SY0-501 Practice Test Free – 50 Questions to Test Your Knowledge
Are you preparing for the SY0-501 certification exam? If so, taking a SY0-501 practice test free is one of the best ways to assess your knowledge and improve your chances of passing. In this post, we provide 50 free SY0-501 practice questions designed to help you test your skills and identify areas for improvement.
By taking a free SY0-501 practice test, you can:
- Familiarize yourself with the exam format and question types
- Identify your strengths and weaknesses
- Gain confidence before the actual exam
50 Free SY0-501 Practice Questions
Below, you will find 50 free SY0-501 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level.
Multiple organizations operating in the same vertical want to provide seamless wireless access for their employees as they visit the other organizations. Which of the following should be implemented if all the organizations use the native 802.1x client on their mobile devices?
A. Shibboleth
B. RADIUS federation
C. SAML
D. OAuth
E. OpenID connect
Which of the following would a security specialist be able to determine upon examination of a server's certificate?
A. CA public key
B. Server private key
C. CSR
D. OID
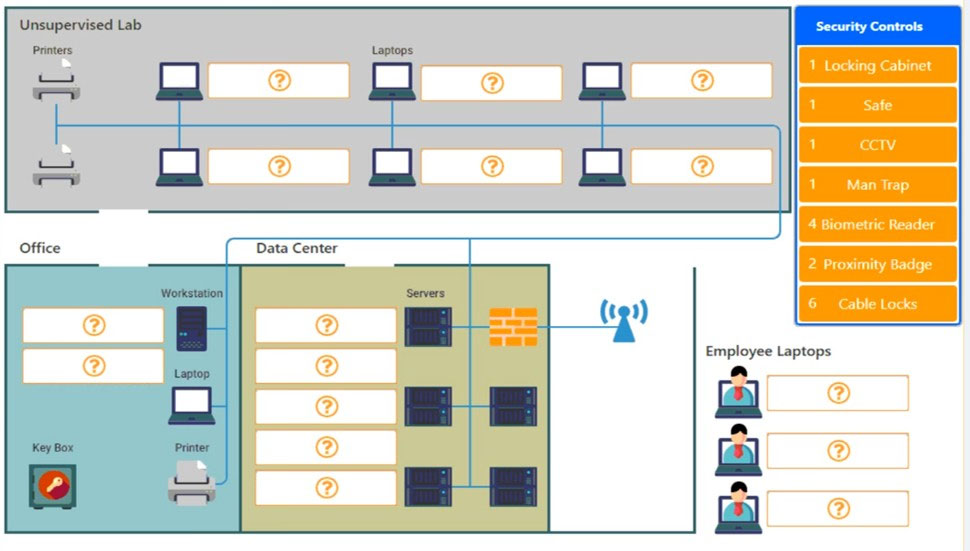
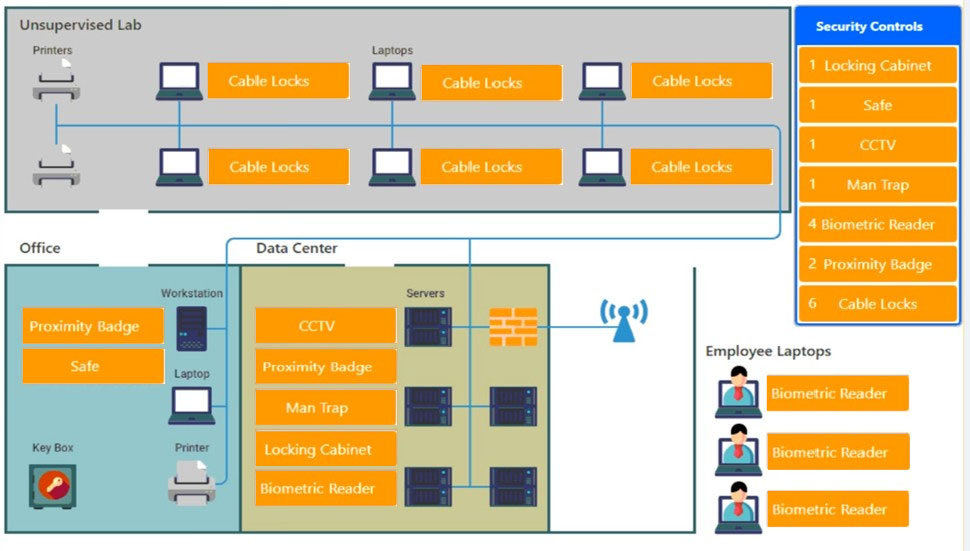
DRAG DROP - You have been tasked with designing a security plan for your company. INSTRUCTIONS - Drag and drop the appropriate security controls on the floor plan. All objects must be used and all place holders must be filled. Order does not matter. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Select and Place:
A department head at a university resigned on the first day of the spring semester. It was subsequently determined that the department head deleted numerous files and directories from the server-based home directory while the campus was closed. Which of the following policies or procedures could have prevented this from occurring?
A. Time-of-day restrictions
B. Permission auditing and review
C. Offboarding
D. Account expiration
A security engineer is configuring a system that requires the X.509 certificate information to be pasted into a form field in Base64 encoded format to import it into the system. Which of the following certificate formats should the engineer use to obtain the information in the required format?
A. PFX
B. PEM
C. DER
D. CER
Which of the following can be provided to an AAA system for the identification phase?
A. Username
B. Permissions
C. One-time token
D. Private certificate
A network administrator wants to implement a method of securing internal routing. Which of the following should the administrator implement?
A. DMZ
B. NAT
C. VPN
D. PAT
A botnet has hit a popular website with a massive number of GRE-encapsulated packets to perform a DDoS attack. News outlets discover a certain type of refrigerator was exploited and used to send outbound packets to the website that crashed. To which of the following categories does the refrigerator belong?
A. SoC
B. ICS
C. IoT
D. MFD
A company is using a mobile device deployment model in which employees use their personal devices for work at their own discretion. Some of the problems the company is encountering include the following: ✑ There is no standardization. ✑ Employees ask for reimbursement for their devices. ✑ Employees do not replace their devices often enough to keep them running efficiently. ✑ The company does not have enough control over the devices. Which of the following is a deployment model that would help the company overcome these problems?
A. BYOD
B. VDI
C. COPE
D. CYOD
A company is currently using the following configuration: ✑ IAS server with certificate-based EAP-PEAP and MSCHAP ✑ Unencrypted authentication via PAP A security administrator needs to configure a new wireless setup with the following configurations: ✑ PAP authentication method ✑ PEAP and EAP provide two-factor authentication Which of the following forms of authentication are being used? (Choose two.)
A. PAP
B. PEAP
C. MSCHAP
D. PEAP- MSCHAP
E. EAP
F. EAP-PEAP
An auditor wants to test the security posture of an organization by running a tool that will display the following:Which of the following commands should be used?
A. nbtstat
B. nc
C. arp
D. ipconfig
Which of the following types of cloud infrastructures would allow several organizations with similar structures and interests to realize the benefits of shared storage and resources?
A. Private
B. Hybrid
C. Public
D. Community
An organization has determined it can tolerate a maximum of three hours of downtime. Which of the following has been specified?
A. RTO
B. RPO
C. MTBF
D. MTTR
Despite having implemented password policies, users continue to set the same weak passwords and reuse old passwords. Which of the following technical controls would help prevent these policy violations? (Choose two.)
A. Password expiration
B. Password length
C. Password complexity
D. Password history
E. Password lockout
Refer to the following code:Which of the following vulnerabilities would occur if this is executed?
A. Page exception
B. Pointer deference
C. NullPointerException
D. Missing null check
Which of the following explains why vendors publish MD5 values when they provide software patches for their customers to download over the Internet?
A. The recipient can verify integrity of the software patch.
B. The recipient can verify the authenticity of the site used to download the patch.
C. The recipient can request future updates to the software using the published MD5 value.
D. The recipient can successfully activate the new software patch.
A penetration tester is crawling a target website that is available to the public. Which of the following represents the actions the penetration tester is performing?
A. URL hijacking
B. Reconnaissance
C. White box testing
D. Escalation of privilege
A security consultant discovers that an organization is using the PCL protocol to print documents, utilizing the default driver and print settings. Which of the following is the MOST likely risk in this situation?
A. An attacker can access and change the printer configuration.
B. SNMP data leaving the printer will not be properly encrypted.
C. An MITM attack can reveal sensitive information.
D. An attacker can easily inject malicious code into the printer firmware.
E. Attackers can use the PCL protocol to bypass the firewall of client computers.
Which of the following best describes routine in which semicolons, dashes, quotes, and commas are removed from a string?
A. Error handling to protect against program exploitation
B. Exception handling to protect against XSRF attacks.
C. Input validation to protect against SQL injection.
D. Padding to protect against string buffer overflows.
As part of a new industry regulation, companies are required to utilize secure, standardized OS settings. A technical must ensure the OS settings are hardened. Which of the following is the BEST way to do this?
A. Use a vulnerability scanner.
B. Use a configuration compliance scanner.
C. Use a passive, in-line scanner.
D. Use a protocol analyzer.
Which of the following threat actors is MOST likely to steal a company's proprietary information to gain a market edge and reduce time to market?
A. Competitor
B. Hacktivist
C. Insider
D. Organized crime.
A security administrator is developing controls for creating audit trails and tracking if a PHI data breach is to occur. The administrator has been given the following requirements: All access must be correlated to a user account.✑ All user accounts must be assigned to a single individual. ✑ User access to the PHI data must be recorded. ✑ Anomalies in PHI data access must be reported. ✑ Logs and records cannot be deleted or modified. Which of the following should the administrator implement to meet the above requirements? (Choose three.)
A. Eliminate shared accounts.
B. Create a standard naming convention for accounts.
C. Implement usage auditing and review.
D. Enable account lockout thresholds.
E. Copy logs in real time to a secured WORM drive.
F. Implement time-of-day restrictions.
G. Perform regular permission audits and reviews.
A security analyst is hardening a server with the directory services role installed. The analyst must ensure LDAP traffic cannot be monitored or sniffed and maintains compatibility with LDAP clients. Which of the following should the analyst implement to meet these requirements? (Choose two.)
A. Generate an X.509-compliant certificate that is signed by a trusted CA.
B. Install and configure an SSH tunnel on the LDAP server.
C. Ensure port 389 is open between the clients and the servers using the communication.
D. Ensure port 636 is open between the clients and the servers using the communication.
E. Remote the LDAP directory service role from the server.
A security analyst is hardening an authentication server. One of the primary requirements is to ensure there is mutual authentication and delegation. Given these requirements, which of the following technologies should the analyst recommend and configure?
A. LDAP services
B. Kerberos services
C. NTLM services
D. CHAP services
Which of the following cryptographic attacks would salting of passwords render ineffective?
A. Brute force
B. Dictionary
C. Rainbow tables
D. Birthday
Which of the following attack types BEST describes a client-side attack that is used to manipulate an HTML iframe with JavaScript code via a web browser?
A. Buffer overflow
B. MITM
C. XSS
D. SQLi
A company hires a consulting firm to crawl its Active Directory network with a non-domain account looking for unpatched systems. Actively taking control of systems is out of scope, as is the creation of new administrator accounts. For which of the following is the company hiring the consulting firm?
A. Vulnerability scanning
B. Penetration testing
C. Application fuzzing
D. User permission auditing
An organization wishes to provide better security for its name resolution services. Which of the following technologies BEST supports the deployment of DNSSEC at the organization?
A. LDAP
B. TPM
C. TLS
D. SSL
E. PKI
A user clicked an email link that led to a website than infected the workstation with a virus. The virus encrypted all the network shares to which the user had access. The virus was not deleted or blocked by the company's email filter, website filter, or antivirus. Which of the following describes what occurred?
A. The user’s account was over-privileged.
B. Improper error handling triggered a false negative in all three controls.
C. The email originated from a private email server with no malware protection.
D. The virus was a zero-day attack.
When connected to a secure WAP, which of the following encryption technologies is MOST likely to be configured when connecting to WPA2-PSK?
A. DES
B. AES
C. MD5
D. WEP
A company is developing a new secure technology and requires computers being used for development to be isolated. Which of the following should be implemented to provide the MOST secure environment?
A. A perimeter firewall and IDS
B. An air gapped computer network
C. A honeypot residing in a DMZ
D. An ad hoc network with NAT
E. A bastion host
When configuring settings in a mandatory access control environment, which of the following specifies the subjects that can access specific data objects?
A. Owner
B. System
C. Administrator
D. User
When identifying a company's most valuable assets as part of a BIA, which of the following should be the FIRST priority?
A. Life
B. Intellectual property
C. Sensitive data
D. Public reputation
A company's user lockout policy is enabled after five unsuccessful login attempts. The help desk notices a user is repeatedly locked out over the course of a workweek. Upon contacting the user, the help desk discovers the user is on vacation and does not have network access. Which of the following types of attacks are MOST likely occurring? (Select two.)
A. Replay
B. Rainbow tables
C. Brute force
D. Pass the hash
E. Dictionary
A company has three divisions, each with its own networks and services. The company decides to make its secure web portal accessible to all employees utilizing their existing usernames and passwords. The security administrator has elected to use SAML to support authentication. In this scenario, which of the following will occur when users try to authenticate to the portal? (Choose two.)
A. The portal will function as a service provider and request an authentication assertion.
B. The portal will function as an identity provider and issue an authentication assertion.
C. The portal will request an authentication ticket from each network that is transitively trusted.
D. The back-end networks will function as an identity provider and issue an authentication assertion.
E. The back-end networks will request authentication tickets from the portal, which will act as the third-party service provider authentication store.
F. The back-end networks will verify the assertion token issued by the portal functioning as the identity provider.
Ann, a security administrator, has been instructed to perform fuzz-based testing on the company's applications. Which of the following best describes what she will do?
A. Enter random or invalid data into the application in an attempt to cause it to fault
B. Work with the developers to eliminate horizontal privilege escalation opportunities
C. Test the applications for the existence of built-in- back doors left by the developers
D. Hash the application to verify it won’t cause a false positive on the HIPS
A security analyst observes the following events in the logs of an employee workstation:Given the information provided, which of the following MOST likely occurred on the workstation?
A. Application whitelisting controls blocked an exploit payload from executing.
B. Antivirus software found and quarantined three malware files.
C. Automatic updates were initiated but failed because they had not been approved.
D. The SIEM log agent was not tuned properly and reported a false positive.
A company has a data classification system with definitions for `Private` and `Public`. The company's security policy outlines how data should be protected based on type. The company recently added the data type `Proprietary`. Which of the following is the MOST likely reason the company added this data type?
A. Reduced cost
B. More searchable data
C. Better data classification
D. Expanded authority of the privacy officer
An analyst wants to implement a more secure wireless authentication for office access points. Which of the following technologies allows for encrypted authentication of wireless clients over TLS?
A. PEAP
B. EAP
C. WPA2
D. RADIUS
When performing data acquisition on a workstation, which of the following should be captured based on memory volatility? (Choose two.)
A. USB-attached hard disk
B. Swap/pagefile
C. Mounted network storage
D. ROM
E. RAM
Which of the following network vulnerability scan indicators BEST validates a successful, active scan?
A. The scan job is scheduled to run during off-peak hours.
B. The scan output lists SQL injection attack vectors.
C. The scan data identifies the use of privileged-user credentials.
D. The scan results identify the hostname and IP address.
After a user reports stow computer performance, a systems administrator detects a suspicious file, which was installed as part of a freeware software package. The systems administrator reviews the output below:Based on the above information, which of the following types of malware was installed on the user's computer?
A. RAT
B. Keylogger
C. Spyware
D. Worm
E. Bot
A senior incident response manager receives a call about some external IPs communicating with internal computers during off hours. Which of the following types of malware is MOST likely causing this issue?
A. Botnet
B. Ransomware
C. Polymorphic malware
D. Armored virus
During a monthly vulnerability scan, a server was flagged for being vulnerable to an Apache Struts exploit. Upon further investigation, the developer responsible for the server informs the security team that Apache Struts is not installed on the server. Which of the following BEST describes how the security team should reach to this incident?
A. The finding is a false positive and can be disregarded
B. The Struts module needs to be hardened on the server
C. The Apache software on the server needs to be patched and updated
D. The server has been compromised by malware and needs to be quarantined.
Which of the following are methods to implement HA in a web application server environment? (Choose two.)
A. Load balancers
B. Application layer firewalls
C. Reverse proxies
D. VPN concentrators
E. Routers
As part of the SDLC, a third party is hired to perform a penetration test. The third party will have access to the source code, integration tests, and network diagrams. Which of the following BEST describes the assessment being performed?
A. Black box
B. Regression
C. White box
D. Fuzzing
The availability of a system has been labeled as the highest priority. Which of the following should be focused on the MOST to ensure the objective?
A. Authentication
B. HVAC
C. Full-disk encryption
D. File integrity checking
An application developer is designing an application involving secure transports from one service to another that will pass over port 80 for a request. Which of the following secure protocols is the developer MOST likely to use?
A. FTPS
B. SFTP
C. SSL
D. LDAPS
E. SSH
A user is presented with the following items during the new-hire onboarding process: -Laptop -Secure USB drive -Hardware OTP token -External high-capacity HDD -Password complexity policy -Acceptable use policy -HASP key -Cable lock Which of the following is one component of multifactor authentication?
A. Secure USB drive
B. Cable lock
C. Hardware OTP token
D. HASP key
Before an infection was detected, several of the infected devices attempted to access a URL that was similar to the company name but with two letters transposed. Which of the following BEST describes the attack vector used to infect the devices?
A. Cross-site scripting
B. DNS poisoning
C. Typo squatting
D. URL hijacking
Get More SY0-501 Practice Questions
If you’re looking for more SY0-501 practice test free questions, click here to access the full SY0-501 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your SY0-501 certification journey!