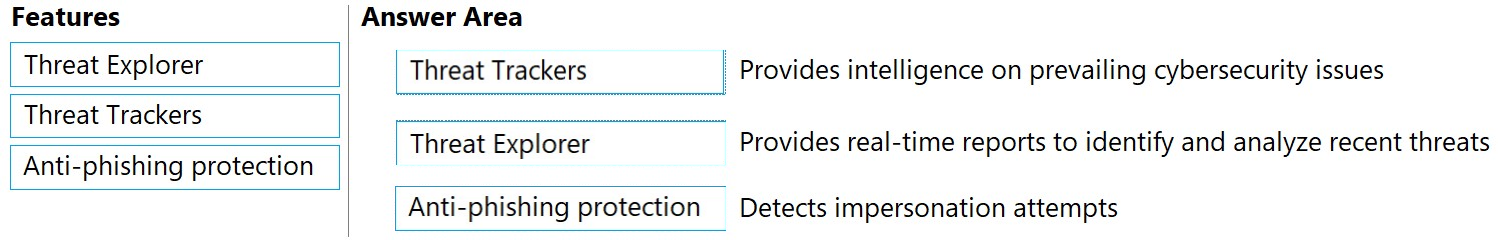
DRAG DROP - Match the Microsoft Defender for Office 365 feature to the correct description. To answer, drag the appropriate feature from the column on the left to its description on the right. Each feature may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:Suggested Answer:
What can you use to view the Microsoft Secure Score for Devices? A. Microsoft Defender for Cloud Apps B. Microsoft Defender for Endpoint C. Microsoft Defender for Identity D. Microsoft Defender for Office 365 Suggested Answer: B
What is an assessment in Compliance Manager? A. A policy initiative that includes multiple policies. B. A dictionary of words that are not allowed in company documents. C. A grouping of controls from a specific regulation, standard or policy. D. Recommended guidance to help organizations align with their corporate standards. Suggested Answer: C
What is the maximum number of resources that Azure DDoS Protection Standard can protect without additional costs? A. 50 B. 100 C. 500 D. 1000 Suggested Answer: B
Which pillar of identity relates to tracking the resources accessed by a user? A. authorization B. auditing C. administration D. authentication Suggested Answer: B
HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems? A. Windows 10 and newer only B. Windows 10 and newer and Android only C. Windows 10 and newer and iOS only D. Windows 10 and newer, Android, and iOS Suggested Answer: A
HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

Which security feature is available in the free mode of Microsoft Defender for Cloud? A. threat protection alerts B. just-in-time (JIT) VM access to Azure virtual machines C. vulnerability scanning of virtual machines D. secure score Suggested Answer: D
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

Which three authentication methods can Azure AD users use to reset their password? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. mobile app notification B. text message to a phone C. security questions D. certificate E. picture password Suggested Answer: ABC
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

What can you use to ensure that all the users in a specific group must use multi-factor authentication (MFA) to sign to Azure Active Directory (Azure AD)? A. Azure Policy B. a communication compliance policy C. a Conditional Access policy D. a user risk policy Suggested Answer: C
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

What is a function of Conditional Access session controls? A. enforcing device compliance B. enforcing client app compliance C. enable limited experiences, such as blocking download of sensitive information D. prompting multi-factor authentication (MFA) Suggested Answer: D
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription? A. secure score B. resource health C. completed controls D. the status of recommendations Suggested Answer: A
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point. A. to meet governance policies B. to connect multiple types of resources C. to separate the resources for budgeting D. to isolate the resources Suggested Answer: BD
What can be created in Active Directory Domain Services (AD DS)? A. line-of-business (LOB) applications that require modern authentication B. computer accounts C. software as a service (SaaS) applications that require modern authentication D. mobile devices Suggested Answer: B
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

What is a characteristic of a sensitivity label in Microsoft 365? A. encrypted B. restricted to predefined categories C. persistent Suggested Answer: C
DRAG DROP - Match the Microsoft Purview Insider Risk Management workflow step to the appropriate task. To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.Suggested Answer:

You have an Azure subscription that contains a Log Analytics workspace. You need to onboard Microsoft Sentinel. What should you do first? A. Create a hunting query. B. Correlate alerts into incidents. C. Connect to your security sources. D. Create a custom detection rule. Suggested Answer: C
You need to ensure repeatability when creating new resources in an Azure subscription. What should you use? A. Microsoft Sentinel B. Azure Policy C. Azure Batch D. Azure Blueprints Suggested Answer: D
Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems? A. Windows 10 and newer only B. Windows 10 and newer and Android only C. Windows 10 and newer and macOS only D. Windows 10 and newer, Android, and macOS Suggested Answer: C
HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

Which three forms of verification can be used with Azure AD Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct answer is worth one point. A. security questions B. the Microsoft Authenticator app C. SMS messages D. a smart card E. Windows Hello for Business Suggested Answer: BCE
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

You have an Azure subscription that contains multiple resources. You need to assess compliance and enforce standards for the existing resources. What should you use? A. Azure Blueprints B. the Anomaly Detector service C. Microsoft Sentinel D. Azure Policy Suggested Answer: D
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

What should you use to associate the same identity to more than one Azure virtual machine? A. an Azure AD user account B. a user-assigned managed identity C. a system-assigned managed identity D. an Azure AD security group Suggested Answer: B
HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

Which score measures an organization’s progress in completing actions that help reduce risks associated to data protection and regulatory standards? A. Adoption Score B. Microsoft Secure Score C. Secure score in Microsoft Defender for Cloud D. Compliance score Suggested Answer: D
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

You plan to move resources to the cloud. You are evaluating the use of Infrastructure as a service (IaaS), Platform as a service (PaaS), and Software as a service (SaaS) cloud models. You plan to manage only the data, user accounts, and user devices for a cloud-based app. Which cloud model will you use? A. SaaS B. PaaS C. IaaS Suggested Answer: A
HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

Which portal contains the solution catalog? A. Microsoft Purview compliance portal B. Microsoft 365 Defender portal C. Microsoft 365 admin center D. Microsoft 365 Apps admin center Suggested Answer: A
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

What should you use in the Microsoft 365 Defender portal to view security trends and track the protection status of identities? A. Reports B. Incidents C. Hunting D. Secure score Suggested Answer: A
You have an Azure subscription. You need to implement approval-based, time-bound role activation. What should you use? A. access reviews in Azure AD B. Azure AD Privileged Identity Management (PIM) C. Azure AD Identity Protection D. Conditional access in Azure AD Suggested Answer: B
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

DRAG DROP - You need to identify which cloud service models place the most responsibility on the customer in a shared responsibility model. In which order should you list the service models from the most customer responsibility to the least? To answer, move all models from the list of models to the answer area and arrange them in the correct order.Suggested Answer:

DRAG DROP - Match the types of Conditional Access signals to the appropriate definitions. To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all. NOTE: Each correct match is worth one point.Suggested Answer:

Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International Organization for Standardization (ISO)? A. the Microsoft 365 admin center B. Azure Cost Management + Billing C. Microsoft Service Trust Portal D. the Microsoft Purview compliance portal Suggested Answer: C
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

What is Azure Key Vault used for? A. to deploy a cloud-based network security service that protects Azure virtual network resources B. to protect cloud-based applications from cyber threats and vulnerabilities C. to safeguard cryptographic keys and other secrets used by cloud apps and services D. to provide secure and seamless RDP/SSH connectivity to Azure virtual machines via TLS from the Azure portal Suggested Answer: C
HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

When you enable Azure AD Multi-Factor Authentication (MFA), how many factors are required for authentication? A. 1 B. 2 C. 3 D. 4 Suggested Answer: B
When a user authenticates by using passwordless sign-in, what should the user select in the Microsoft Authenticator app? A. an answer to a security question B. a number C. an alphanumeric key D. a passphrase Suggested Answer: B
Which service includes Microsoft Secure Score for Devices? A. Microsoft Defender for IoT B. Microsoft Defender for Endpoint C. Microsoft Defender for Identity D. Microsoft Defender for Office 365 Suggested Answer: B
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

You have an Azure subscription that contains a Log Analytics workspace. You need to onboard Microsoft Sentinel. What should you do first? A. Create a hunting query. B. Correlate alerts into incidents. C. Connect to your data sources. D. Create a custom detection rule. Suggested Answer: C
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:

What can you use to protect against malicious links sent in email messages, chat messages, and channels? A. Microsoft Defender for Cloud Apps B. Microsoft Defender for Office 365 C. Microsoft Defender for Endpoint D. Microsoft Defender for Identity Suggested Answer: B
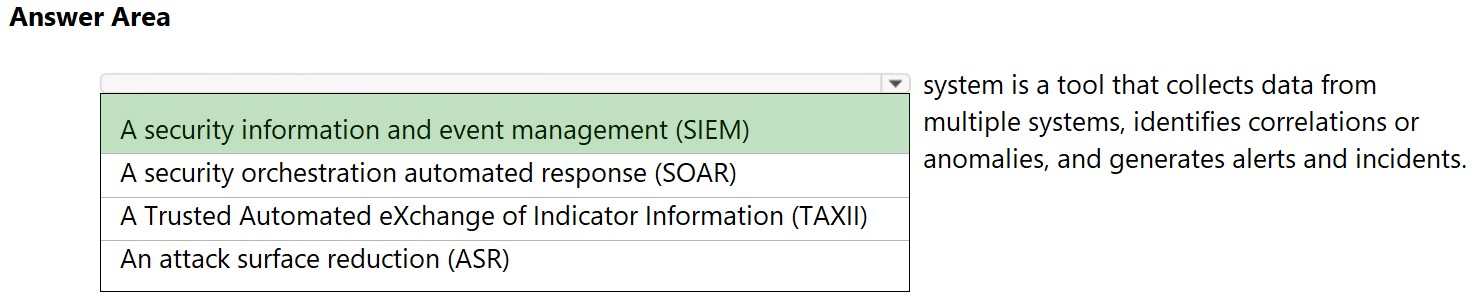
Which solution performs security assessments and automatically generates alerts when a vulnerability is found? A. cloud security posture management (CSPM) B. DevSecOps C. cloud workload protection platform (CWPP) D. security information and event management (SIEM) Suggested Answer: D
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.Suggested Answer:

Which Microsoft Purview solution can be used to identify data leakage? A. insider risk management B. Compliance Manager C. communication compliance D. eDiscovery Suggested Answer: A
HOTSPOT - Select the answer that correctly completes the sentence.Suggested Answer:
