A recent security audit identified that a company's application team injects database credentials into the environment variables of an AWS Fargate task. The company's security policy mandates that all sensitive data be encrypted at rest and in transit.
Which combination of actions should the security team take to make the application compliant with the security policy? (Choose three.)
A. Store the credentials securely in a file in an Amazon S3 bucket with restricted access to the application team IAM role. Ask the application team to read the credentials from the S3 object instead.
B. Create an AWS Secrets Manager secret and specify the key/value pairs to be stored in this secret.
C. Modify the application to pull credentials from the AWS Secrets Manager secret instead of the environment variables.
D. Add the following statement to the container instance IAM role policy:
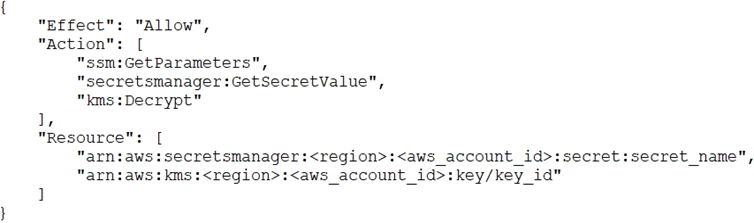 E. Add the following statement to the task execution role policy:
E. Add the following statement to the task execution role policy:
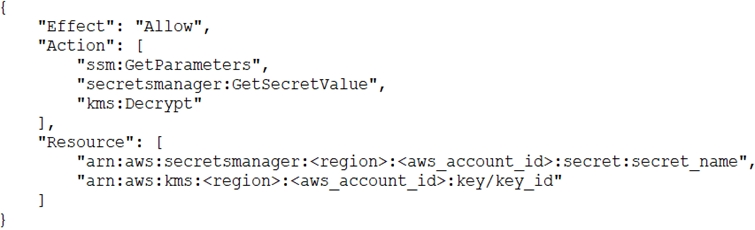 F. Log in to the AWS Fargate instance, create a script to read the secret value from AWS Secrets Manager, and inject the environment variables. Ask the application team to redeploy the application.
Suggested Answer: AEF
Community Answer: BCE
This question is in SCS-C01 AWS Certified Security – Specialty Exam
For getting AWS Certified Security – Specialty Certificate
Disclaimers:
The website is not related to, affiliated with, endorsed or authorized by Amazon.
Trademarks, certification & product names are used for reference only and belong to Amazon.
The website does not contain actual questions and answers from Amazon's Certification Exam.
F. Log in to the AWS Fargate instance, create a script to read the secret value from AWS Secrets Manager, and inject the environment variables. Ask the application team to redeploy the application.
Suggested Answer: AEF
Community Answer: BCE
This question is in SCS-C01 AWS Certified Security – Specialty Exam
For getting AWS Certified Security – Specialty Certificate
Disclaimers:
The website is not related to, affiliated with, endorsed or authorized by Amazon.
Trademarks, certification & product names are used for reference only and belong to Amazon.
The website does not contain actual questions and answers from Amazon's Certification Exam.Please login or Register to submit your answer






